A key negotiation method for dynamic credential authentication in wireless sensor networks
An authentication key agreement, wireless sensor technology, applied in wireless communication, key distribution, can solve problems such as inapplicability and high computational cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to better understand the present invention, the implementation process of the present invention will be described in detail below based on the above-mentioned technical solution, and the implementation scope of the present invention is a general scenario, not limited to the situation described below.
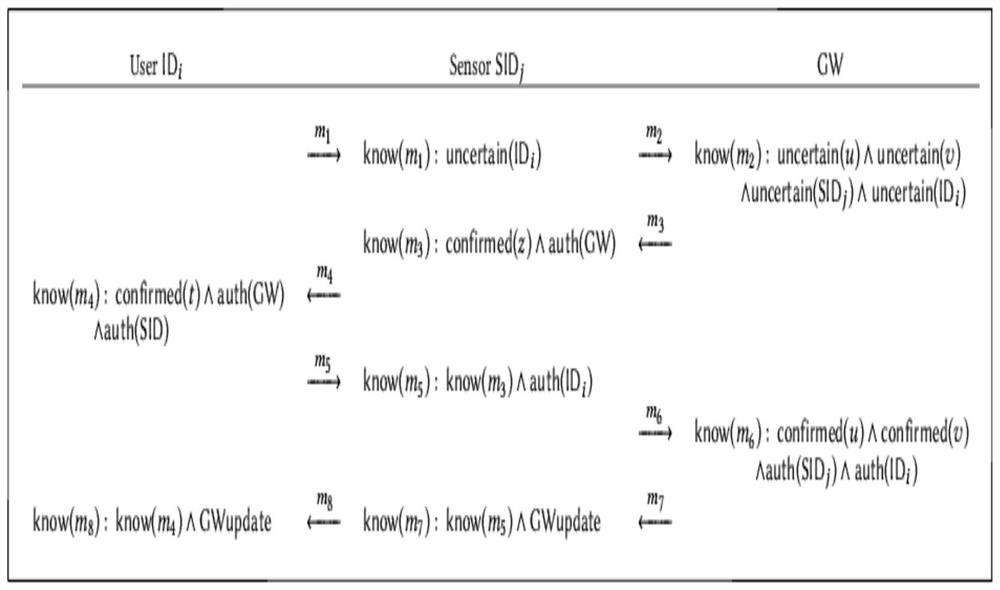
[0049] Such as figure 1 As shown, the present invention provides a novel wireless sensor network dynamic credential authentication key agreement protocol, including the following steps:
[0050] Step 1: U i (User) Select Identity ID i and long-term authentication key lk i , generate a random number r i , to calculate the median lp i =h(r i ||lk i ), summarizing user confidential information m rg Send to GW.
[0051] Step 2: GW chooses a random number r i ' and rk GW , calculate pseudonym TI i =h(r' i ||ID i ) with dynamic authentication credentials ss i,t :=h(TI i ||rk GW ||t), save the confidential information to GW, and save the smart card conte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com