Network security simulation system
A simulation system and network security technology, applied in the field of network security, can solve the problems of limited attack simulation scenarios, single function of attack tools, time-consuming and labor-intensive, etc., to achieve flexible and diverse network adjustment, overcome physical servers, and improve the effect of protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
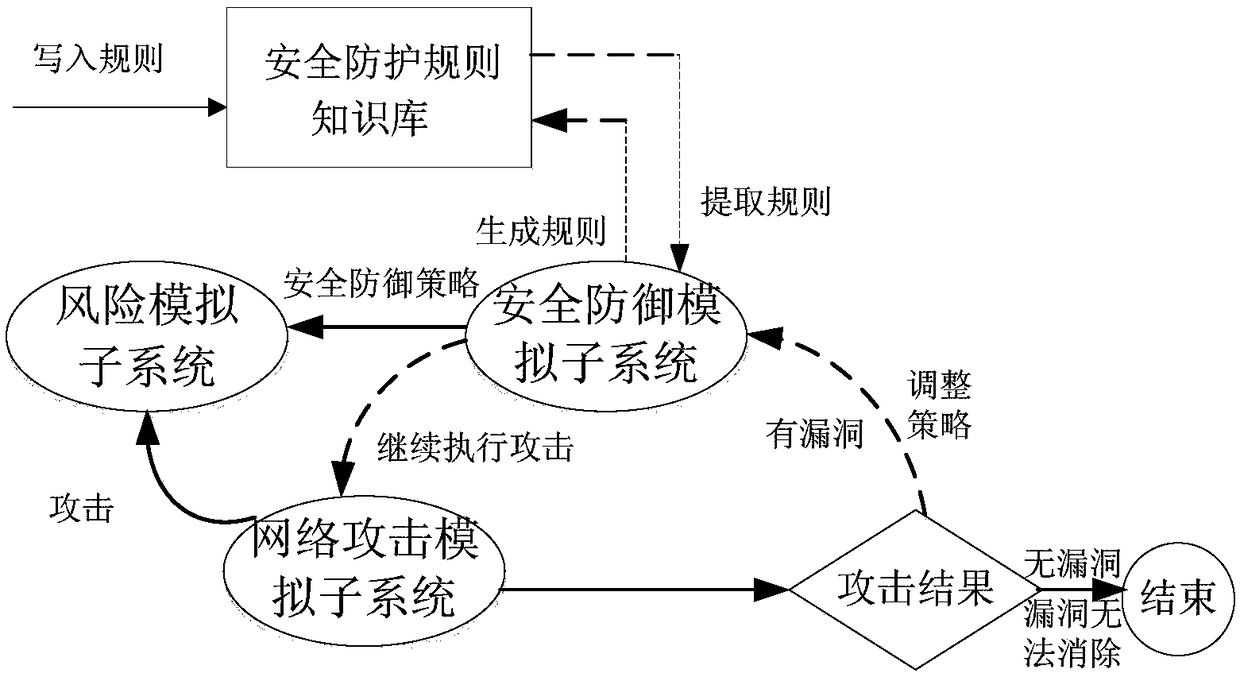
[0036] Such as figure 1 As shown, the present invention proposes a network security simulation system, including a network attack simulation subsystem, a risk simulation subsystem and a security defense simulation subsystem.
[0037] Risk simulation subsystem: Build a risk simulation environment, including network topology and network systems with vulnerabilities (such as various common operating systems, databases, and WEB systems).
[0038] Specific steps are as follows:
[0039] Using virtualization technology, build different types of network system templates with loopholes; design network topology according to the actual network environment; select the corresponding network system template according to the network topology, generate network system nodes, and form a risk simulation environment.
[0040] Network attack simulation subsystem: Provide a variety of attack tools and attack parameters, according to the attack tools and attack parameters selected by the user, rea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com