A third party secure access method in the form of a service provider H5 application
A secure access and form technology, applied to electrical components, transmission systems, etc., can solve problems such as long access cycle, complex process, and uncontrollable data use, and achieve strong reusability, fast online speed, and low development costs. control effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
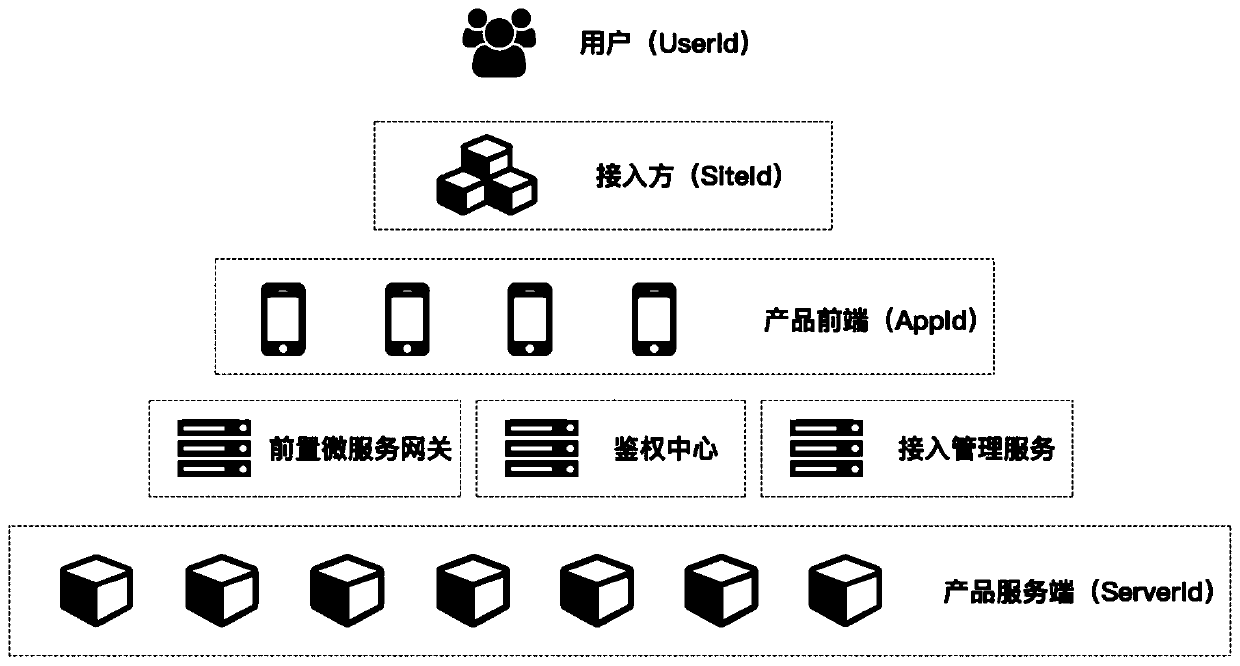
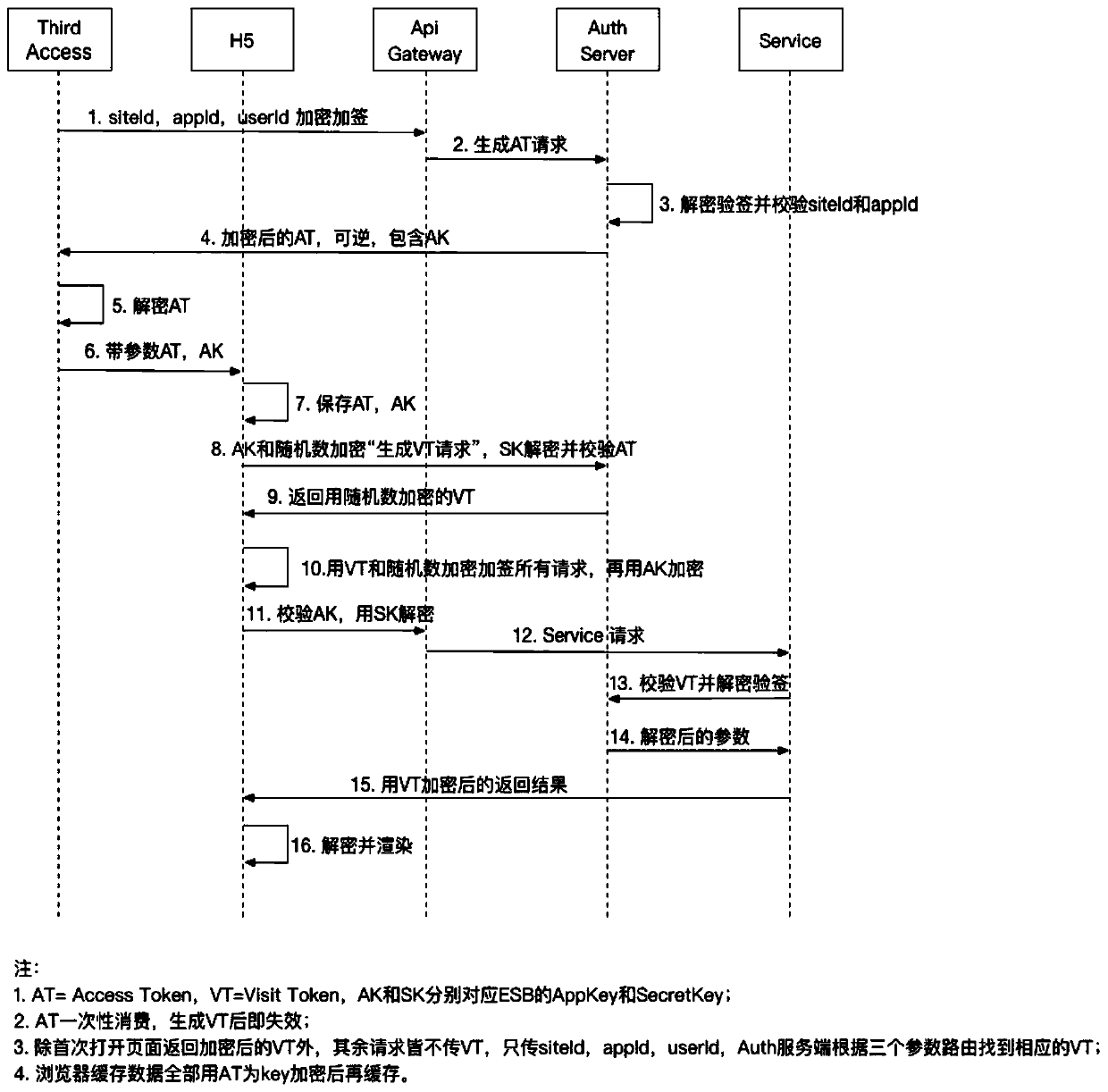
[0045] Such as Figure 1 to Figure 2 As shown, the third-party security access method in the form of H5 application of the service provider includes the third-party backend, the H5 end of the service provider, the gateway server of the service provider, the authentication end of the service provider, and the backend of the service provider. Include the following steps:
[0046] A. The user of the third-party client clicks an entry request to enter the service application provided by the service provider, and notifies the third-party backend of the message;
[0047] B. The third-party backend initiates a request to the service provider to generate an access key AT (Access Token, referred to as AT) through the service provider gateway server, and the service provider generates the access key AT and passes it through the service provider gateway The server returns to the third-party backend;
[0048] C. After the third-party backend receives the encrypted AT, it decrypts the AT...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com