Implicit protection method and system based on multi-sensor data fusion
A data fusion and multi-sensor technology, applied in digital data authentication, electronic digital data processing, instruments, etc., can solve the problems of stealing user account privacy information, limited scope of application, peeping of lock screen passwords, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
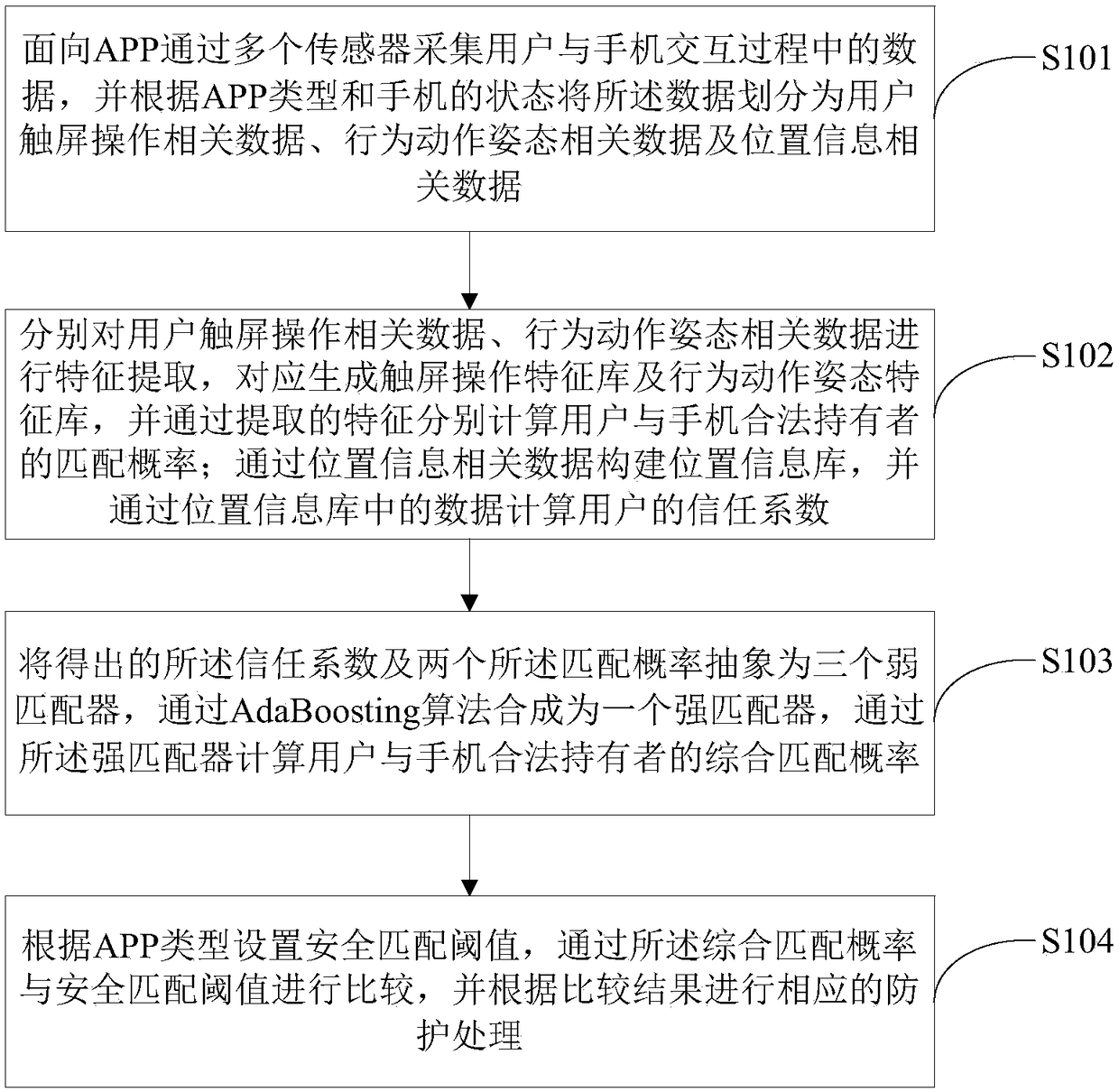
[0086] Such as figure 1 As shown, a kind of implicit protection method based on multi-sensor data fusion of the present invention includes:
[0087] Step S101: collect data during the interaction between the user and the mobile phone through multiple sensors for the APP, and divide the data into data related to the user's touch screen operation, data related to behavior, action and posture, and data related to location information according to the type of APP and the state of the mobile phone ;include:
[0088] 1) Get sensor data
[0089] There are many sensors in modern mobile phones, and their sensitivity is constantly improving. When a user usually uses a mobile phone, a large amount of sensor data will be generated, which can directly or indirectly reflect the user's behavioral characteristics. Utilize this feature to collect sensor data from the interaction between the mobile phone and the user to realize the identification of the user's identity. The main sensors use...
Embodiment 2
[0274] Such as Figure 15 As shown, a kind of implicit protection system based on multi-sensor data fusion of the present invention comprises:
[0275] The data collection and division module is used to collect data during the interaction between the user and the mobile phone through multiple sensors facing the APP, and divide the data into data related to the user's touch screen operation, data related to behavior, action and gesture, and data according to the type of APP and the state of the mobile phone. Data related to location information;
[0276] The matching probability and trust coefficient generation module extracts the features of the user's touch-screen operation-related data and behavior-action-gesture-related data, correspondingly generates a touch-screen operation feature library and a behavior, action, and gesture feature library, and calculates the user and mobile phone information based on the extracted features. The matching probability of legal holders; co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com