A security visual analysis system based on company internal log
A technology for analyzing systems and logs, applied in file systems, file system functions, structured data retrieval, etc., can solve problems such as neglect, internal employee attack behavior and illegal operations that cannot be effectively supervised, and achieve the effect of wide coverage and low threshold
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings.
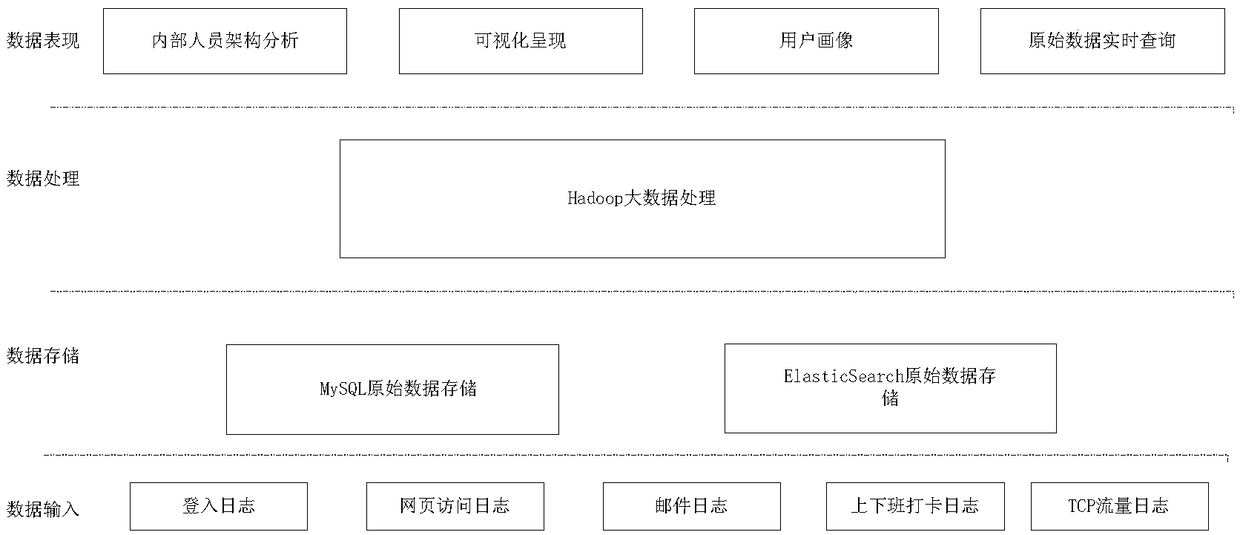
[0030] refer to Figure 1 to Figure 8 , a security visualization analysis system based on the company's internal security logs in the big data scenario, based on the perspective of internal network user behavior, mining internal network security threat events in a visualized form, and based on internal employee network behavior data in a variety of The display in the form of a visual view can better display the user behavior information of employees.
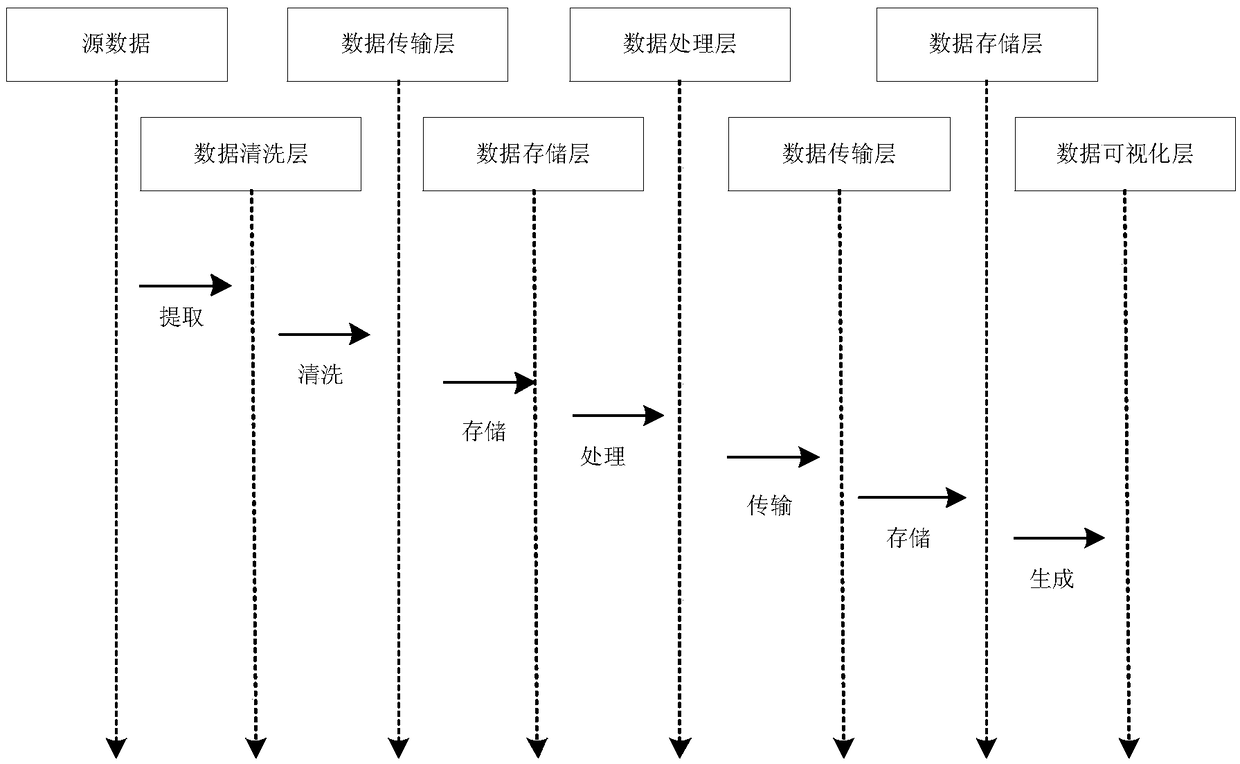
[0031] The security visualization analysis system is divided into five levels: data cleaning layer, data storage layer, data processing layer, data transmission layer and data visualization layer;
[0032] The data cleaning layer is used to store the original internal security log into the corresponding folder in the distributed system HDFS of Hadoop in units of days by the form of the API interface of Hadoop, and the n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com