A kind of car sharing method and car key
A car key, car sharing technology, applied in vehicle parts, anti-theft vehicle accessories, transportation and packaging, etc., can solve the problems of complex transformation process and high cost, and achieve the effect of avoiding transformation process and saving transformation cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
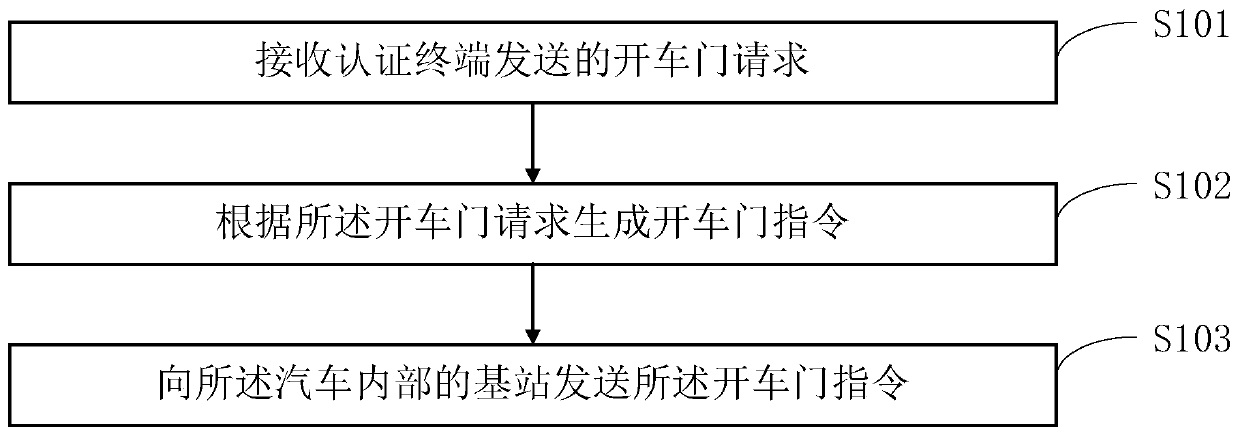
[0058] Such as figure 1 As shown, one embodiment of the present invention provides a car sharing method, which is implemented based on a car key placed in a car start keyhole inside the car.
[0059] In specific applications, the car key can be implemented on the basis of the current common car RKE (Remote Keyless Entry) key or PKE (Passive Keyless Enter, keyless entry system) key, as long as the existing RKE The key or the PKE key can be realized by adding a wireless communication module that can establish a wireless communication connection relationship with the external terminal, and has the function of verifying the legality of the identity of the external terminal. The car door can be opened by receiving the door opening request through the car key, so that any user can open the car door by sending a door opening request to the car key through an authentication terminal without the car key, so as to realize the car sharing function .
[0060]In a specific application, t...
Embodiment 2
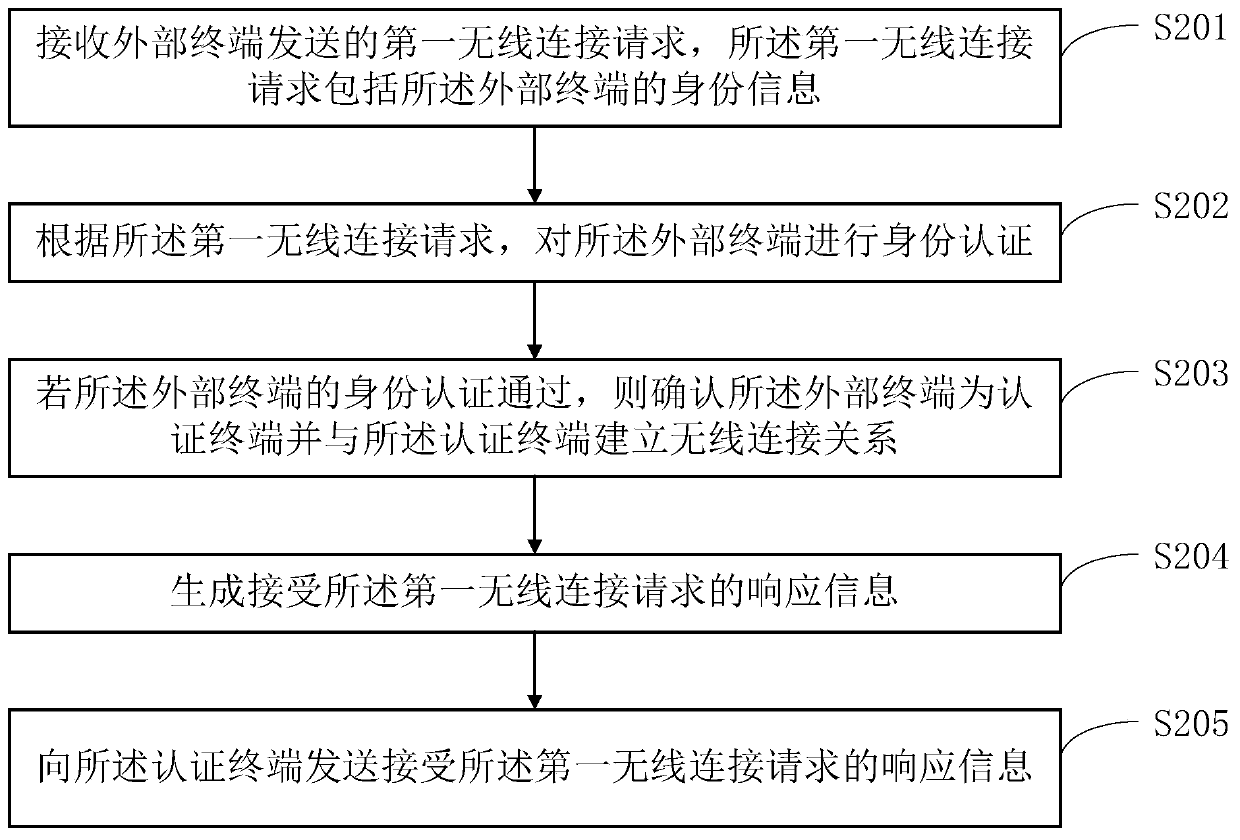
[0097] Such as figure 2 As shown, in one embodiment of the present invention, before step S101 in the first embodiment, it includes:
[0098] Step S201: Receive a first wireless connection request sent by an external terminal, where the first wireless connection request includes identity information of the external terminal.
[0099] In a specific application, the first wireless connection request may specifically be a Bluetooth connection request, which is used to request to establish a wireless connection relationship with the car key.
[0100] In a specific application, the identity verification information of the external terminal may specifically include legal account information registered in advance by the holder of the external terminal to control the car. The legal account information includes user name, user password, device information of the external terminal, etc. , may also include personal information such as the user's real name, certificate number, date of b...
Embodiment 3
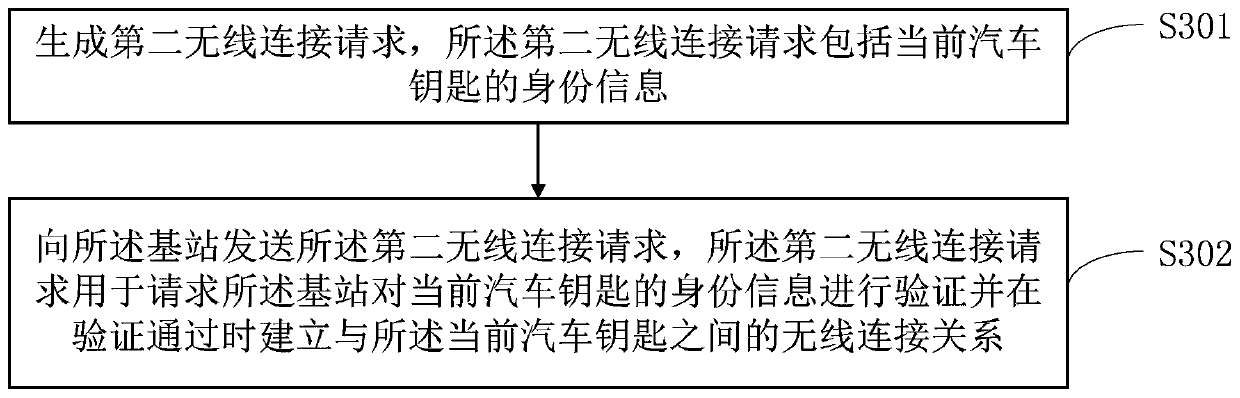
[0113] Such as image 3 As shown, in one embodiment of the present invention, before step S103 in the first embodiment, it includes:
[0114] Step S301: Generate a second wireless connection request, where the second wireless connection request includes the identity information of the current car key.
[0115] In a specific application, the second wireless connection request specifically refers to a radio frequency connection request, which is used to request to establish a radio frequency connection relationship with the vehicle body base station. To realize the communication connection relationship of data transmission.
[0116] In a specific application, the identity verification information of the car key may specifically include a unique device identification or identification code of the car key, and the unique device identification or identification code is unique.
[0117] Step S302: Send the second wireless connection request to the base station, the second wireless...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com