Integrity checking method during kernel running anda computer readable storage medium
A technology for integrity verification and storage media, applied in the field of integrity verification when the kernel is running, and computer-readable storage media, can solve problems such as inability to ensure security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0078] Please refer to figure 2 , Embodiment one of the present invention is: a kind of integrity verification method based on trustzone kernel runtime; This method is based on the following conditions: (1) have trustzone hardware architecture; Run a safe operating system, instead of running a common operating system (such as linux / android or other operating systems) in a non-safe area, that is, the object that this method needs to protect; (3) all image data have passed static integrity before running Verification, where trusted boot technology is used for verification. Otherwise, it is meaningless to perform a runtime integrity check on a kernel that has been injected with malicious programs.
[0079] The sequence of the entire static integrity check is: trusted root program -> first level loader -> safe operating system program -> second level loader -> non-safety operating system program. The direction of the arrow indicates the sequence in which the software components...
Embodiment 2
[0098] This embodiment is a further extension of Embodiment 1.
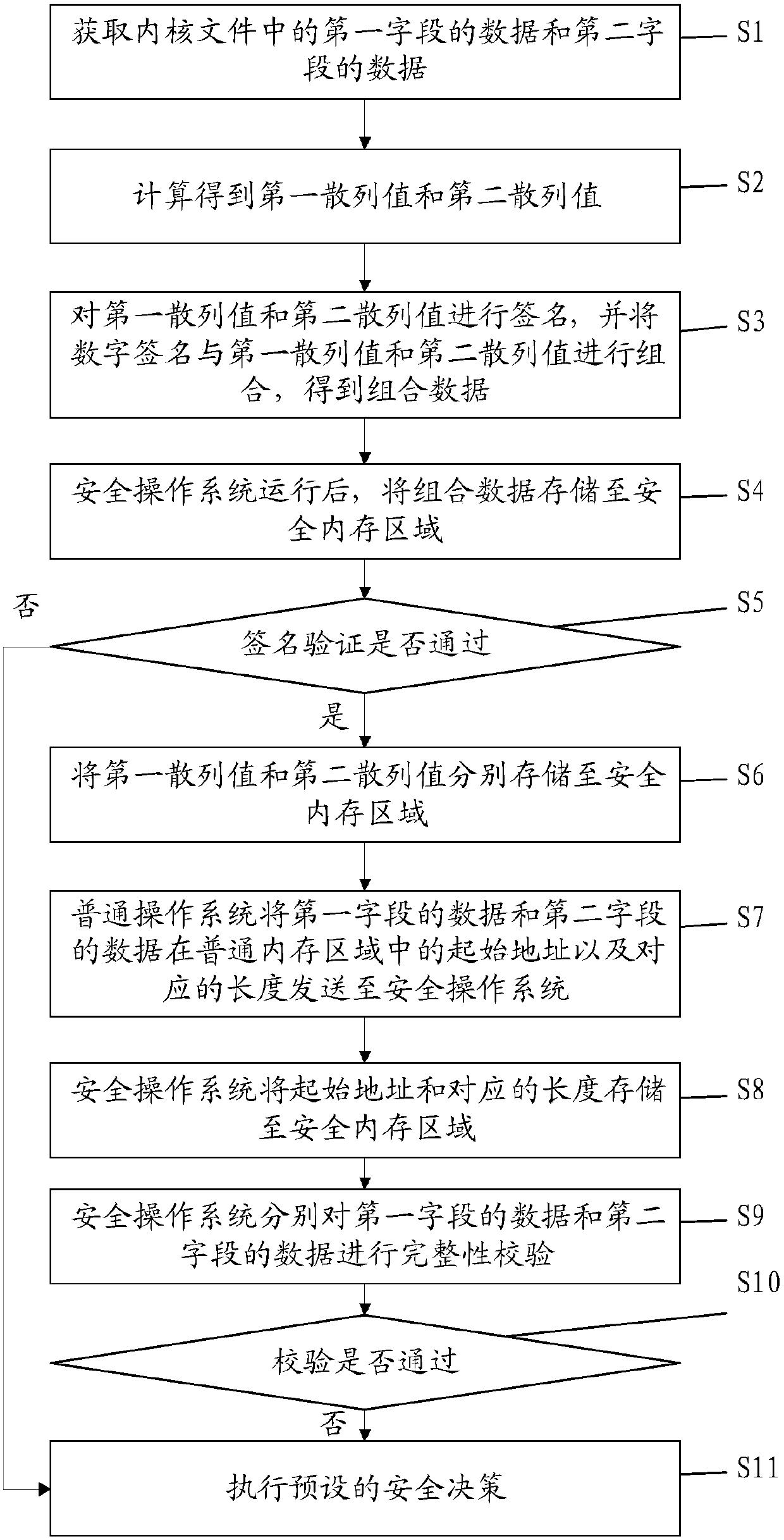
[0099] In step S2, the data in the first field and the data in the second field are respectively subjected to block-by-block one-way hash calculation to obtain a first hash value and a second hash value.
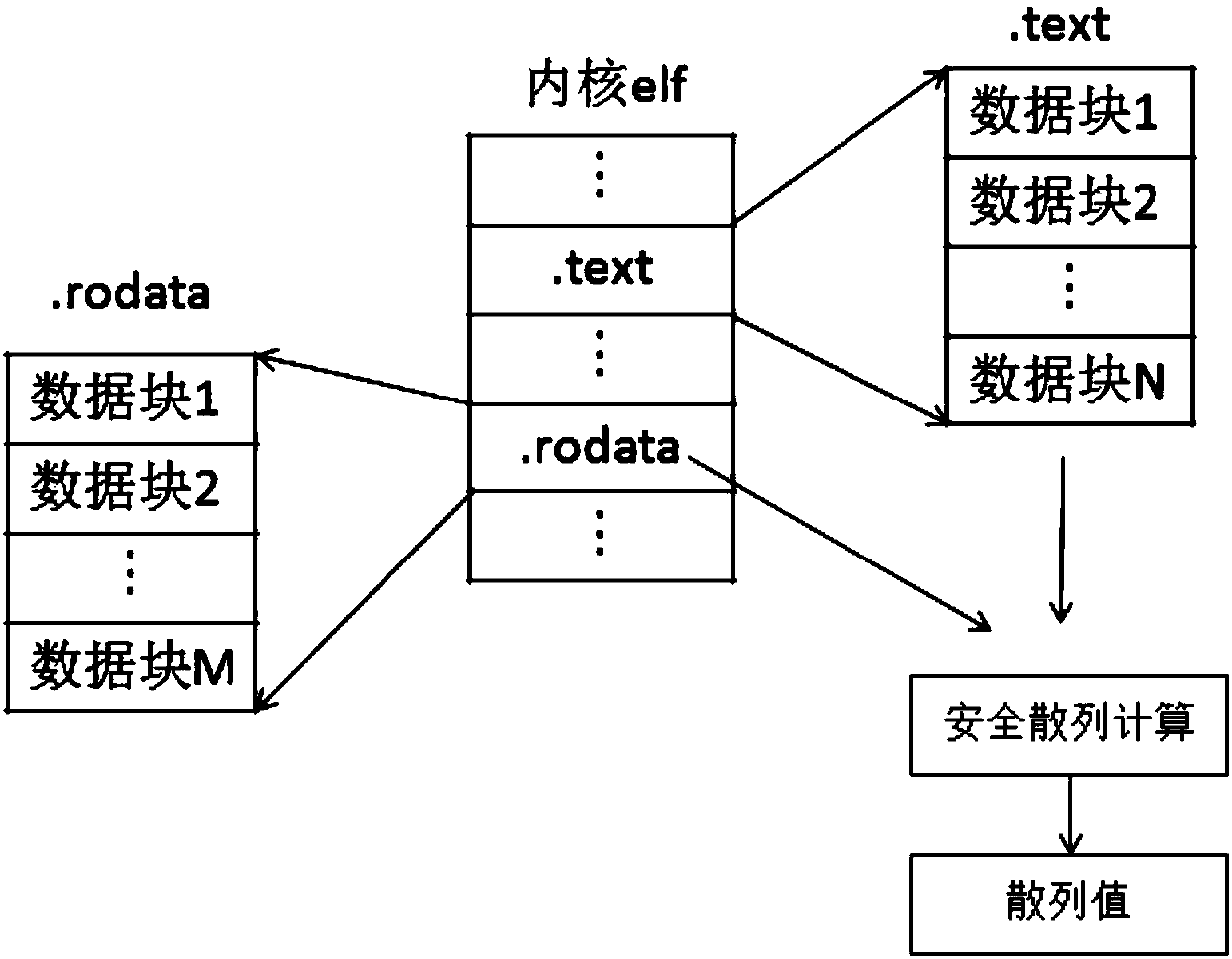
[0100] In this embodiment, the data in the first field is taken as an example for description. Such as image 3 As shown, according to the preset block size, the data in the first field is divided into multiple data blocks; for example, the size of each block is 4K, assuming that the size of .text data is 1M, it can be divided into 256 blocks; if the final data If it is less than 4K, for example, the last block is only 2K, it is also counted as one block.
[0101] Then calculate the hash value of the first data block; for each next data block, perform one-way hash calculation on the hash value of the current data block and the previous data block to obtain the hash value of the current data block; That is, t...
Embodiment 3
[0108] This embodiment is a computer-readable storage medium corresponding to the above-mentioned embodiments, on which a computer program is stored, and when the program is executed by a processor, the following steps are implemented:
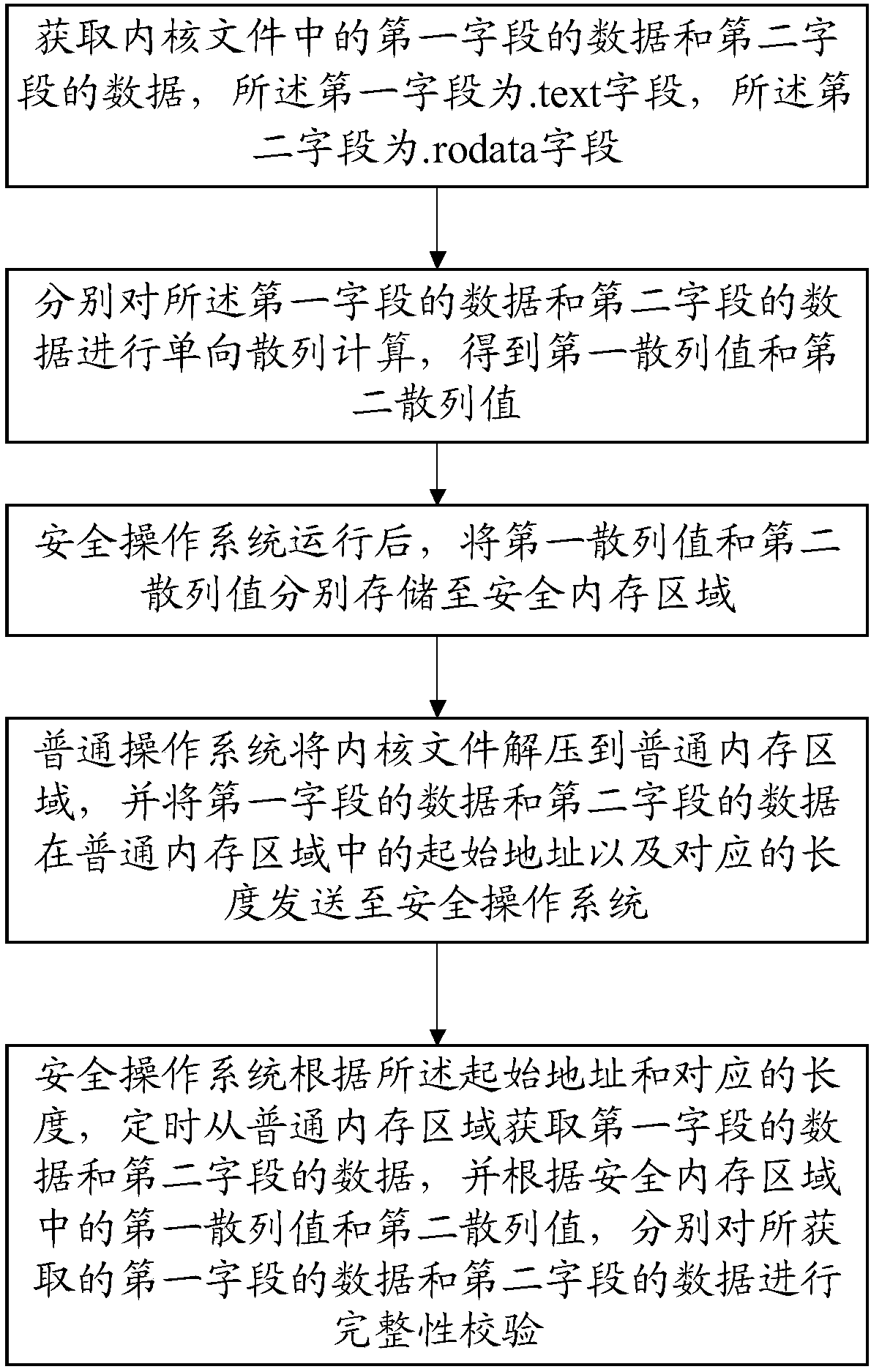
[0109] Obtain the data of the first field and the data of the second field in the kernel file, the first field is the .text field, and the second field is the .rodata field;
[0110] performing a one-way hash calculation on the data in the first field and the data in the second field, respectively, to obtain a first hash value and a second hash value;
[0111] After the secure operating system is running, store the first hash value and the second hash value in the secure memory area respectively;
[0112] The normal operating system decompresses the kernel file to the normal memory area, and sends the starting addresses and corresponding lengths of the data of the first field and the data of the second field in the normal memory area to the se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com