Electronic separation wall method, device and system for protecting network space security
A technology of cyberspace, wall, applied in the field of computer network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
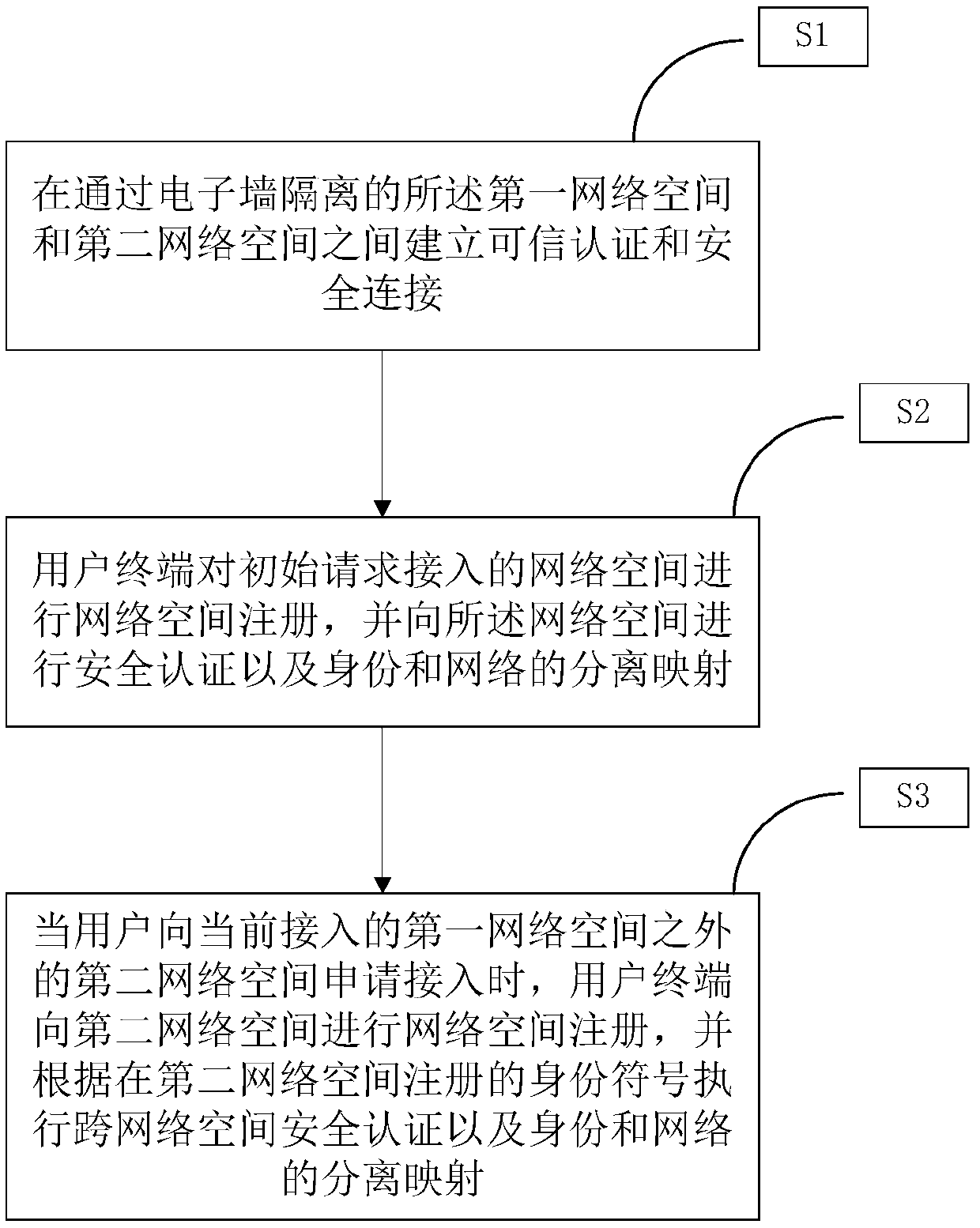
[0069] figure 1 It is a flow chart of an electronic separation wall method for protecting cyberspace security in Embodiment 1 of the present invention, including:
[0070] S1 establishes a trusted authentication and secure connection between the first cyberspace and the second cyberspace separated by the electronic wall.
[0071] Establishing a trusted authentication and secure connection between the first cyberspace and the second cyberspace separated by an electronic wall, including:
[0072] The first network space and the second network space respectively notify the other party of information, and both parties verify the received information respectively. After the two parties verify successfully, they respectively save the connection relationship and send it to the mapping server device of their respective network space, and send a negotiation signaling After the signaling negotiation is successful, establish and save the secure virtual dedicated channel, save the mappin...
Embodiment 2
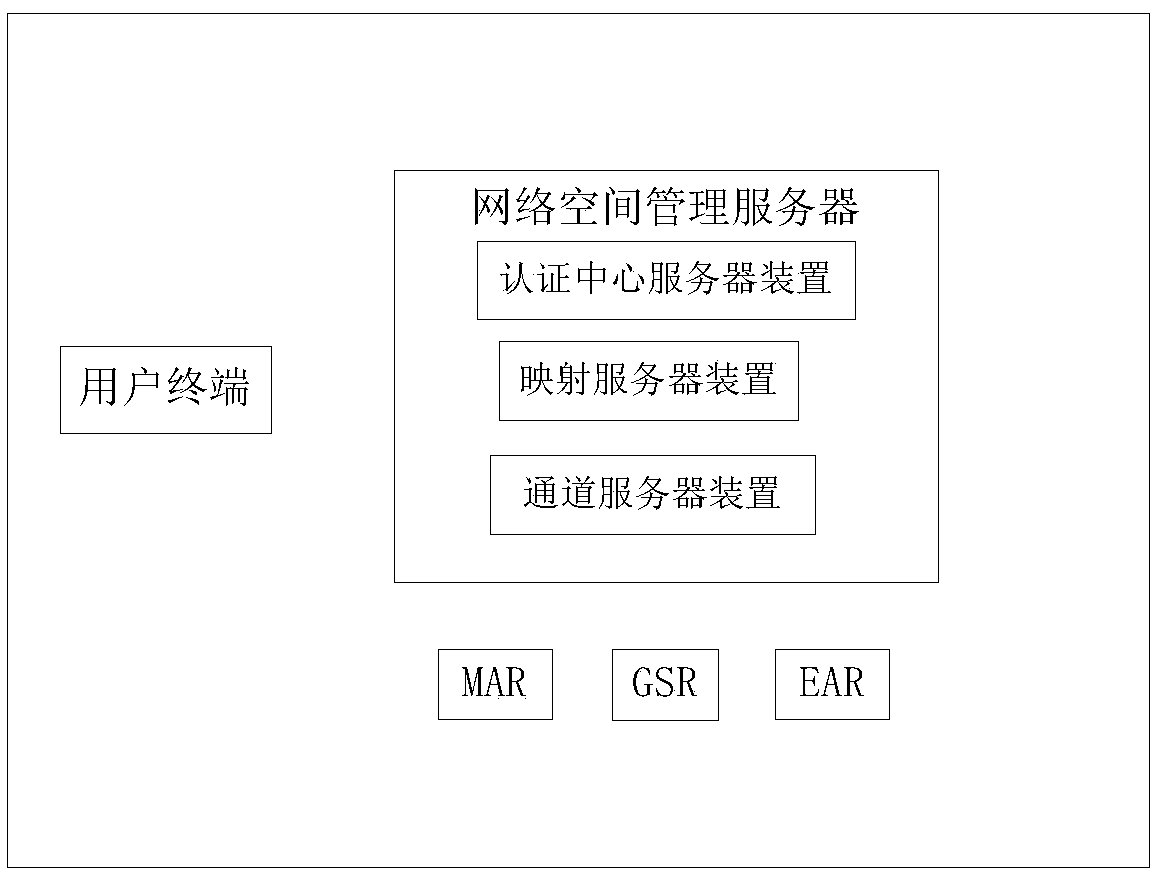
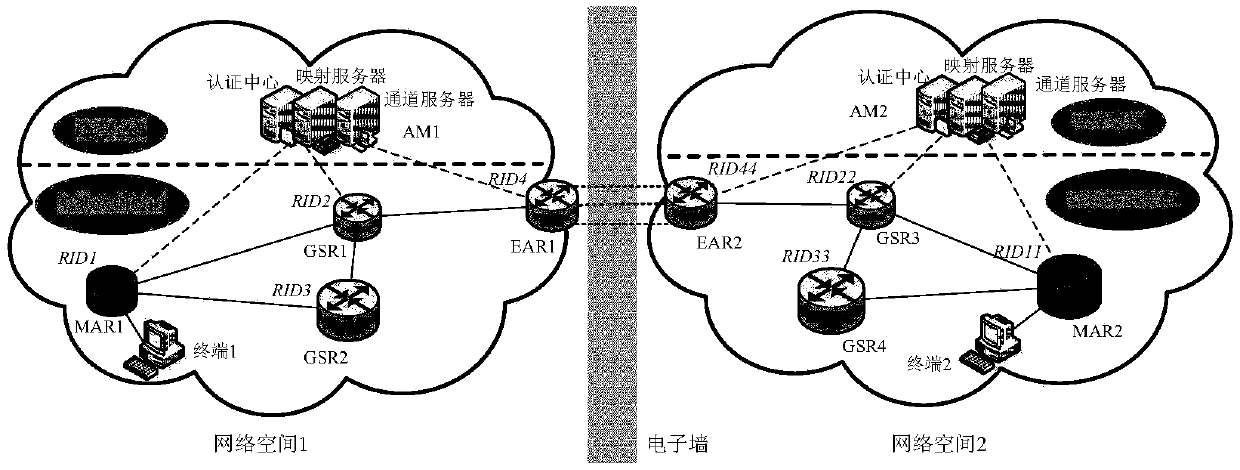
[0122] Embodiment 2 of the present invention provides a user electronic wall isolation method for the future Internet, image 3 It is a schematic diagram of the user electronic wall isolation system of the future Internet of the present embodiment 2, as image 3 As shown, two cyberspaces (cyberspace 1 and cyberspace 2) are separated by an electronic wall. According to the division of the topology diagram in Figure 13, each network space is divided into two layers, the management layer and the switching and routing layer. At the management level, the network space is provided with an authentication center device, a mapping server device and a channel server device, which are collectively referred to as the network space manager AM. At the switching and routing level, the main deployment includes multiple access routers (Multiple Access Router, MAR), generalized switching routers (General Switch Router, GSR), edge access routers (Edge Access Router, EAR) and user terminals and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com