Java program execution method and device
A program execution and program technology, applied in the field of Java program execution methods and devices, can solve problems such as inability to effectively protect Java programs, and achieve the effect of preventing decompilation and theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
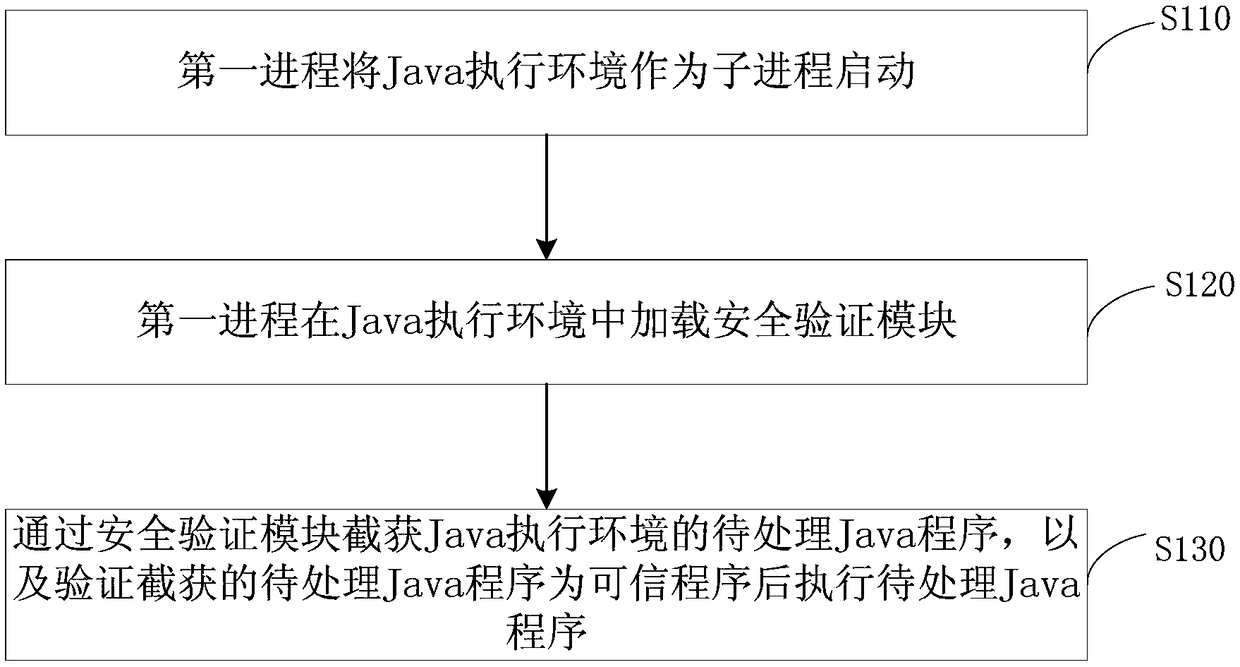
[0020] figure 1 It is a flowchart of a method for executing a Java program provided in Embodiment 1 of the present invention. This embodiment is applicable to the Java platform, and the method can be executed by a Java program execution device, which can be composed of hardware and / or software. Such as figure 1 As shown, it specifically includes the following steps:
[0021] S110. The first process starts the Java execution environment as a child process.
[0022] Optionally, before the first process starts the Java execution environment as a child process, it further includes: injecting the first process, the Java execution environment and a security verification module. The embodiment of the present invention does not modify the Java execution environment.
[0023] After the first process is started, the Java execution environment is started as a child process.
[0024] S120. The first process loads the security verification module in the Java execution environment.
[...
Embodiment 2
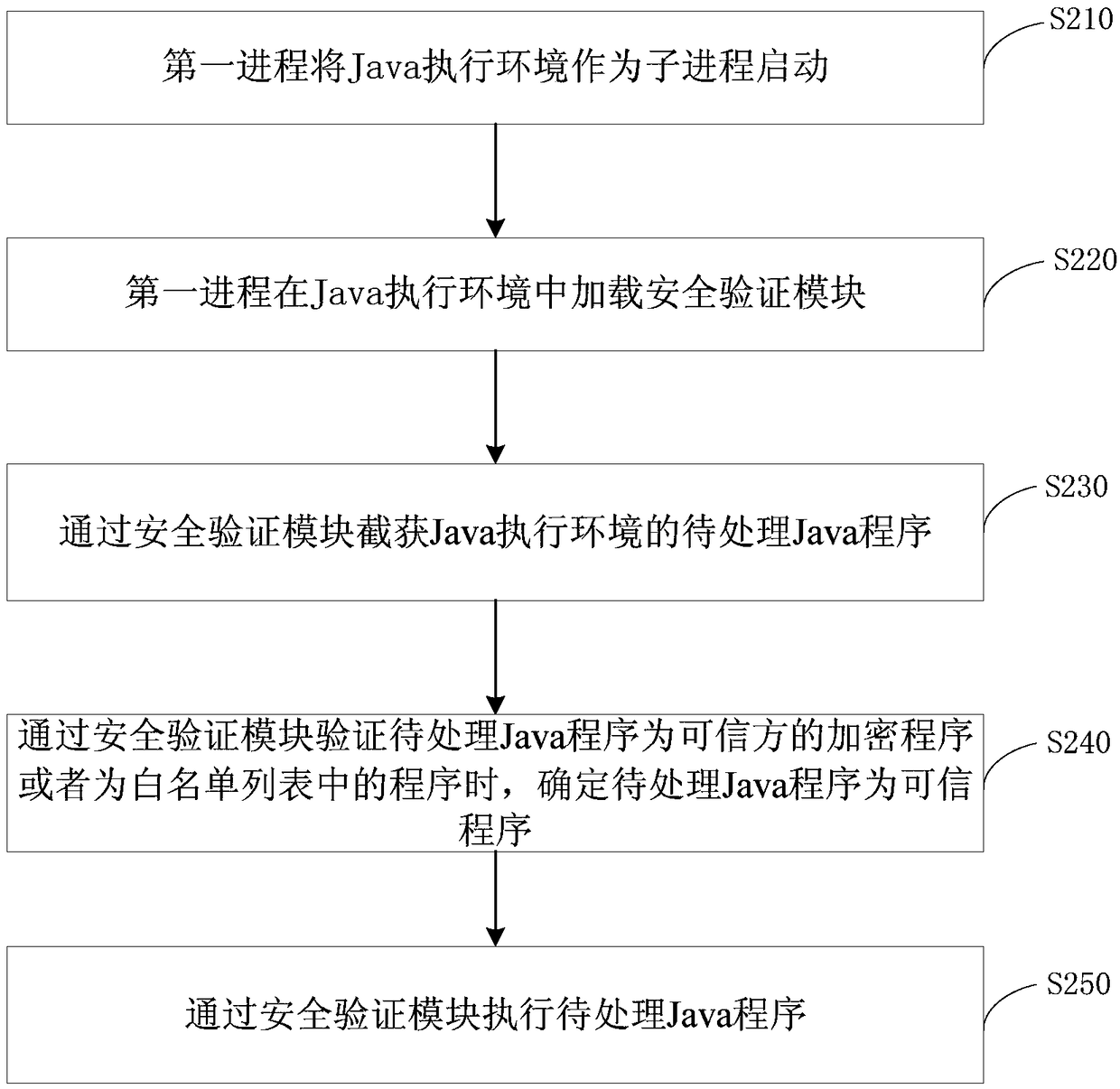
[0035] figure 2 It is a flow chart of a Java program execution method provided by Embodiment 2 of the present invention. On the basis of the optional implementation modes of the above-mentioned embodiments, this embodiment will "verify the intercepted Java program through the security verification module as a valid Trusted program" is optimized to "determine that the Java program to be processed is a trusted program when the security verification module verifies that the Java program to be processed is an encrypted program of a trusted party or is a program in the white list". Such as figure 2 As shown, it specifically includes the following steps:
[0036] S210. The first process starts the Java execution environment as a child process.
[0037] S220. The first process loads the security verification module in the Java execution environment.
[0038] S230. Intercept the Java program to be processed in the Java execution environment through the security verification modul...
Embodiment 3
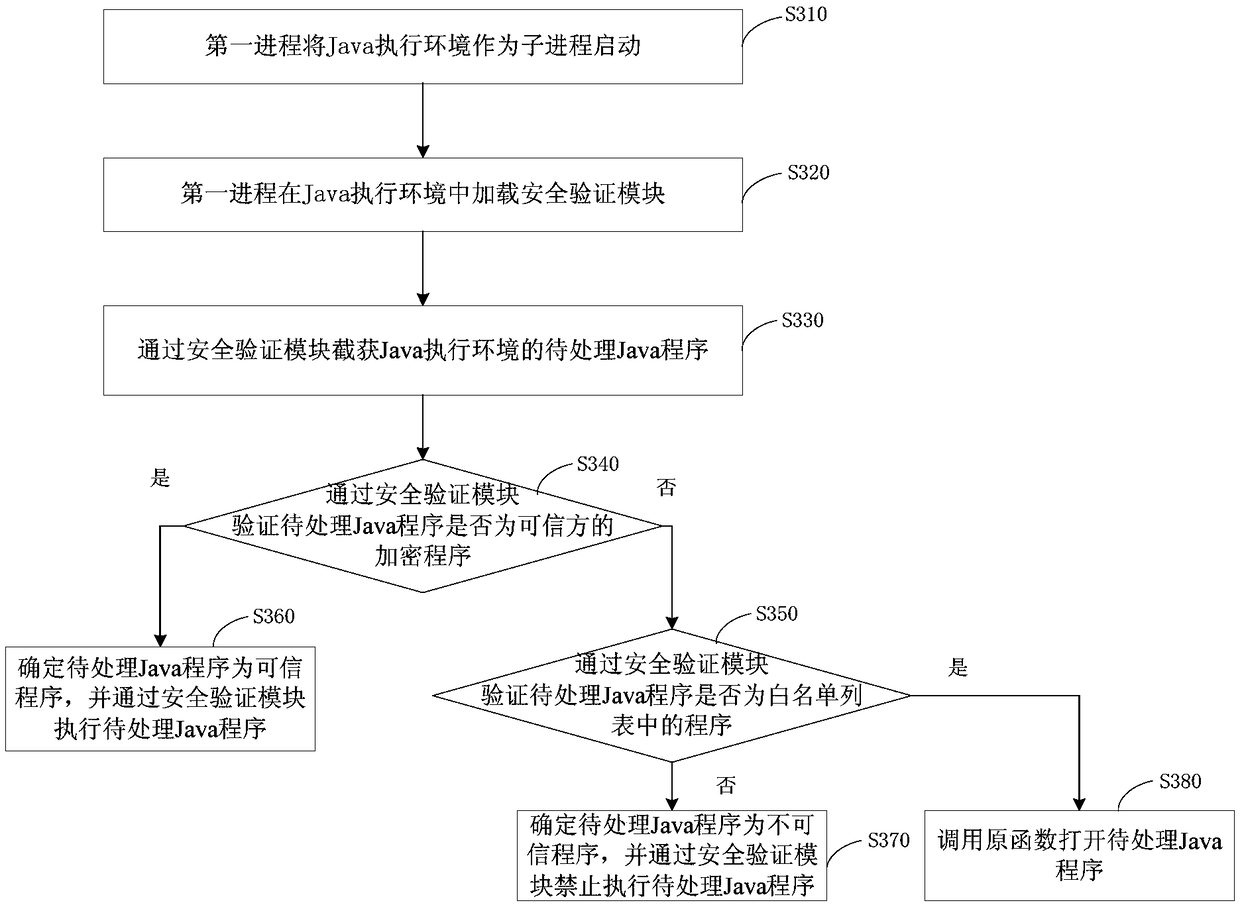
[0052] image 3 It is a flow chart of a Java program execution method provided by Embodiment 3 of the present invention, which is further optimized on the basis of each optional implementation mode of the above-mentioned embodiments, and specifically "verifies and intercepts the Java program to be processed through the security verification module as Trusted program is "optimized to" through the security verification module to determine whether the Java program to be processed is an encryption program of a trusted party, and if the Java program to be processed is an encryption program of an untrusted party, verify whether the Java program to be processed is a whitelist program in the program; if it is verified that the Java program to be processed is a program in the whitelist, it is determined that the Java program to be processed is a trusted program". Such as image 3 As shown, it specifically includes the following steps:
[0053] S310. The first process starts the Java ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com