An intrusion detection method based on traffic visualization and machine learning algorithm
An intrusion detection and machine learning technology, applied in the Internet field, can solve problems such as complex feature extraction, inability to accurately detect every attack, and high cost of resource occupancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0087] The specific embodiments of the present invention are described below to facilitate those skilled in the art to understand the present invention, but it should be clear that the present invention is not limited to the scope of the specific embodiments. For those of ordinary skill in the art, as long as various changes Such changes are obvious within the spirit and scope of the present invention as defined and determined by the appended claims, and all inventions and creations utilizing the inventive concept are within the scope of protection.
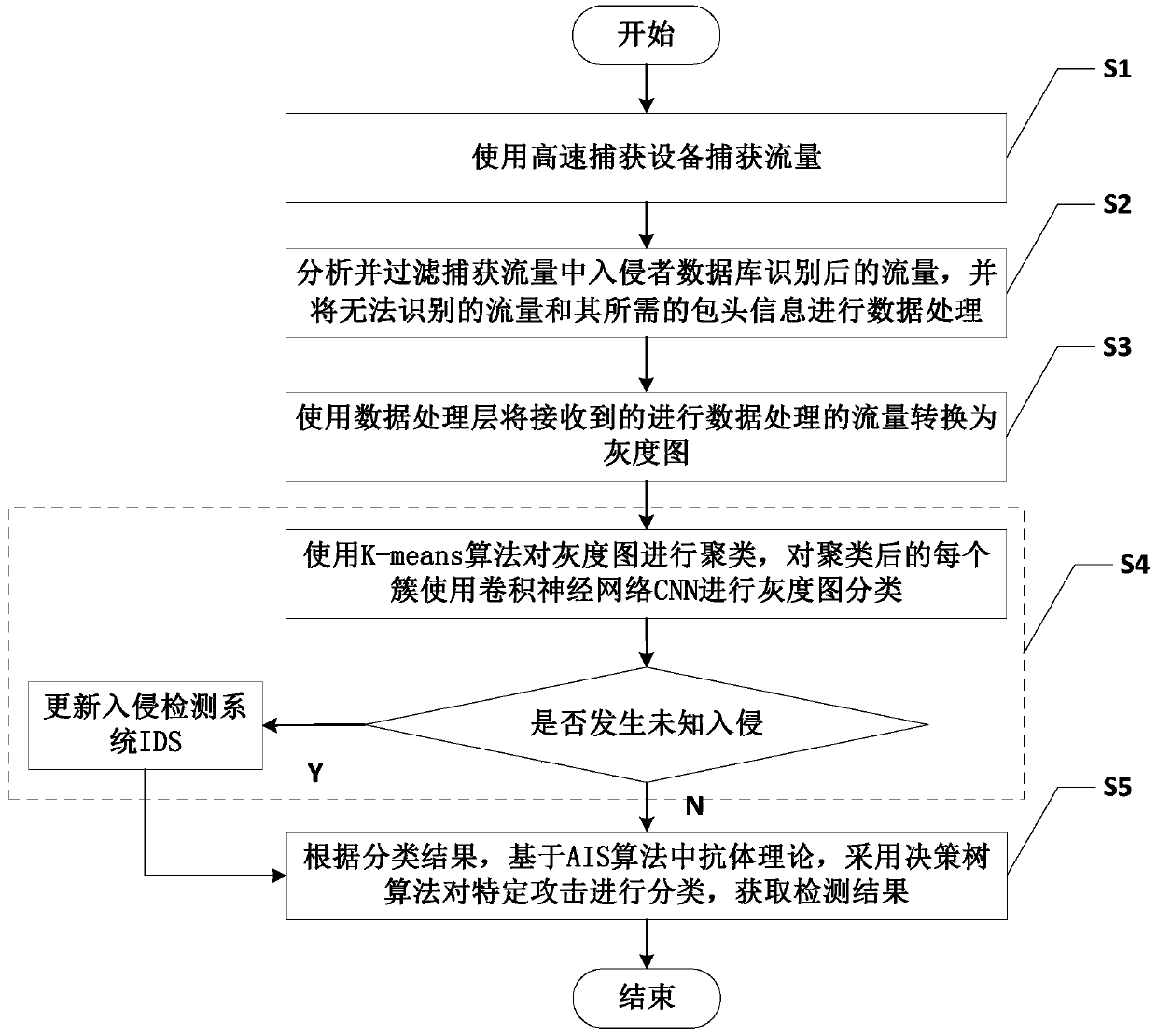
[0088] like figure 1 As shown, an intrusion detection method based on traffic visualization and machine learning algorithm includes the following steps:
[0089] S1: Use high-speed capture device RF_RING or TNAPI to capture traffic;
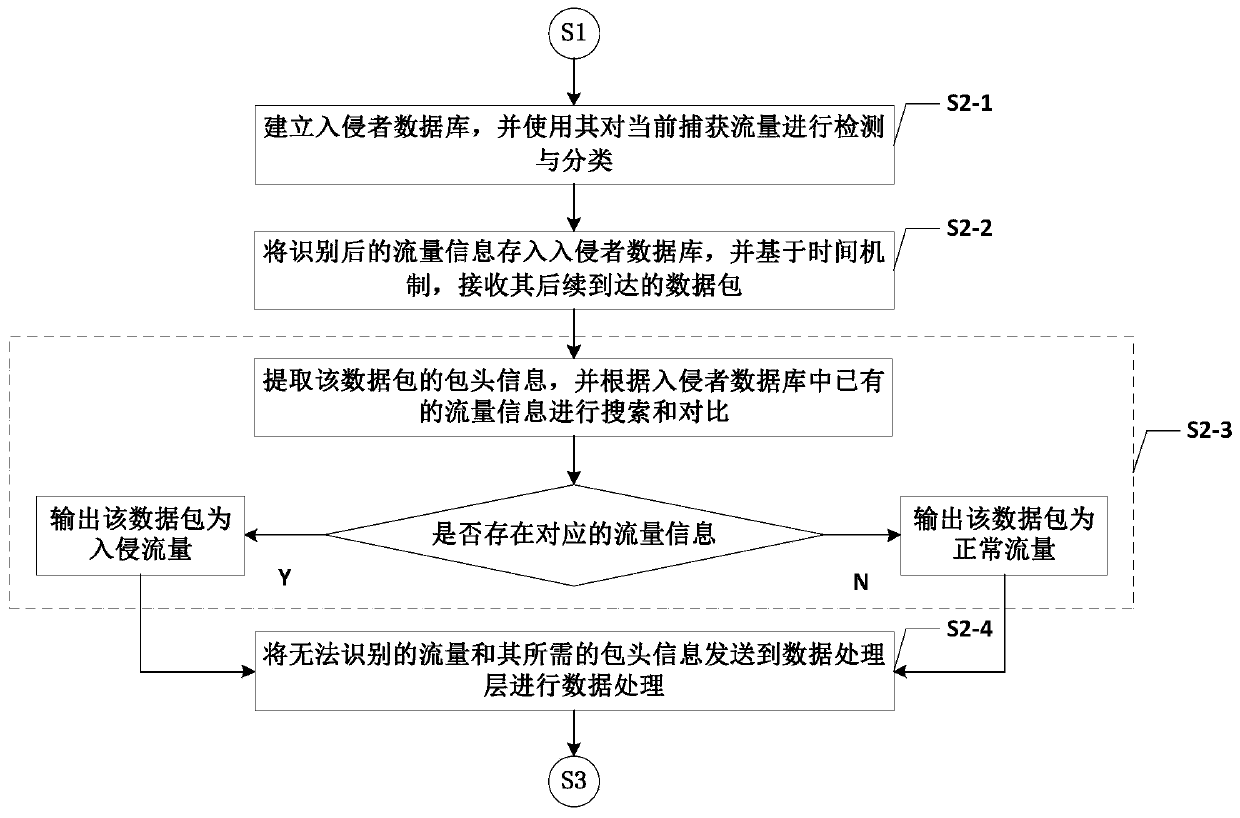
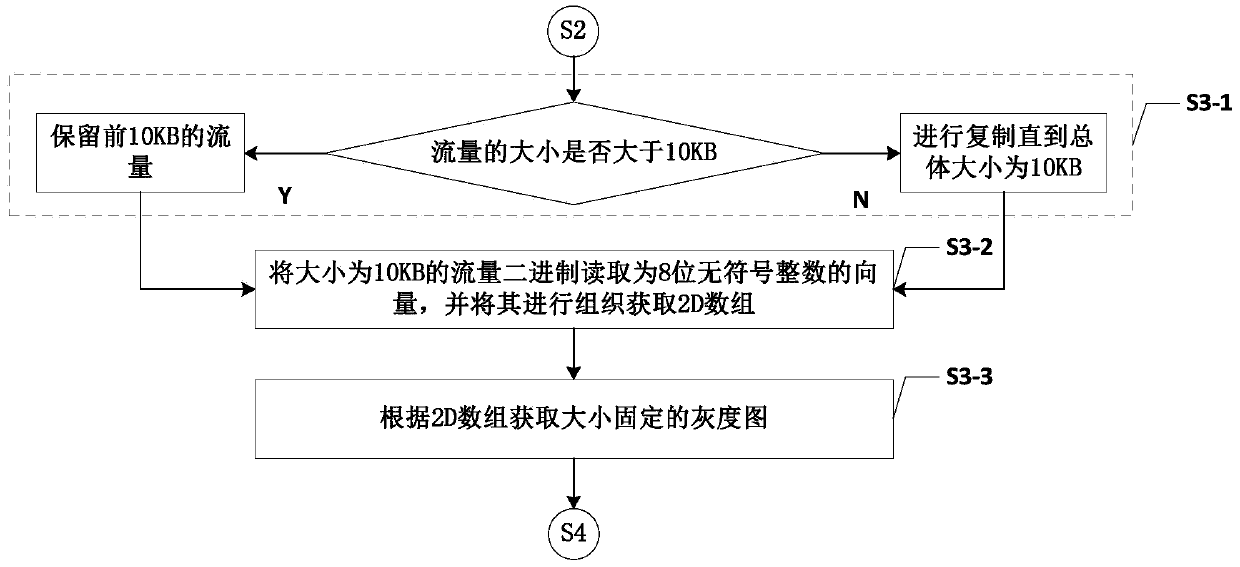
[0090] S2: Analyze and filter the traffic identified by the intruder database in the captured traffic, and send the unidentified traffic and its required header information to the data processing l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com