Patents
Literature
50results about How to "Secure identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
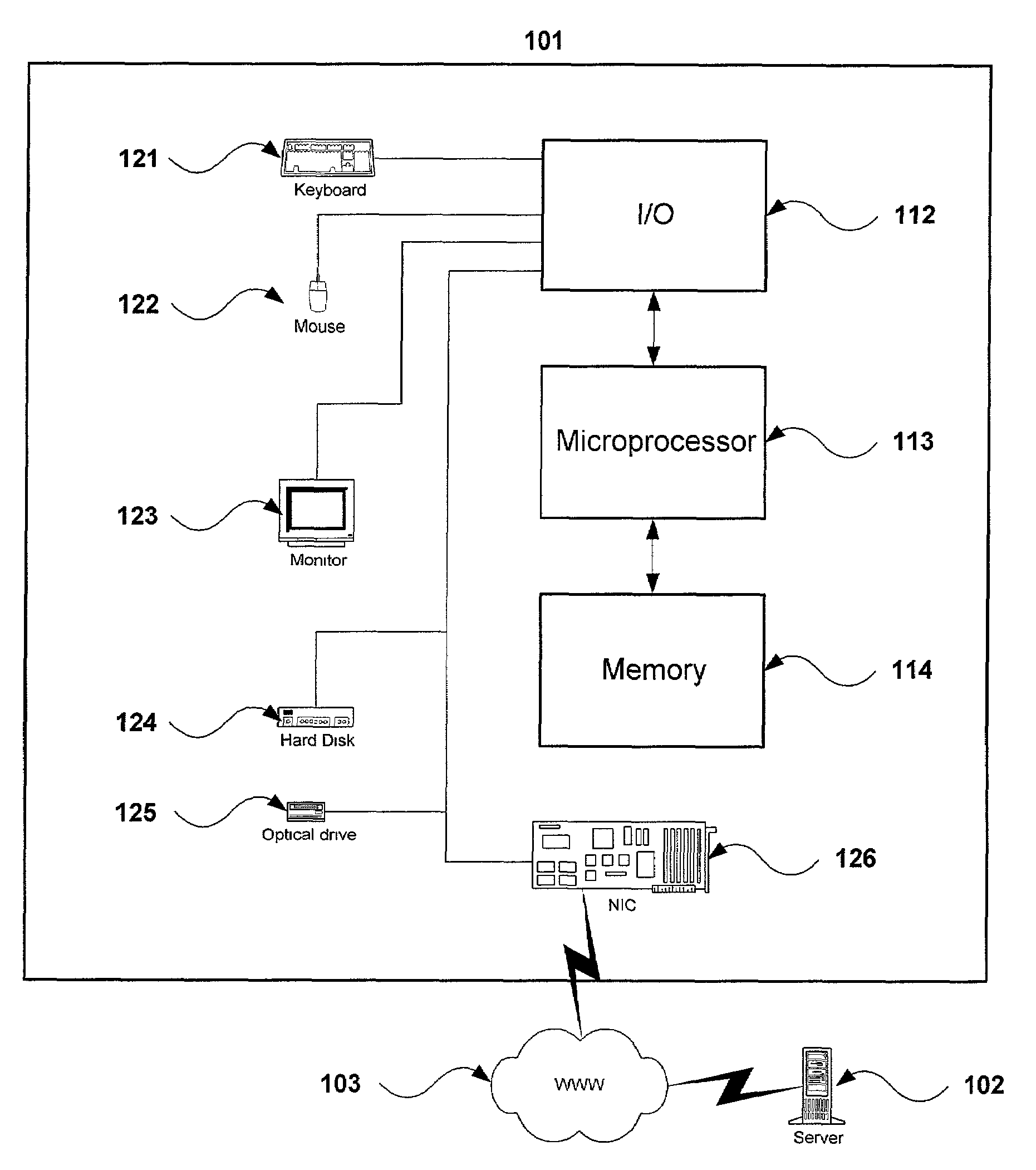
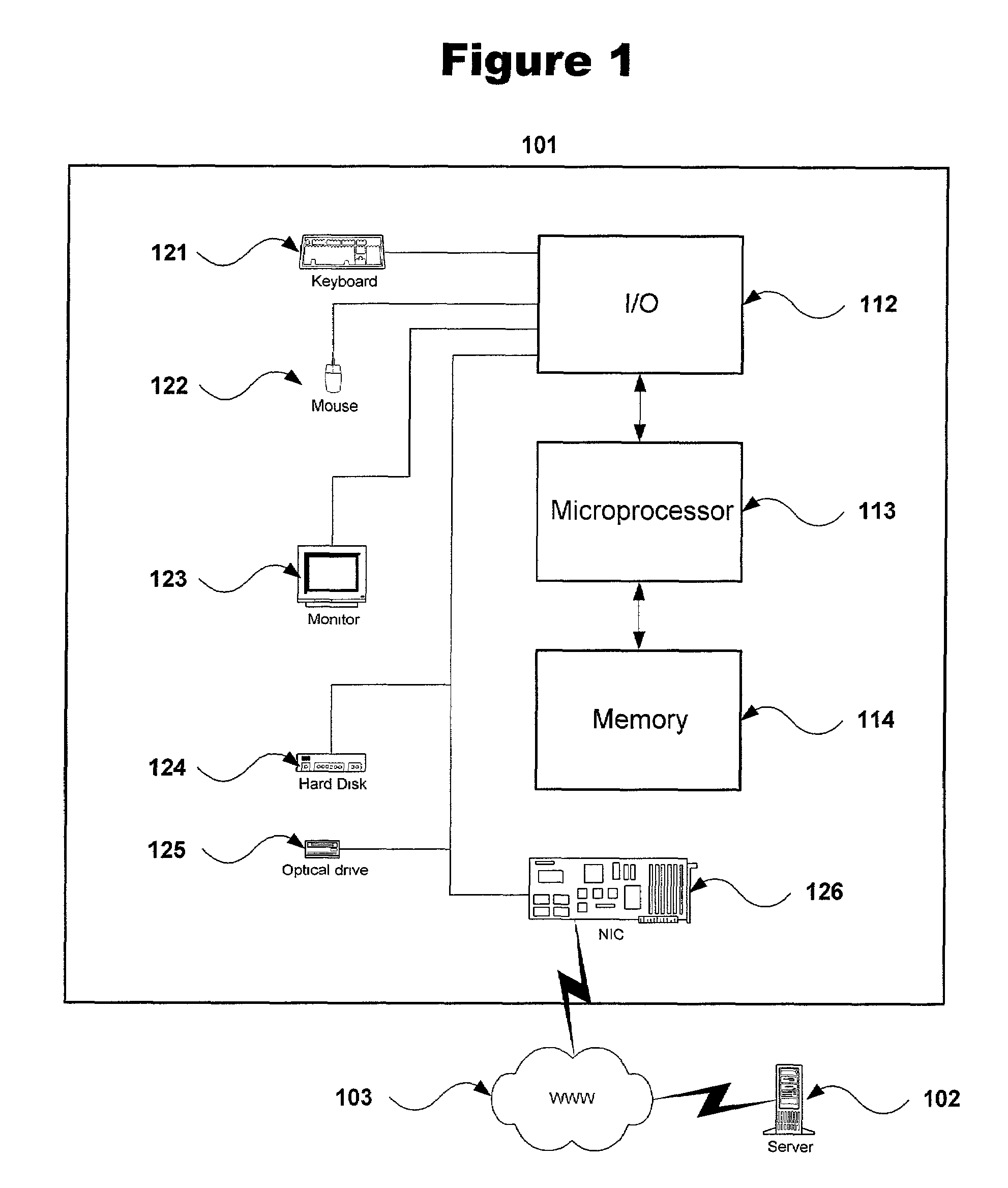
Medical records data security system
InactiveUS6874085B1Secure identityComputer security arrangementsSecuring communicationMedical recordThe Internet
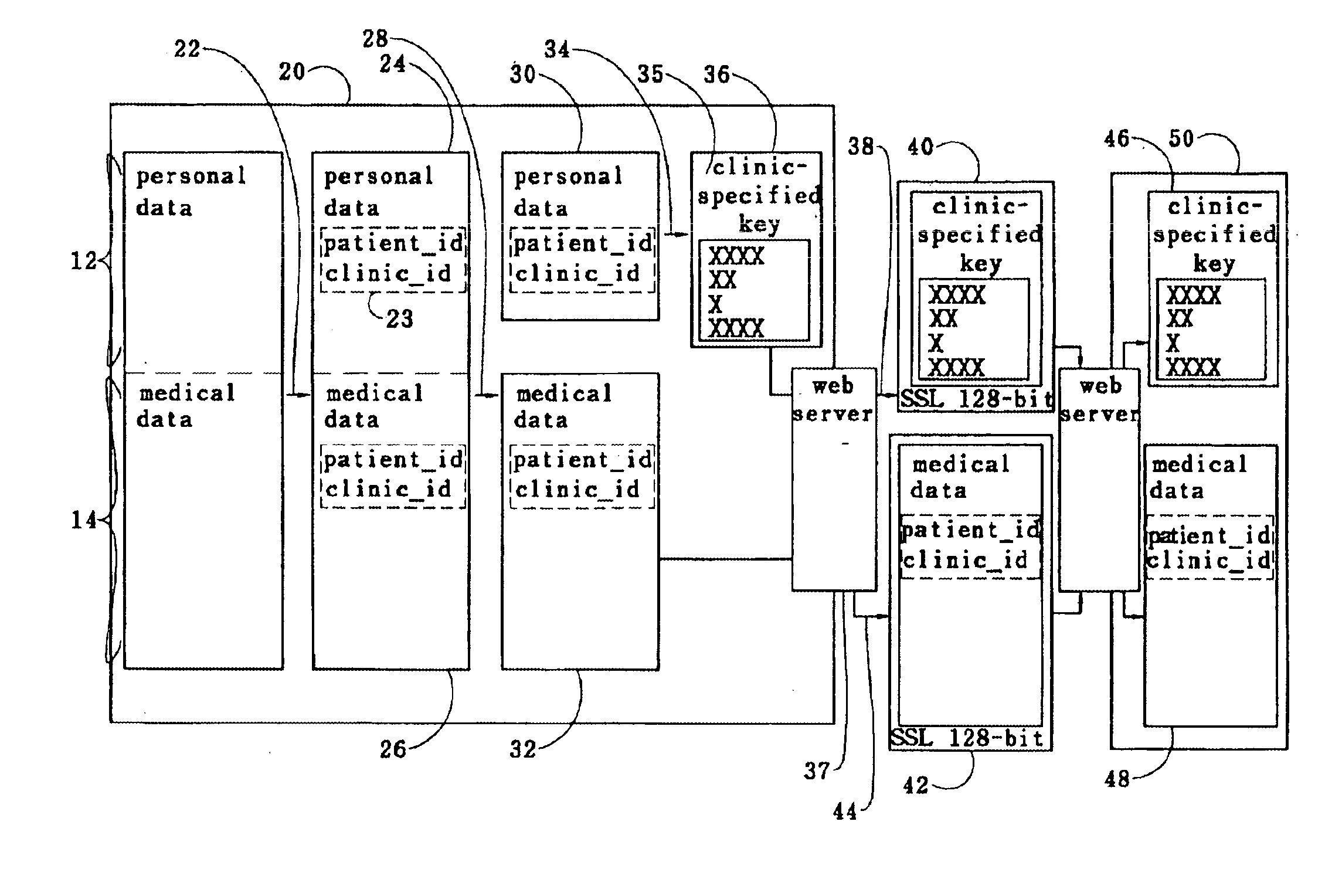
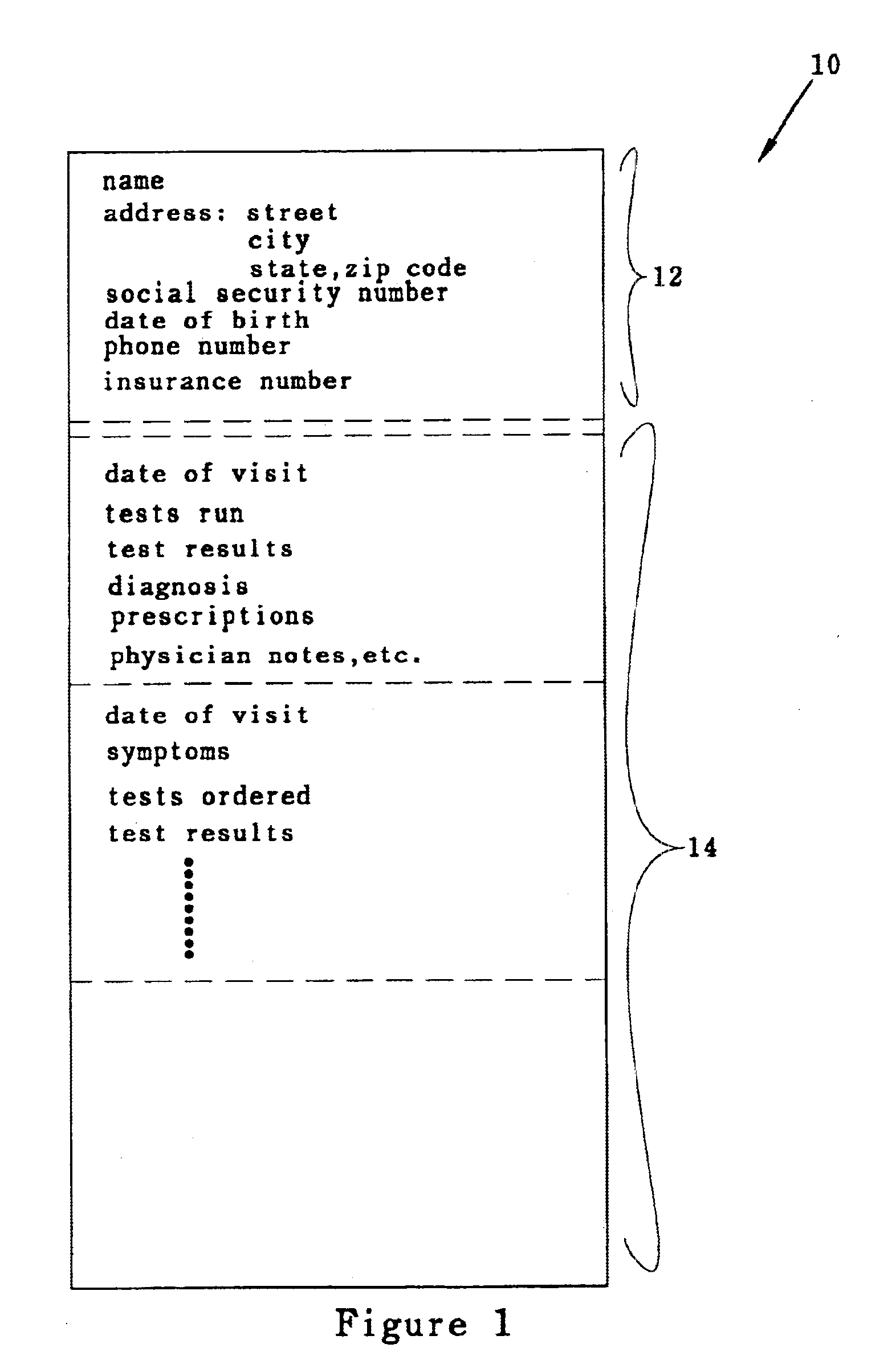
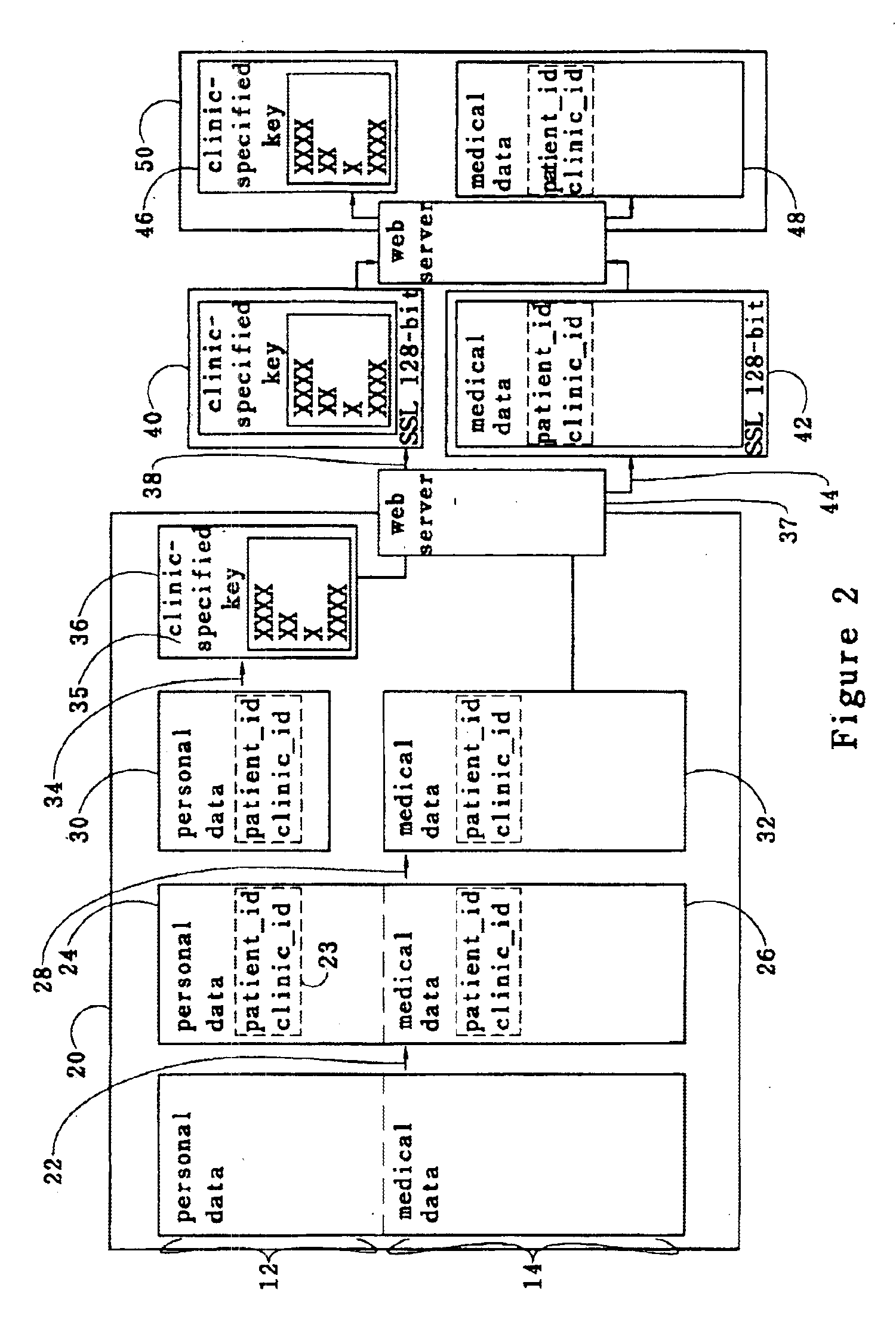
A medical record is partitioned into personal and medical data portions, and an identification code is concatenated into each portion. The personal data portion is encrypted so a patient's identity cannot be linked to the patient's medical data except by authorized viewers. Each portion of the secure medical record can be transferred over a network as separate files, and stored in a data storage system separately. Access to the entire medical record is thereby provided only to those who know the key for the personal data portion of the medical record. The system and method can be used to help ensure patient confidentiality while allowing patient medical records to be accessed over a network such as the Internet, providing physicians and patients quick access to their medical records. The system and method can be used to create a database of anonymous medical records useful for medical research.
Owner:APRIMA MEDICAL SOFTWARE
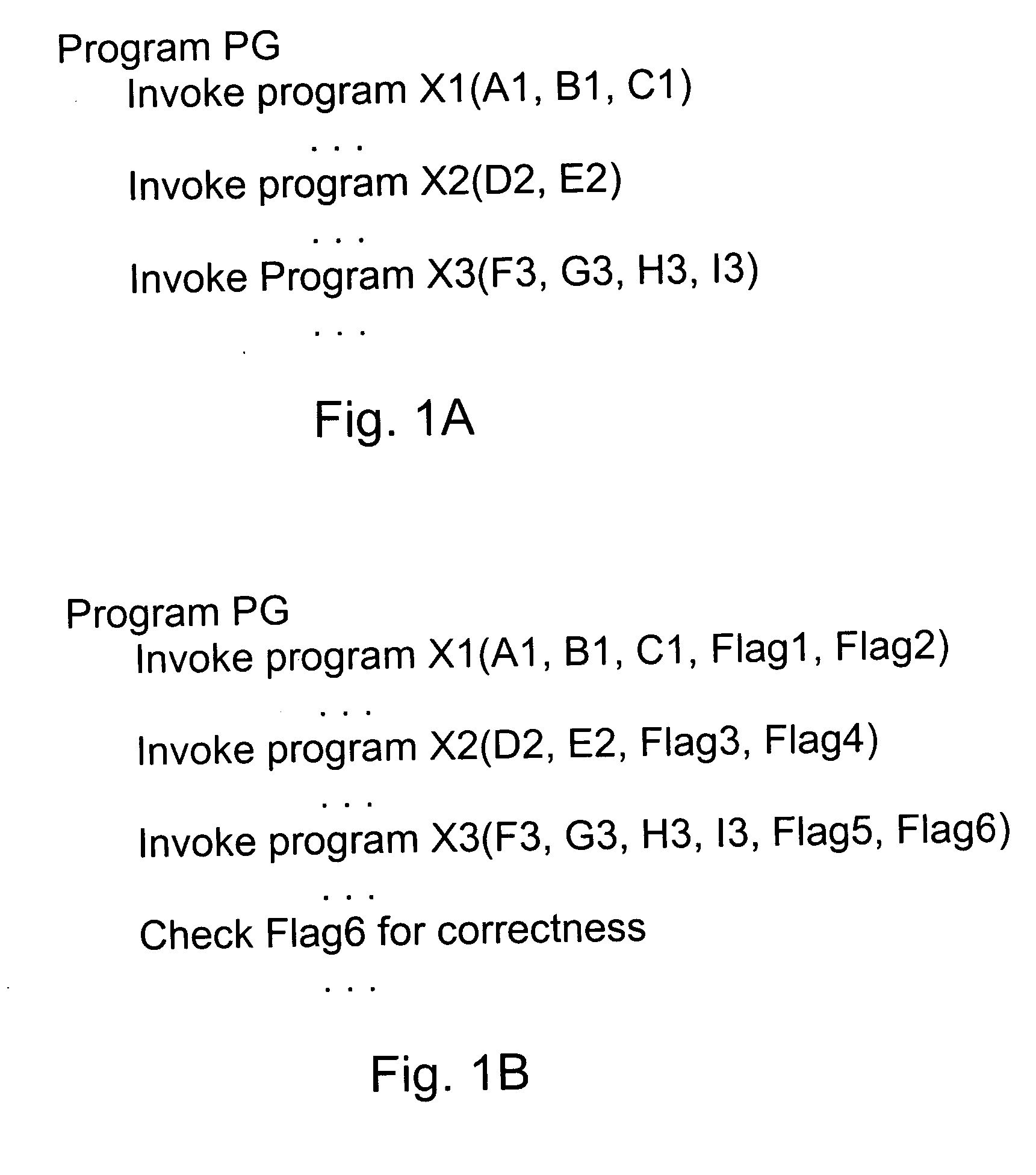
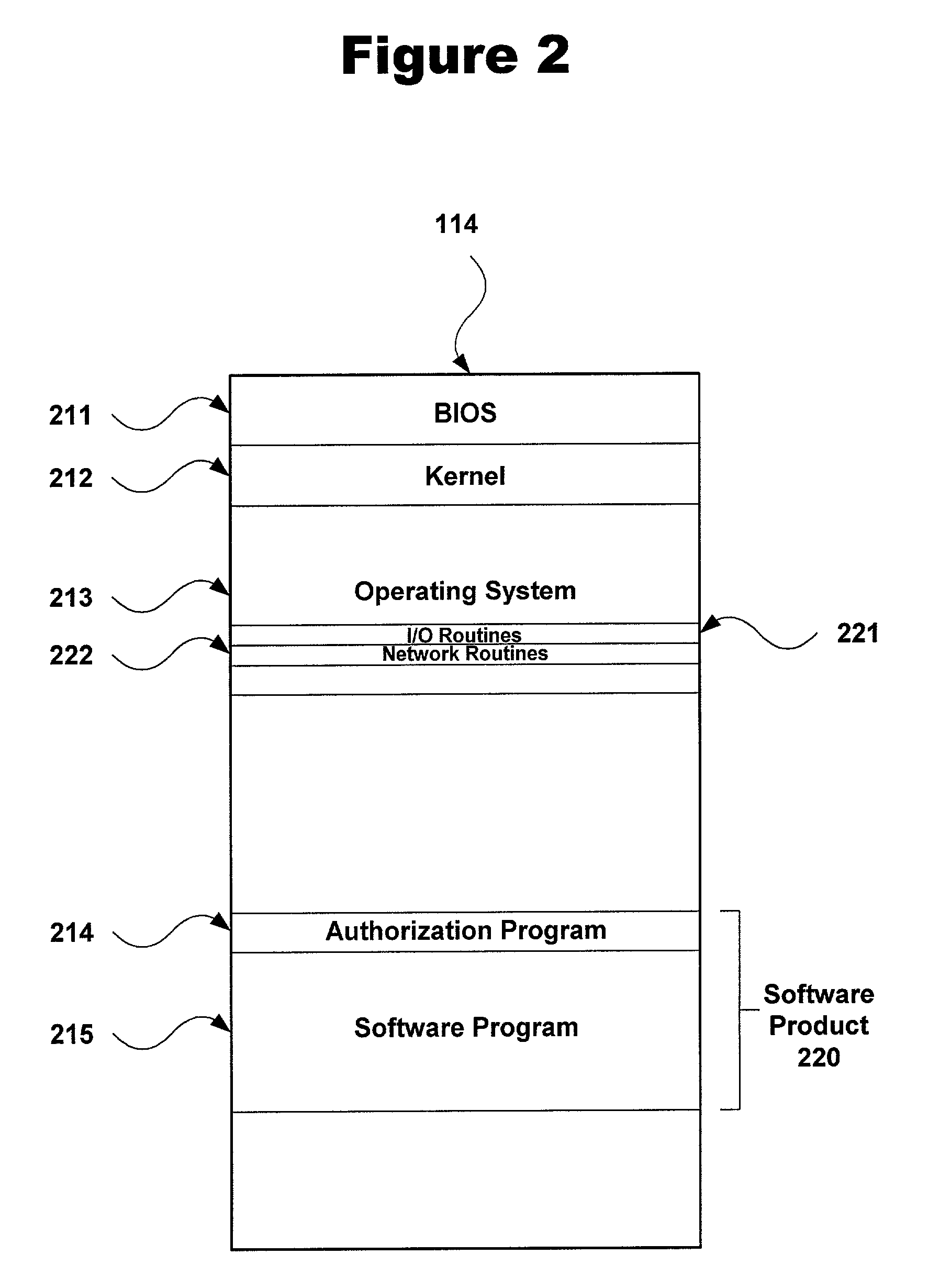
Method and system for fortifying software
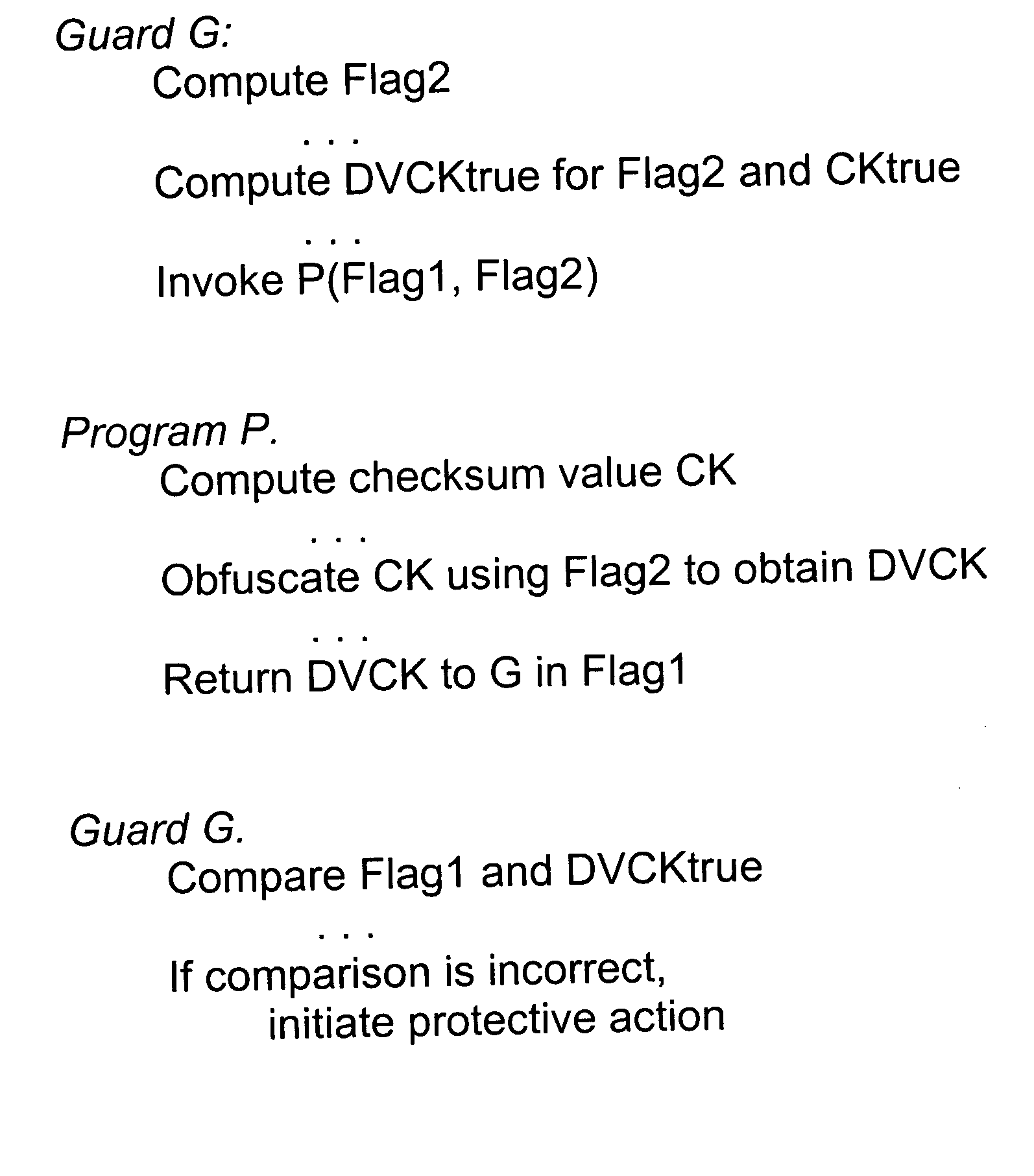
InactiveUS20060101047A1Improve securitySecure identityDigital data processing detailsDigital data protectionMalwareSecurity policy
A method of developing fortified software using external guards, identifying information, security policies and obfuscation. External guards protect protected programs within the fortified software that they are not part of. The external guards can read and check the protected programs directly to detect tampering or can exchange information with the protected programs through arguments of call statements or bulleting boards. External guards can read instructions and check empty space of the protected program before, during or after it executes, and can check for changes in the variables of the protected program when it is not executing, to more effectively detect viruses and other malware. The identification information can be stored in lists or generated dynamically and registered between the relevant programs for identification purposes during execution.
Owner:ARXAN TECHNOLOGIES
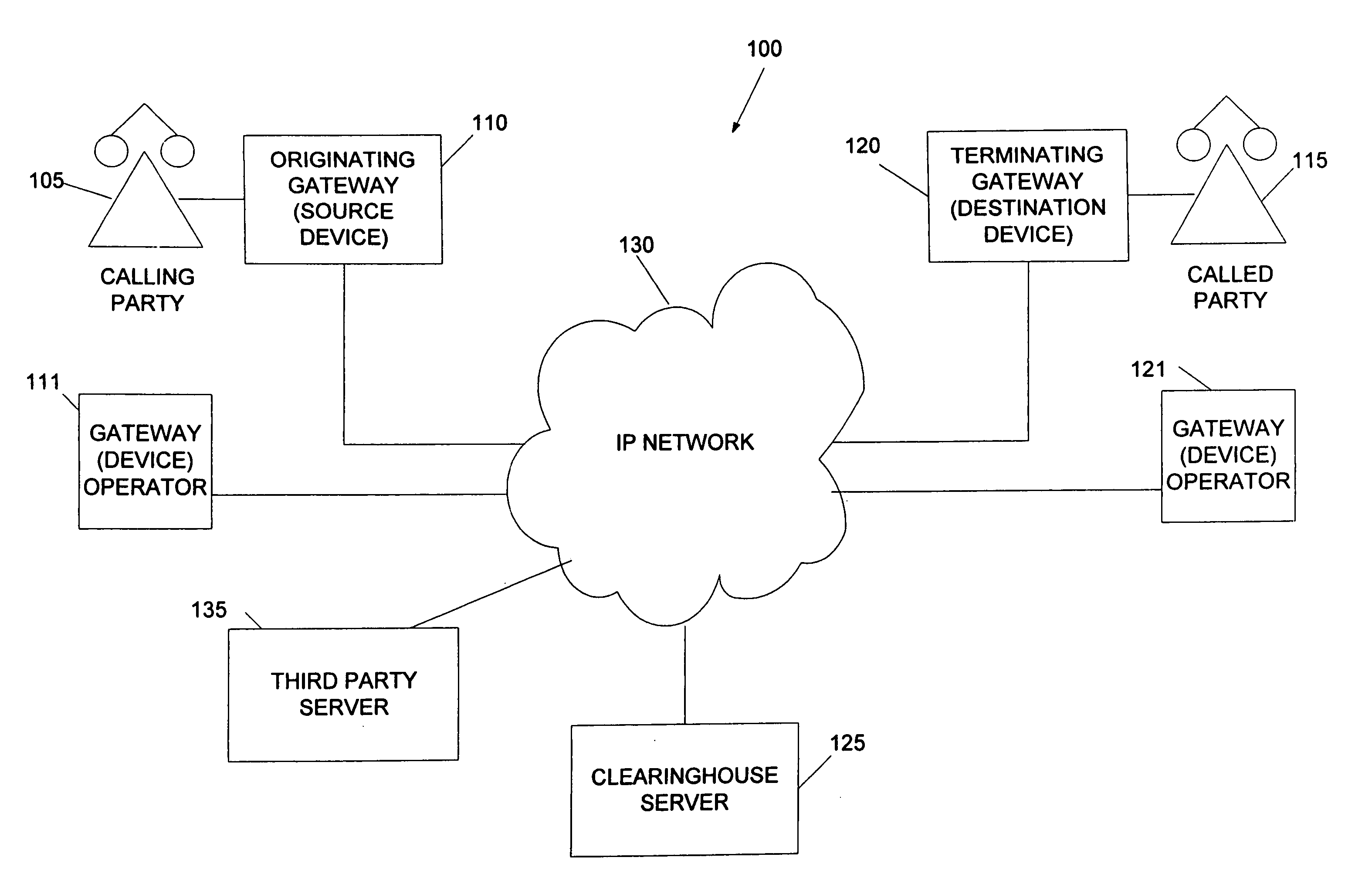
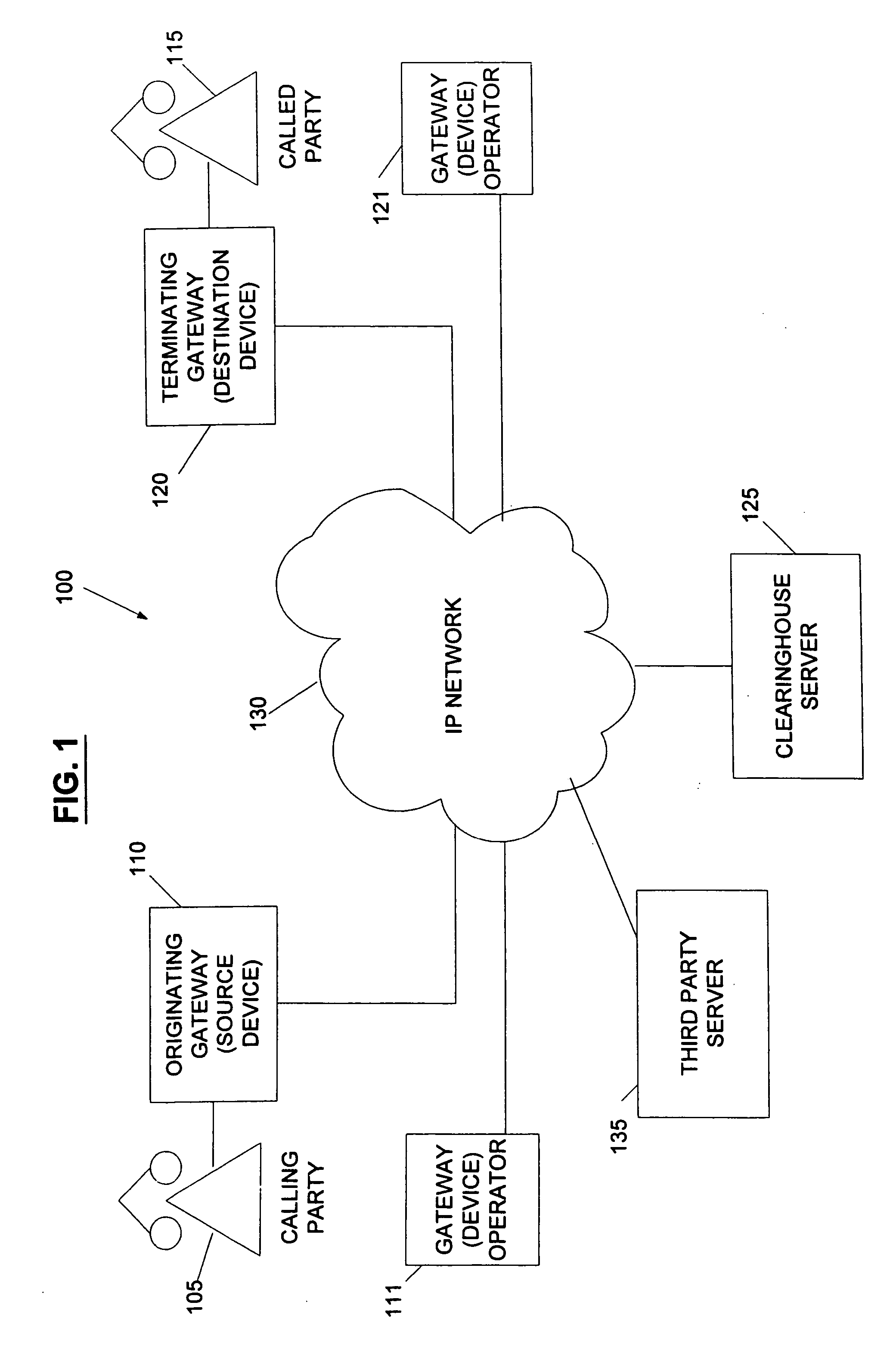
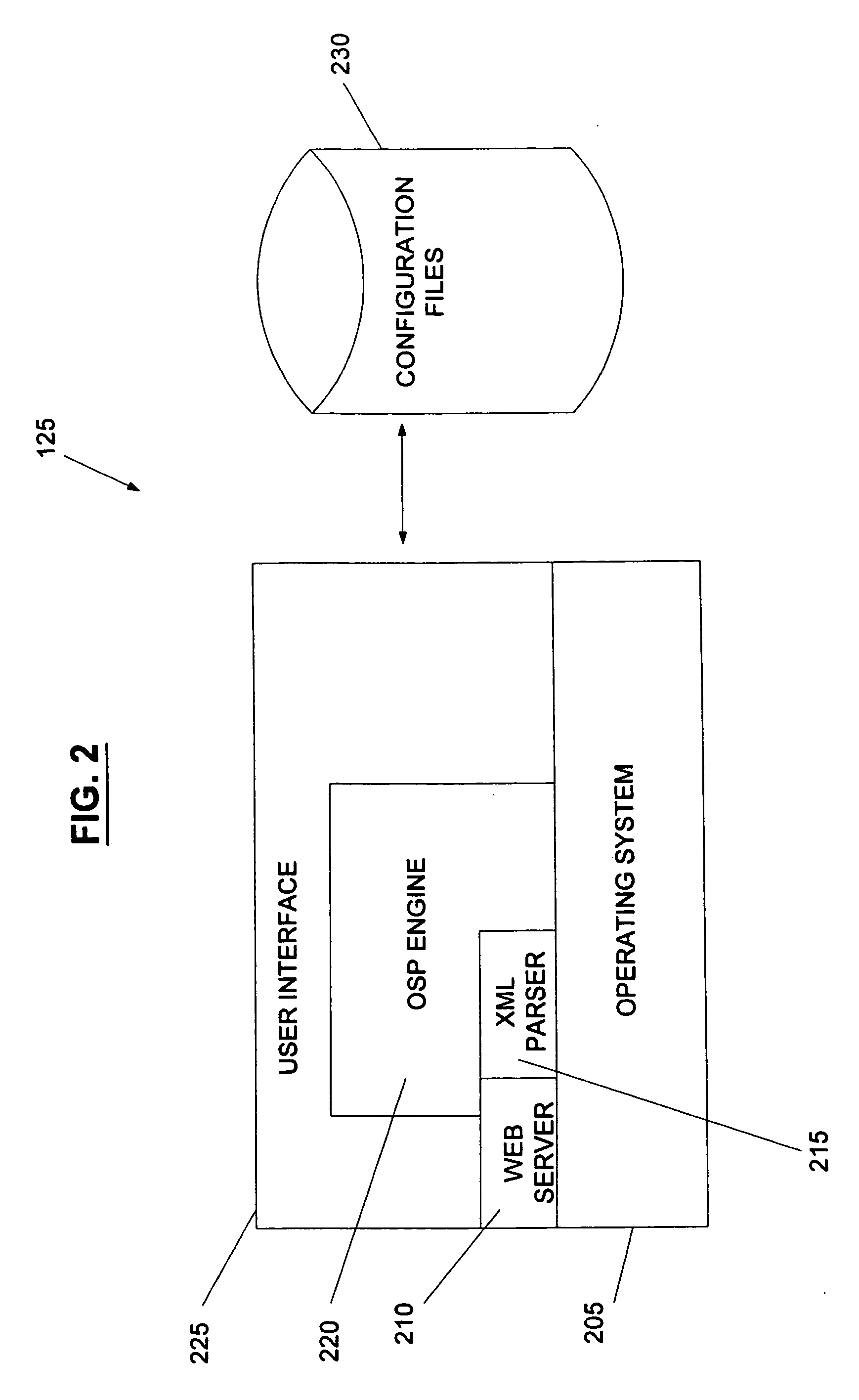
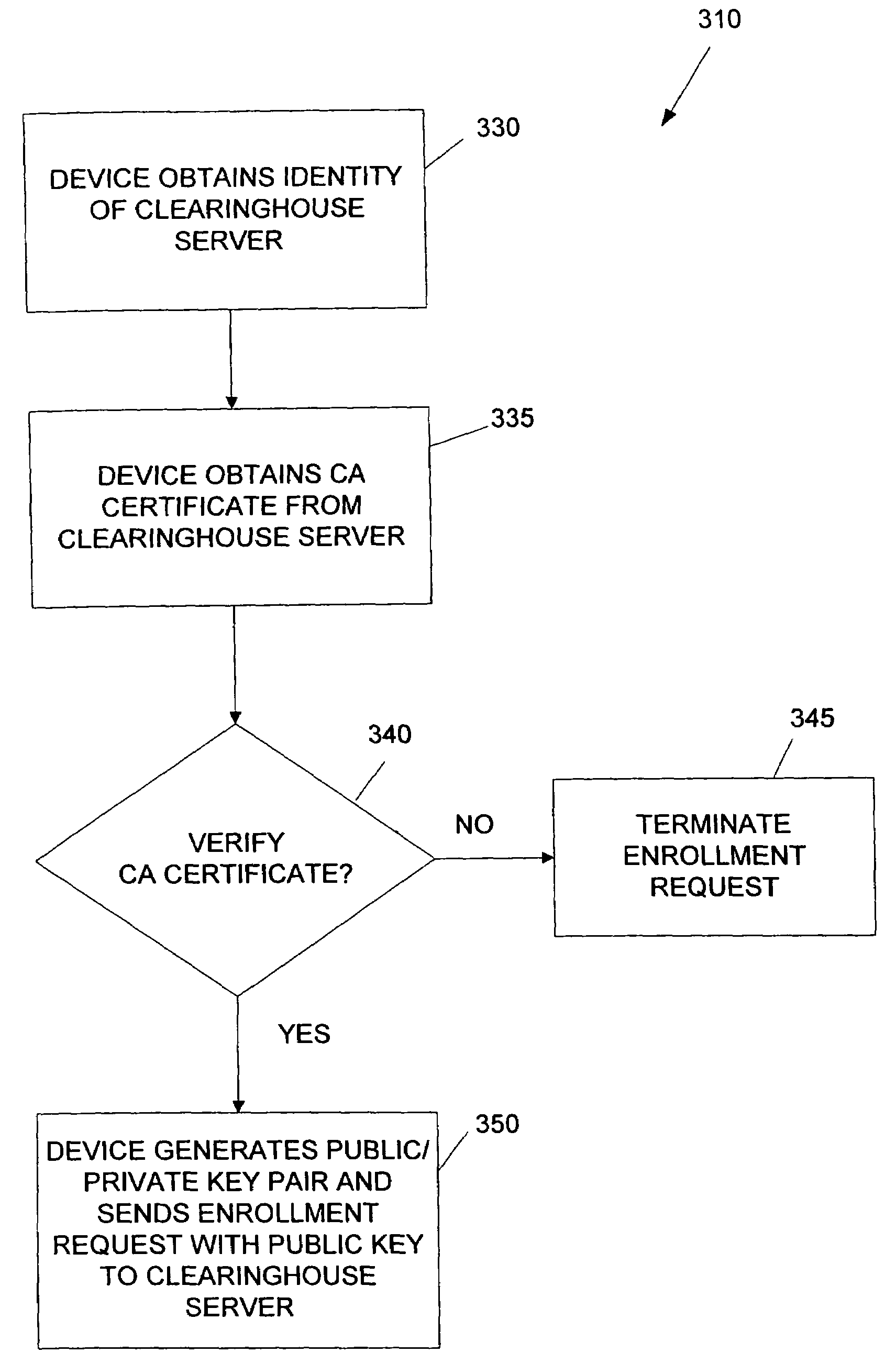
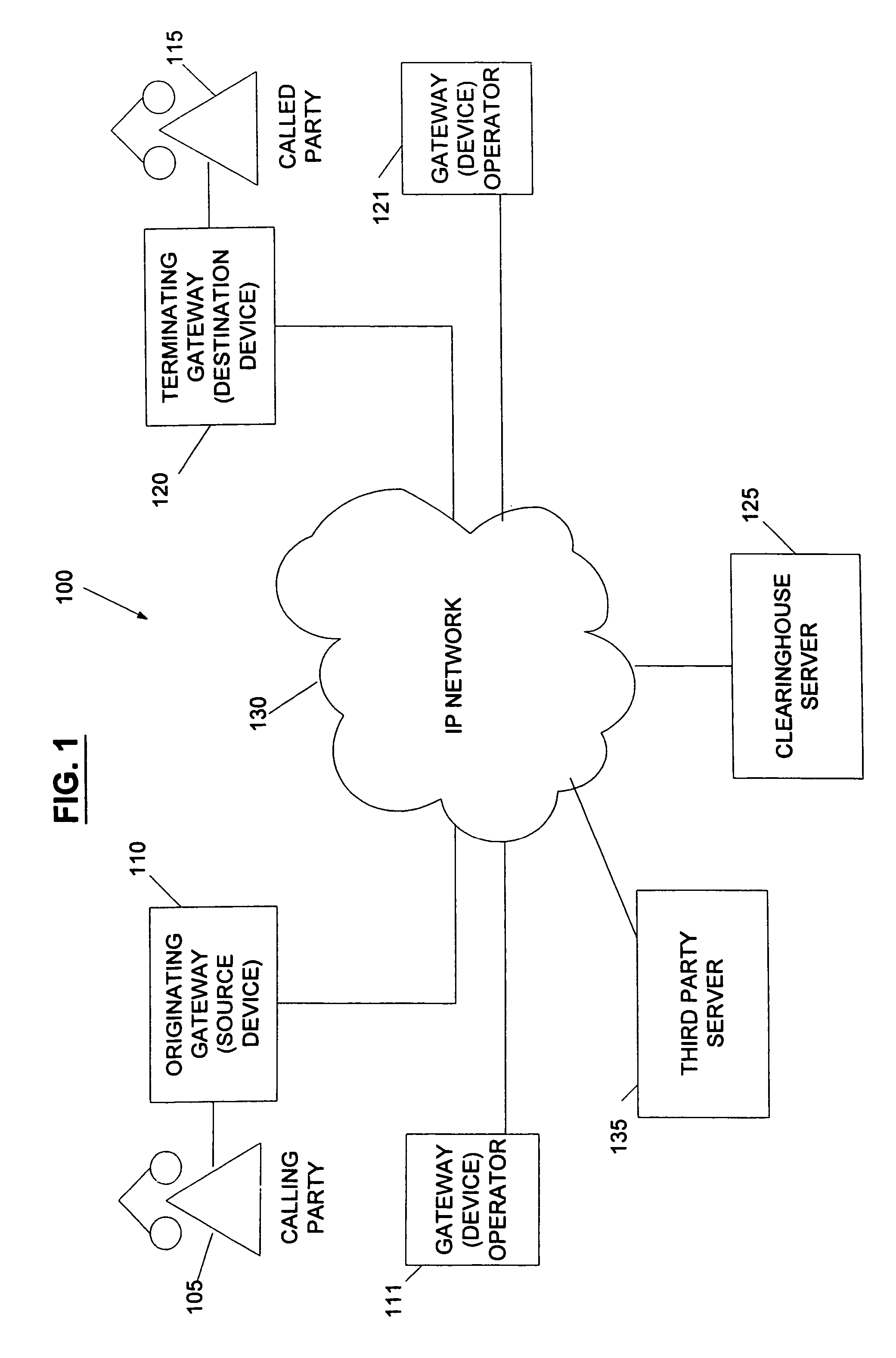
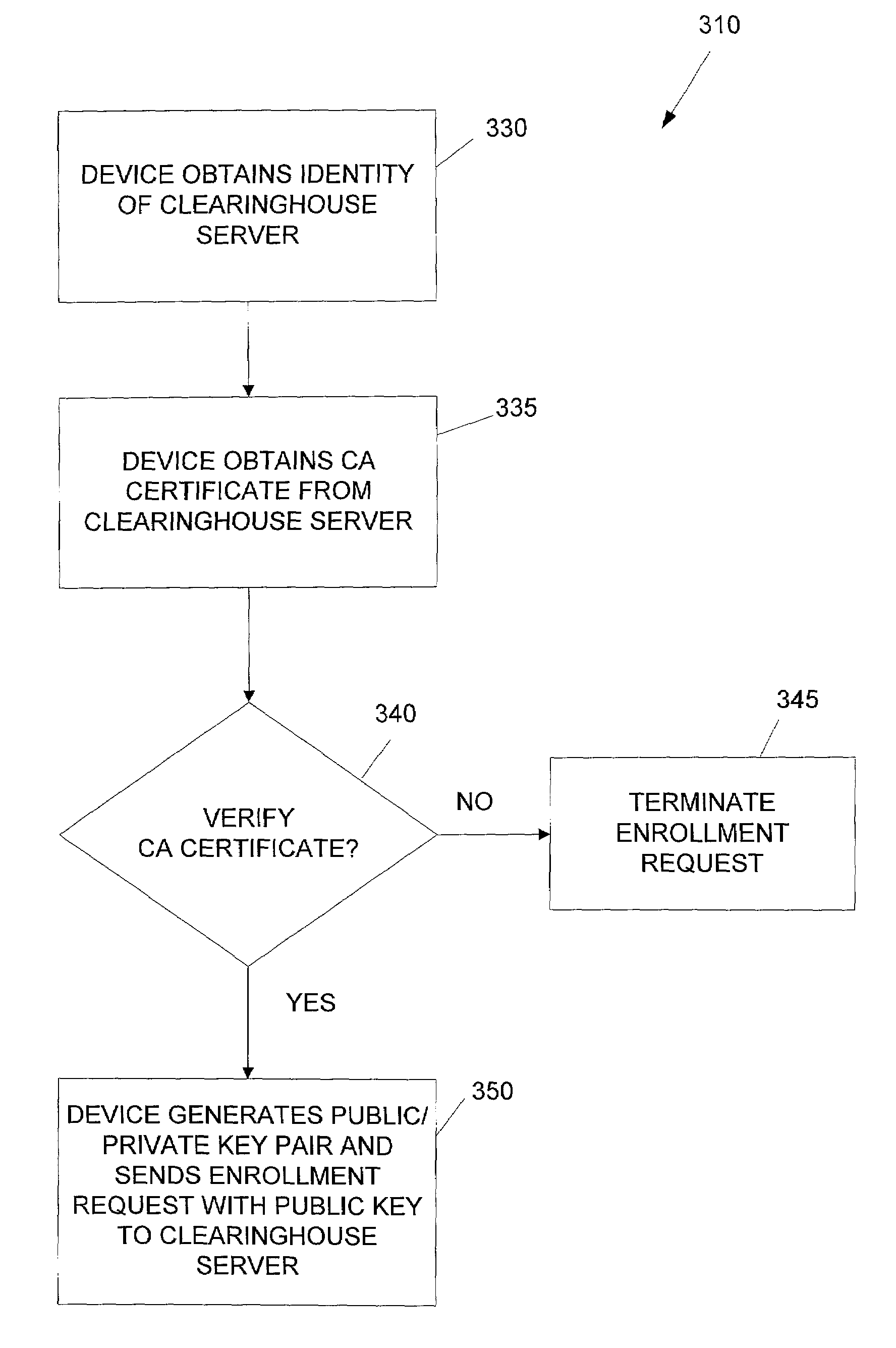
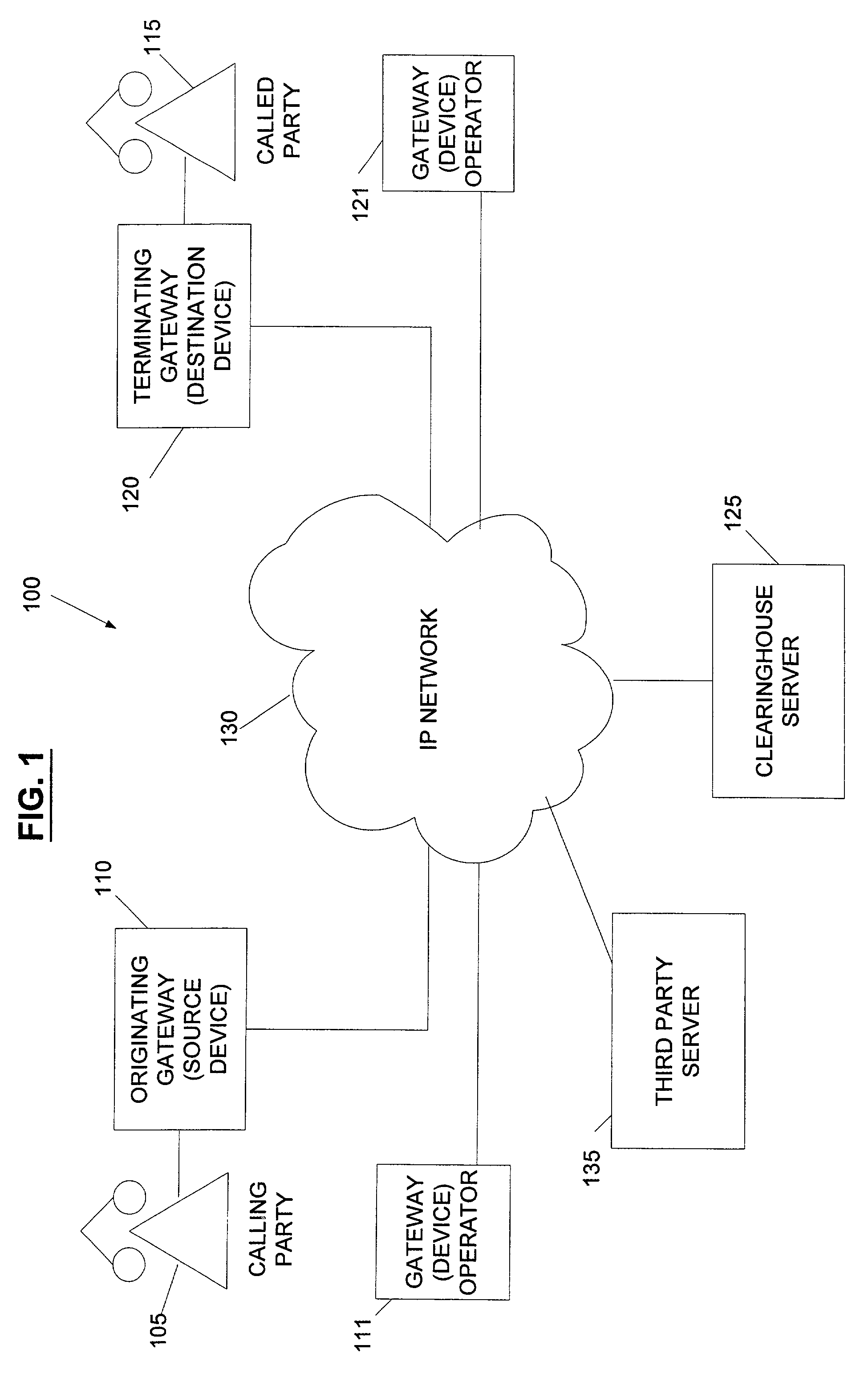
System and method for the secure enrollment of devices with a clearinghouse server for internet telephony and multimedia communications
InactiveUS20070033644A1Secure identitySecurely identifyingInterconnection arrangementsFinanceThe InternetSecurity level
Enrolling devices with a clearinghouse server for Internet telephony and multimedia communications. Enrollment can be the process of taking a network device (such as a router, gateway, gatekeeper, etc.) and exchanging encrypted information with the clearinghouse server, so that later communications with that device can be secured. The enrollment is done with levels of security and verification that ensures the devices and clearinghouse server is legitimate.
Owner:TRANSNEXUS
Delivery of a secure software license for a software product and a toolset for creating the software product
ActiveUS7742992B2Easy to useSecure identityPayment architectureProgram/content distribution protectionSecurity softwareSoftware license
A method for delivery of a licensed toolset to a software publisher for creating license-managed software products is disclosed. The method comprises providing an authorization process, and implementing the authorization process for both a toolset publisher and related toolset and a software publisher and related software product, whereby the same authorization process is used to obtain respective licenses. The authorization process includes creating a first public and private key pair for the software publisher, creating a second public and private key pair for the software product, creating an authorization program for the software program, with embedded copies of the first and second public keys, and combining the software program and the authorization program, such that when the authorization program is invoked, the authorization program obtains a license for controlling the use of the software program. The license is obtained by creating a license request, encrypting the license request using the second private key, transmitting the license request to a key authority, receiving a license from the key authority with license terms, decrypting the license, and using the license terms to control the use of the software program.
Owner:PACE ANTI PIRACY
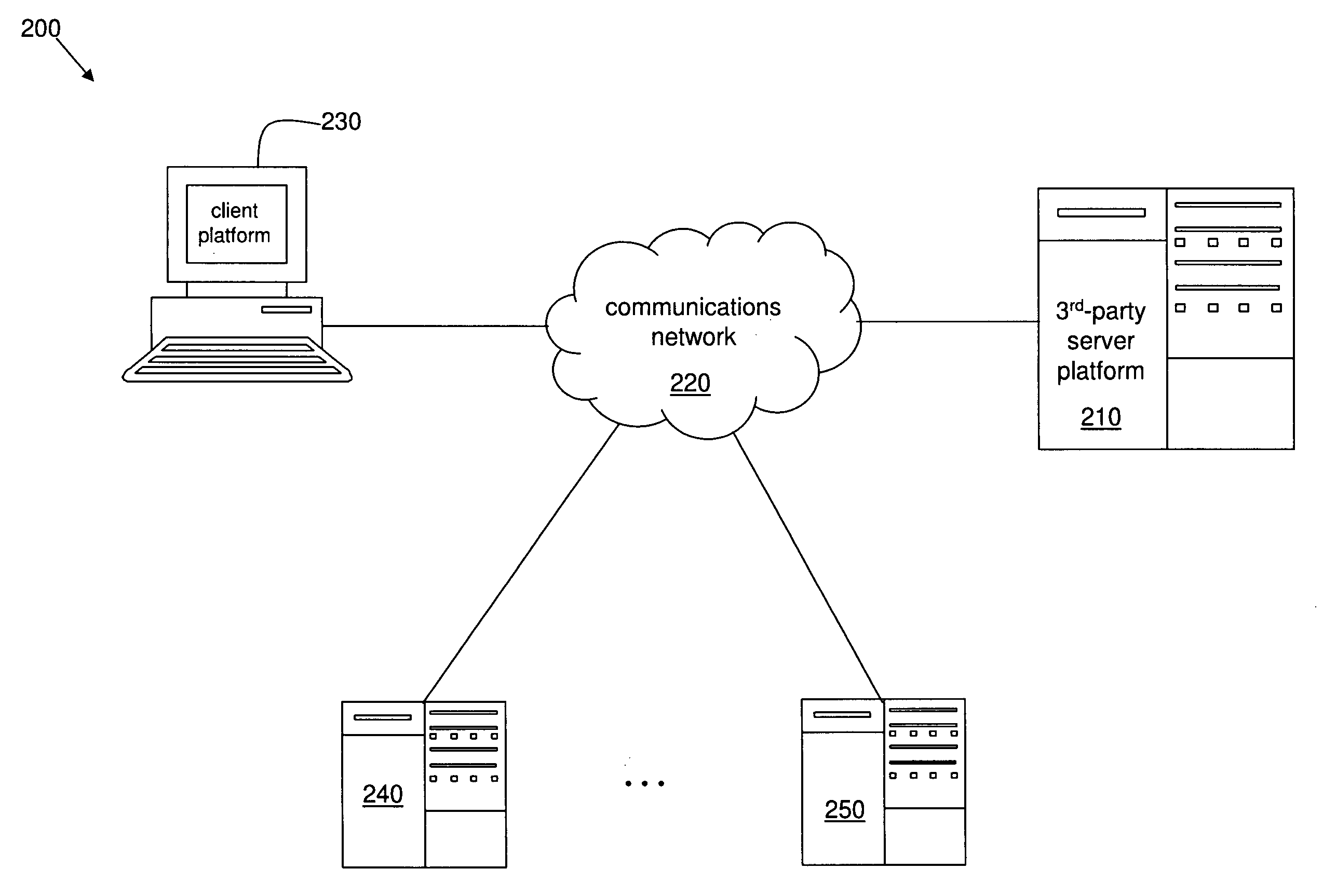
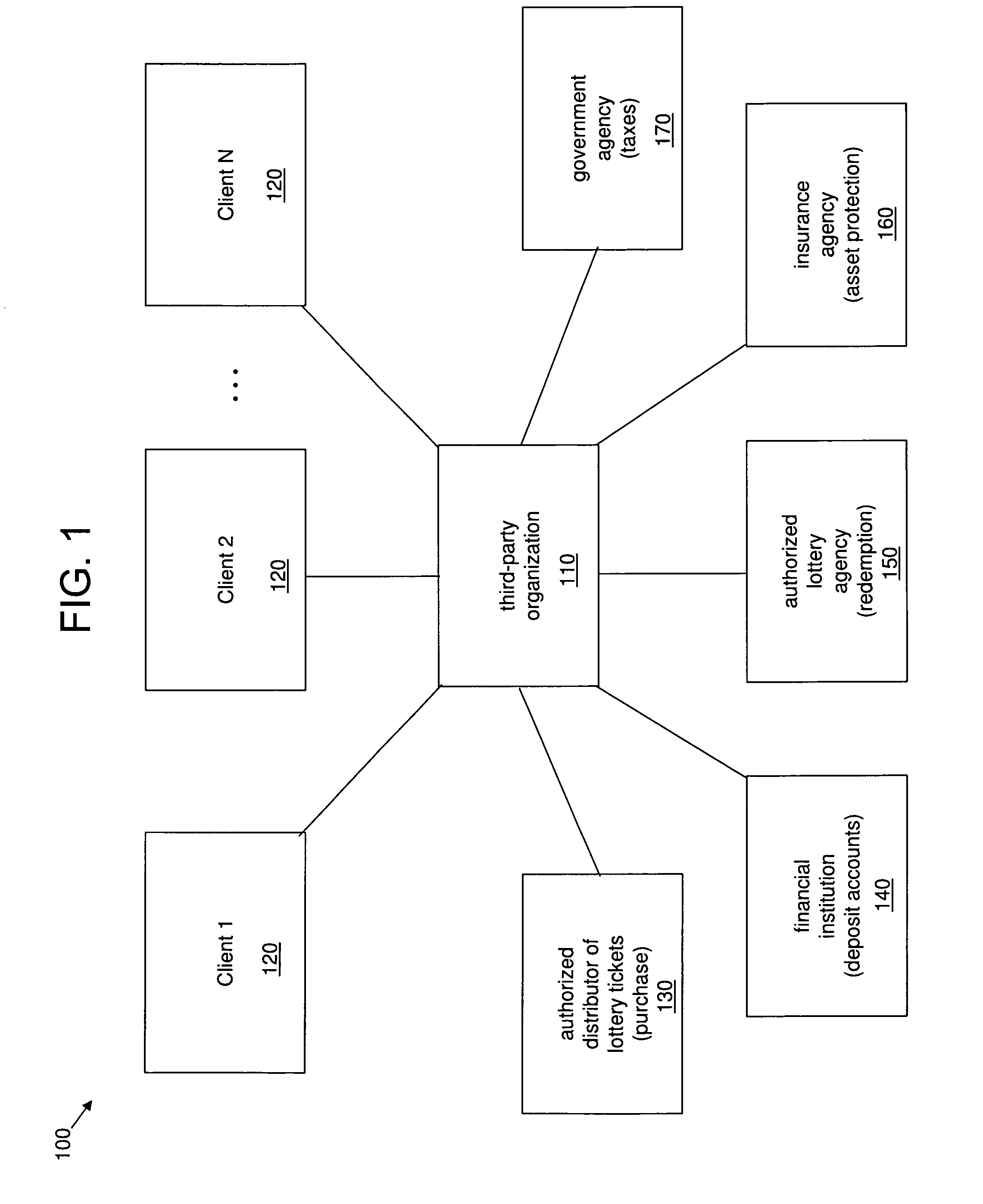
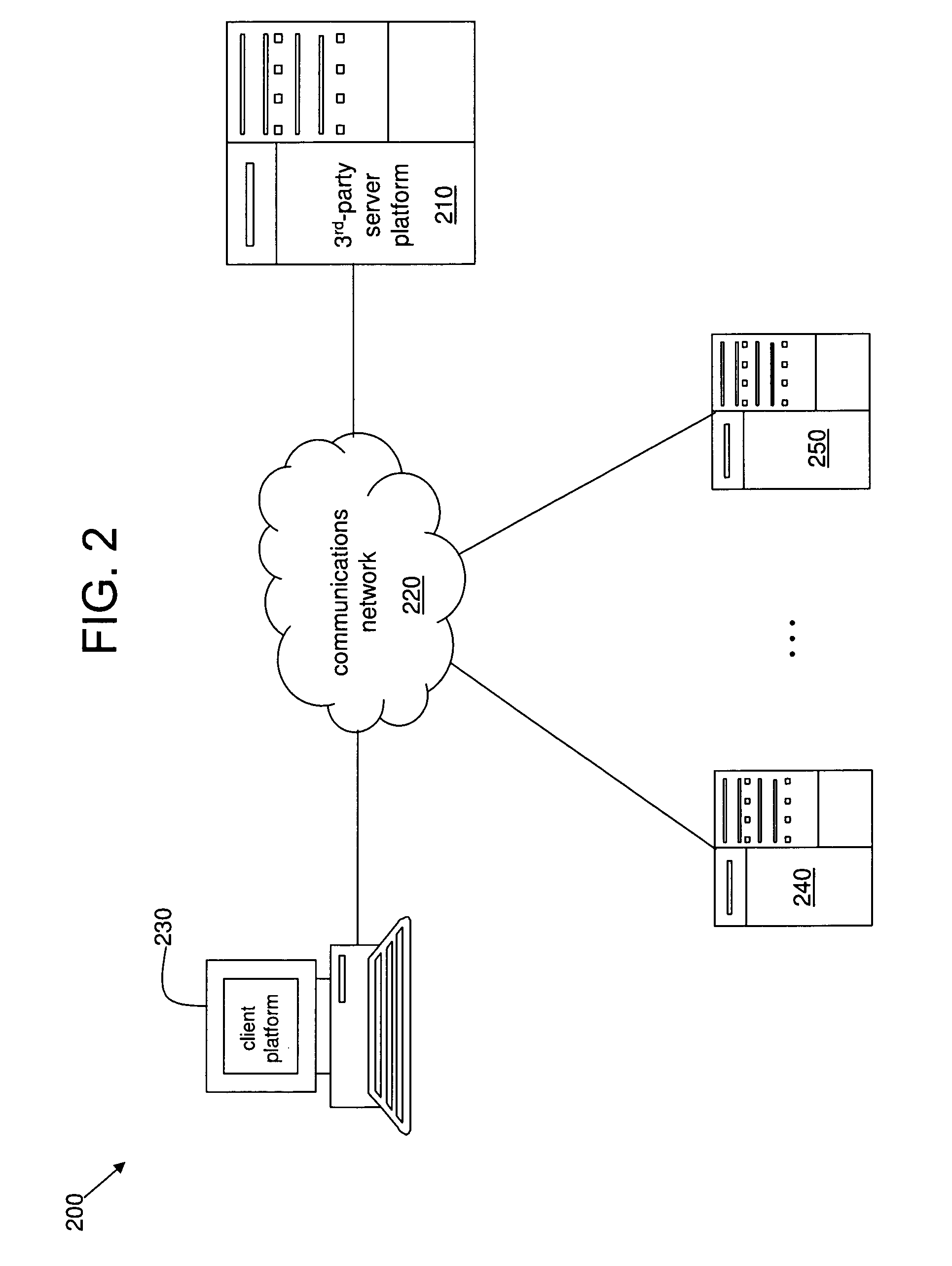
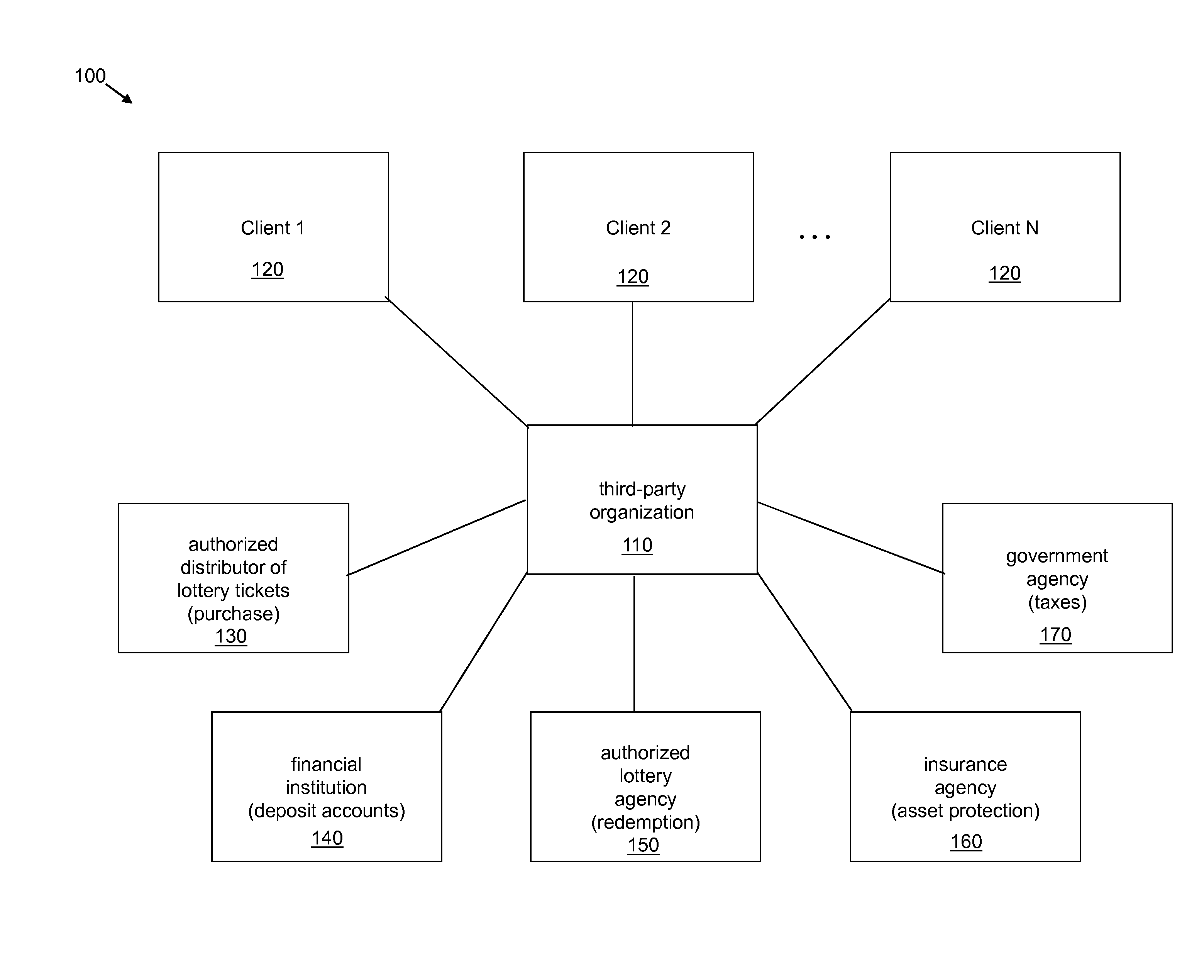
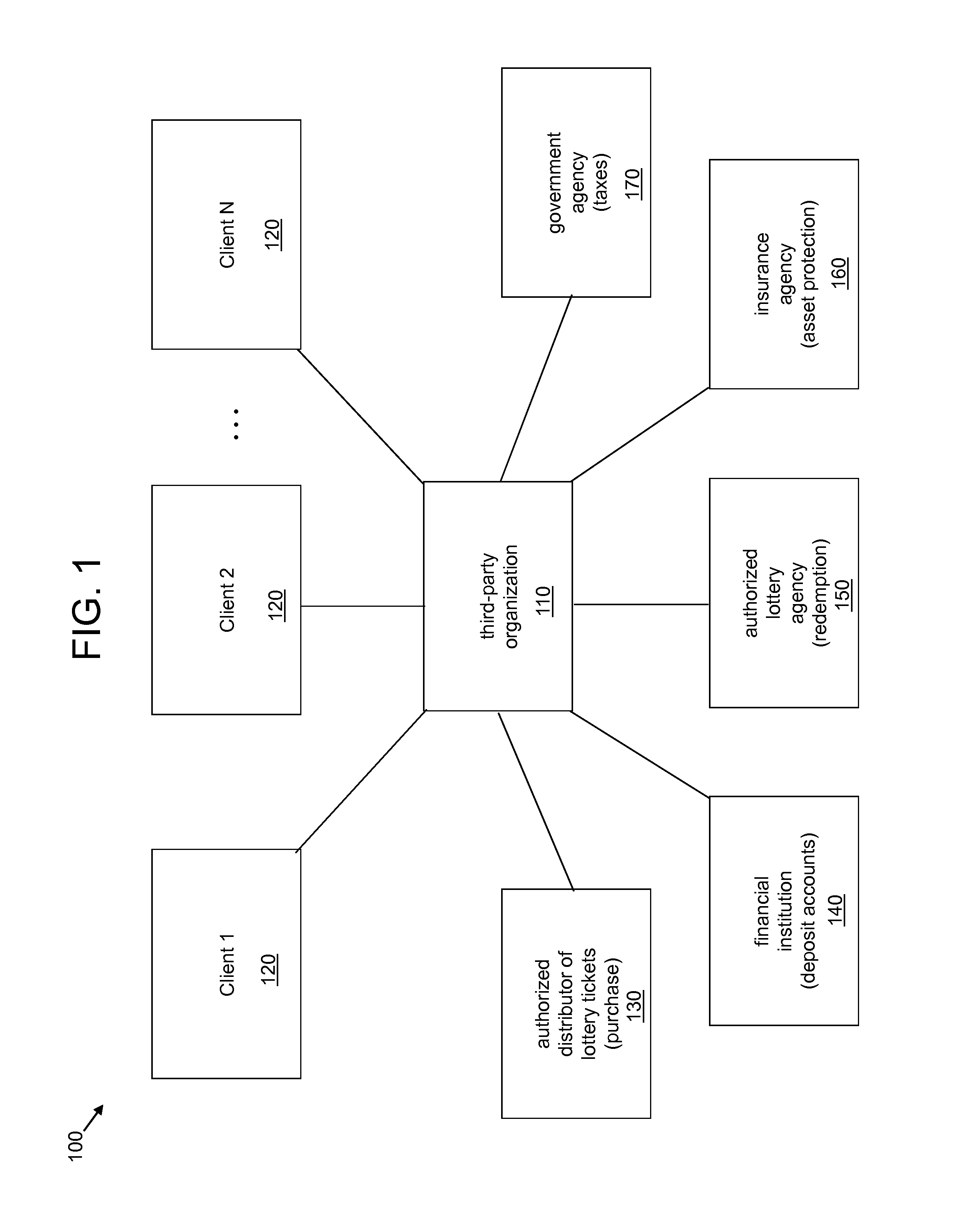
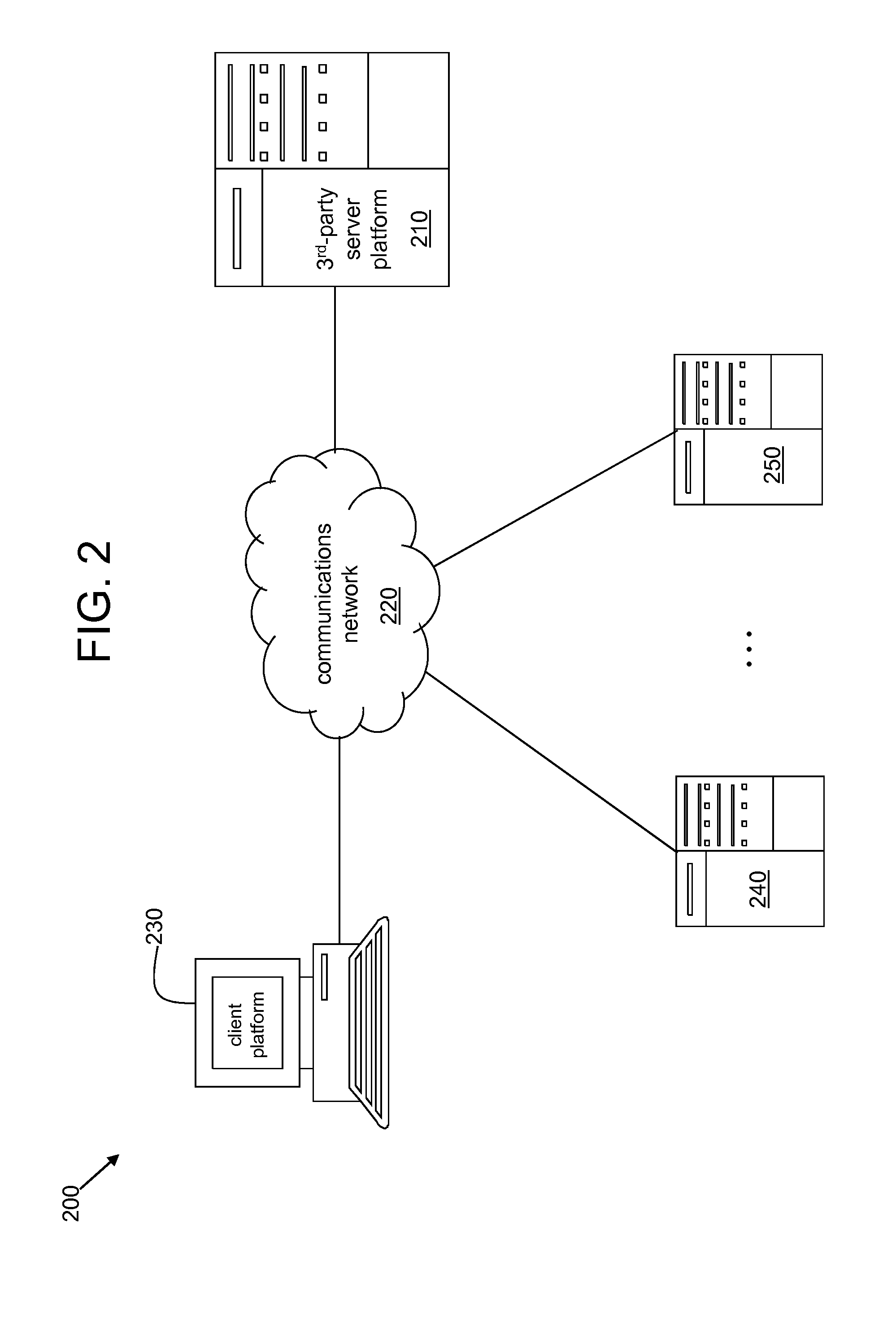
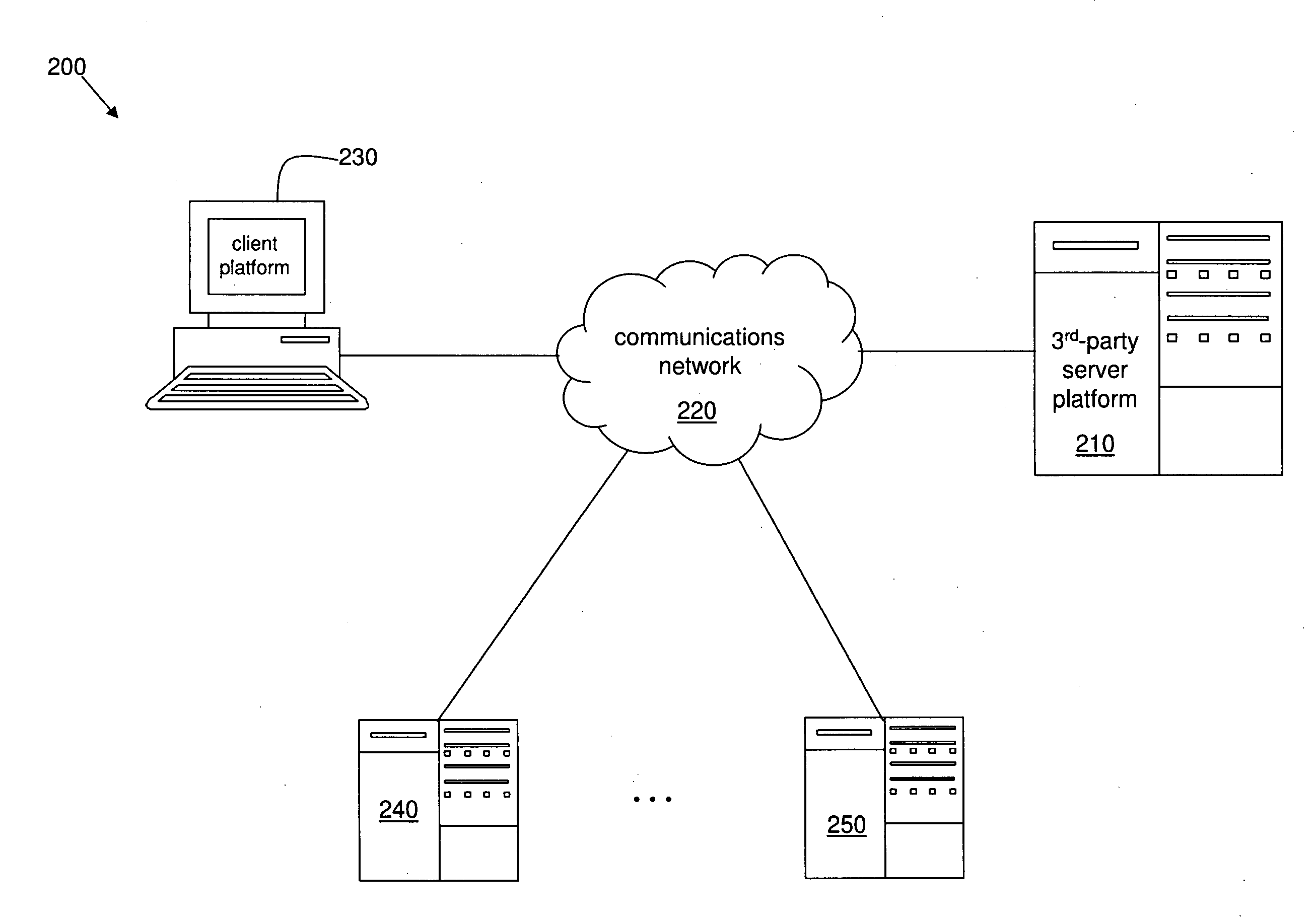
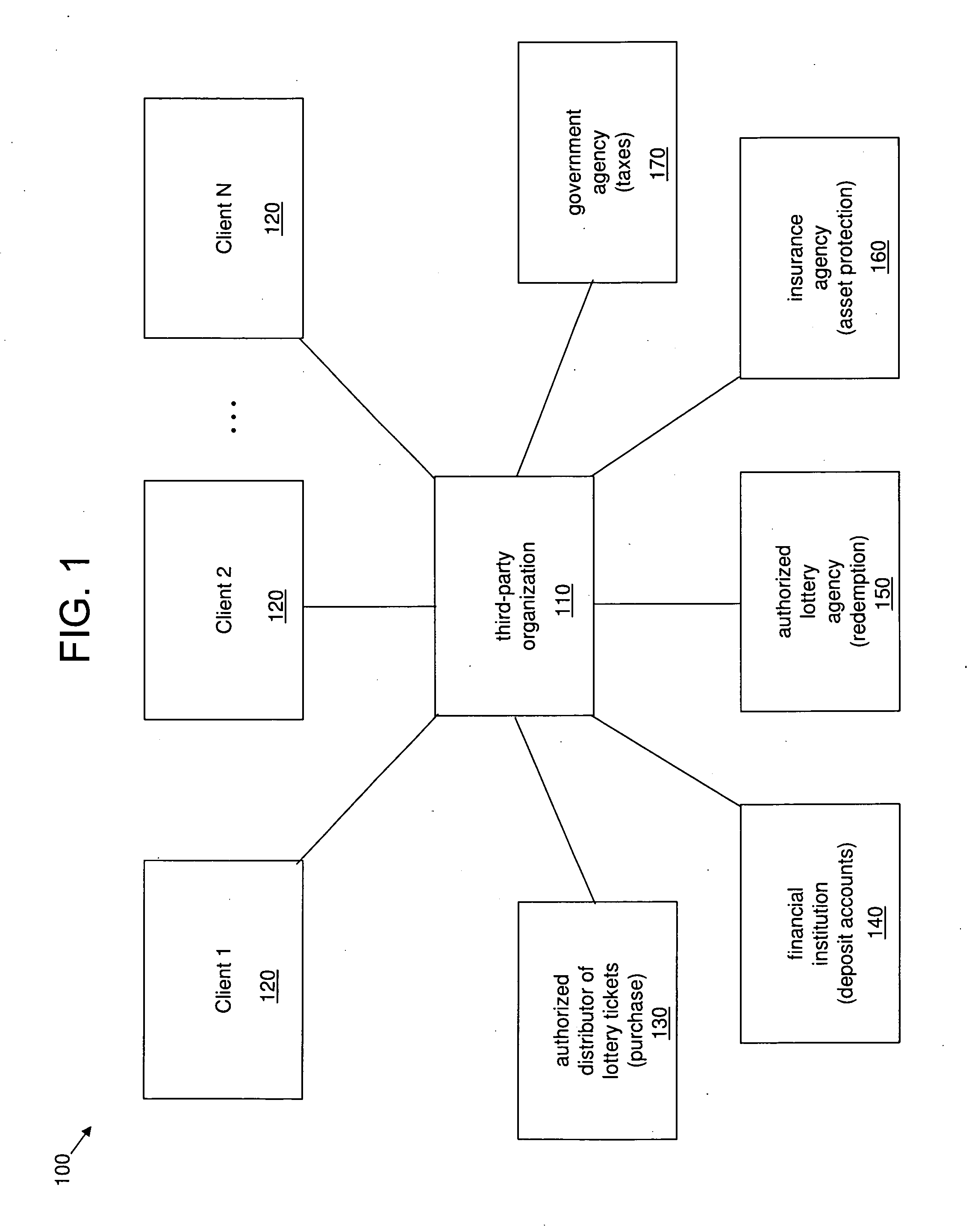
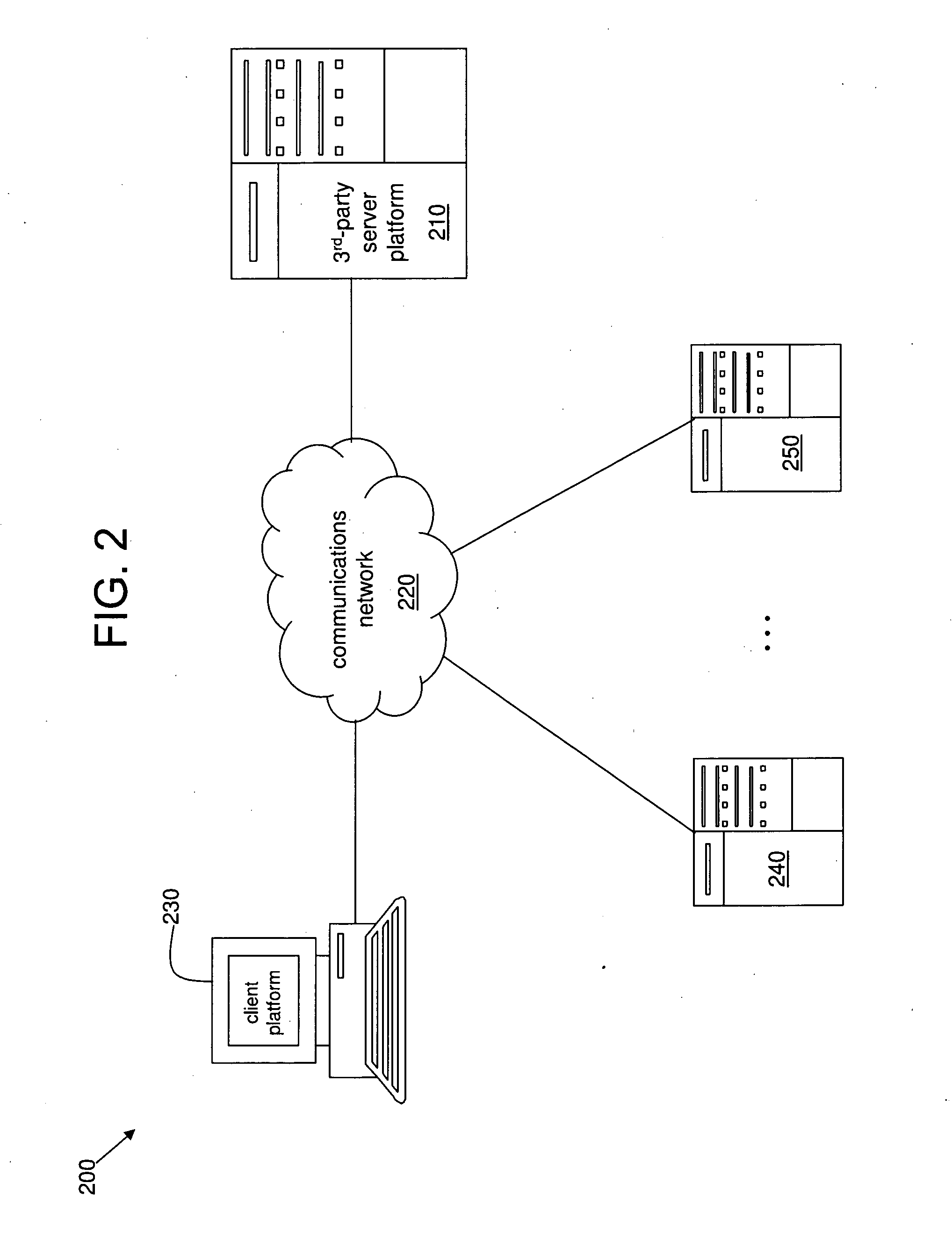
System and method for anonymously servicing lottery players
ActiveUS8219497B2Facilitate methodImprove identityDiscounts/incentivesPayment architectureThird partyClient-side
A system and method for servicing at least one lottery player while protecting an identity of the at least one lottery player. The system includes a server platform of a third party organization that facilitates the method. The method includes receiving a client request at the server platform via a communications network. The method further includes the third party organization obtaining at least one lottery ticket in response to the client request, and securely holding the at least one lottery ticket for the at least one lottery player specified in the client request. The method also includes the third party organization determining a status of the at least one lottery ticket via the server platform and the communications network. The method further includes the third party organization transforming the at least one lottery ticket into a monetary amount if a status of the at least one lottery ticket is or changes to a winning status. The method also includes the third party organization securely transferring at least a first portion of the monetary amount to at least one account or trust.
Owner:CRUCS HLDG
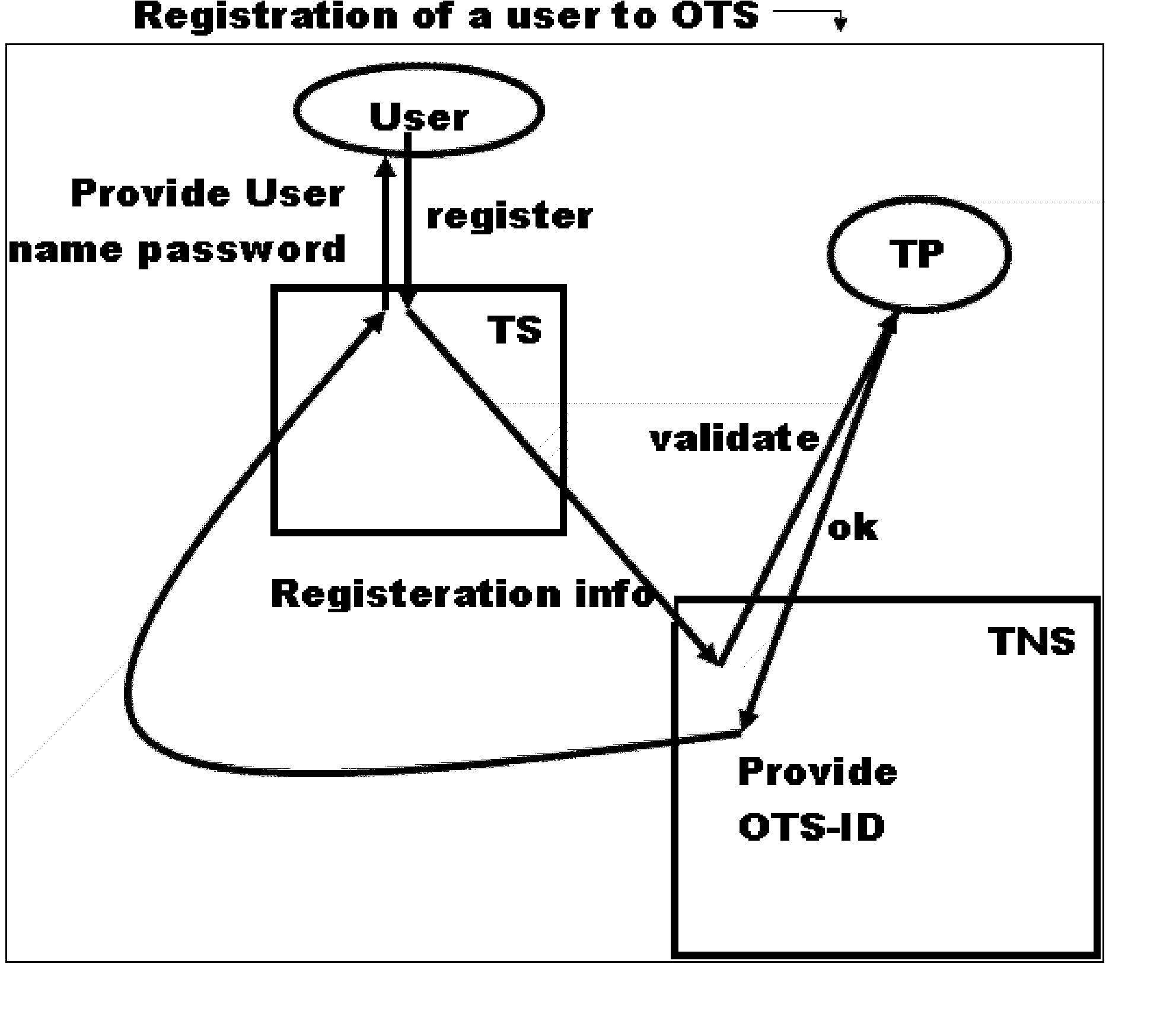
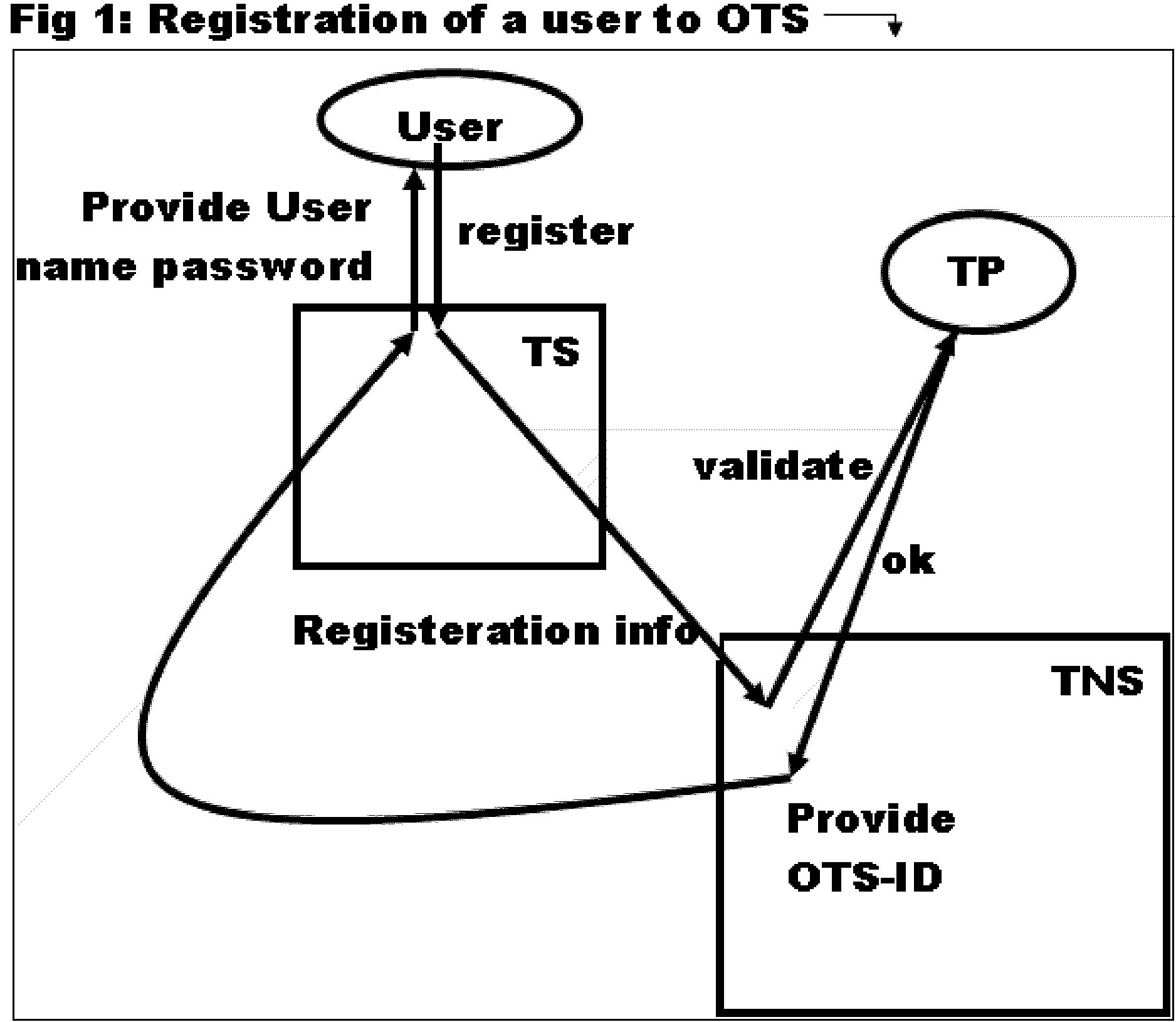
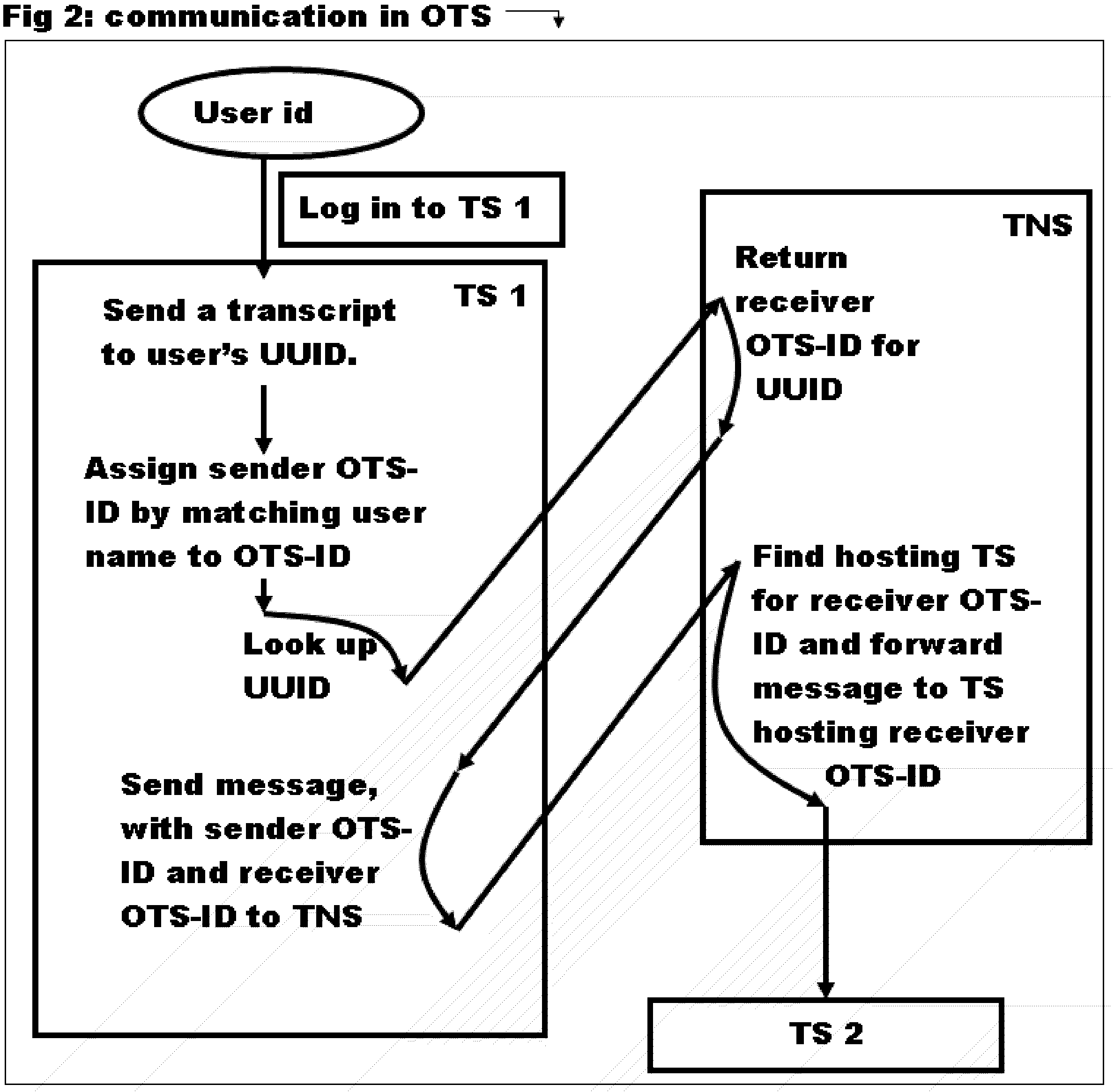
Original Transcript System: Method and System to issue, submit and view original electronic transcripts.
InactiveUS20050251679A1Secure identityEliminate needMicrobiological testing/measurementUser identity/authority verificationMultimediaComputer science
Transcript in OTS refer to any electronic file that can include a PDF, word or an image file, and is issued by an issuer. The original transcript system consists of transcript servers that register and host users. These transcript servers talk securely to each other through the transcript network server. Each OTS-ID that refers to a user can act in one of the roles of issuer, applicant or reviewer for a transcript that is defined by the user type. When a transcript is issued or submitted only the envelope for transcript information is sent. A view request causes the transcript file to be downloaded directly from the issuer. OTS provides web based access of transcripts and enables sharing of transcripts by the applicant to multiple reviewers, without the issuer having to explicitly share it to reviewers.
Owner:NARAYANAN PRASANNA
System and method for the secure enrollment of devices with a clearinghouse server for internet telephony and multimedia communications
InactiveUS7398551B2Securely identifyingSecure identityInterconnection arrangementsFinanceThe InternetSecurity level
Enrolling devices with a clearinghouse server for Internet telephony and multimedia communications. Enrollment can be the process of taking a network device (such as a router, gateway, gatekeeper, etc.) and exchanging encrypted information with the clearinghouse server, so that later communications with that device can be secured. The enrollment is done with levels of security and verification that ensures the devices and clearinghouse server is legitimate.
Owner:TRANSNEXUS
Secure transaction execution method based on smart contract
ActiveCN113222606AGuaranteed legal effectSolve financial problemsPayment protocolsTransaction dataFinancial transaction
The invention discloses a secure transaction execution method based on a smart contract. The method comprises the following steps: deploying a blockchain node service; receiving the original transaction voucher information for uplink storage; enabling each transaction processing node to sign a smart contract and deploy the smart contract to the blockchain; recording the encrypted transaction voucher information on a transaction data alliance chain based on the smart contract; judging whether a contract is deployed on a blockchain for a current smart contract, analyzing transaction parameters corresponding to the smart contract, checking the identity compliance, security and authority of the transaction parameters of the smart contract, packaging the smart contract, and enabling an execution end to call the smart contract and execute the smart contract; sending the effective consensus information to other transaction processing nodes, determining that the smart contract is effective, and performing uplink evidence storage. According to the invention, the information security is ensured, the requirements of the bank for transaction checking and account checking and clearing are met, the processing efficiency of each link in the transaction process is improved, the default risk caused by human factors is reduced, and the cost reduction and benefit increase of an industrial chain are promoted.
Owner:中企链信(北京)科技有限公司
Anti-counterfeit method and system for digital file
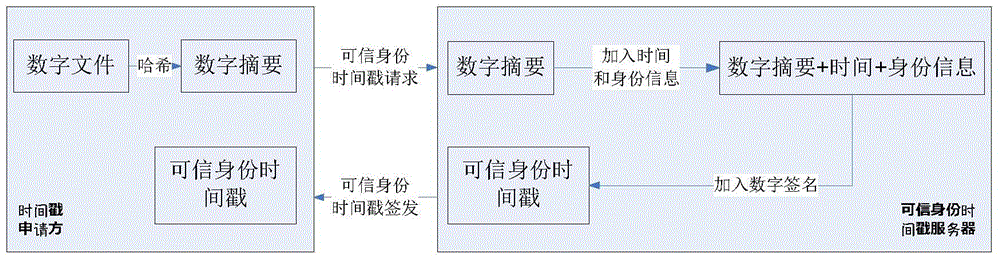
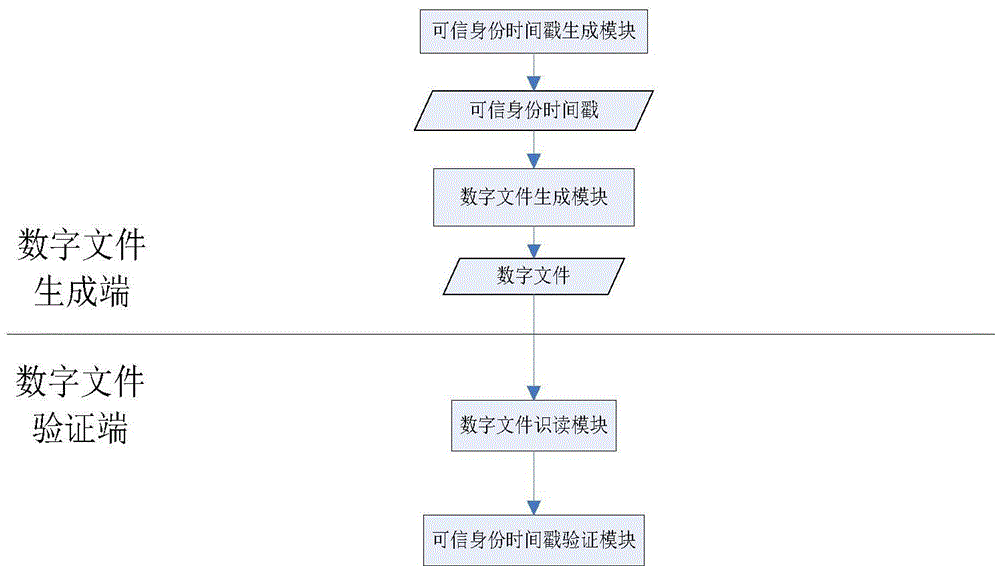
The invention discloses an anti-counterfeit method and system for a digital file. The invention comprises that a digital file producer generates a digital summary according to the content of a digital file, applies for a trusted identity timestamp from a trusted identity timestamp server, and generates a trusted digital file according to original information of the digital file and the trusted identity timestamp; and when the digital file is required for use or verification, the effectiveness and integrity of the generation time and content of the digital file are ensured, as well as the identity authenticity of the digital file producer by verifying the trusted identity timestamp in the digital file.
Owner:许田 +1
Access control system for machine room and control method for entry of machine room
InactiveCN107610306AEliminate potential safety hazardsSecure identityIndividual entry/exit registersEngineeringMedia access control
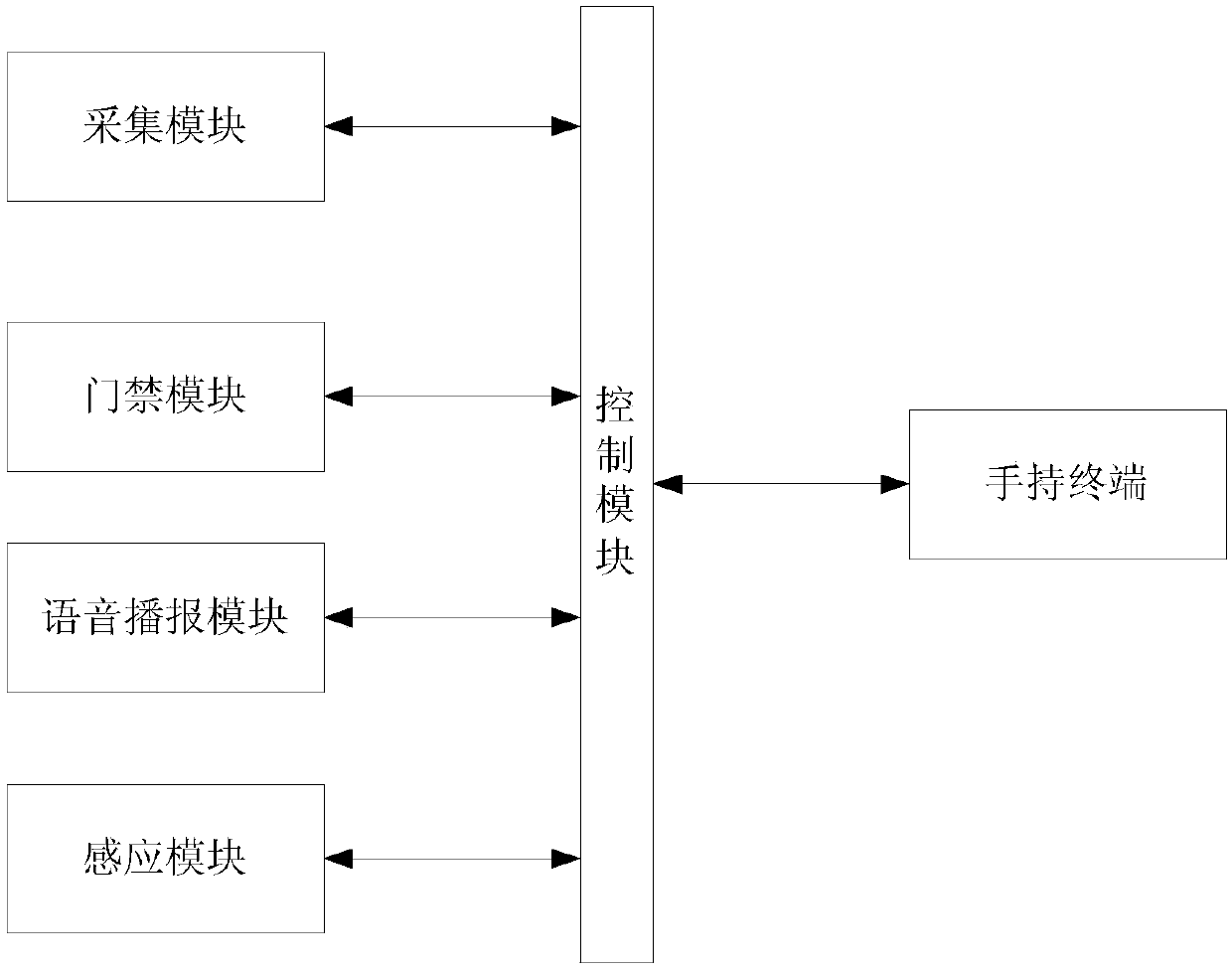
The invention provides an access control system for a machine room and a control method for the entry of the machine room, in order to solve the problem of the potential safety hazard of the machine room caused by the incapability of guaranteeing the identity of the present access control administrator. In the access control system, a collecting module is used for collecting the identity information of people who want to enter into the machine room; a control module is used for verifying people who want to enter into the machine room according to the collected information and sending the identity information of people who want to enter into the machine room to a handheld terminal after passing the verification; an administrator judges if allow people who want to enter into the machine roomto enter into the machine room according to the identity information received by the handheld terminal, sends an access-denying instruction or sends an admission instruction in the manner of inputting fingerprint information; a control module is used for sending a voice broadcast signal after receiving the access-denying instruction and sending an opening signal after receiving the admission instruction; an access control module is used for opening the machine room door according to the opening signal; a voice broadcast module is used for broadcasting the access-denying instruction accordingto the voice broadcast signal. The access control system is capable of guaranteeing the identity of the administrator in the manner of fingerprint verification and is capable of eliminating the potential safety hazard of the machine room.
Owner:INFORMATION & COMM COMPANY OF STATE GRID HEILONGJIANG ELECTRIC POWER COMPANY +1
System and method for the secure enrollment of devices with a clearinghouse server for internet telephony and multimedia communications
InactiveUS7203956B2Securely identifyingSecure identityInterconnection arrangementsFinanceThe InternetSecurity level
Enrolling devices with a clearinghouse server for Internet telephony and multimedia communications. Enrollment can be the process of taking a network device (such as a router, gateway, gatekeeper, etc.) and exchanging encrypted information with the clearinghouse server, so that later communications with that device can be secured. The enrollment is done with levels of security and verification that ensures the devices and clearinghouse server is legitimate.
Owner:TRANSNEXUS
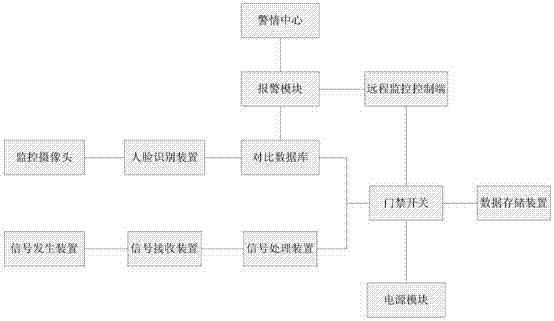
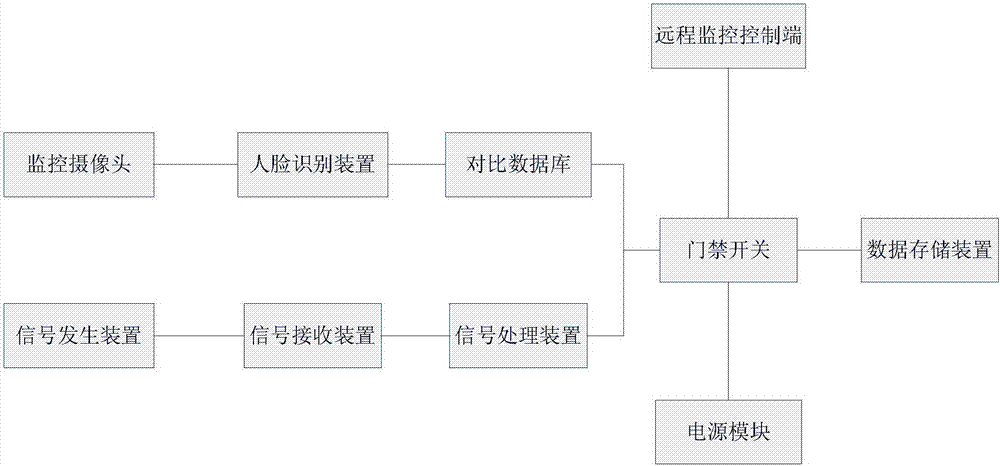
Access control system capable of identifying and alarming intelligently
InactiveCN107301700AIntelligent RecognitionAutomatic door releaseCharacter and pattern recognitionIndividual entry/exit registersSurveillance cameraEmbedded system
The invention discloses an access control system capable of identifying and alarming intelligently. The access control system capable of identifying and alarming intelligently comprises a monitoring camera, a face identifying device, a comparison database, a signal generating device, a signal receiving device, a signal processing device, an alarming module, an alarming situation centre, an access control switch, a remote monitoring control end, an access control switch, a power supply module and a data storage device; data can be transmitted among the monitoring camera, the face identifying device, the comparison database, the signal generating device, the signal receiving device, the signal processing device, the alarming module, the alarming situation centre, the access control switch, the remote monitoring control end, the access control switch, the power supply module and the data storage device; the monitoring camera is used for acquiring video data in a target area and transmitting the data to the face identifying device; the face identifying device is used for converting the video data which are transmitted by the monitoring camera into pictures and transmitting the pictures into the comparison database; the comparison database is used for comparing the obtained pictures with the pictures which are stored in the database, and transmitting a comparison result to the access control switch and the alarming module; the signal generating device is used for transmitting a signal to the signal receiving device when the signal generating device is at a certain distance from the signal receiving device.
Owner:成都智慧家信息技术有限公司
Message safety transfer system
InactiveCN101170554AImprove securityImprove application levelKey distribution for secure communicationError preventionCode bookInformation transmission
An information security transmission system is disclosed. The system comprises a first information equipment and a second information equipment, wherein the first information equipment can obtain at least one certification data, connecting to the second information equipment through a network for processing an information transmission, accordingly, a key pair used for encryption / decryption can be obtained through the certificate authority or that can be obtained without the certificate authority selectively, such that the information transmission security channel can be established and the data transmission security can be ensured. The first information equipment and the second information equipment respectively comprises a first dynamic codec and a second dynamic codec for processing a coding / decoding process depending on a dynamic code book, furthermore, an automatic error detecting mechanism and an error correcting mechanism can be associated for ensuring the data transmission security and the data correction especially at one time transmission. The transmission data is under the protection of accessing limit, such as time limit, number of times limit, or equipment limit, such that once the receiver end has received the transmission data, the transmission data can be read under the accessing limit, therefore, if the accessing limit is overtook, then the transmission data would be removed for preventing the data to be lost.
Owner:STARS TECH
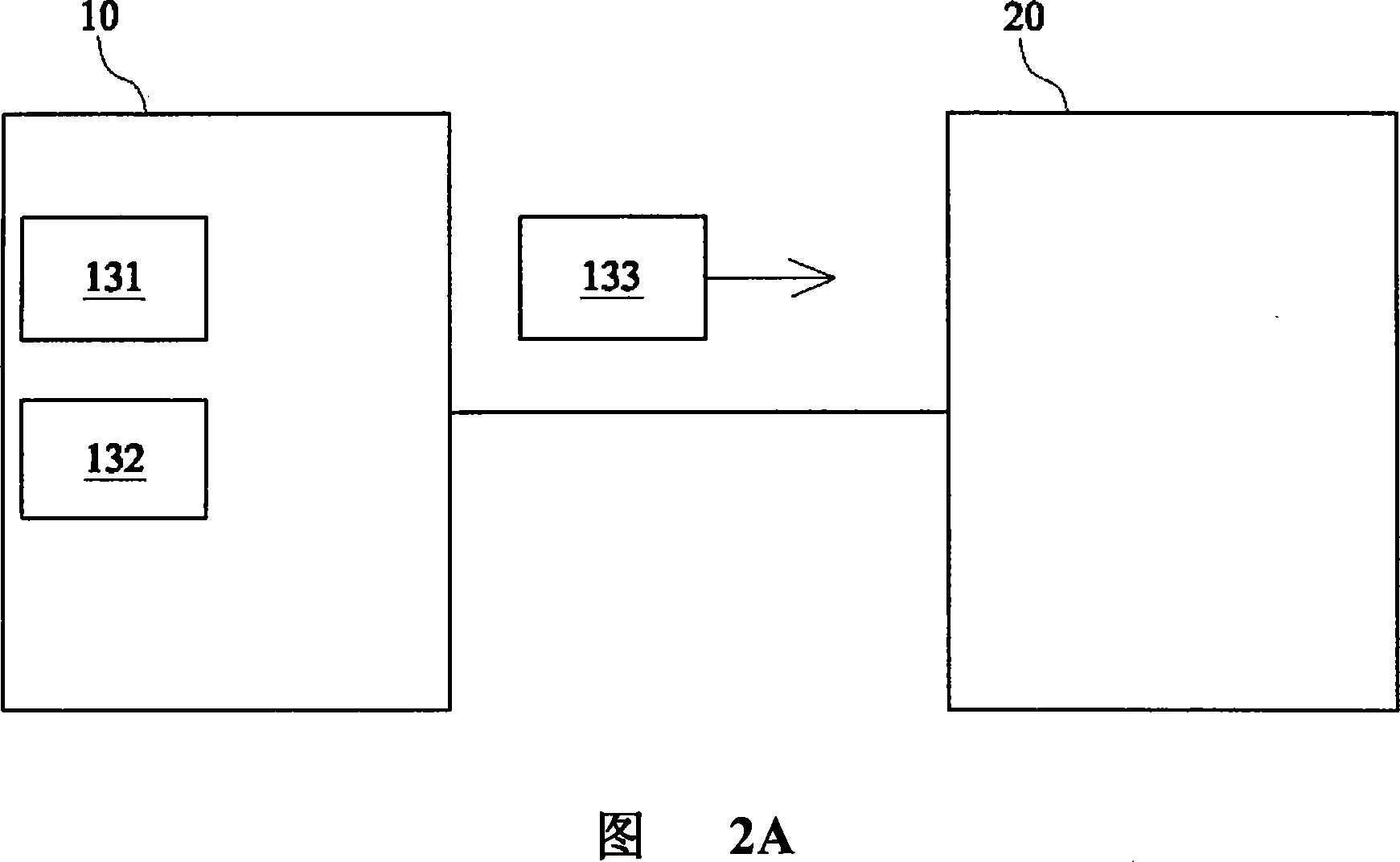
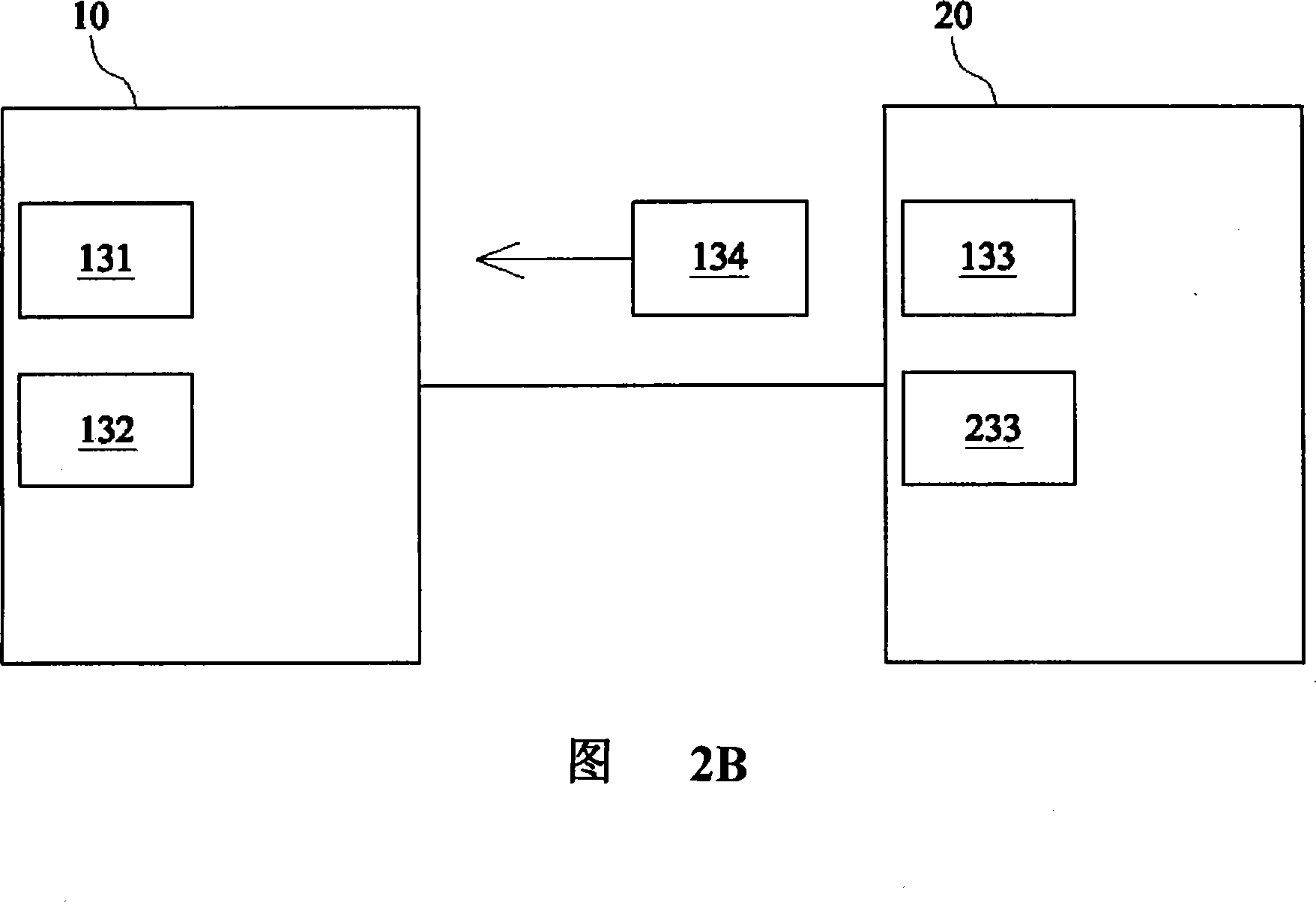
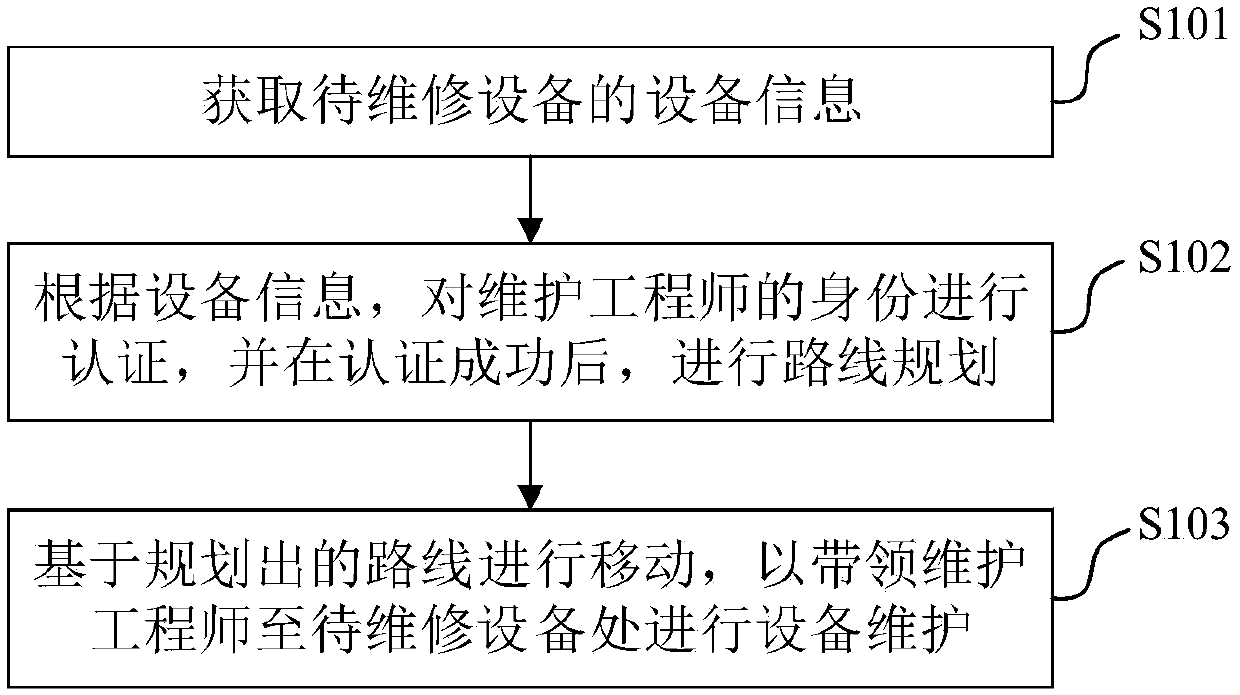
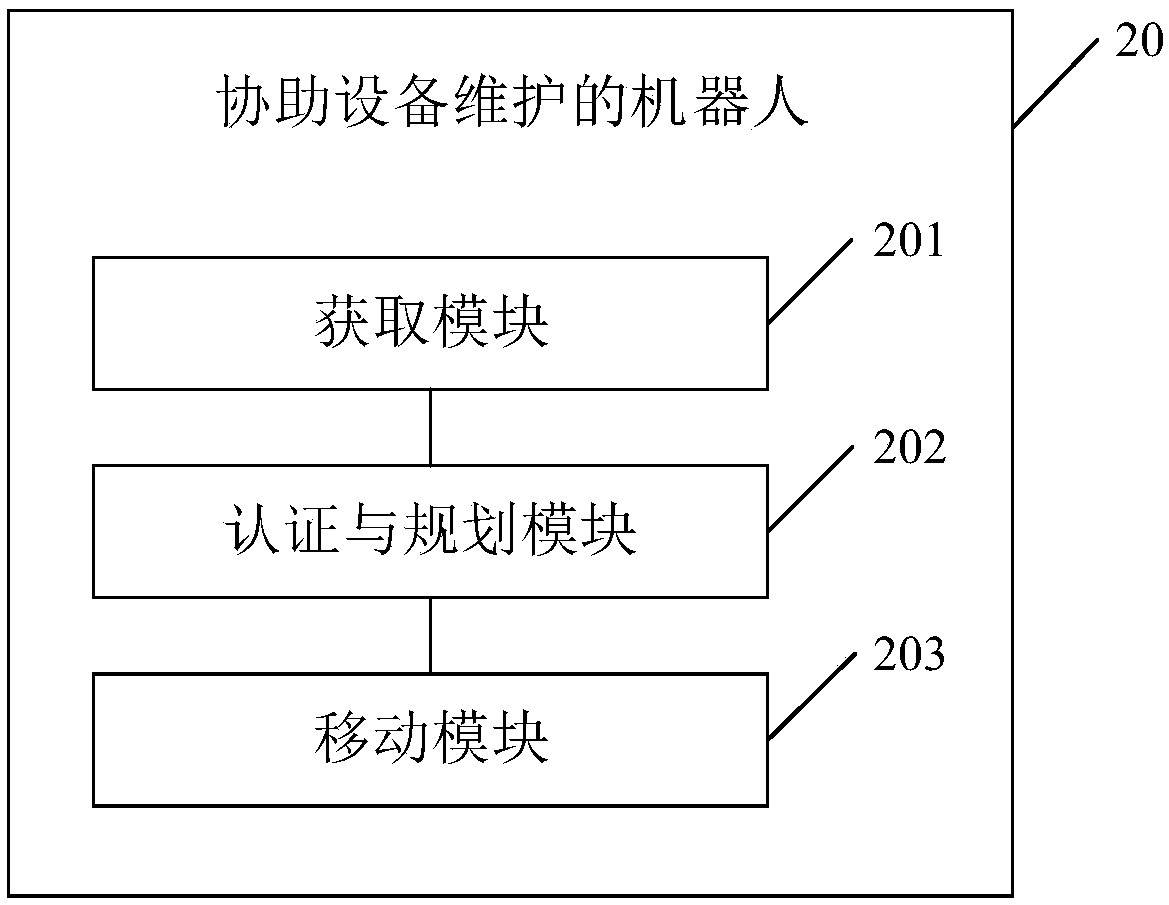
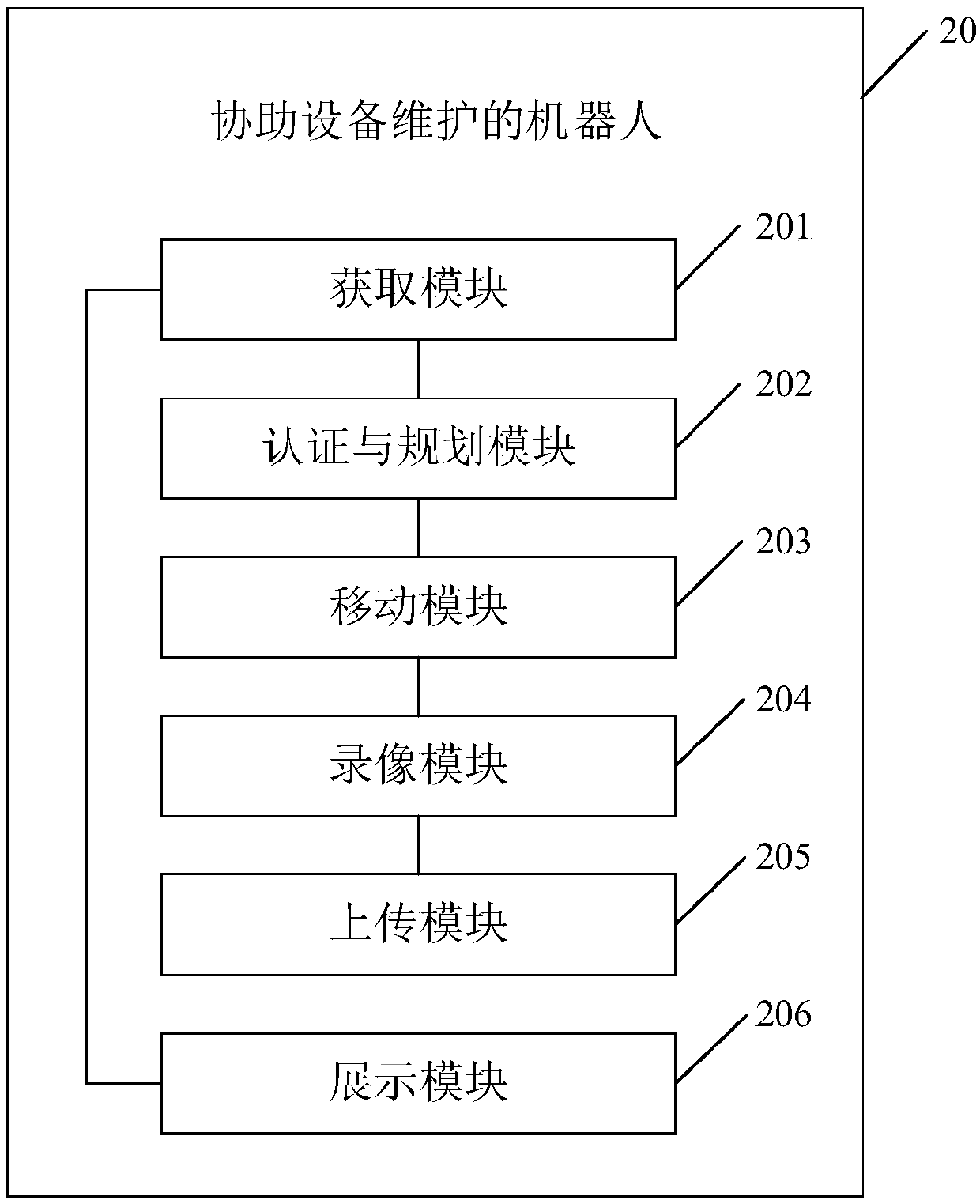
Method for assisting equipment maintenance by utilizing robot, robot and electronic device
PendingCN109635538ASecure identityReduce workloadForecastingDigital data authenticationMaintenance engineeringMaintaining equipment
The invention provides a method for assisting equipment maintenance by utilizing a robot, a robot and an electronic device, and relates to the technical field of machine room management. The method comprises the following steps: obtaining equipment information of to-be-maintained equipment; authenticating the identity of a maintenance engineer according to the equipment information, and planning aroute after the authentication is successful; and moving based on the planned route so as to lead a maintenance engineer to the to-be-maintained equipment for equipment maintenance. According to themethod and the device, the maintenance engineer who successfully authenticates the identity is assisted to work, so that the identity of the maintenance engineer is guaranteed, the maintenance engineer can be guided to the to-be-maintained equipment for equipment maintenance, the workload of the maintenance engineer is reduced, and the maintenance efficiency and reliability are improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
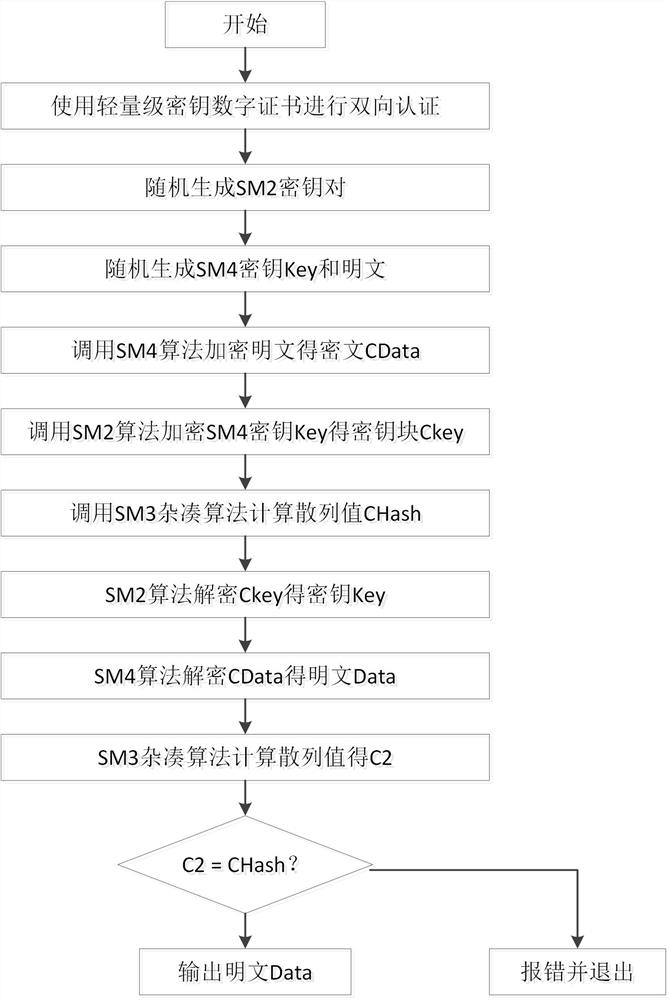
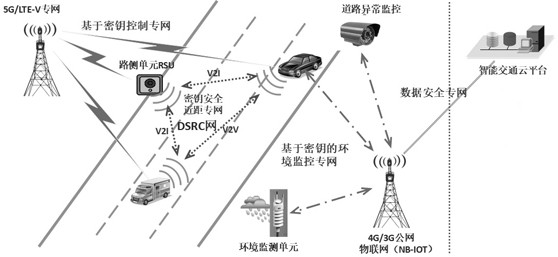
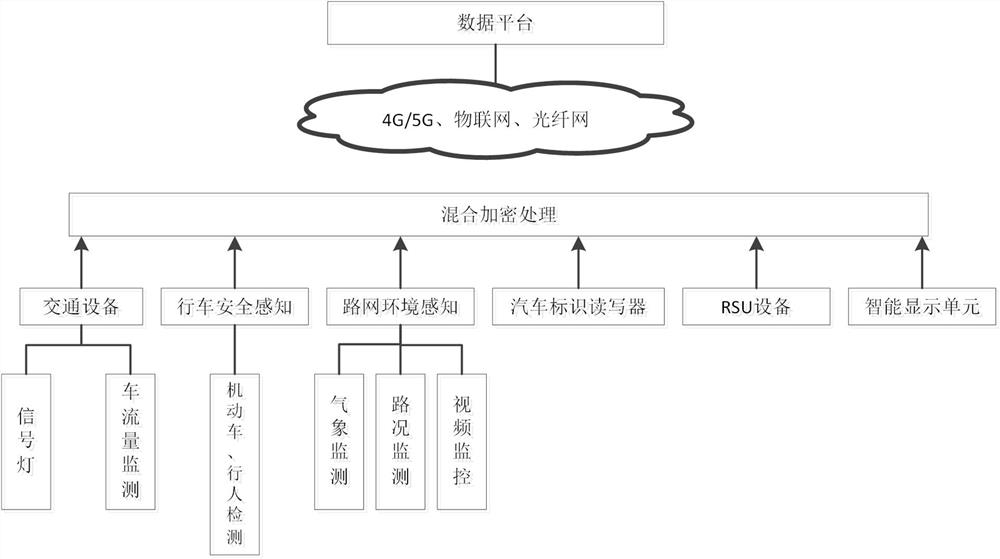
Traffic sensor network data transmission method and system based on hybrid encryption, and medium
ActiveCN112469003ASimplify the data parsing processImprove authentication efficiencyParticular environment based servicesNetwork topologiesPlaintextSmart infrastructure
The invention discloses a traffic sensor network data transmission method and system based on hybrid encryption, and the method comprises the steps: carrying out the end-to-end data transmission between an intelligent vehicle-mounted terminal and intelligent infrastructure side equipment and a cloud computing center, and carrying out the bidirectional authentication through an intelligent trafficlight-weight secret key digital certificate borne by a server; and in the data transmission process, using a hybrid encryption transmission method for carrying out dual encryption on data, and meanwhile, adding a random key and a random plaintext to calculate a hash value for comparison and verification. According to the method, the advantages of high encryption and decryption speed of the SM4 symmetric encryption algorithm and low management difficulty and high security of the encryption key of the SM2 asymmetric encryption algorithm are combined, so that the method can be applied to the communication process of an intelligent terminal, intelligent basic side equipment and a computing center, and the security and the transmission efficiency of data transmission of the traffic sensor network can be effectively improved.
Owner:NANJING UNIV OF SCI & TECH
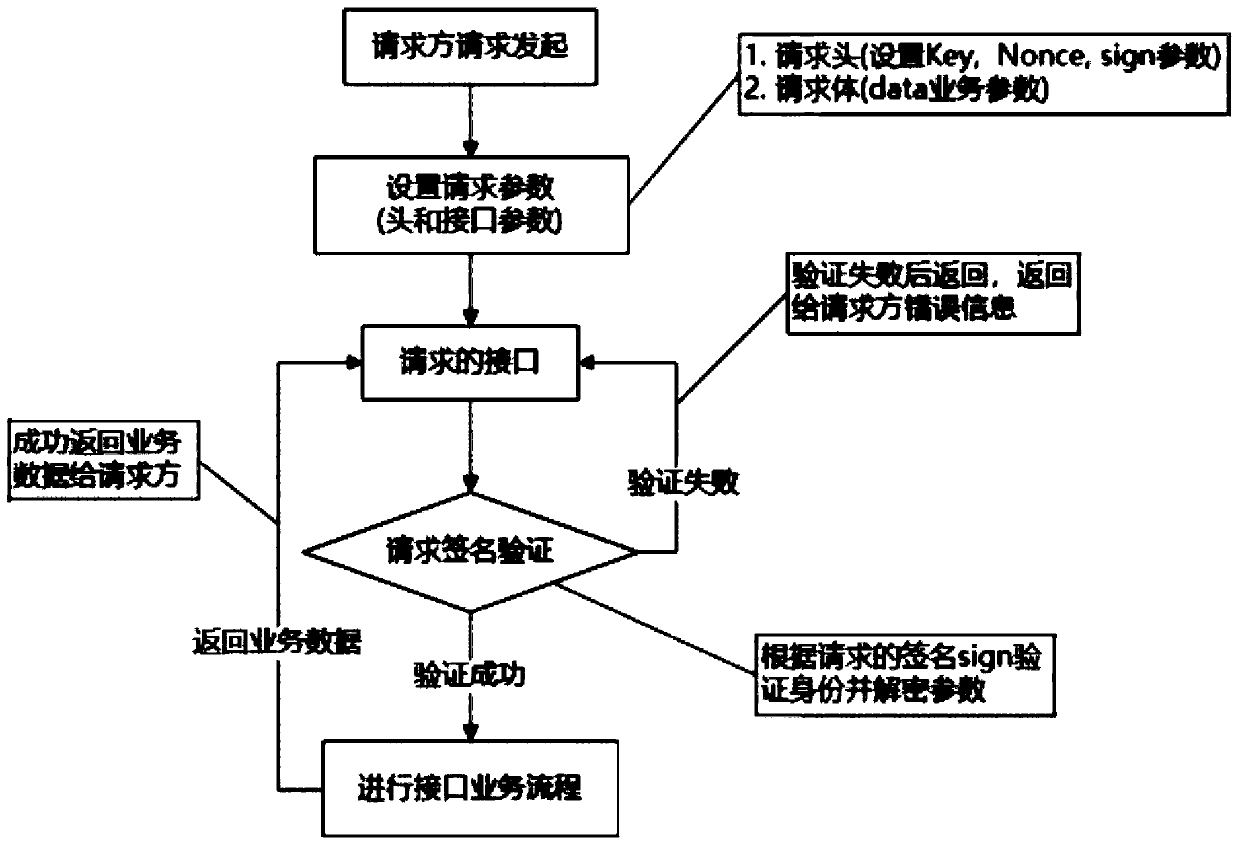
A method for safely providing a restful interface
InactiveCN109818746ASecure identityEncryption method is flexibleKey distribution for secure communicationEncryption apparatus with shift registers/memoriesStatus changedEncryption
The invention relates to a safe method for providing a restful interface, which comprises the following steps of: S1, firstly, a key and a secret are respectively distributed to each request interfaceparty, and s the keys and the secret are stored in a system by an interface provider and enabling the interface provider to be in one-to-one correspondence with the identities of requesters; S2, a request interface party needs to bring a specific identity verification parameter according to the requirement for calling the interface every time; And S3, after the interface of the interface providerreceives the request, if the parameter verification is passed, RSA decryption is performed on the service parameters in the request body, and data required by the request is returned. According to the invention, the data security transmitted by the interface is ensured; Compared with the same type of security interface, the encryption mode is more flexible and safer; Identities of requesters areensured, and requests are prevented from forgery to obtain data.
Owner:深圳竹云科技股份有限公司
System and method for anonymously servicing lottery players
InactiveUS20120270628A1Facilitate methodImprove identityDiscounts/incentivesPayment architectureThird partyInternet privacy
A system and method for servicing at least one lottery player while protecting an identity of the at least one lottery player. The system includes a server platform of a third party organization that facilitates the method. The method includes receiving a client request of a client at a server platform of a third party organization via a communication network, obtaining a lottery ticket from an authorized distributor of lottery tickets in response to the client request and securely holding the lottery ticket for the lottery player specified in the client request, automatically determining a status of the lottery ticket via an authorized lottery agency over the communication network, transforming the lottery ticket into a monetary amount when a status of the lottery ticket is or changes to a winning status, and securely transferring at least a first portion of the monetary amount to an account or trust.
Owner:CRUCS HLDG
System and method for anonymously servicing lottery players
ActiveUS20100009739A1Facilitate methodImprove identityDiscounts/incentivesPayment architectureThird partyDatabase
A system and method for servicing at least one lottery player while protecting an identity of the at least one lottery player. The system includes a server platform of a third party organization that facilitates the method. The method includes receiving a client request at the server platform via a communications network. The method further includes the third party organization obtaining at least one lottery ticket in response to the client request, and securely holding the at least one lottery ticket for the at least one lottery player specified in the client request. The method also includes the third party organization determining a status of the at least one lottery ticket via the server platform and the communications network. The method further includes the third party organization transforming the at least one lottery ticket into a monetary amount if a status of the at least one lottery ticket is or changes to a winning status. The method also includes the third party organization securely transferring at least a first portion of the monetary amount to at least one account or trust.
Owner:CRUCS HLDG
Access control device triggered by approaching
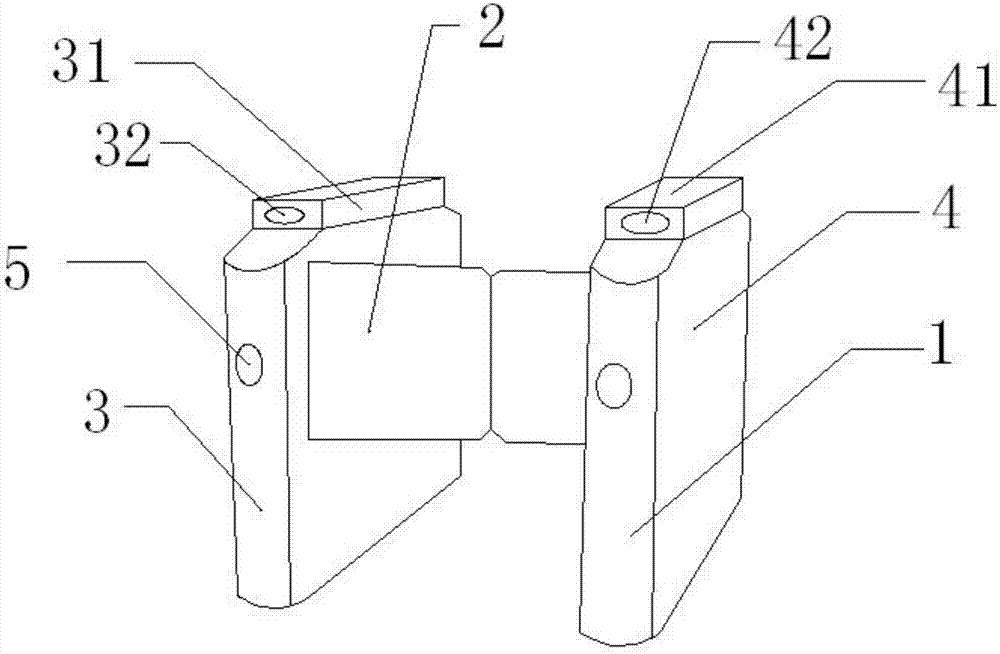
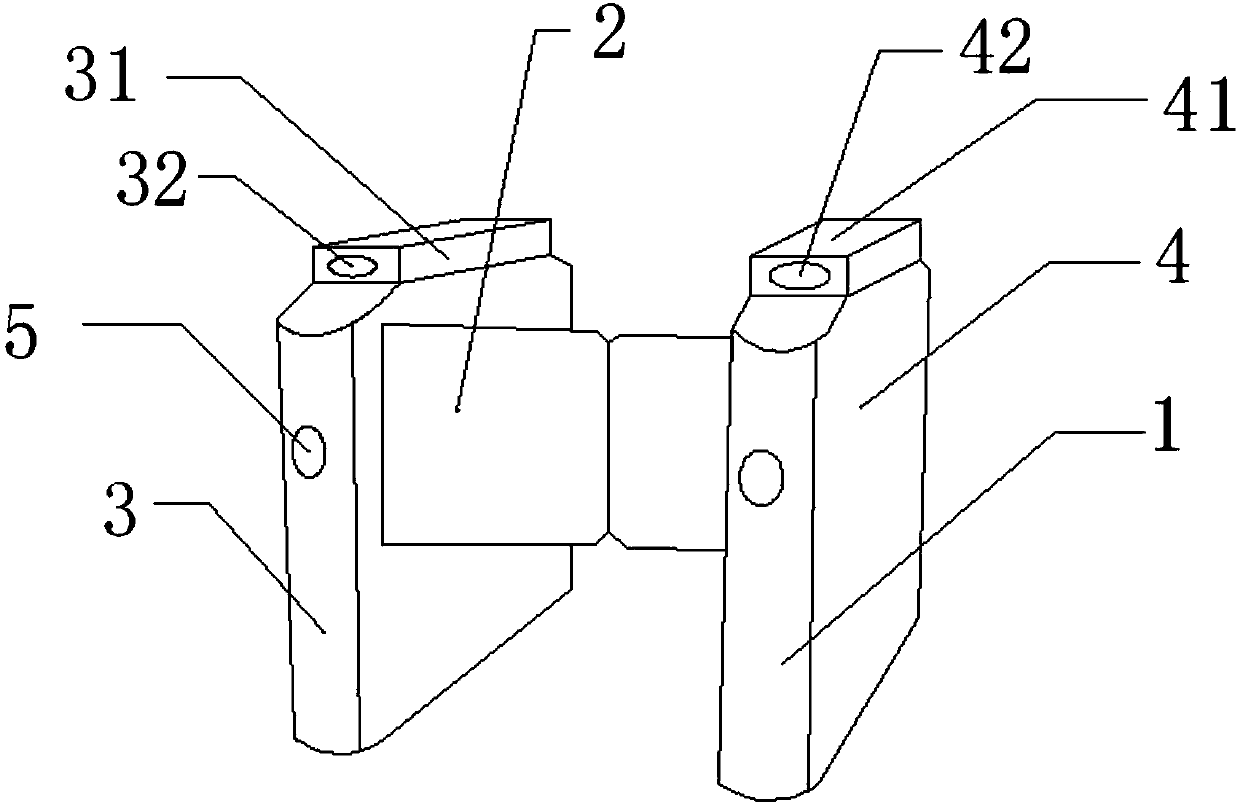
InactiveCN107293013AAutomatic door releaseSecure identityIndividual entry/exit registersTraffic restrictionsEmbedded systemIdentification device
The invention discloses an access control device triggered by approaching. The access control device comprises access control brakes and gates which are connected with each other. The access control device is characterized in that the gates are arranged on the lateral end faces of the access control brakes; indicators are arranged on the front end faces of the access control brakes; the access control brakes comprise a left access control brake and a right access control brake; the left access control brake is matched with the right access control brake; the gates which are arranged on the left access control brake and the right access control brake are oppositely mounted; a camera recognition device is arranged on an end face above the left access control brake; and a signal receiving processing device is arranged on the upper end face of the right access control brake. The left access control brake is started when a user carries no signal triggering device and the gates are opened after the user information is compared. The right access control brake is used for automatically opening the gates after the signal triggering device sends a signal to the signal receiving device and the signal is treated when the user carries the signal triggering device and is 5 meters away from the signal receiving processing device on the right access control brake.
Owner:成都智慧家信息技术有限公司
Electronic separation wall method, device and system for protecting network space security
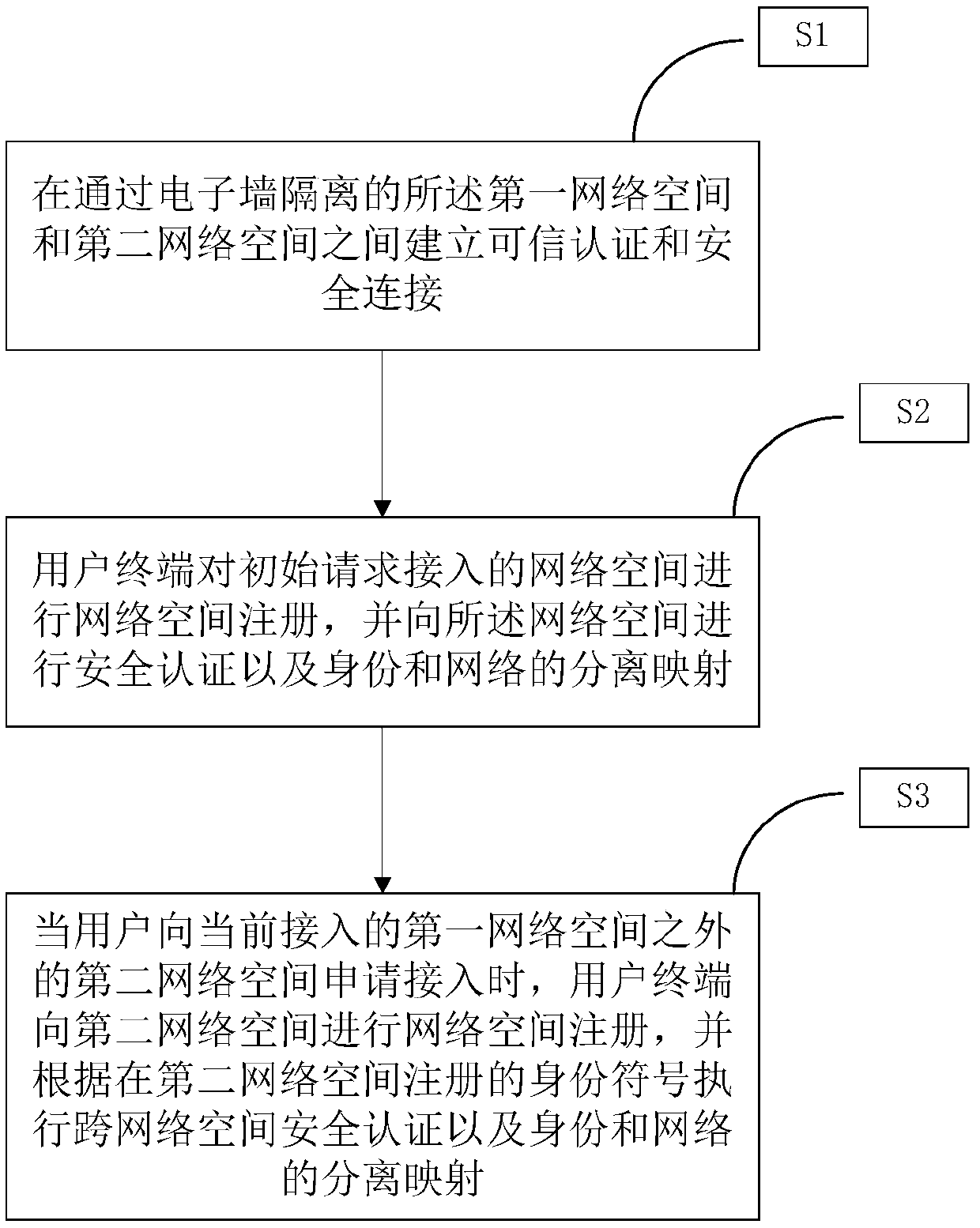
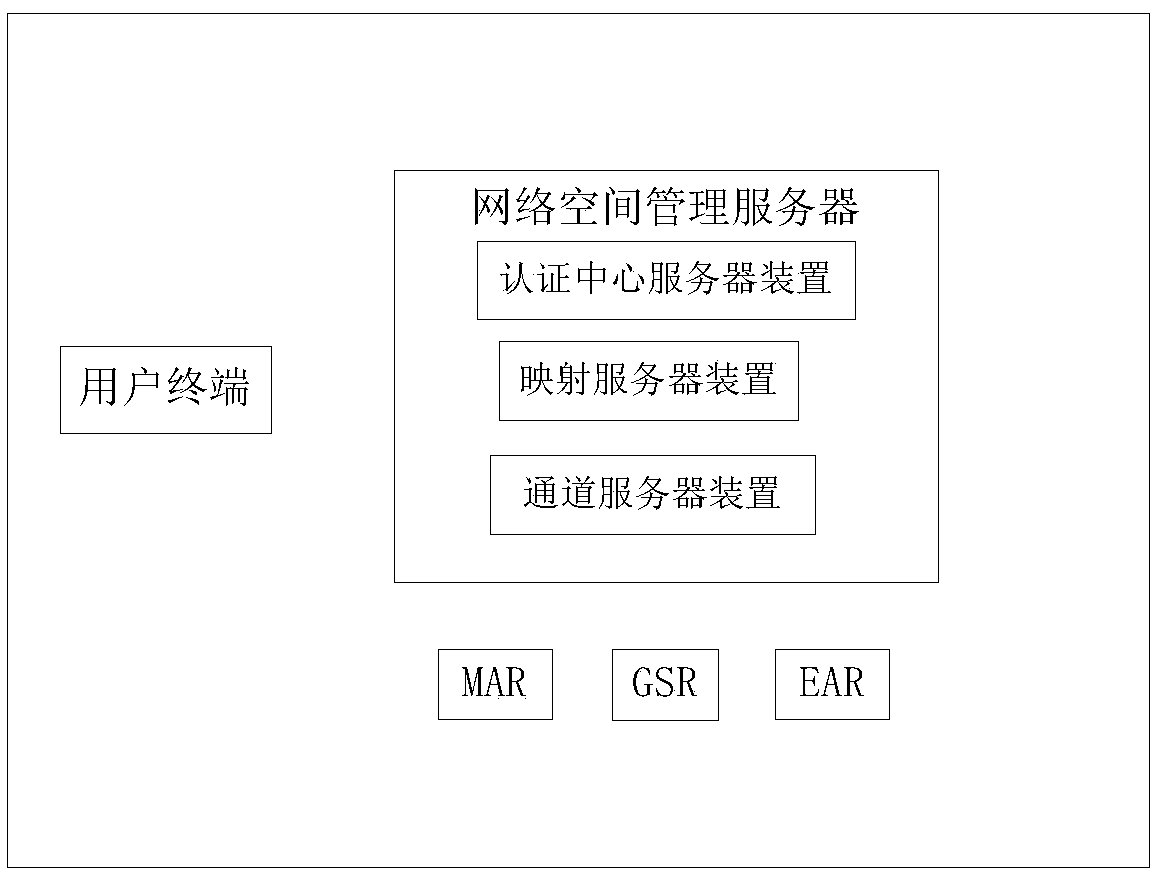
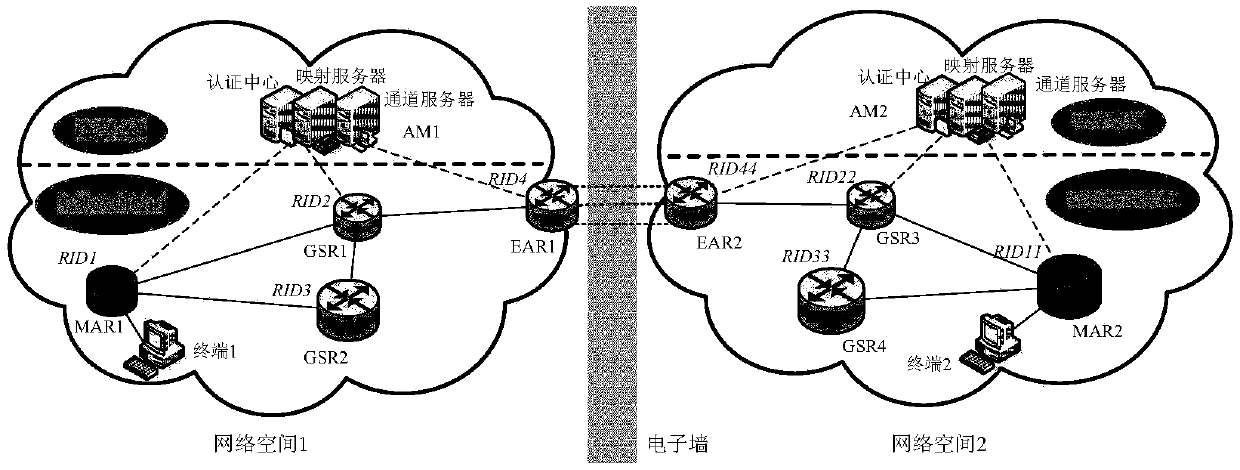
InactiveCN109547470AGuaranteed identityEnsure safetyTransmissionComputer terminalSecure authentication
The invention provides an electronic separation wall method, device and system for protecting network space security. The electronic separation wall method for protecting the network space security comprises the steps that: trusted authentication and security connection are established between a first network space and a second network space, which are separated through an electronic wall; a userterminal performs network space registration on a network space initially requested for access, and performs security authentication and identity and network separation mapping on the network space; and, when a user applies for access to the currently accessed second network space, except the first network space, the user terminal performs network space registration on the second network space, and executes cross-network space security authentication and identity and network separation mapping according to the identity symbol registered in the second network space. By means of the method, thesecurity problem of the identity, position and behaviour privacy of the user in the network space is solved.
Owner:BEIJING JIAOTONG UNIV
Campus card management system
InactiveCN108109092ASimple and reasonable designAvoid network failureData processing applicationsService systemComplete data
The invention discloses a campus card management system. The campus card management system includes a terminal service system, a cloud computing system, a campus card service terminal, a mobile client; the terminal service system and the cloud computing system can complete data interaction through a network; the cloud computing system can complete data interaction with the campus card service terminal and the mobile client through the network; the terminal service system includes an identity permission type-in module, an expense settlement module, a query module, a loss report module, a monitoring alarm module, a course information management module, a school map information module and a terminal database; the mobile client includes an authentication module, a course information module, apositioning module, a recharge module, a sign-in module, and a leave module; and NFC modules are arranged in the terminal service system and the mobile client. The campus card management system is simple and reasonable in unit design, can achieve the functions of campus consumption, authentication, course sign-in, door guard opening, course information querying, and campus internal location positioning.
Owner:NANJING INST OF TECH
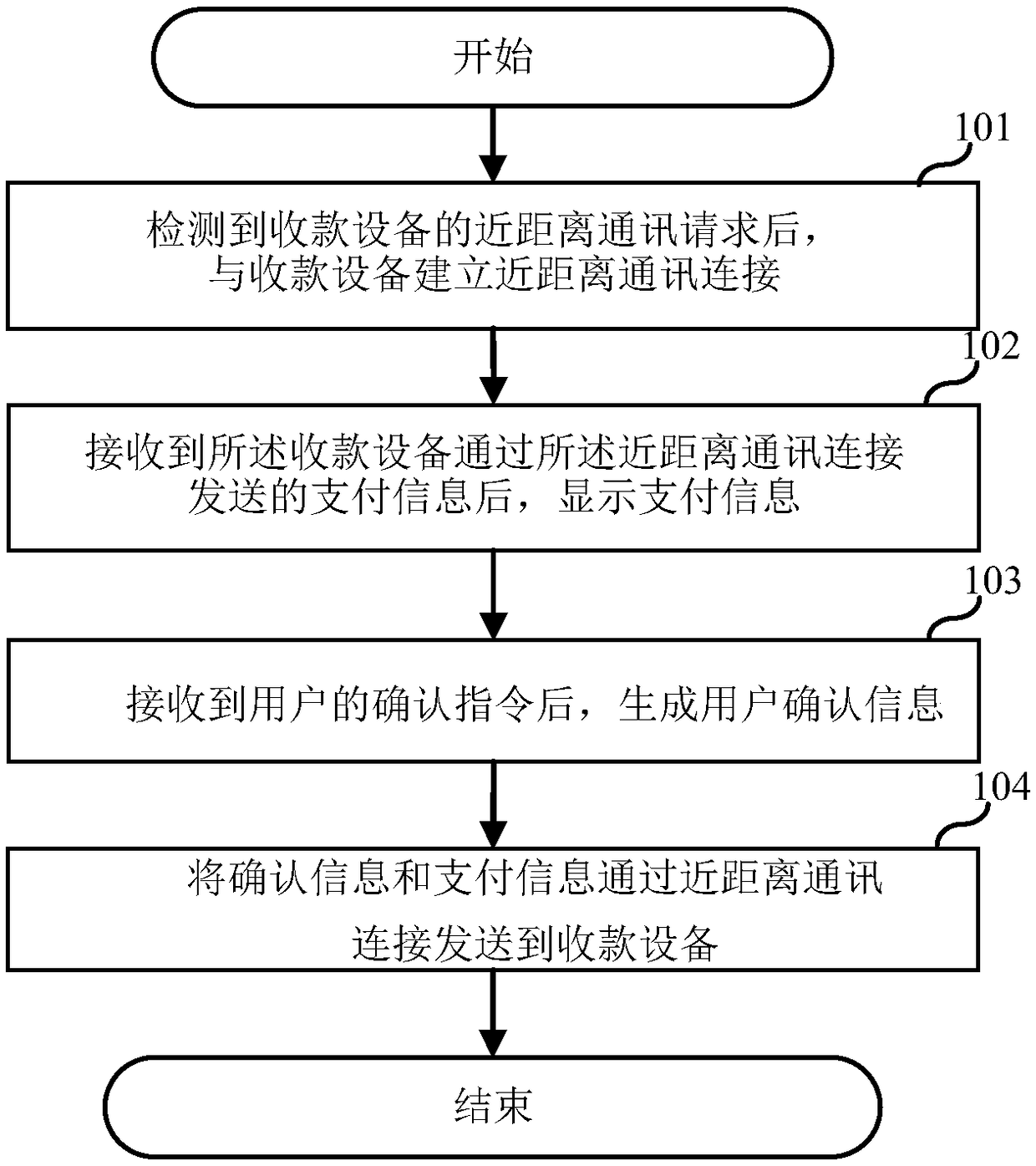
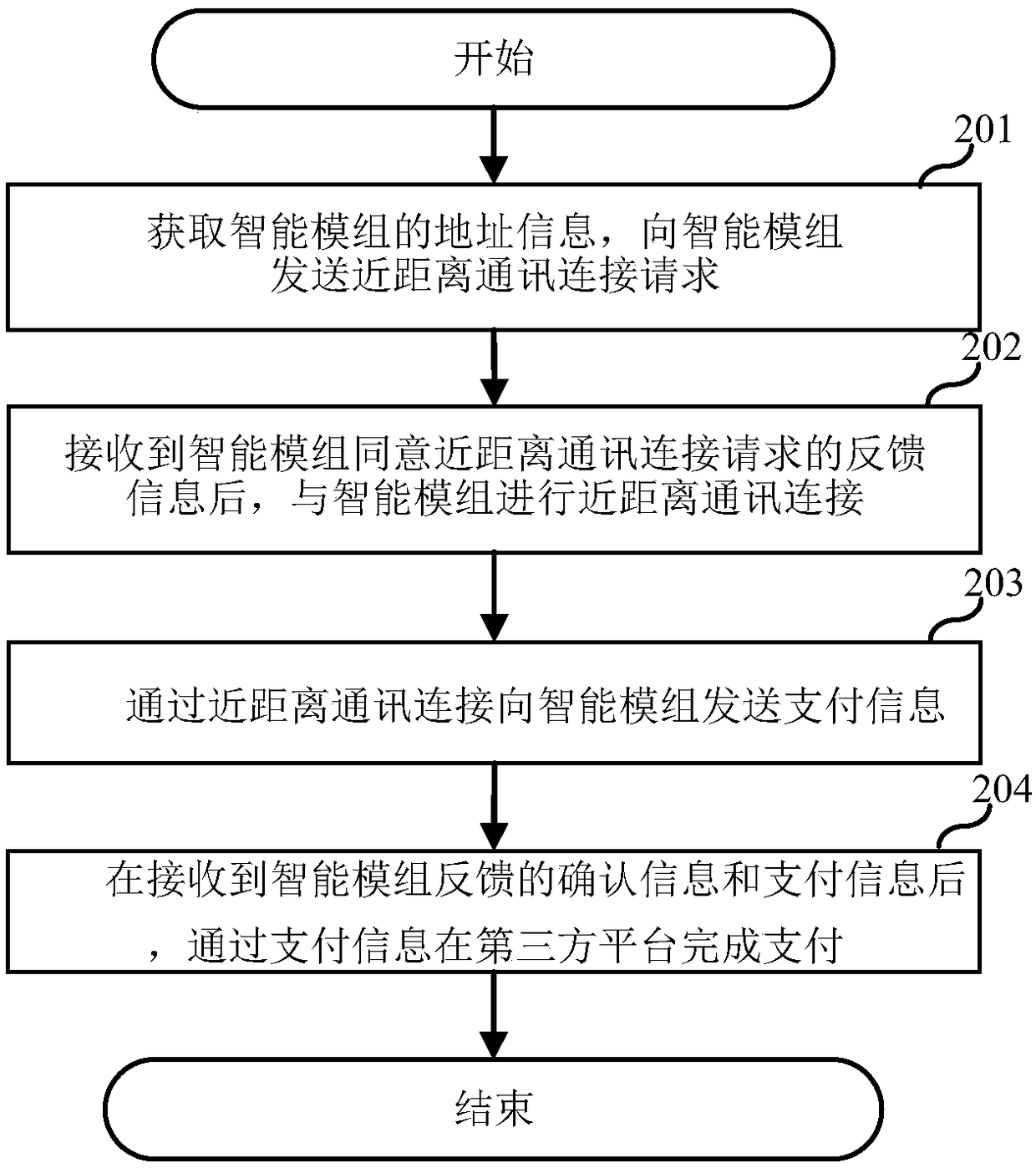
Payment method, intelligent module and collection device
The embodiment of the invention relates to the field of intelligent devices and discloses a payment method, an intelligent module and a collection device. The payment method is applied to the intelligent module, and the intelligent module is bound to payment information of a user. The payment method comprises the steps that after a near field communication request of the collection device is detected, near field communication connection with the collection device is established; after the payment information sent by the collection device through near field communication connection is received,the payment information is displayed for the user to confirm; and after a confirmation instruction of the user is received, user confirmation information is generated, and the confirmation information and the payment information are sent to the collection device through near field communication connection. In this way, the intelligent module can complete payment operation for the user when the user needs payment, and the intelligent module is simpler in structure and more convenient to carry by the user compared with existing payment devices.
Owner:SHANGHAI YUDE COMM TECH
System security infrastructure facilitating protecting against fraudulent use of individual identity credentials
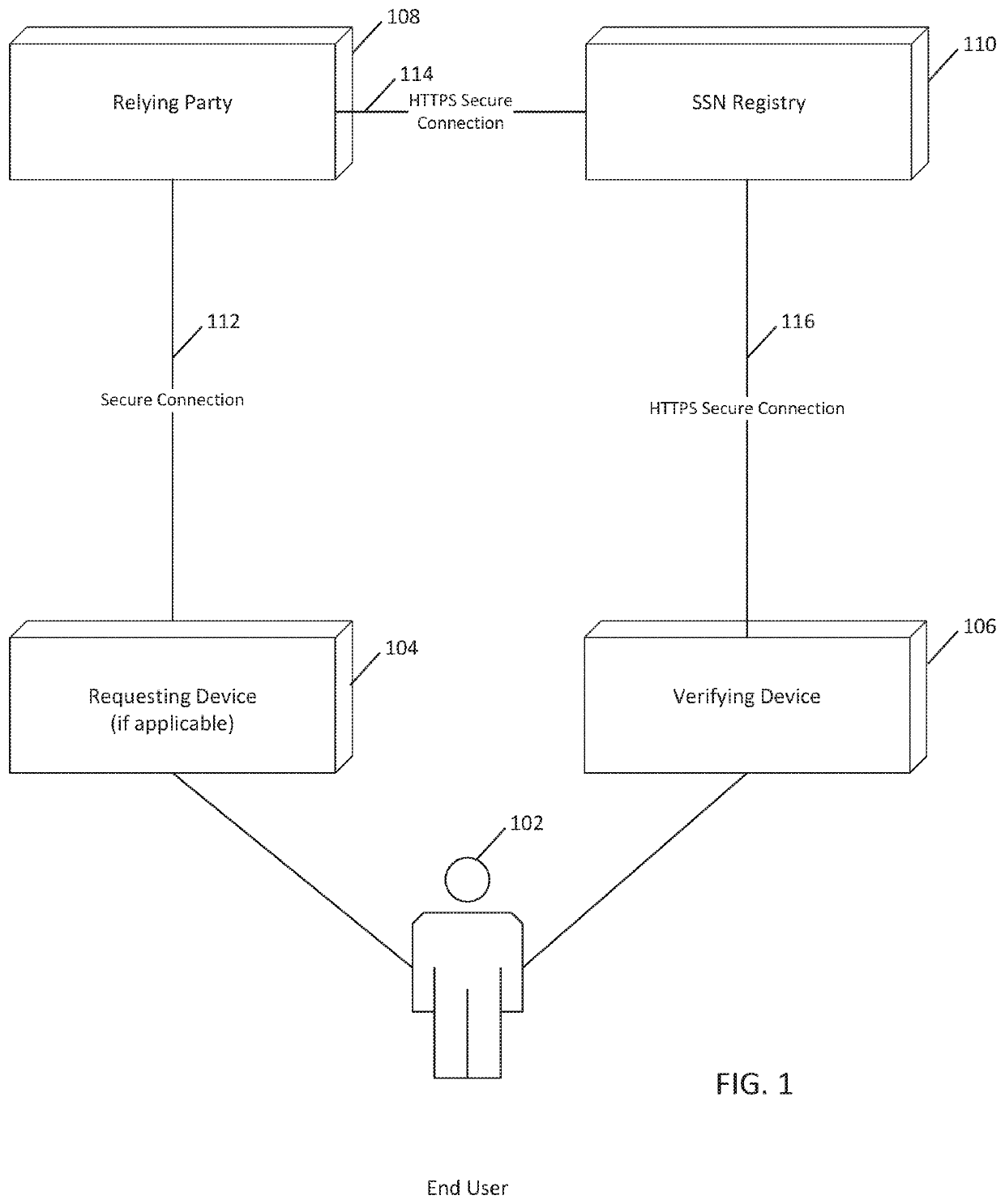
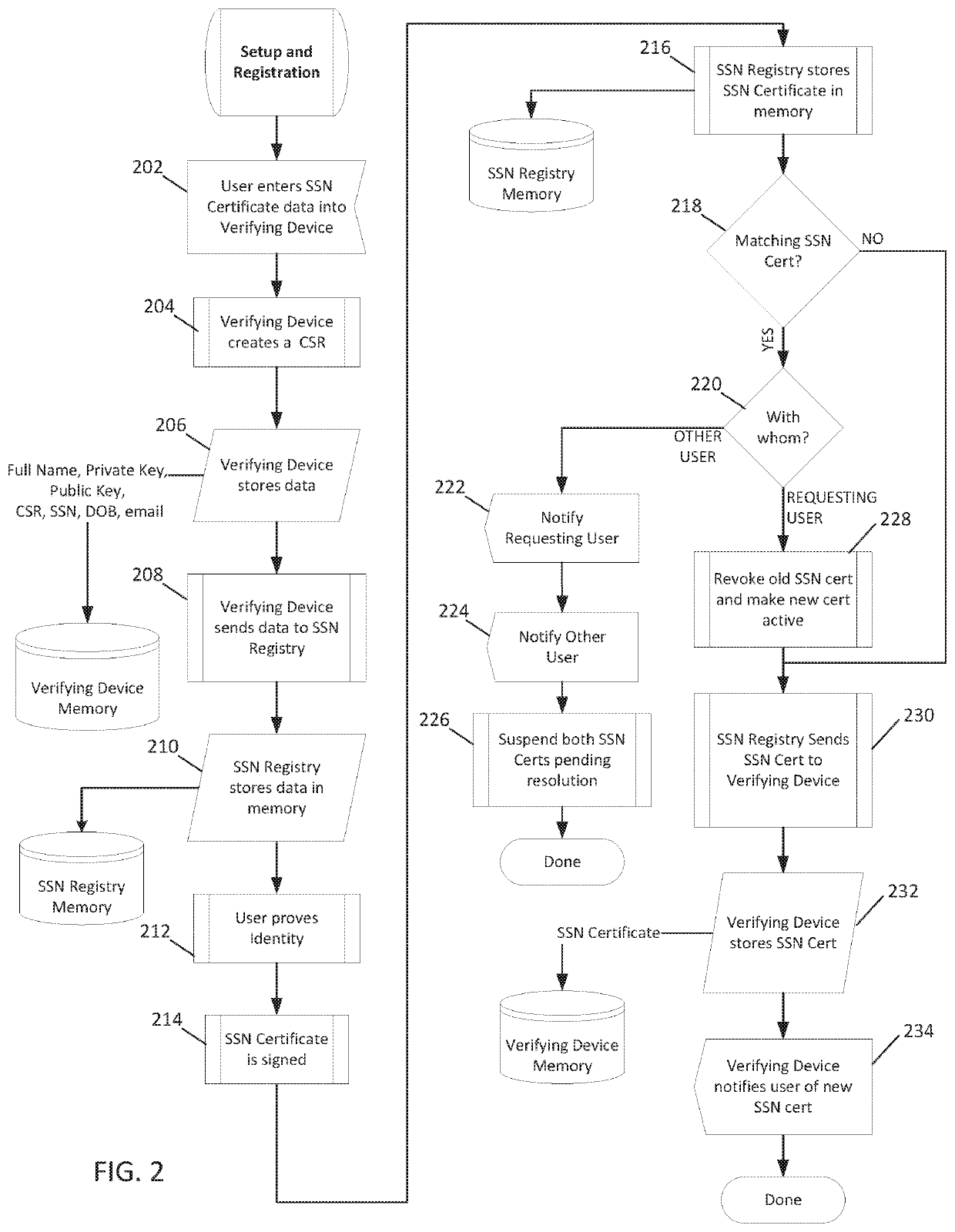
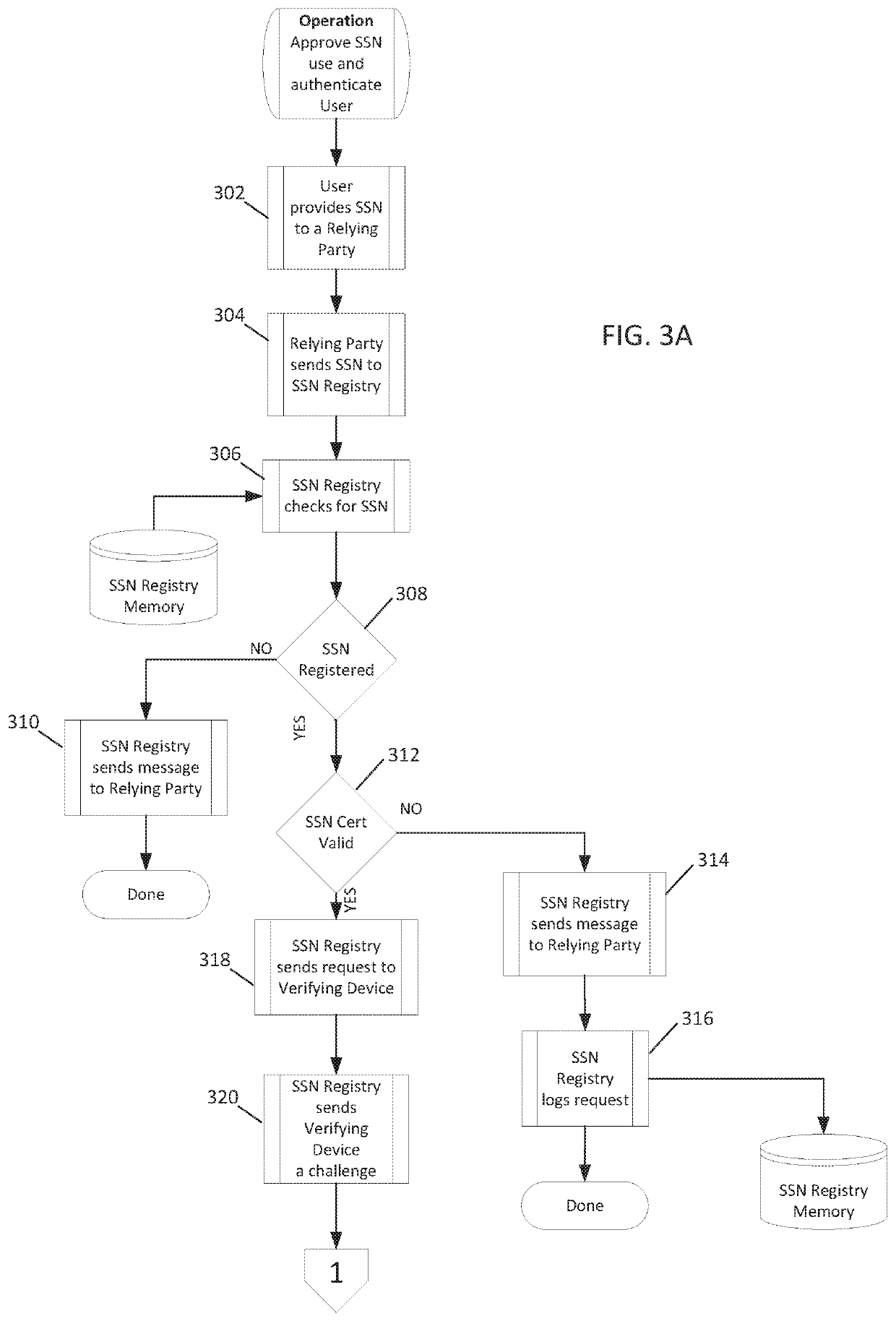
ActiveUS20200112552A1Easy to operateLimited accessDigital data authenticationData switching networksInternet privacySocial Security number
A networked infrastructure is described that includes a set of programmed computing nodes, each node being configured with a processor and non-transitory computer readable media including computer-executable instructions that, when executed by the processor, facilitate a social security number registry server carrying out a method that provides an individual with the ability to remotely approve or disapprove, in real-time, the use of his / her social security number (SSN) by a relying party server.
Owner:TACTICAL LIGHTING SYST
Intelligent monitoring and management system of library
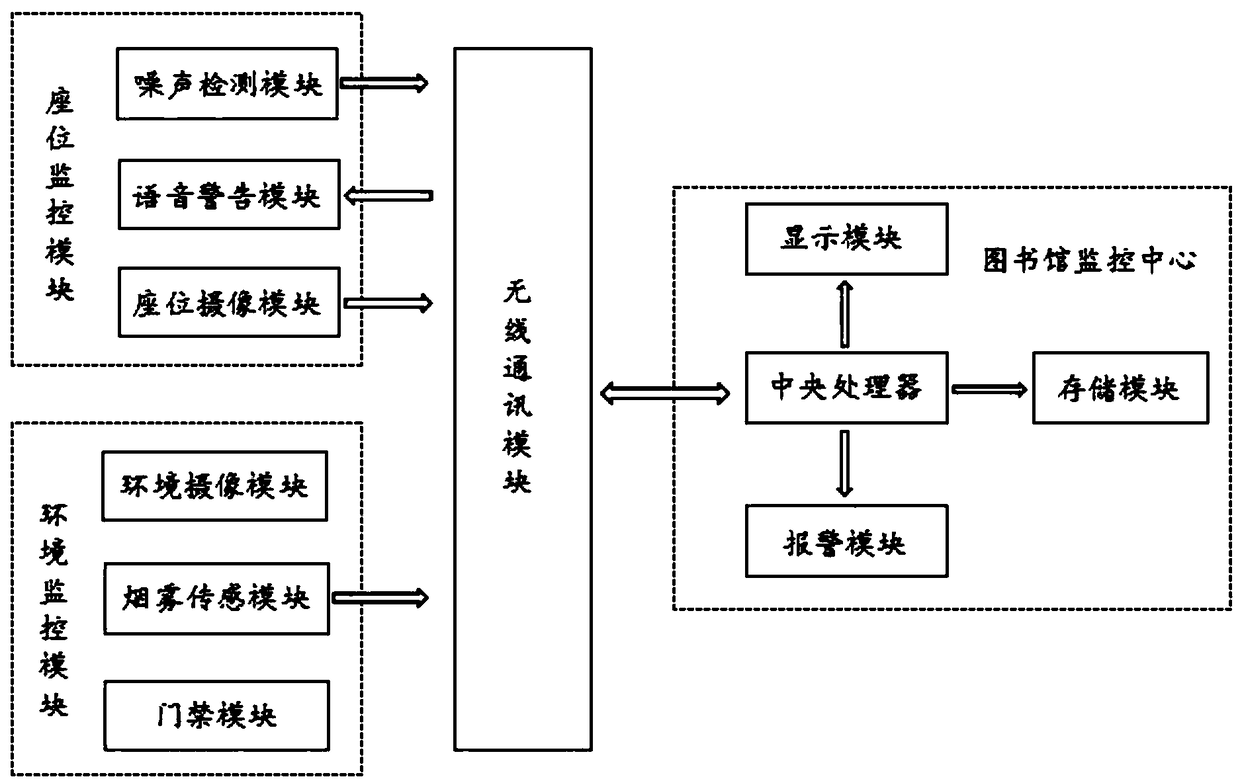
InactiveCN108549291ASimple structureGuaranteed safe operationProgramme controlComputer controlNoise detectionManagement system
Owner:安徽省久晟信息科技有限责任公司
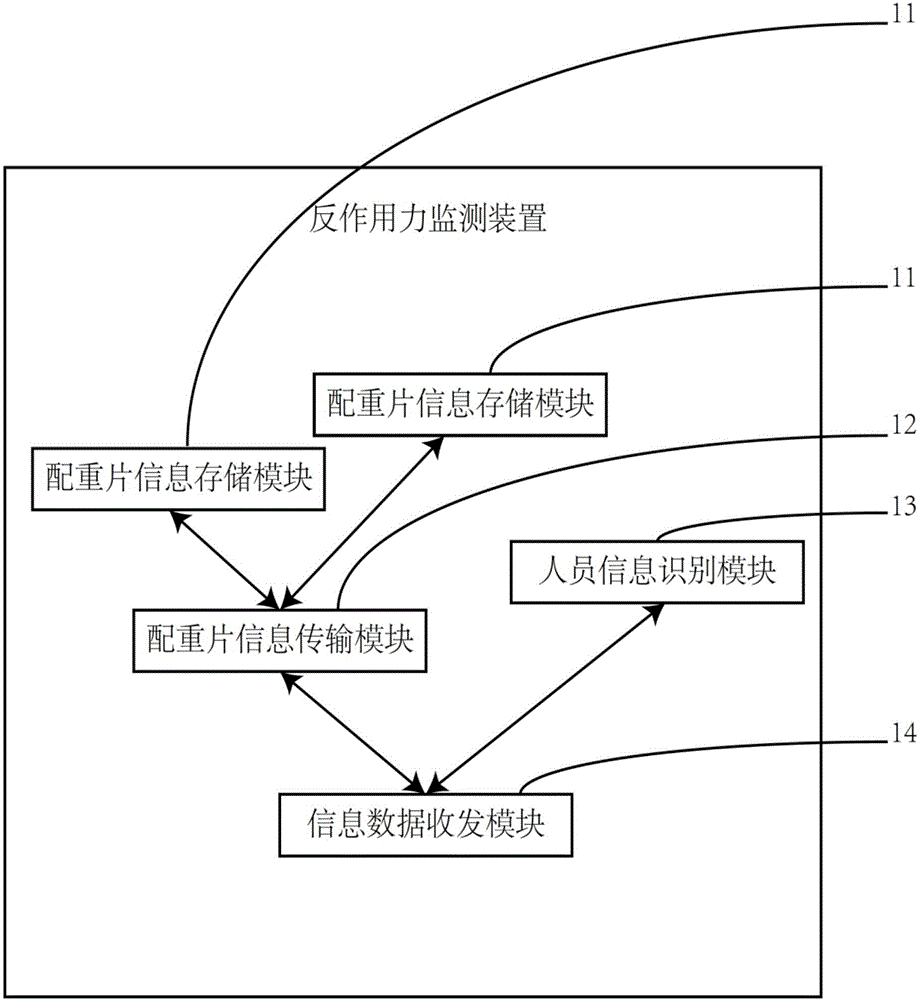
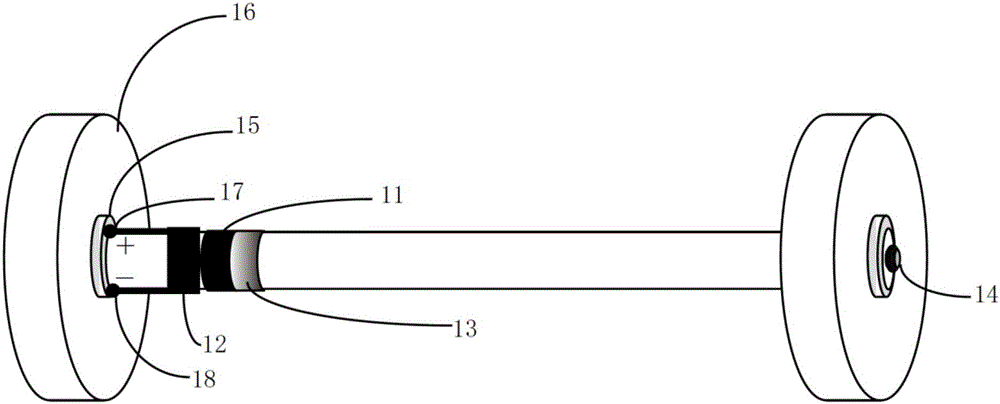
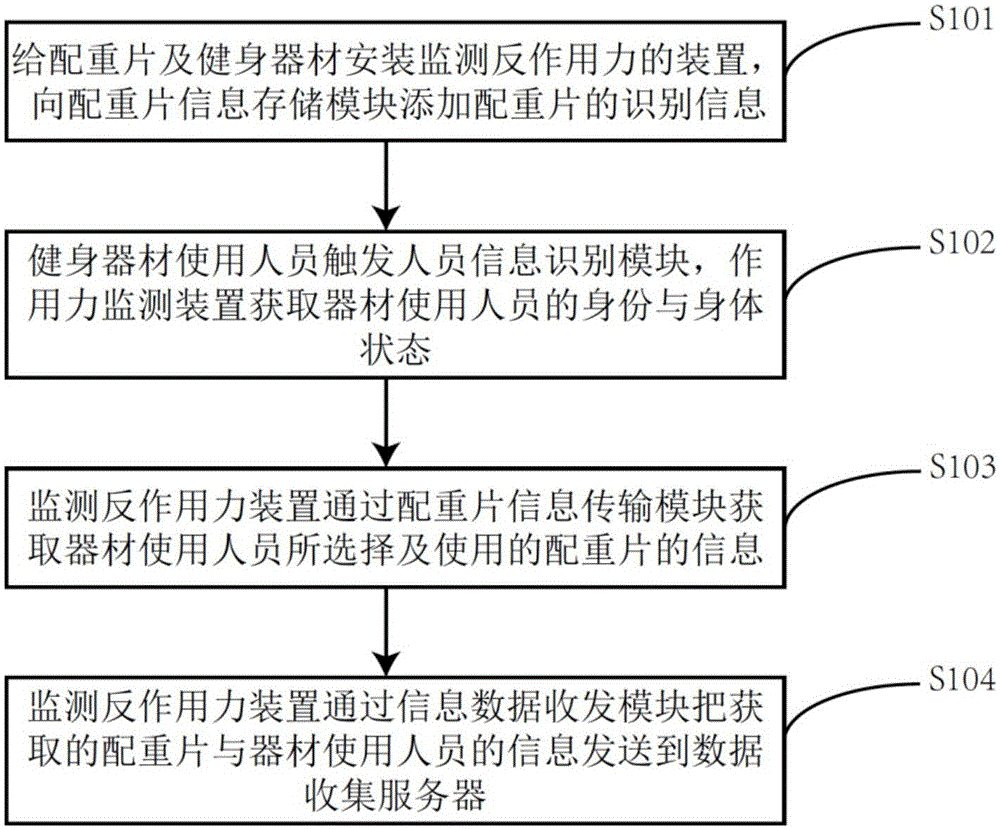
Device and method for monitoring reactive force
ActiveCN106840490AAchieve readAchieve interactionApparatus for force/torque/work measurementPersonalizationInformation transmission
The invention discloses a device and method for monitoring reactive force, belonging to the fitness equipment field. The device comprises a weight stack information storage module, a weight stack information transmission module, a personal information identification module and an information data receiving and dispatching module; by arranging the weight stack information storage module and the weight stack information transmission module in design, the storage, reading and interaction of weight, position and serial number information of the weight stack are realized; by arranging the personal information identification module in design, the purpose of carrying out individualized monitoring for fitness equipment users is realized; by arranging the information data receiving and dispatching module in design, interaction, recording and storage can be performed between the information of the weight stack and equipment users and the information of other equipment. Therefore, the device disclosed by the invention is good in safety, high in reliability and simple in use, makes a breakthrough in overcoming the technical and functional bottlenecks of existing fitness equipment, and has an excellent application prospect and market value.
Owner:SHAANXI NORMAL UNIV
Control device and method for opening and closing computer software and hardware system based on biology authentication
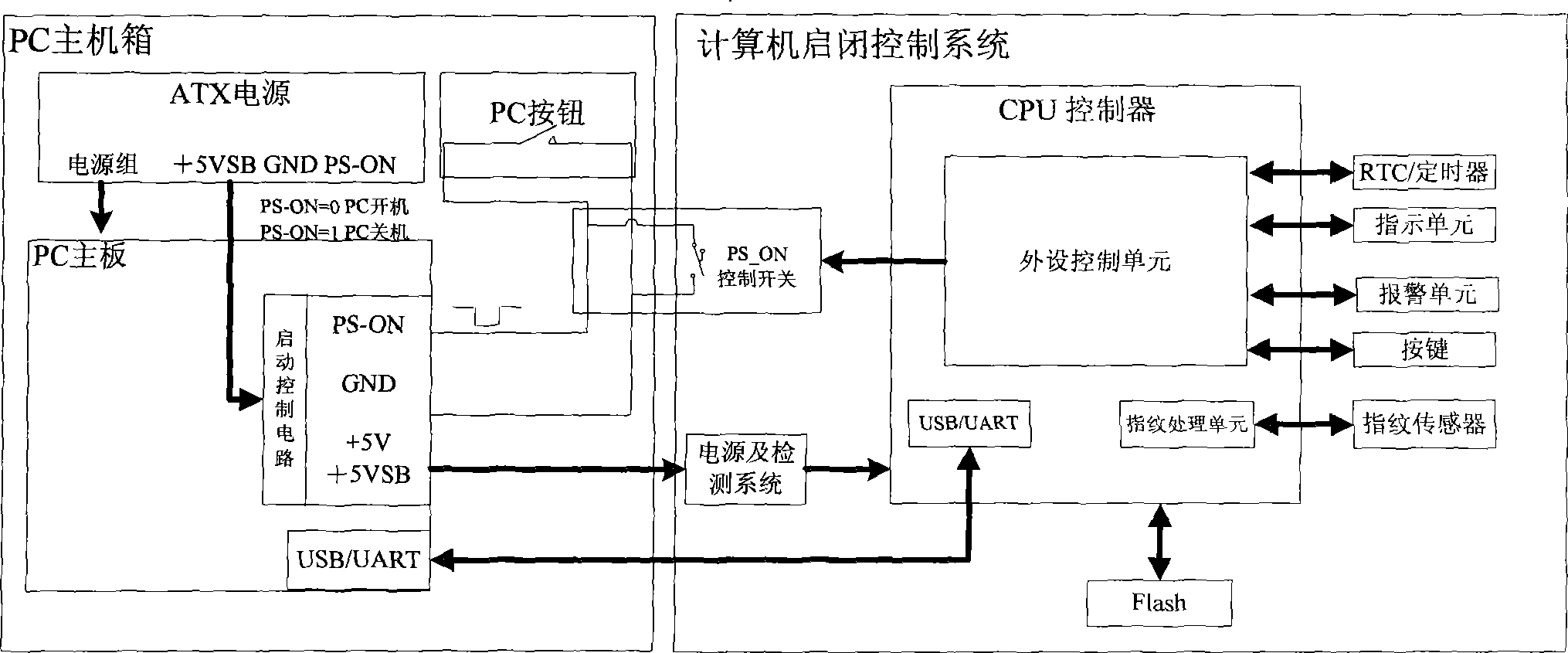
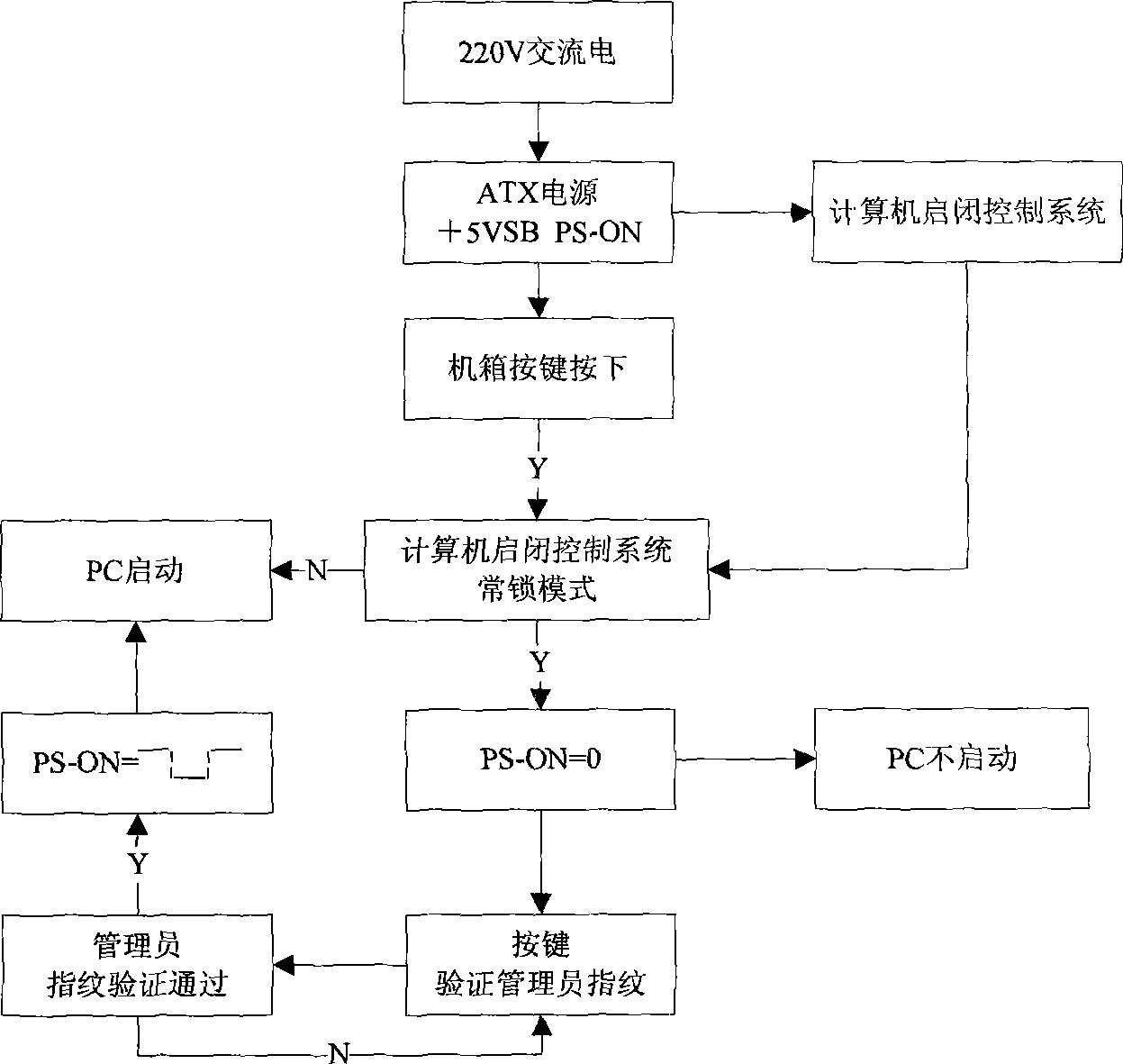
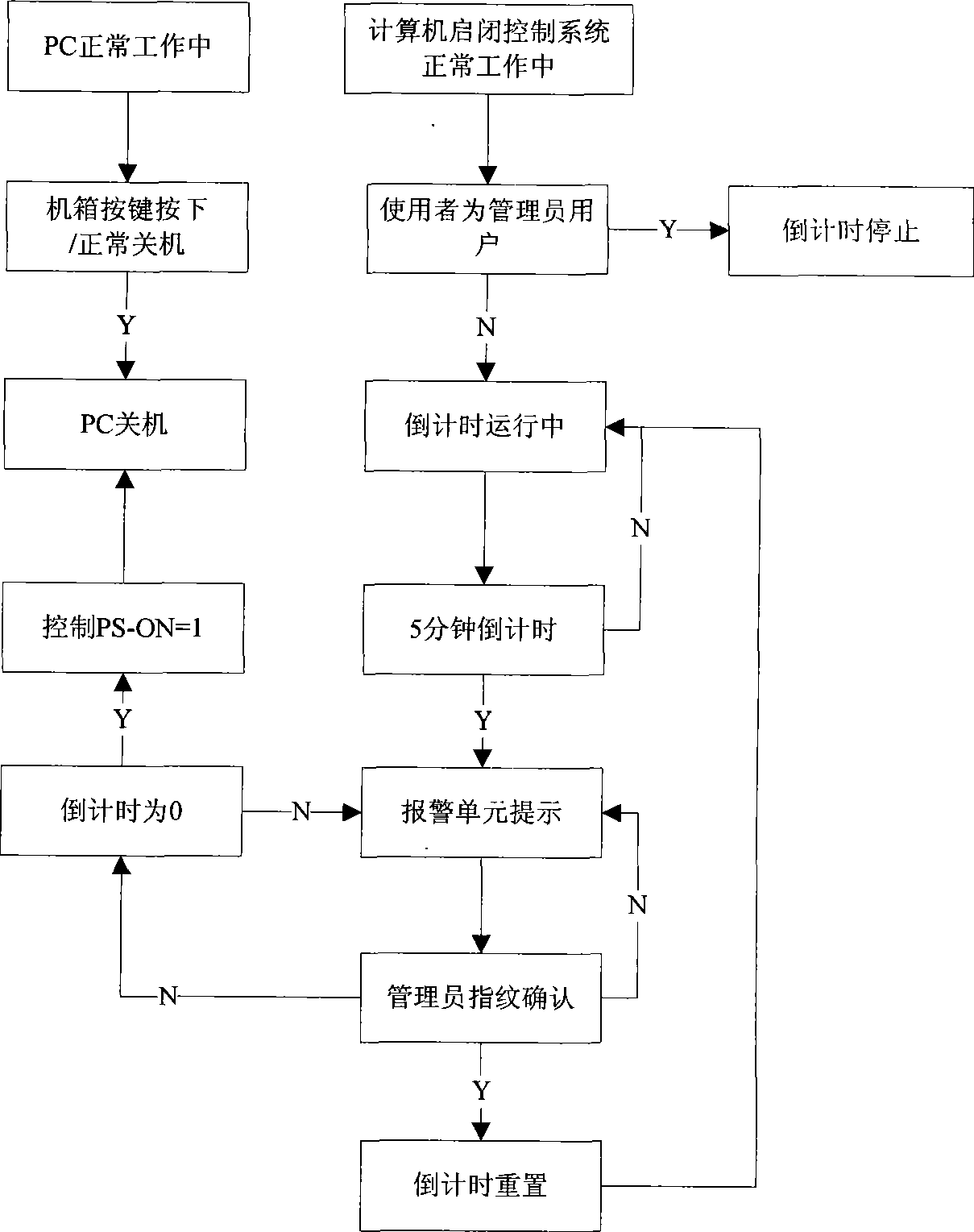
ActiveCN101382977BLoss of controlAvoid situations where the PC does not workDigital data authenticationControl systemControl cell
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
Access control device triggered in approaching modes
InactiveCN107644480AAutomatic door releaseSecure identityIndividual entry/exit registersIdentification deviceEmbedded system
The invention discloses an access control device triggered in approaching modes. The access control device comprises access control gate machines connected with gates, and is characterized by furthercomprising the gates; the gates are arranged on side end surfaces of the access control gate machines, indicator lamps are arranged on the front end surfaces of the access control gate machines, the access control gate machines include a left access control gate machine and a right access control gate machine, the left access control gate machine is matched with the right access control gate machine, the gates arranged on the left access control gate machine and the right access control gate machine are mounted in opposite directions, a photographing and recognition device is arranged on the end surface of the upper side of the left access control gate machine, and a signal receiving and processing device is arranged on the upper end surface of the right access control gate machine. The access control device has the advantages that the left access control gate machine is started when users do not carry signal triggering devices, and information of the users is compared, so that the access control device can be opened by the aid of the left access control gate machine; signals can be transmitted to a signal receiving device by the signal triggering devices when the users carry the signal triggering devices and are separated from the signal receiving and processing device on the right access control gate machine by the distances of 5 meters, and can be processed, so that the access control device can be automatically opened by the right access control gate machine.
Owner:刘俊华
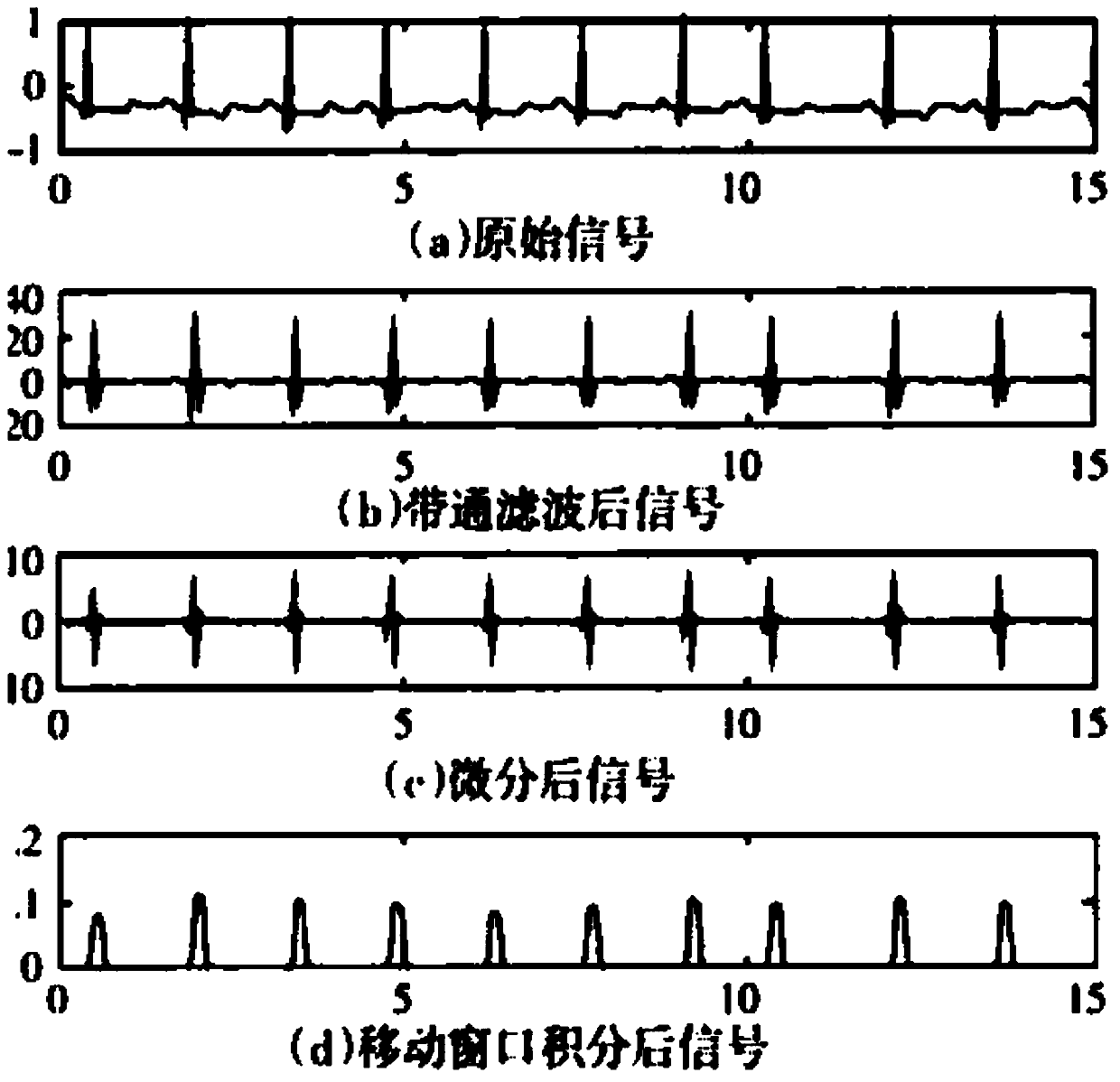
Fingerprint and electrocardio characteristic dual-authentication identity recognition system and method
PendingCN111324880ASecure identityProcessing speedDigital data authenticationDiagnostic recording/measuringMetallic electrodeIdentity recognition
The invention provides a fingerprint and electrocardio characteristic dual-authentication identity recognition system and method. The system comprises a computer host, human body electrocardio detection equipment, a fingerprint recognition module and a fingertip electrocardio detection module. The fingerprint recognition module is used for collecting fingerprint information and comprises a fingertouch recognition area and a metal electrode surrounding the finger touch recognition area, and the metal electrode is connected with the fingertip electrocardio detection module; the method comprisesthe following steps: firstly, a patient registers information on a computer host and inputs a fingerprint; then, after human body electrocardio detection equipment is installed on the body of the patient, the finger is pressed in the finger touch recognition area of the fingerprint recognition module, and the fingerprint recognition module obtains fingerprint information of the patient and compares the fingerprint information with registered fingerprint information; if it is determined that the user is the registered user, collecting finger electrocardiosignals and body electrocardiosignals,and if QRS wave group pulse sequences of the finger electrocardiosignals and the body electrocardiosignals are synchronous, passing identity authentication, and immediately conducting electrocardiograph detection through human body electrocardiograph detection equipment.
Owner:中山市连心电子科技有限公司
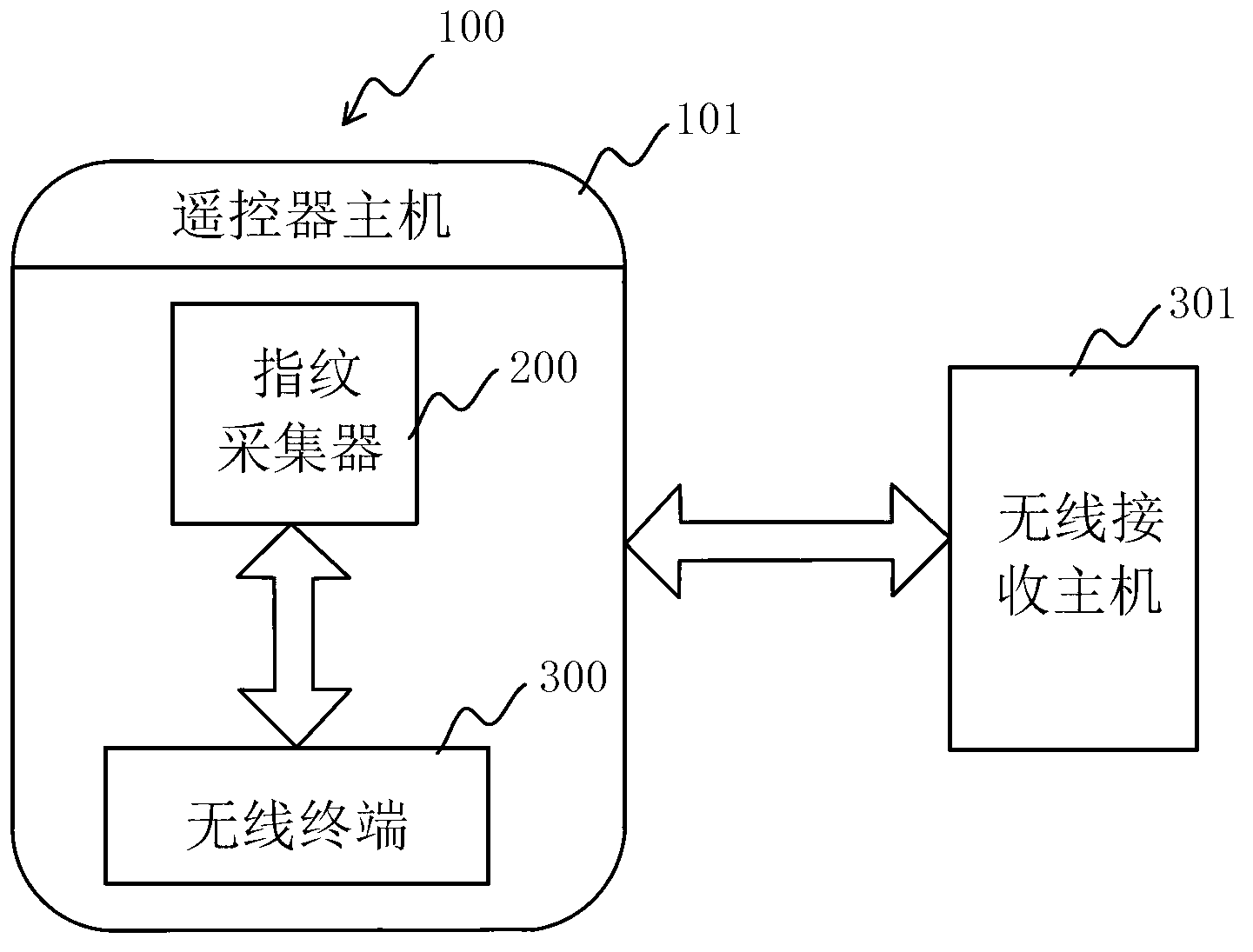
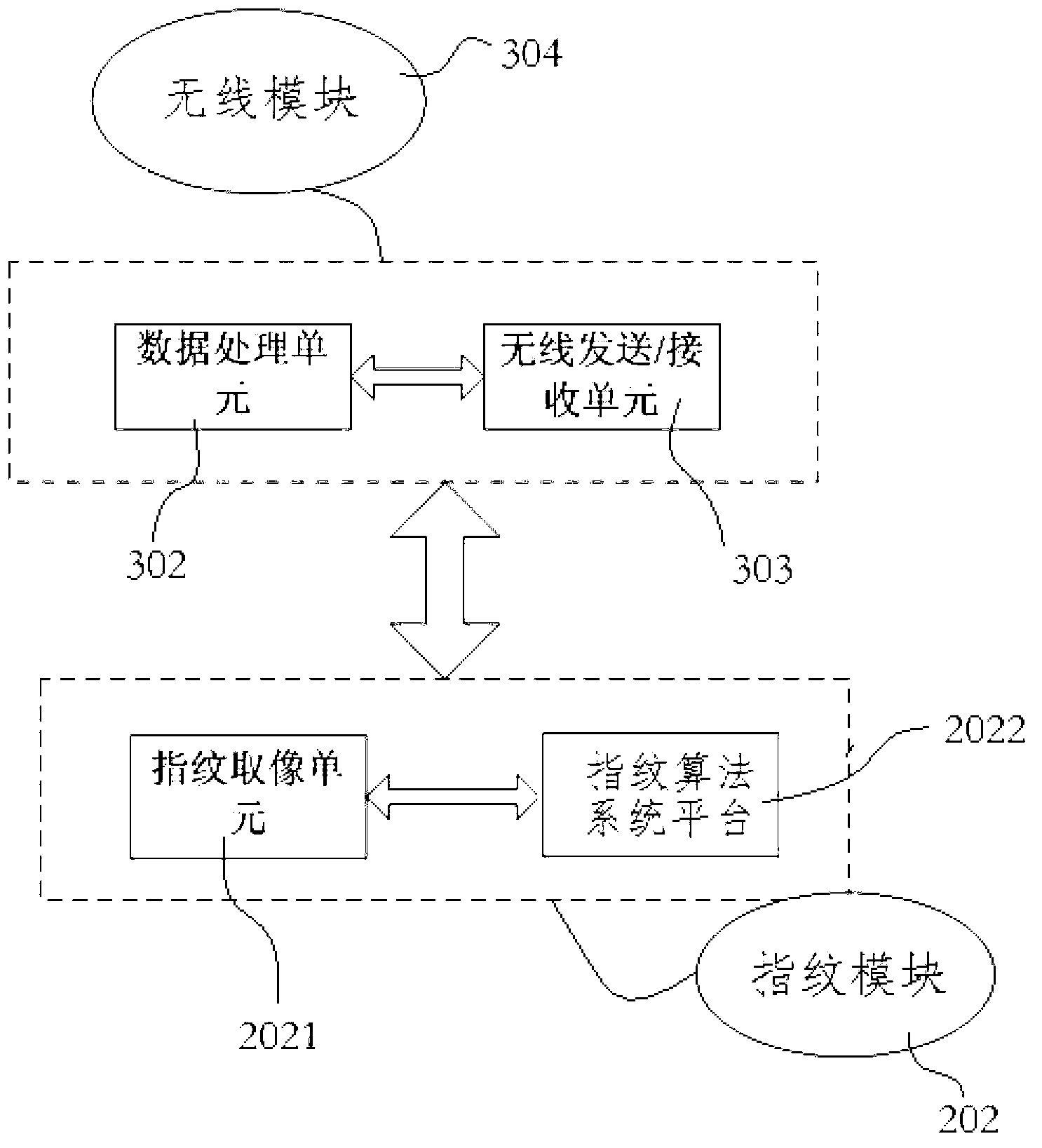
Authentication device of fingerprint remote controller
InactiveCN103236148AEasy to operateAny operationTransmission systemsCharacter and pattern recognitionWireless transmissionComputer terminal
The invention discloses an authentication device of a fingerprint remote controller. The authentication device comprises a remote controller terminal, a remote controller host arranged inside the terminal, and a fingerprint acquirer, wherein the fingerprint acquirer is connected with the remote controller host, and the data transmission is implemented between the fingerprint acquirer and the remote controller host. Since the fingerprint acquirer is arranged inside the remote controller terminal, in addition, the data transmission is implemented between the fingerprint acquirer and the remote controller host, and the wireless transmission is implemented under the combination of a wireless terminal, so that the authentication device is convenient to operate without being limited by a connecting line, and can be operated at will within a reasonable range.
Owner:AIWEIDA INTELLIGENT ELECTRONICS TECH KUNSHAN
Intelligent approaching triggered access control system
InactiveCN107195054AAutomatic door releaseSecure identityIndividual entry/exit registersMonitoring systemMedia access control
The invention discloses an intelligent approaching triggered access control system. Due to the improvement of safety awareness of people, the safety requirements of areas where people stay are further improved. The access control system is applied to various daily work and life occasions such as community, office building, government, banks, and the like, is co-used with intelligent safeguard systems such as monitoring system, alarming system, and the like, and greatly enhance the safety level for people in work and life. For some special places, such as amusement parks, senior clubs, and the like, the number of people in the places is usually limited for the safety reason; while a conventional access control system can only open / close a door and cannot control the number of people who enter the special places. The provided intelligent approaching triggered access control system can intelligently recognize a user, all data is stored in a memory device, and the identity of the user can be recognized.
Owner:成都智慧家信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com