A fuzzy searching method for encrypted images
A technology of encrypting images and fuzzy search, applied in the Internet field, can solve problems such as key management difficulties, deviations between input and target information, and unclear data owners
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] In order to better explain the present invention and facilitate understanding, the present invention will be described in detail below with reference to the accompanying drawings and through specific embodiments.
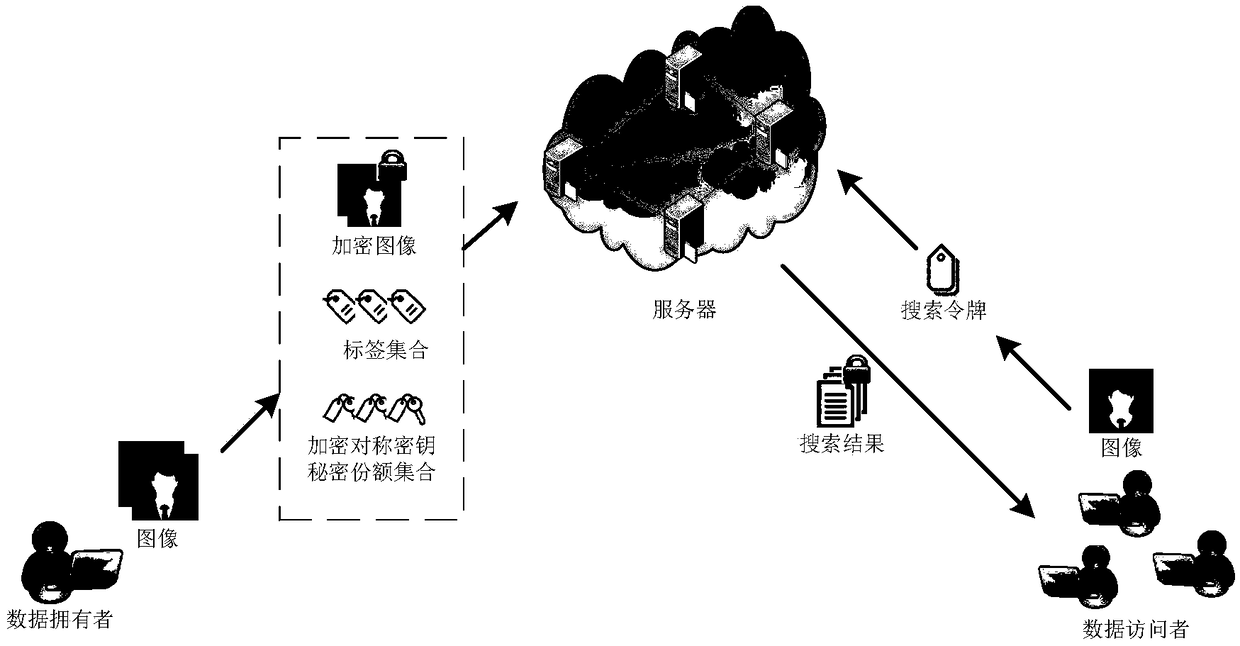
[0068] The architecture of the fuzzy search method for encrypted images of this embodiment is as follows: figure 1 As shown, the method contains three types of entities. One is the data owner (the owner of the image data), the second is the cloud server (responsible for storing encrypted data and building a secure index), and the third is the data visitor (the data owner can also be the data visitor). From figure 1 It can be seen that the data visitor first processes the original image, obtains the encrypted image, the label set and the encrypted symmetric key secret share set and uploads it to the cloud server, and then the cloud server stores it and builds a secure index. When a visitor makes a query, a search token must be constructed using the search image...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com