Electronic banking anti-fraud method and device
An electronic banking and behavioral technology, applied in the field of computer information, can solve the problems of low accuracy rate and achieve the effect of improving accuracy rate and ensuring account security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
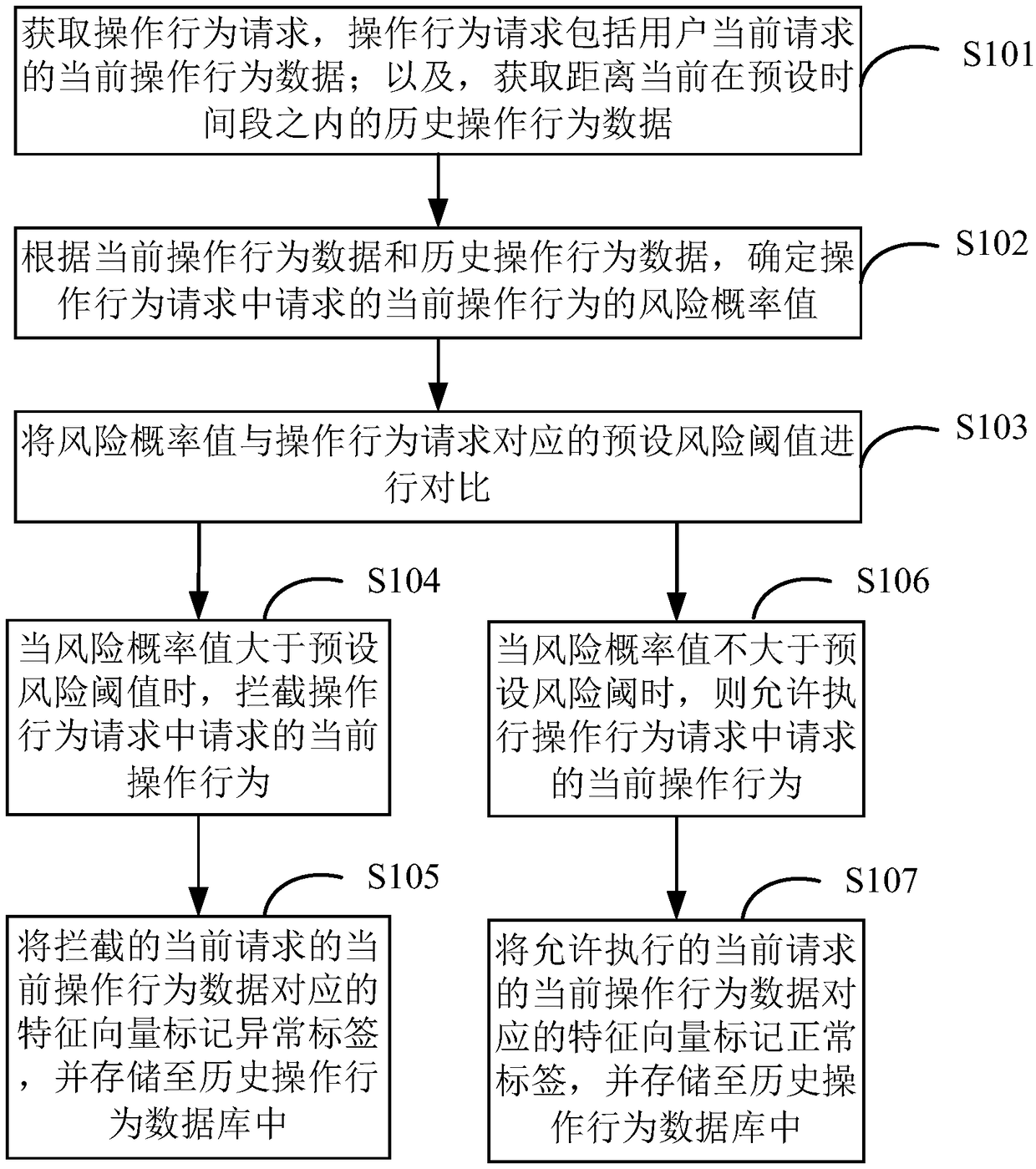
[0066] Such as figure 2 As shown, it is a flow chart of an electronic bank anti-fraud method provided in the embodiment of this application, and the specific steps are as follows:
[0067] S101. Obtain an operation behavior request, where the operation behavior request includes current operation behavior data currently requested by the user; and acquire historical operation behavior data within a preset time period from the current one.
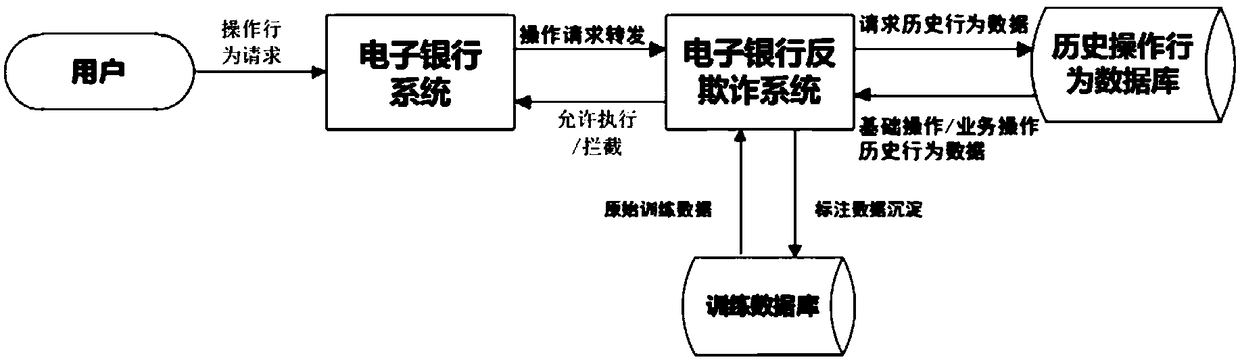
[0068] In a specific implementation, when the electronic bank client detects that the user is operating the electronic bank, the electronic bank client may transmit the detected operation behavior request of the user to the electronic bank anti-fraud system. Furthermore, the electronic banking anti-fraud system can obtain the user's operation behavior request, and the operation behavior request includes the current operation behavior data currently requested by the user. Among them, the type of the operation behavior request can be divided ...
Embodiment 2
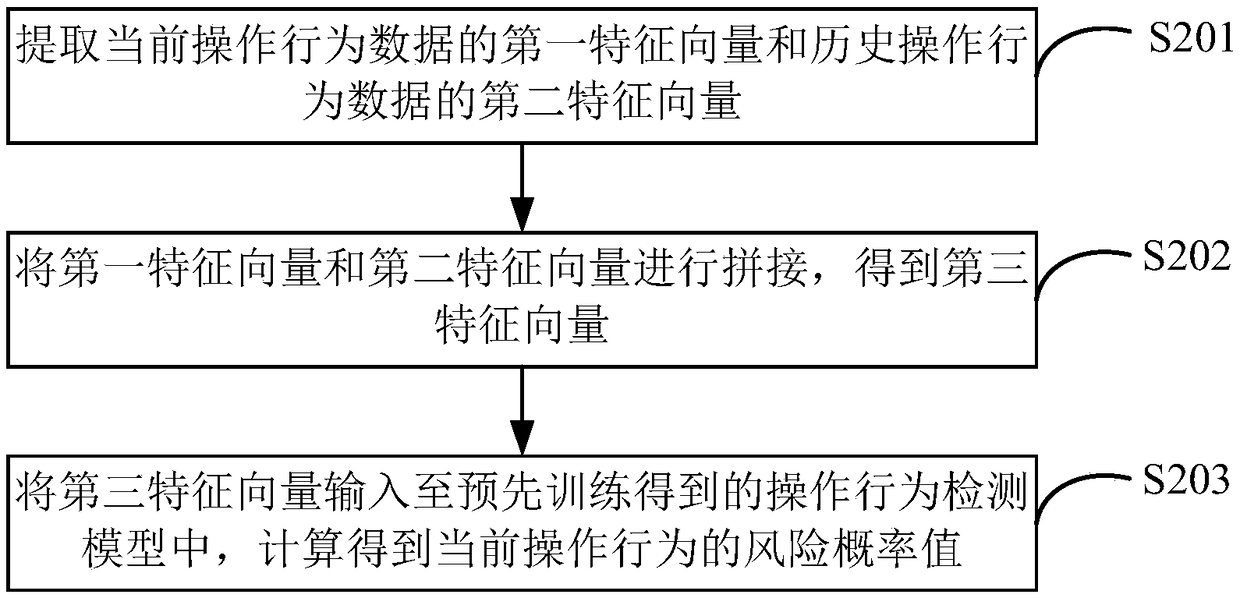
[0118] Such as Figure 8 As shown, it is a flow chart of training the operation behavior detection model in an electronic bank anti-fraud method provided by the embodiment of the present application. The specific steps are as follows:
[0119] S401. Obtain a training sample set, the training sample set includes a positive sample pair and a negative sample pair, wherein each positive sample pair includes the normal historical operation behavior data at the i-th moment and the preset time before the i-th moment Each negative sample pair includes the abnormal historical operating behavior data at the jth moment and the historical operating behavior data within the preset time period before the jth moment.
[0120] Before the operation behavior detection model to be trained is trained, a training sample set is obtained, which includes a large number of positive sample pairs and negative sample pairs, and the obtained training sample set is input into the operation behavior detecti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com