Double-layer frame optical watermark method based on computational ghost imaging
An optical watermarking and ghost imaging technology, applied in image watermarking, computing, image data processing, etc., can solve the problems of weak anti-attack ability and poor robustness, and achieve the goal of enhancing security, improving security, and expanding key space. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
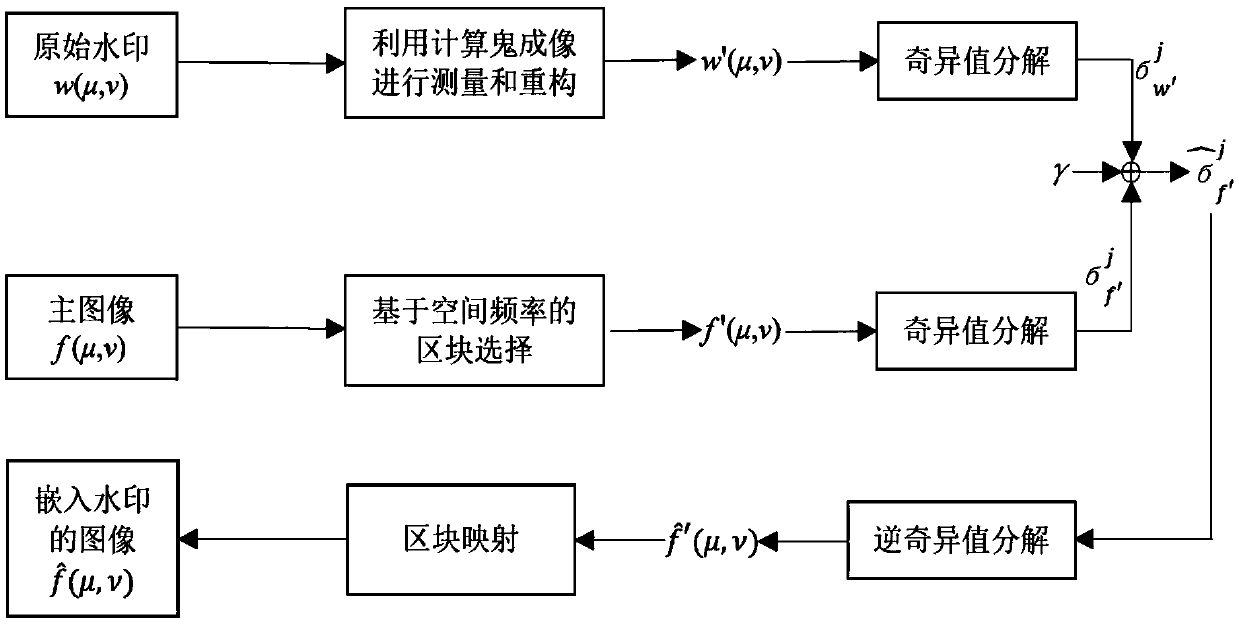
[0047] Such as Figure 2a , Figure 2b , in the USC-SIPI image database, the grayscale image "pepper" with a pixel size of 128×128 is used as the main image; the binary image "flower" with a pixel size of 64×64 is used as the watermark. The size of non-overlapping blocks segmented from the main image is set to 4×4 pixels, ie p=4 and q=4. Based on the singular value decomposition, the actual weighting factor for embedding the new watermark into the reference image is set to 1×10 -5 , the applied nonlinear strength was set to ρ = 0.4. Specific steps are as follows:
[0048] Step 1, use the computational ghost imaging method to encode the original watermark image "flower" into a series of measured intensity values, and rearrange these intensity data into a two-dimensional temporary image as the new watermark of the first layer, the resulting optically measured intensity The value expression is:
[0049] B i =∫∫dμdνI i (μ,ν)T(μ,ν) (1)
[0050] where T(μ,v) is the transfer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com