A mobile communication system user identity concealment method initiated by a terminal
A mobile communication system and user identity technology, applied in the field of user identity concealment in mobile communication systems, can solve the problems of inability to resist attacks or APT attacks, and security measures are difficult to meet high security users, and achieve the effect of a wide range of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
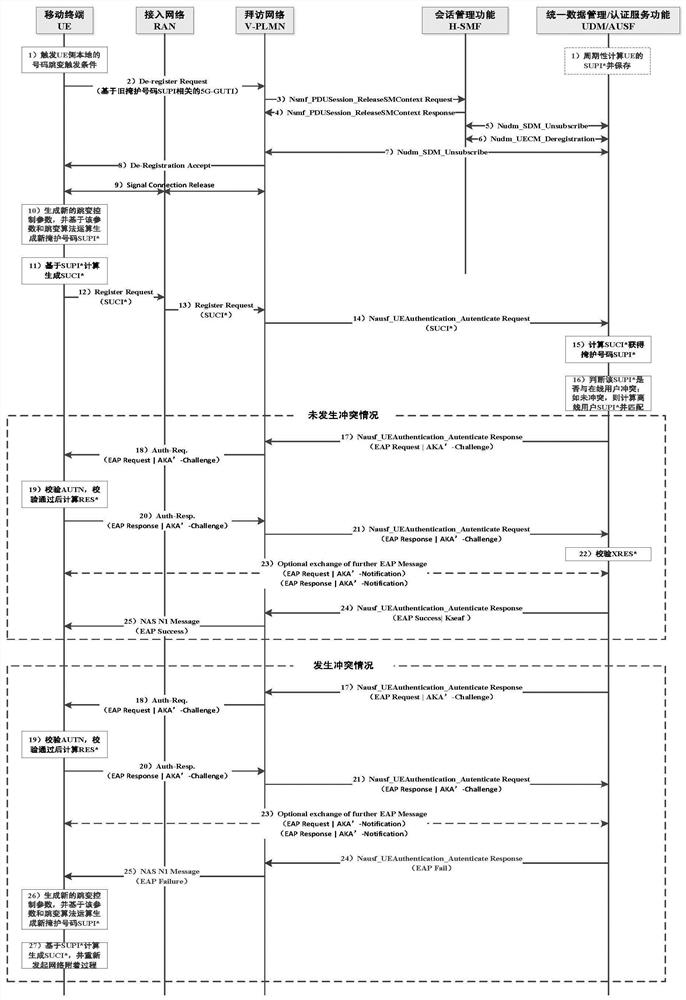
[0026] Aiming at the problem in the prior art that it is difficult to hide the real IMSI or SUPI of the UE in the service network, the present invention provides a method for concealing the IMSI or SUPI initiated by the terminal in the mobile communication system, which is based on the following foundations: Users who need this kind of identity concealment (referred to as special users) belong to the same industry or the same organization or the same group. They can be established by specific industries, party, government, military, government departments, large enterprises or operators for users who need special security services. Specific user groups (referred to as specific industries) have the same identity information concealment requirements, and the user's subscription information is invisible to mobile operators when they are not authorized; operators are willing to provide support for identity concealment for special users, providing additional IMSI or SUPI number reso...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com