Malware classification method for optimizing feature extraction
A malicious software and classification method technology, applied in the field of information security, to achieve the effect of improving accuracy, reducing false alarm rate, and good classification effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be described in further detail below in conjunction with the accompanying drawings.
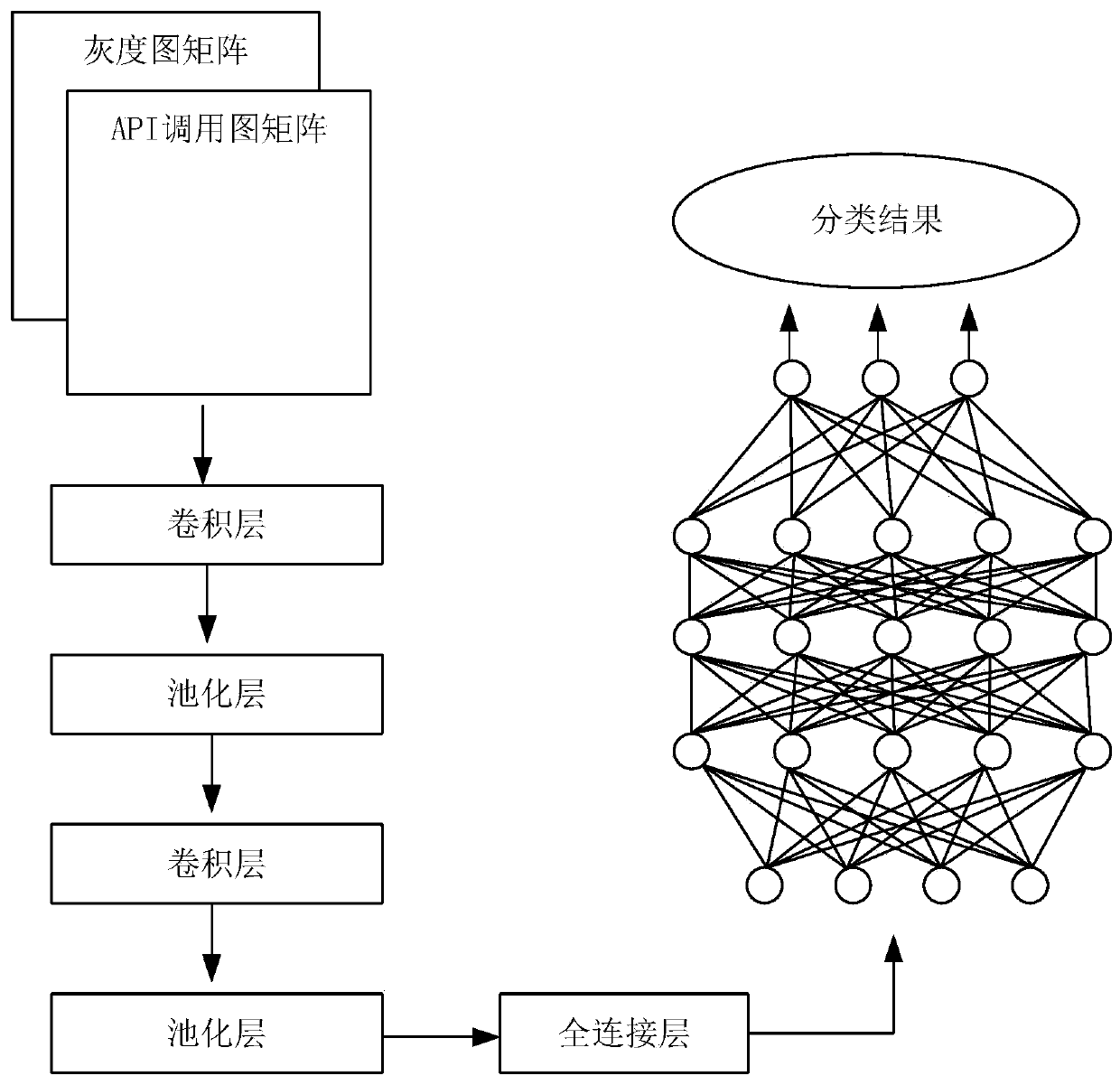
[0022] combine figure 1 , the implementation process of this method is divided into the following steps:
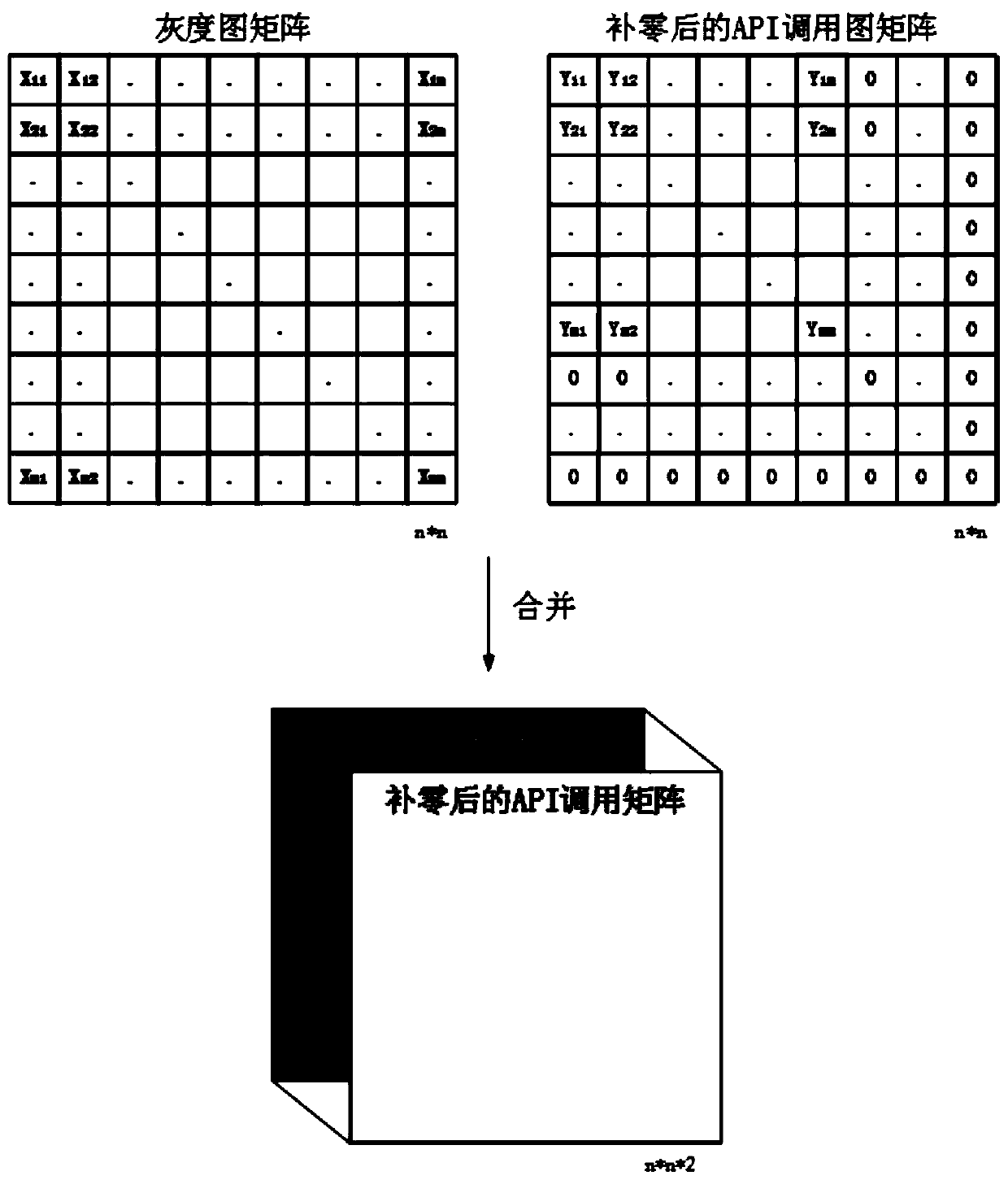
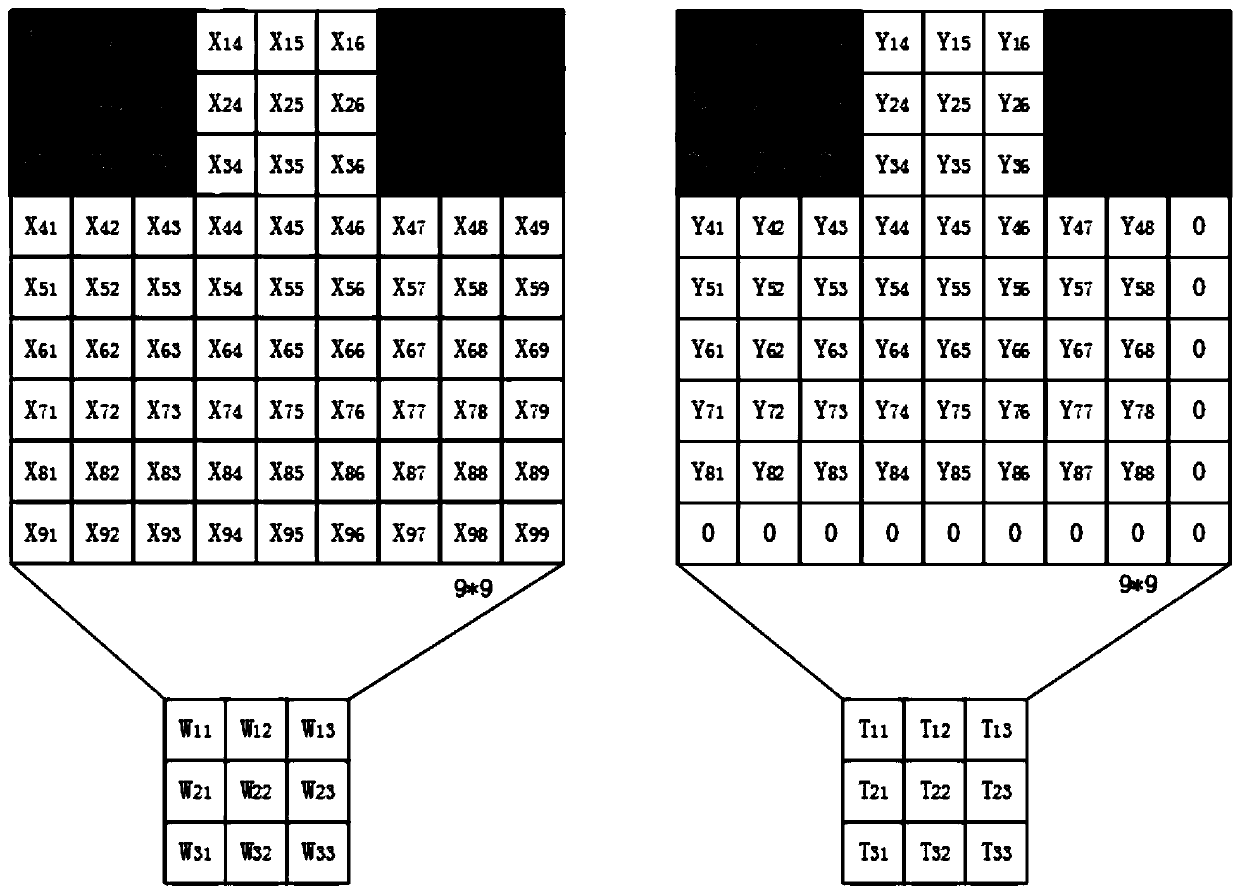
[0023] 1. Raw data feature processing: use IDA pro to disassemble all malware samples, the binary files of malicious code are disassembled to obtain their corresponding assembly codes, divide the assembly codes into basic blocks, scan each basic block separately, and select the The statement of the call instruction and the statement containing the jump instruction, such as jz, jmp, jnz, etc. The functions invoked by the call instruction are divided into two categories, user-defined functions and APIs. If the calling target is a self-defined function, enter the interior of the self-defined function, continue to scan its internal assembly statement, and filter its internal API. After the screening, according to the order of API execution and the jump st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com