Pseudowire encryption method in MPLS-TP
An encryption method and pseudowire technology, which is applied in the field of pseudowire encryption in MPLS-TP, can solve problems such as the lack of pseudowire end-to-end encryption solutions, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
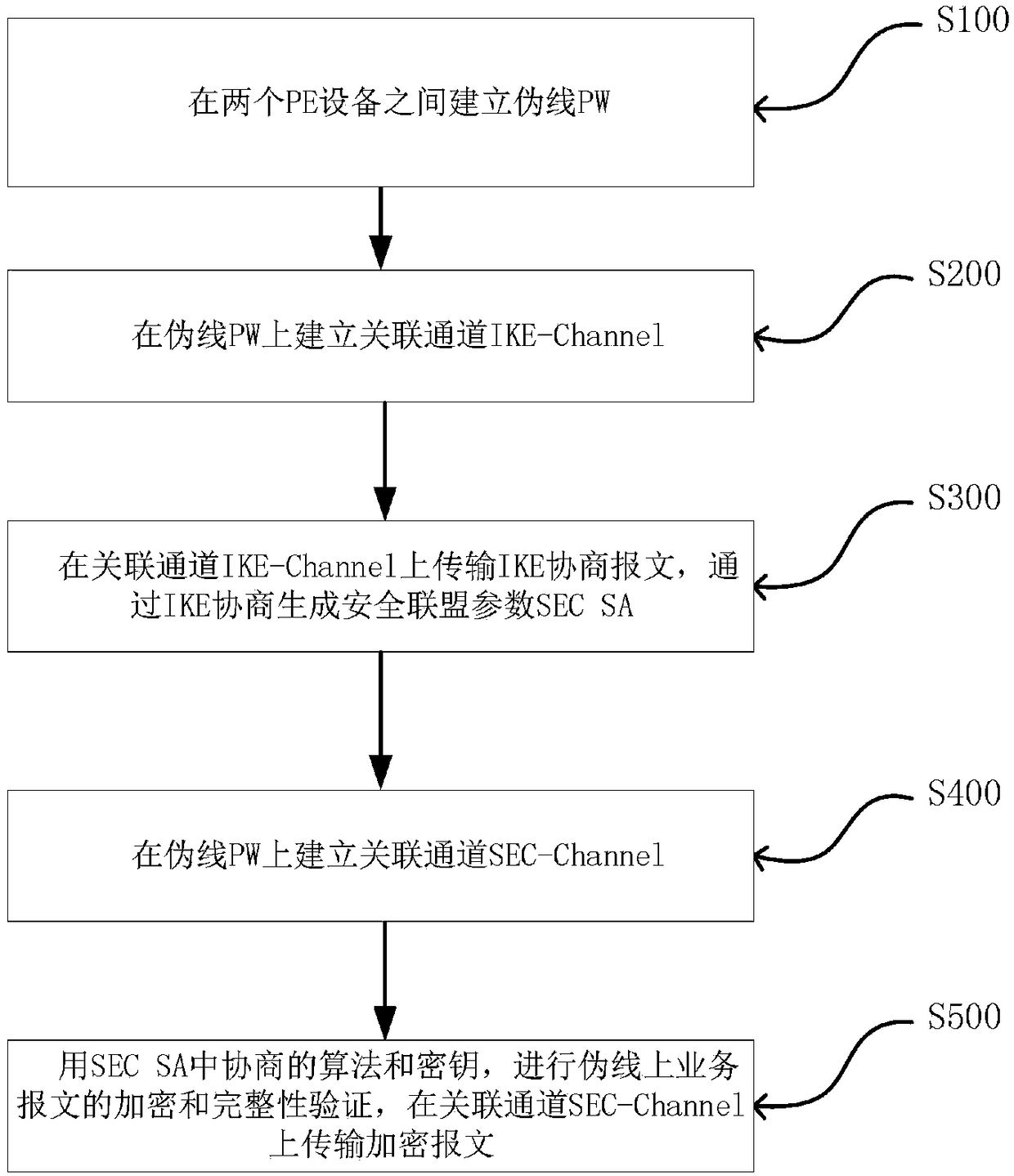
[0067] Pseudowire encryption using IKEv1 negotiation; including the following steps:
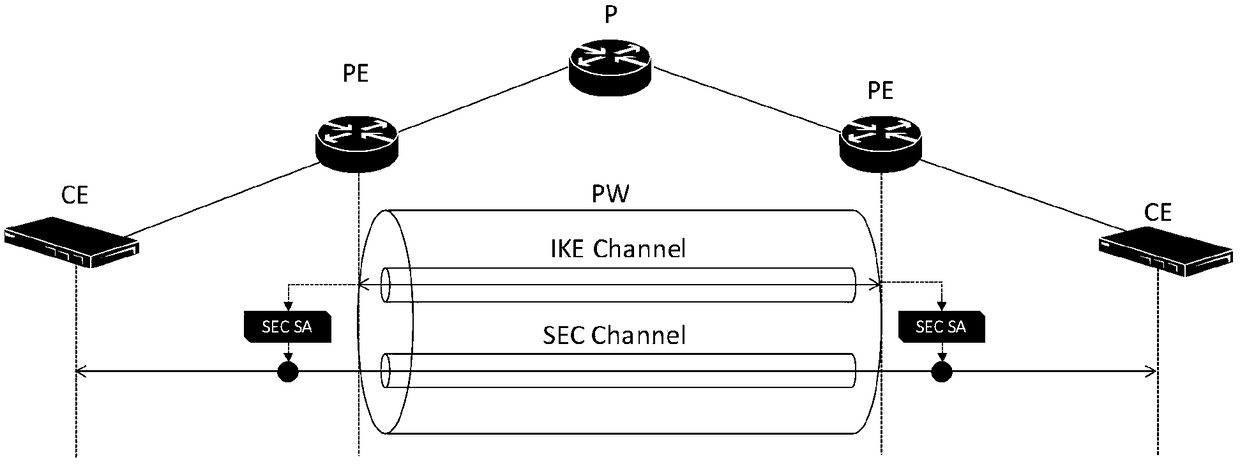
[0068] Step 1: Establish a pseudowire PW between two PE devices. The detailed steps are: configure MPLS-TP between two PE devices, including:
[0069] 1) Set the device IP address and routing;
[0070] 2) Define VPWS instance;
[0071] 3) Configure the AC port;
[0072] 4) Configure pseudowire parameters;
[0073] Step 2: Establish an associated channel IKE-Channel on the pseudowire PW. The detailed steps are: configure the IKE parameter set, including:
[0074] 1) IKE version and mode, such as IKEv1 main mode;
[0075] 2) Encryption and decryption algorithms, such as AES-128;
[0076] 3) Integrity verification algorithm, such as SHA-256;
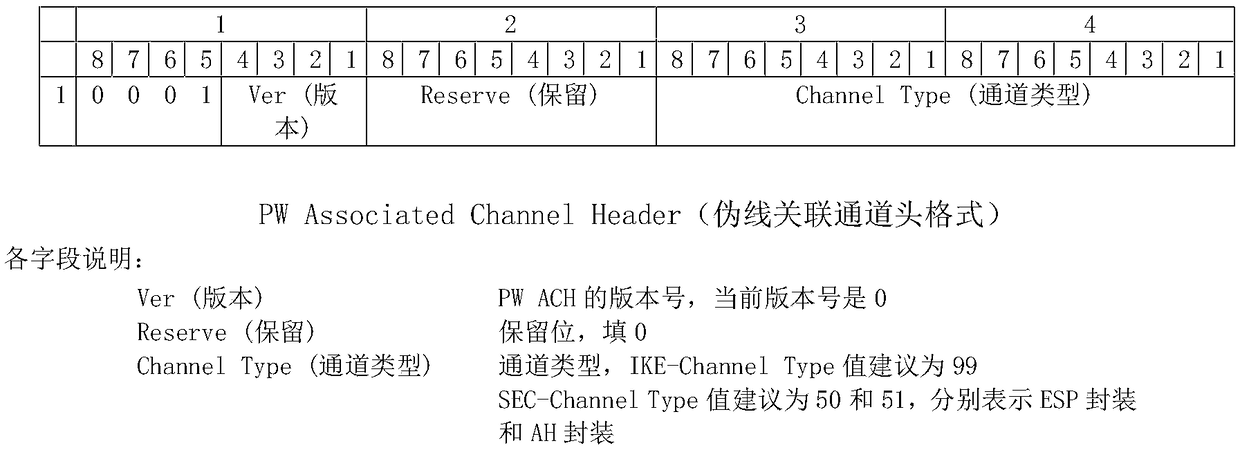
[0077] 4) An identity authentication method, such as a pre-shared key; 5) Select an encapsulation format, such as ESP. Then configure the associated channel IKE-Channel on the pseudowire PW, set the Channel-type value to 99, and associate the IKE p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com