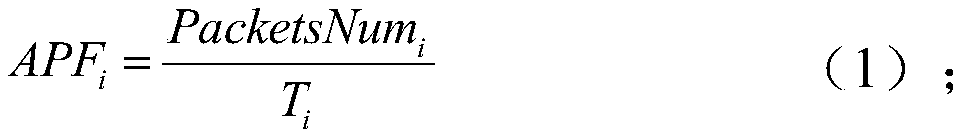A method and system for detect LDoS attack data stream in cloud environment
A detection method and data flow technology, applied in transmission systems, instruments, character and pattern recognition, etc., can solve problems such as high cost, high cost, and inability to guarantee, and achieve the effect of improving service quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
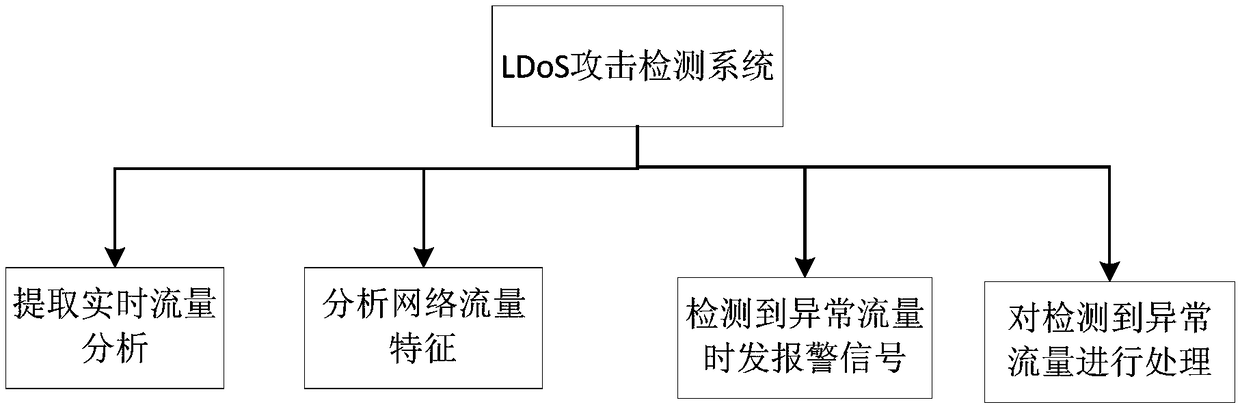
[0054] The present invention discloses a cloud environment LDoS attack data flow detection method and system. In order to make the present invention more obvious and understandable, the present invention will be further described below in conjunction with the accompanying drawings and specific implementation methods.
[0055] Such as figure 1 As shown, the cloud environment LDoS attack data flow detection method of the present invention comprises the following steps:
[0056] S1: Simulate various LDoS attacks on network simulation software, and extract corresponding network traffic.
[0057] Among them, the network simulation software is a free software simulation platform with open source code for network technology, which can simulate real communication to the greatest extent, and set different parameters according to experimental requirements to simulate different communication processes. During the LDoS attack process, extracting the corresponding experimental data can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com