A medical CT image secret sharing method
A CT image and secret sharing technology, applied in the field of medical information security, can solve problems such as inability to effectively protect CT image theft and tampering, weak resistance to plaintext or selective plaintext attacks, etc., to achieve resistance to plaintext attacks or selective plaintext attacks, The effect of reducing suspicion that secret information is contained
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
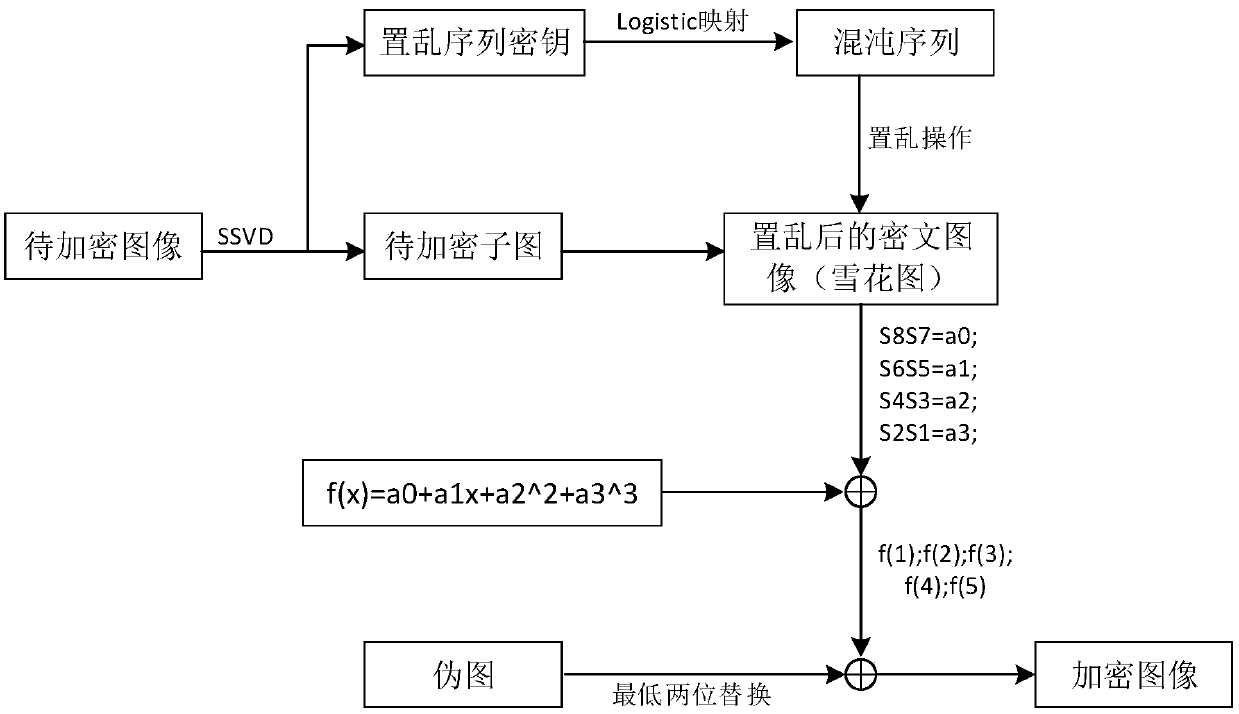
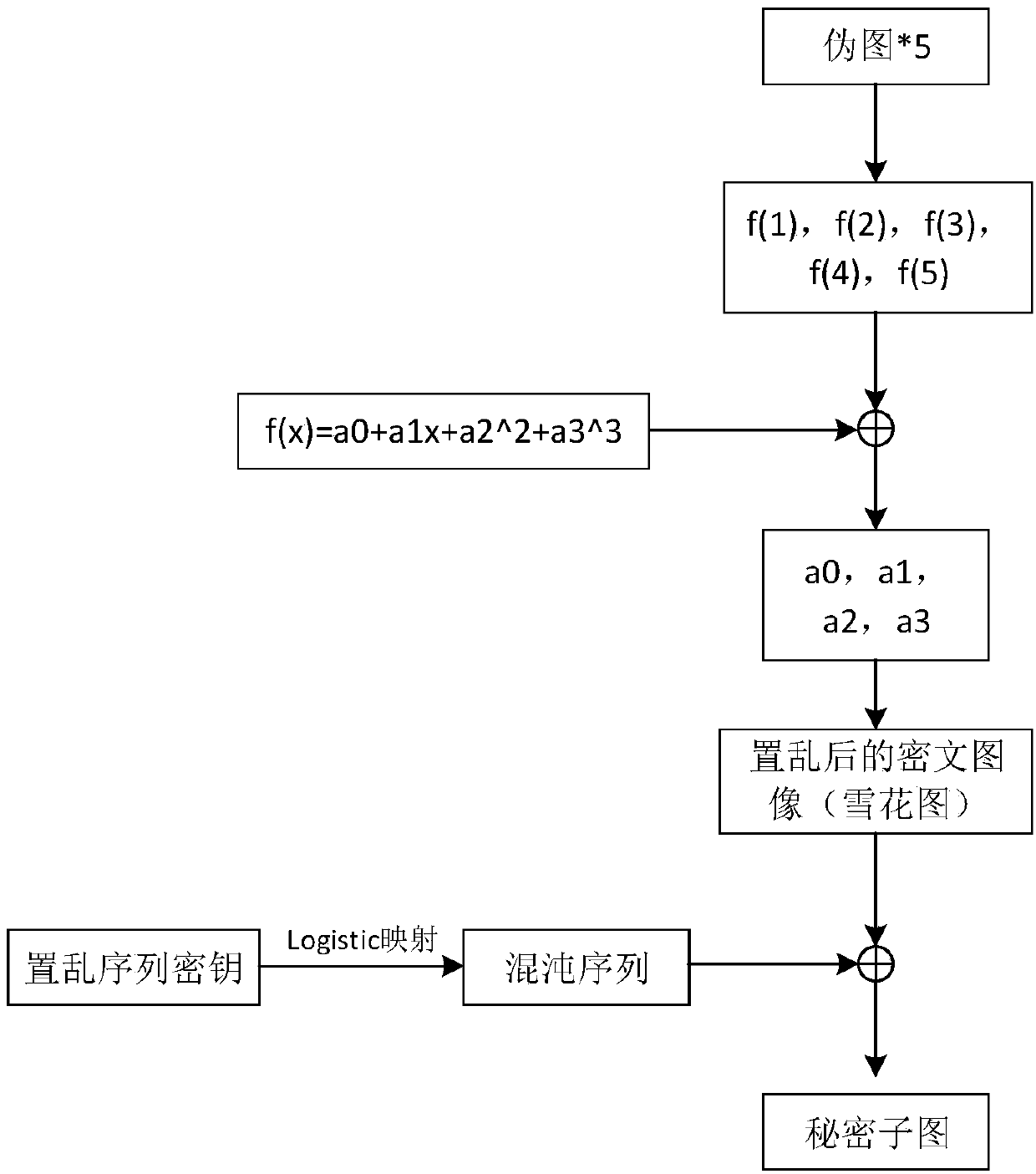
[0023] like Figure 1 to Figure 6 As shown, a method for secret sharing of medical CT images comprises the following steps:
[0024] In the encryption stage, first obtain the CT image subimage corresponding to the receiver’s permission level and a decimal matrix through sparse singular value decomposition, and then obtain the key of the two-dimensional Logistic map through the decimal matrix and use the map to generate two Chaotic sequence, scrambling the pixel positions of the CT image sub-images to obtain a snowflake image, and then dividing the snowflake image into five function value matrices by polynomials, and finally embedding the elements in the function value matrix into the camouflage image selected by the user In the lower two bits, five shadow images are obtained; in the decryption stage, the user collects five different shadow images and extracts the lower two bits of these shadow images, reorganizes the five function value matrices, and then obtains the snowflake...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com