Logging records of traffic in computer network
A computer program, computer system technology, applied in the direction of computer security devices, computing, data exchange networks, etc., can solve problems such as inability to take, no intrusion detected, unclear computer network security, compromised computer network, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
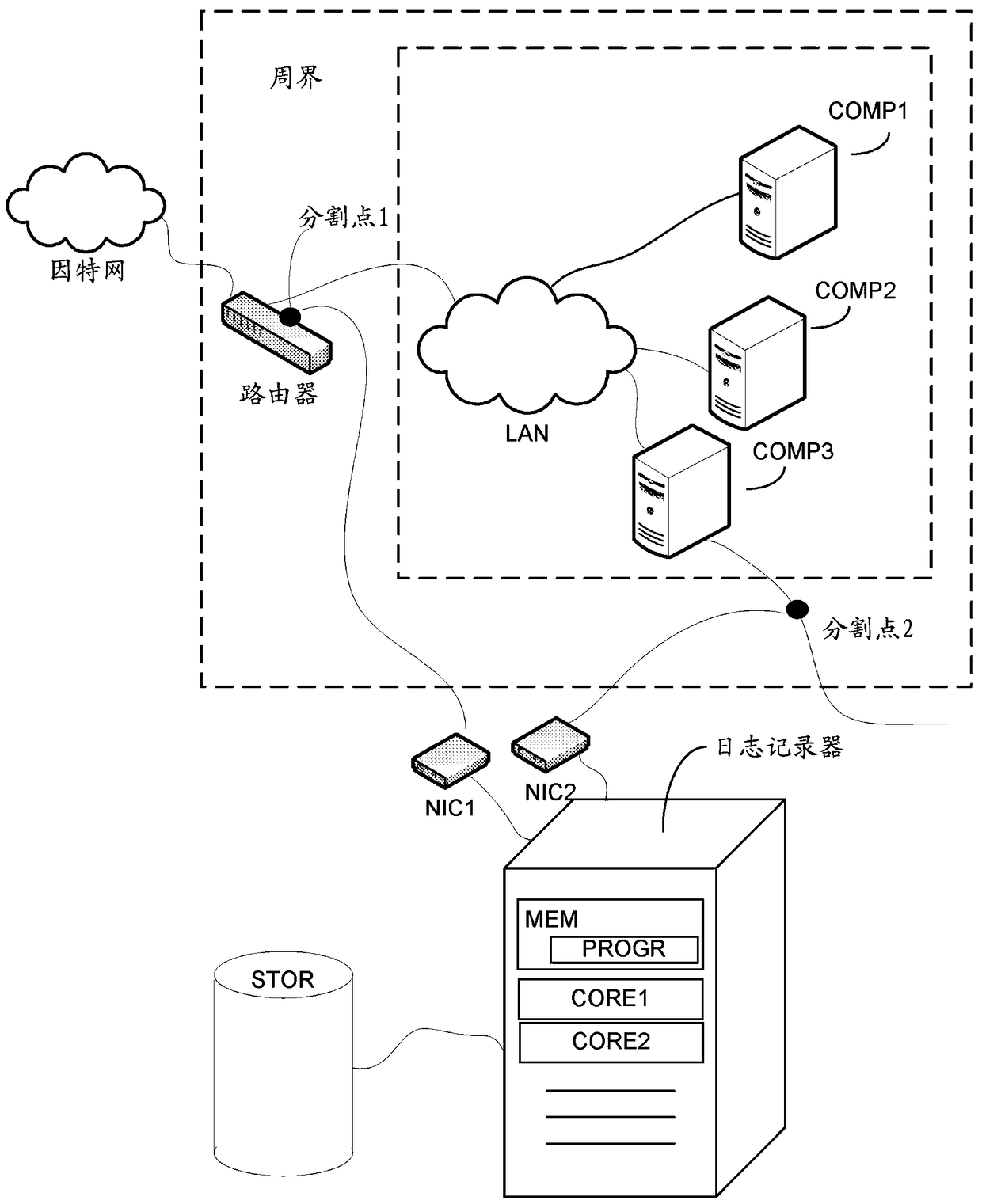
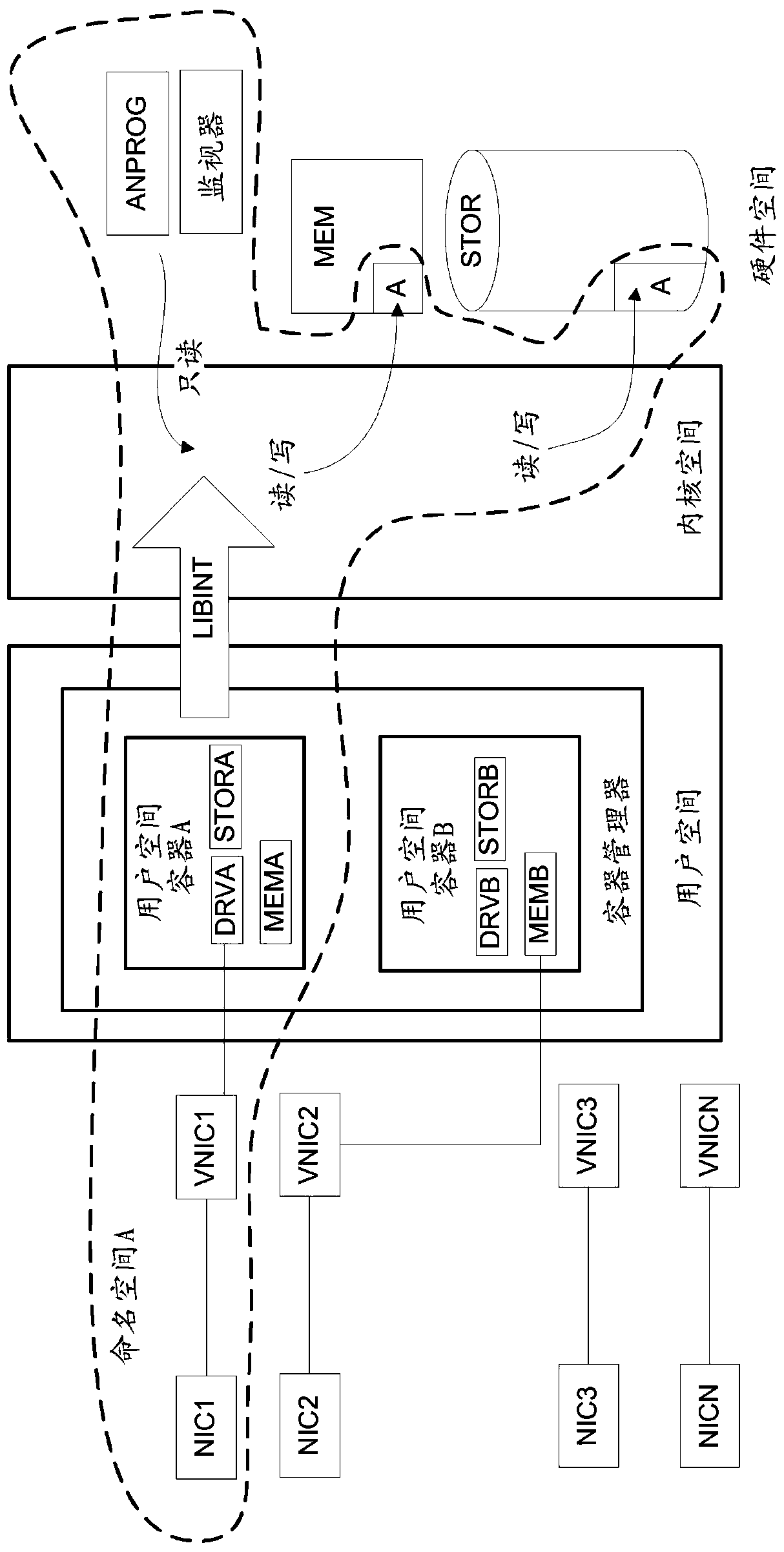
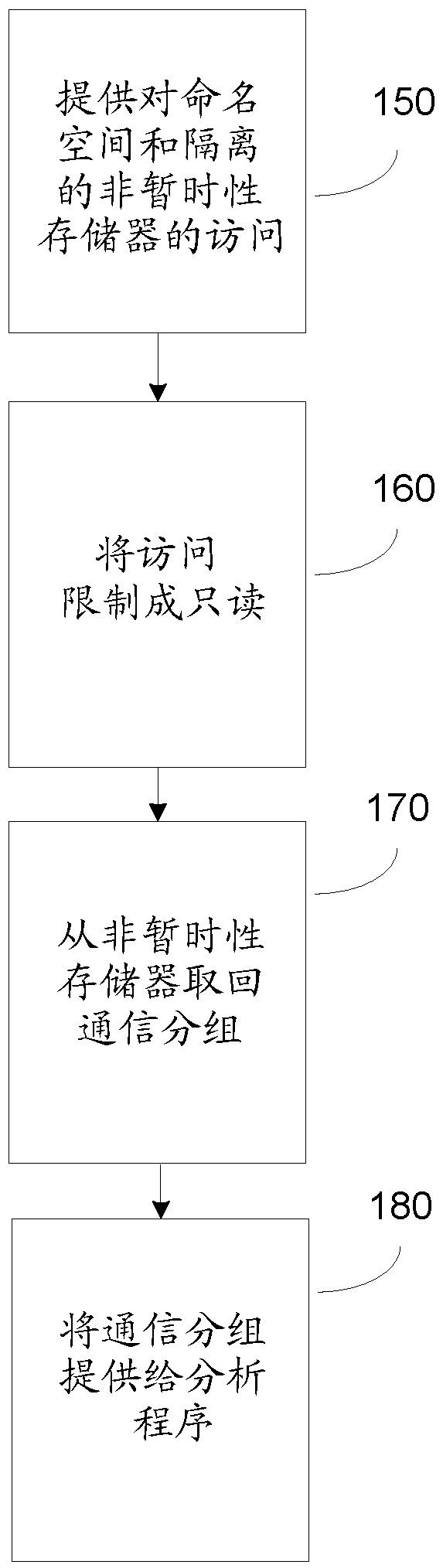
[0015] In the following, several embodiments of the invention will be described in the context of example computer hardware arrangements and example computer hardware elements. Note, however, that the invention is not limited to any particular hardware or software. The different embodiments have application in virtually any environment where logging of computer network traffic is required, and they may be implemented with different hardware and software arrangements. For example, the examples given in this specification can be combined into any working combination for logging and analyzing computer network traffic.
[0016] In packet data networks, data is transmitted in finite-length packets containing an envelope and a payload. Identifiers such as sender and receiver are provided in the packet, along with some information that usually describes the payload. In a layered network model, data is encapsulated into packets on several layers. For example, inside a layer 2 packe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com