Improved AKA identity authentication system and method based on symmetric secret key pool and relay communication
An identity authentication and relay communication technology, applied in the field of private identity authentication and key negotiation, can solve the problems of key information leakage, insufficient transmission of important information, and inability to maintain the freshness of the key seed or the variable range, etc. The effect of ensuring safety and improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0074] systems mannual
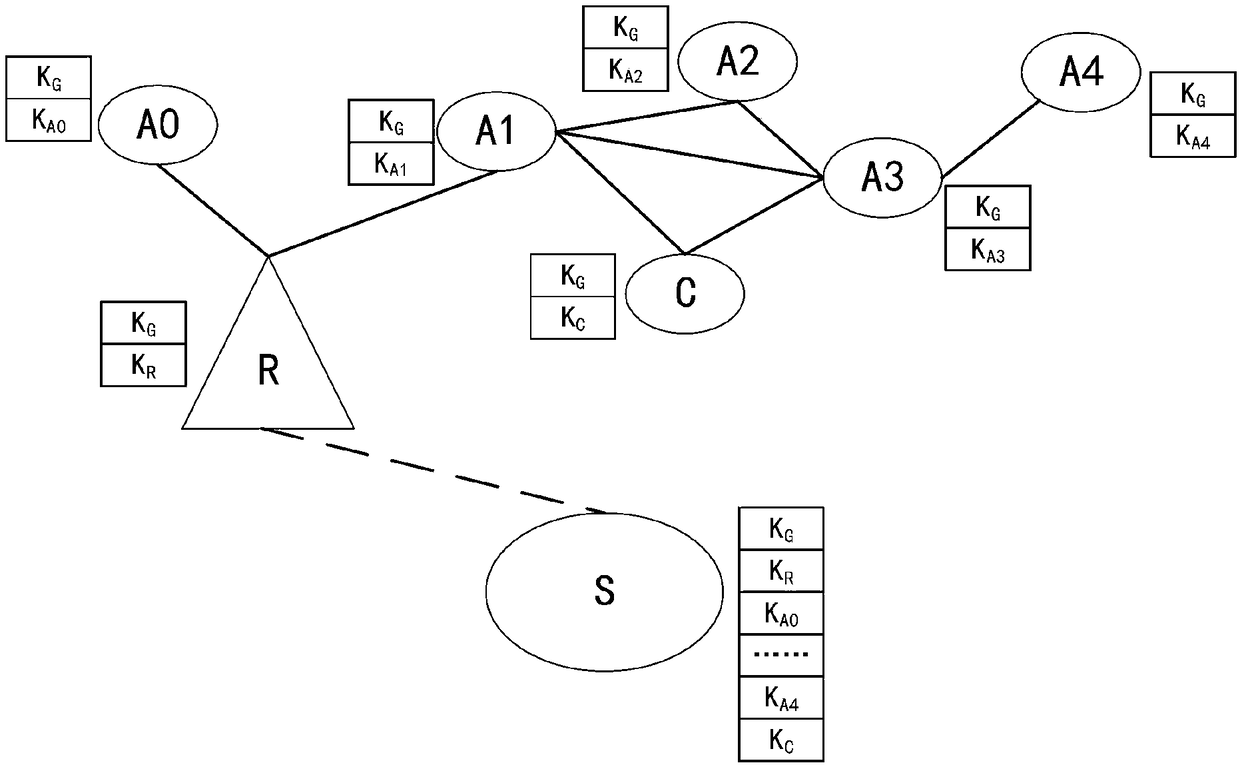
[0075] The scenario of this embodiment is as figure 1 As shown, in this figure, member R, member A0, member A1, member A2, member A3, member A4, and member C are all members of the same group, and member R is a relay unit.
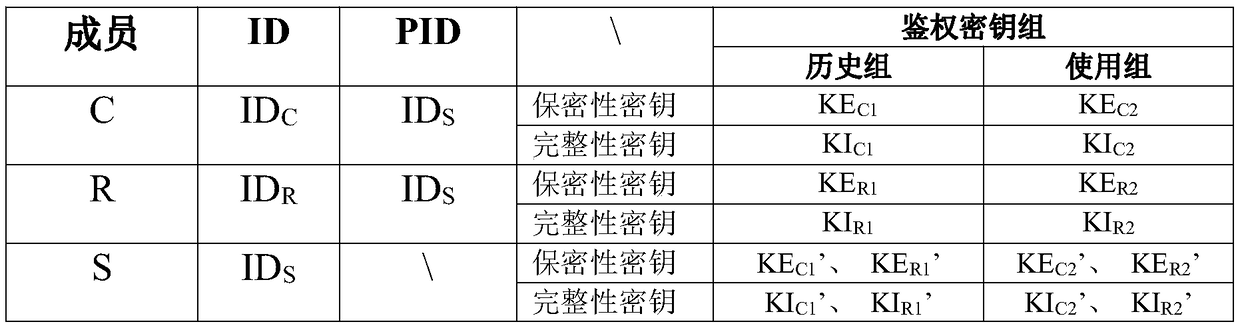
[0076] In this figure, the active party participating in the authentication is C, which contains the private key pool K C and group key pool K G ; The passive party participating in the authentication is R, which contains the private key pool K R and group key pool K G .
[0077] The private key pool is a symmetric key pool between members and the server, and the group key pool is a symmetric key pool between members in the group.
[0078] Member S is the key management server and also serves as the server. Both member C and member R belong to S, which contains the private key pool and group key pool K of all members. G .
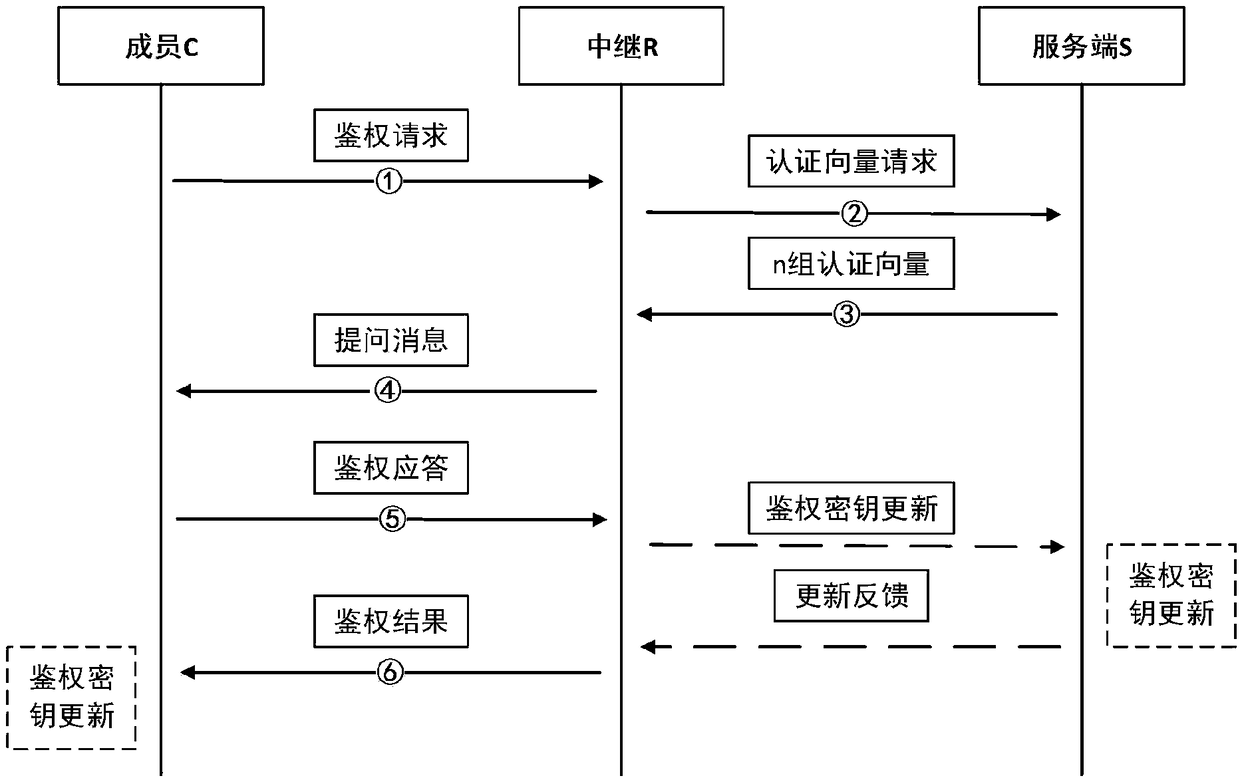
[0079] As a communication relay, member R has performed identity authentication and key negotiation wi...
Embodiment 2
[0138] systems mannual
[0139] Such as Figure 4 As shown, the identity authentication system of the present invention may include multiple key management servers, and different key management servers are located in different quantum network service stations. Each quantum network service station is in the quantum communication network, so quantum network service stations can share inter-station quantum keys through QKD, thus ensuring high information security.
[0140] Such as Figure 4 , in this figure, member R, member A0, member A1, member A2, member A3, member A4 and member C are all members of the same group, and member R is a relay unit. The active party participating in the authentication is C, who is a member of the group and contains the private key pool K C and group key pool K G ; The passive party participating in the authentication is R, which is a relay member and contains a private key pool K R and group key pool K G ; Members S1 and S2 are key management...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com