Message safety transfer system
A transmission system and information technology, applied in the field of information security transmission system, can solve problems such as wasting time and network burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
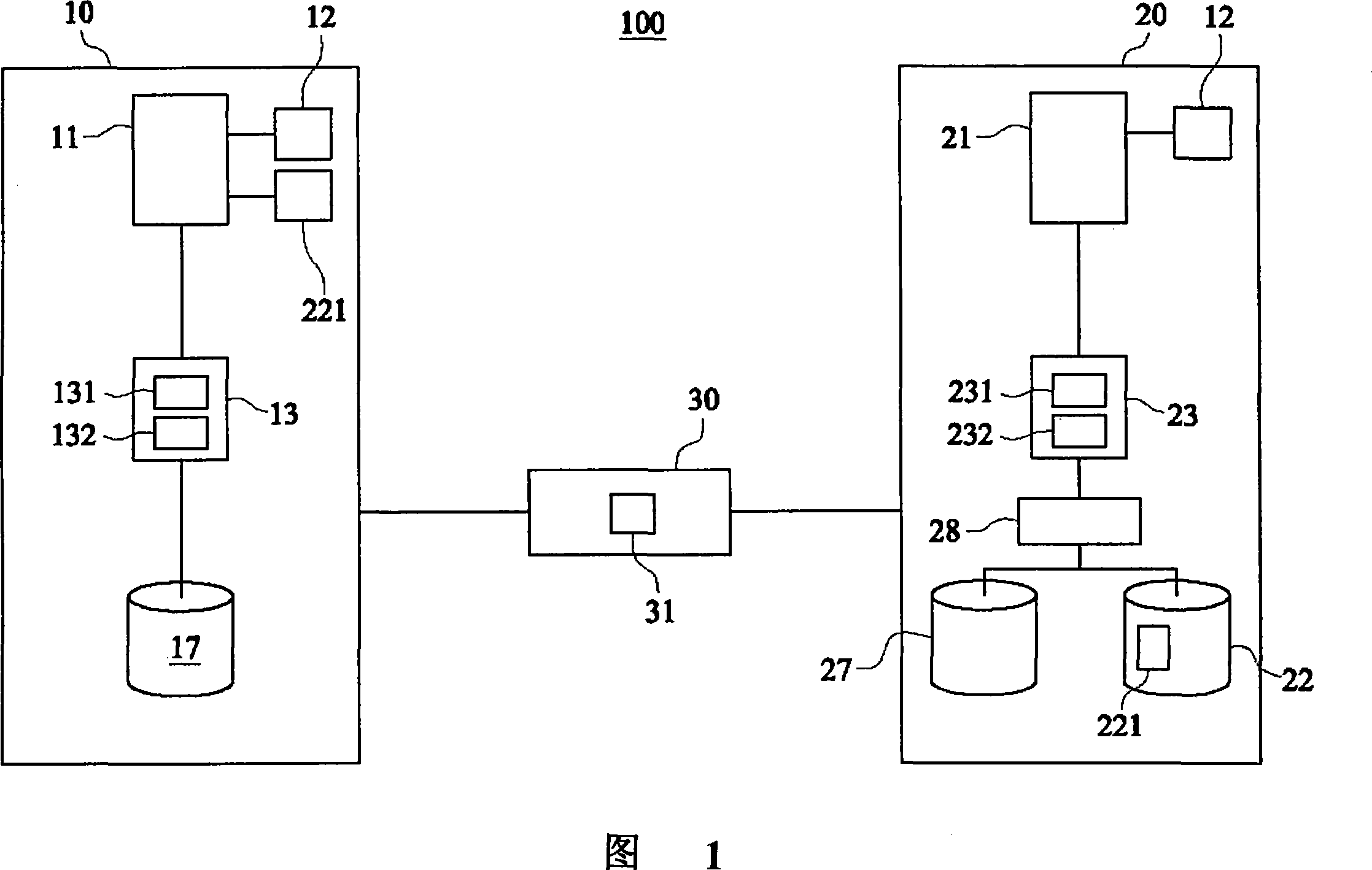
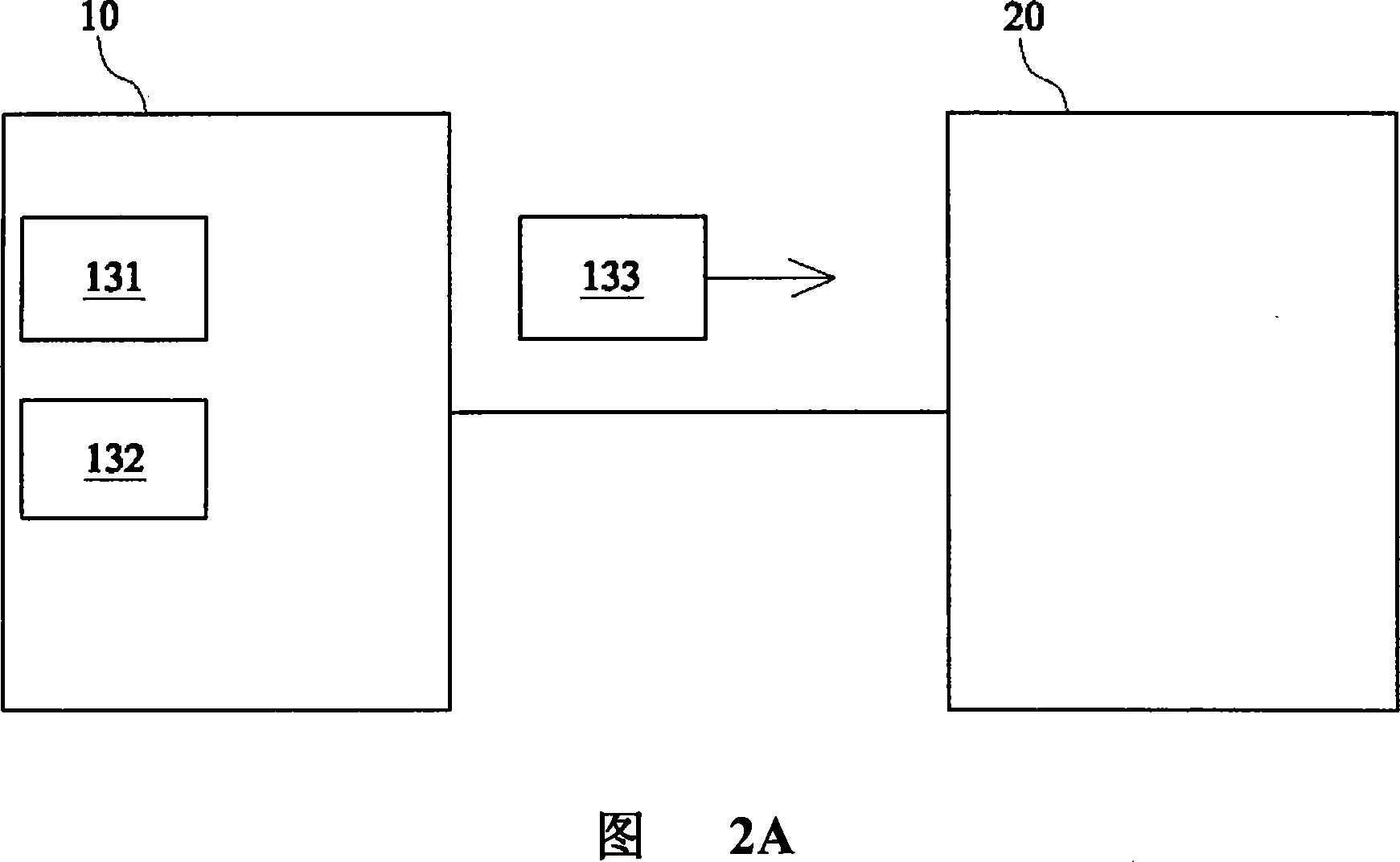
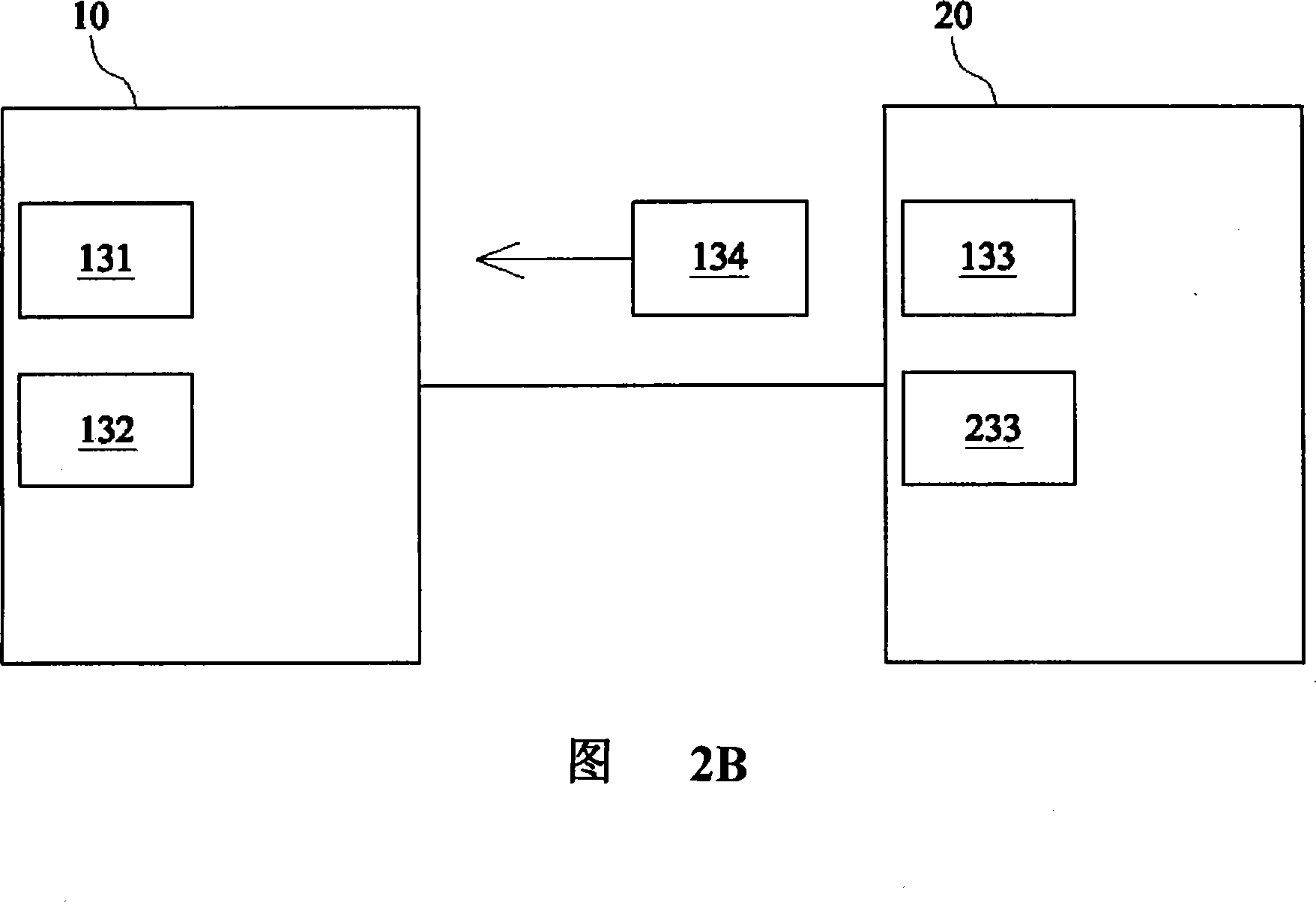
[0043] First, please refer to FIG. 1 , as shown in the figure, the information security delivery system of the present invention mainly includes a first information device 10 and a second information device 20 . The first information equipment 10 and the second information equipment 20 are connected to each other through a network 30 . The first information device 10 obtains at least one authentication data 221 and stores the authentication data 221 in the database 22 of the second information device 20 to obtain authorization. Therefore, the first information device 10 can start an information exchange procedure by obtaining the authentication data 221 . The first information device 10 includes a first key generator 13 which generates a first public key 131 and a first private key 132 arranged in pairs. The second information device 20 includes a second key generator 23 which generates a second public key 231 and a second private key 232 arranged in pairs. The first public ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com