Method for cross-domain tracing based on stream fingerprint
A fingerprint and cross-domain technology, which is applied in the field of cross-domain traceability based on flow fingerprints, can solve problems such as false data packet and IP header replacement attacks, misleading suspicious path extraction, and limited marked content, so as to avoid loop deception and build paths Efficient, damage-reducing effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments, but the protection scope of the present invention is not limited thereto.
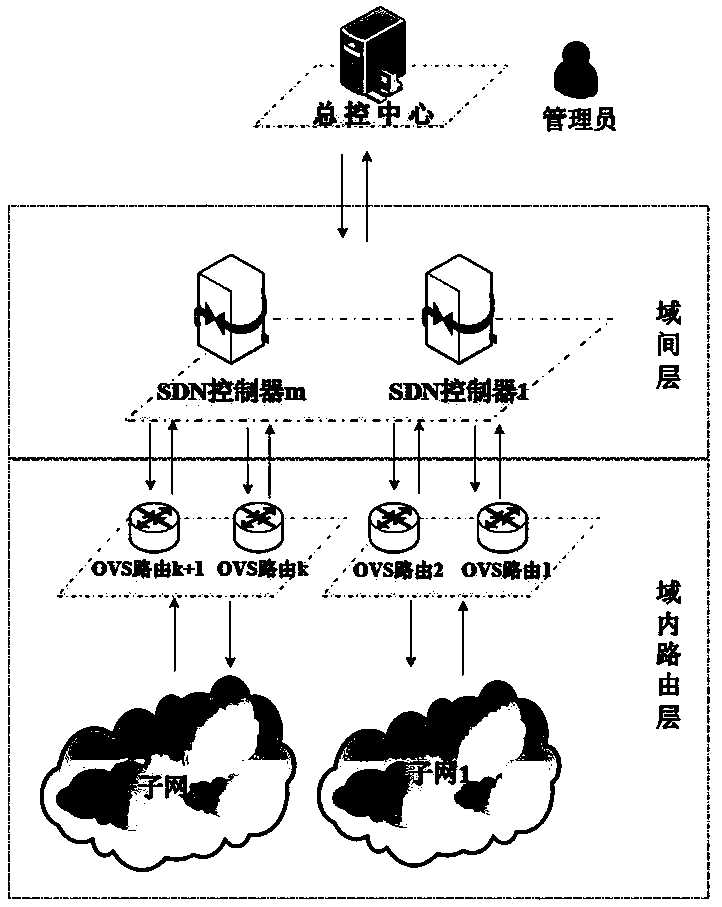
[0045] The present invention provides a method for cross-domain source tracing based on flow fingerprints. By adopting the idea of multi-layer collaboration, attack path reconstruction and suspicious attack source location are respectively performed from the inter-domain layer and the intra-domain routing layer. The method includes the following steps:
[0046] Step 1: In the inter-domain layer, first construct the global network topology relationship according to the inter-domain SDN controller; on this basis, use the flow fingerprint of the suspicious data flow to realize the association of different data flows, so as to construct the inter-domain suspicious attack path.
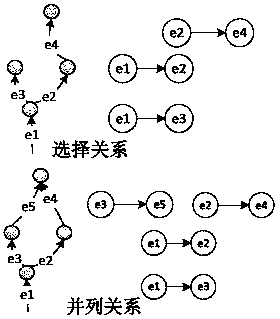
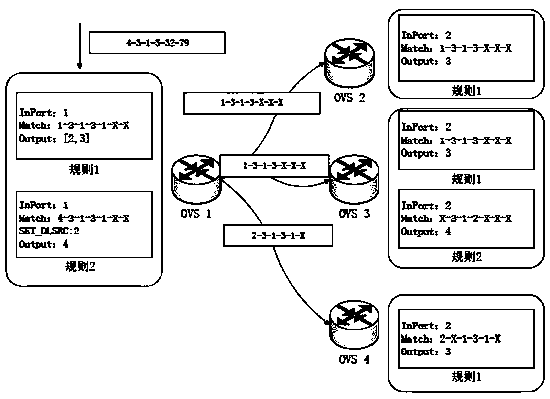
[0047] Furthermore, because the construction of suspicious attack paths between domain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com