A method and system for identifying abnormal transactions based on a fund transaction network
A transaction network and abnormal transaction technology, applied in the fields of finance, data processing applications, instruments, etc., can solve the problems of small help in money laundering investigation work, inability to accurately and comprehensively detect abnormal transactions, etc., and achieve the effect of reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
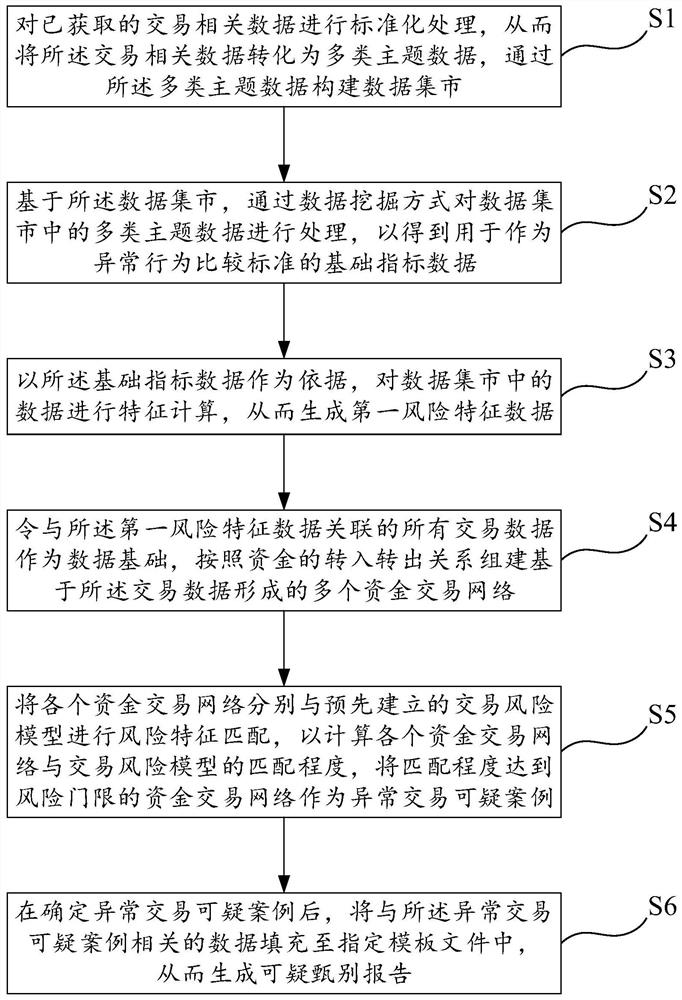
[0064] This embodiment discloses a method for identifying abnormal transactions based on a capital transaction network. The identification of abnormal transactions (including money laundering risks) in the present invention is based on bank customer data, account data, and various transaction records, such as figure 1 As shown, the abnormal transaction identification method includes the following steps.
[0065] Step S1, obtain the bank's transaction-related data, and standardize the acquired transaction-related data, so as to convert the transaction-related data into multiple types of subject data, such as converting the data of the credit system, the national knot system, and the core system into the same subject Standards, build a data mart through multiple types of subject data, which is used as the basis for identifying abnormal transactions; in this embodiment, multiple types of subject data include customer subject data, account subject data, and transaction subject data...
Embodiment 2
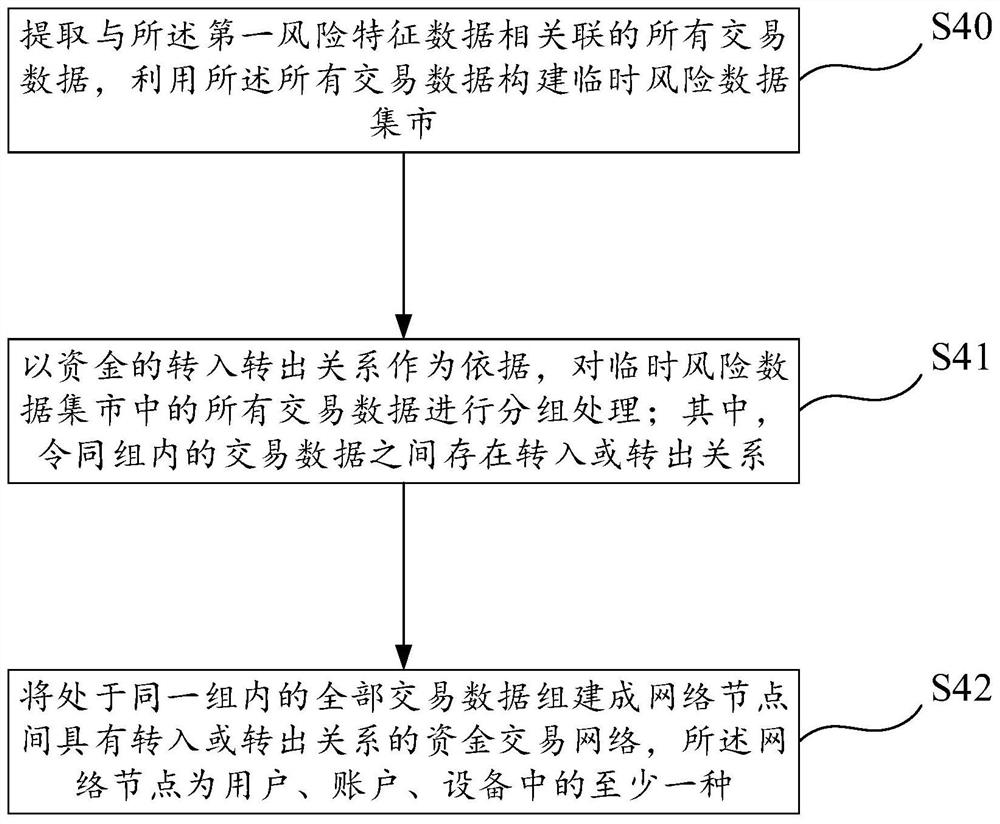
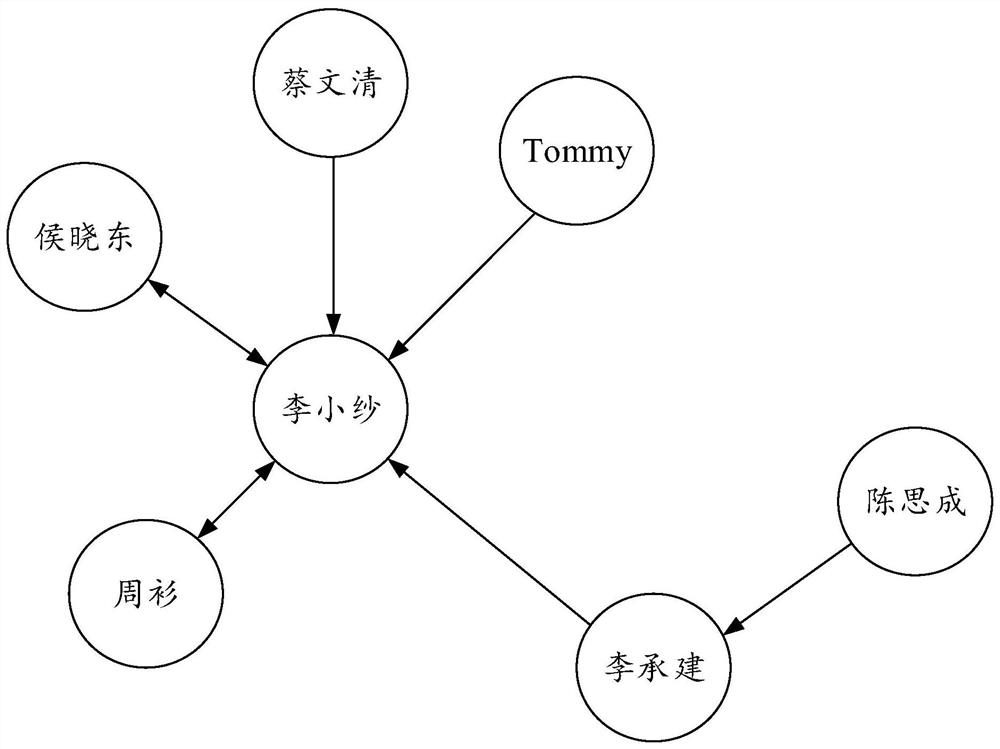
[0082] Such as Figure 5 As shown, based on the same inventive concept as Embodiment 1, this embodiment provides an abnormal transaction identification system based on a capital transaction network for implementing the abnormal transaction identification method of Embodiment 1. The abnormal transaction identification system includes: data The market construction module, basic index mining module, risk feature generation module, transaction network construction module, suspicious case generation module, screening report generation module and risk model establishment module are described in detail in this embodiment as follows.
[0083] The data mart building module is used to standardize the acquired transaction-related data, so as to convert the transaction-related data into multi-category subject data, and to construct a data mart through multi-category subject data.
[0084] The basic index mining module is used to process multiple types of subject data in the data mart thro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com