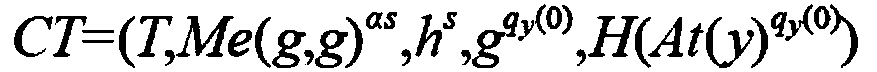A computer network information security control system and method
A computer network and information security technology, applied in the field of computer network information security control system, can solve the problems of loss, reduce the efficiency of information collection, expand the influence of rumors, etc., and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In order to further understand the content, features and effects of the present invention, the following examples are given, and detailed descriptions are given below with reference to the accompanying drawings.
[0047] The structure of the present invention will be described in detail below in conjunction with the accompanying drawings.
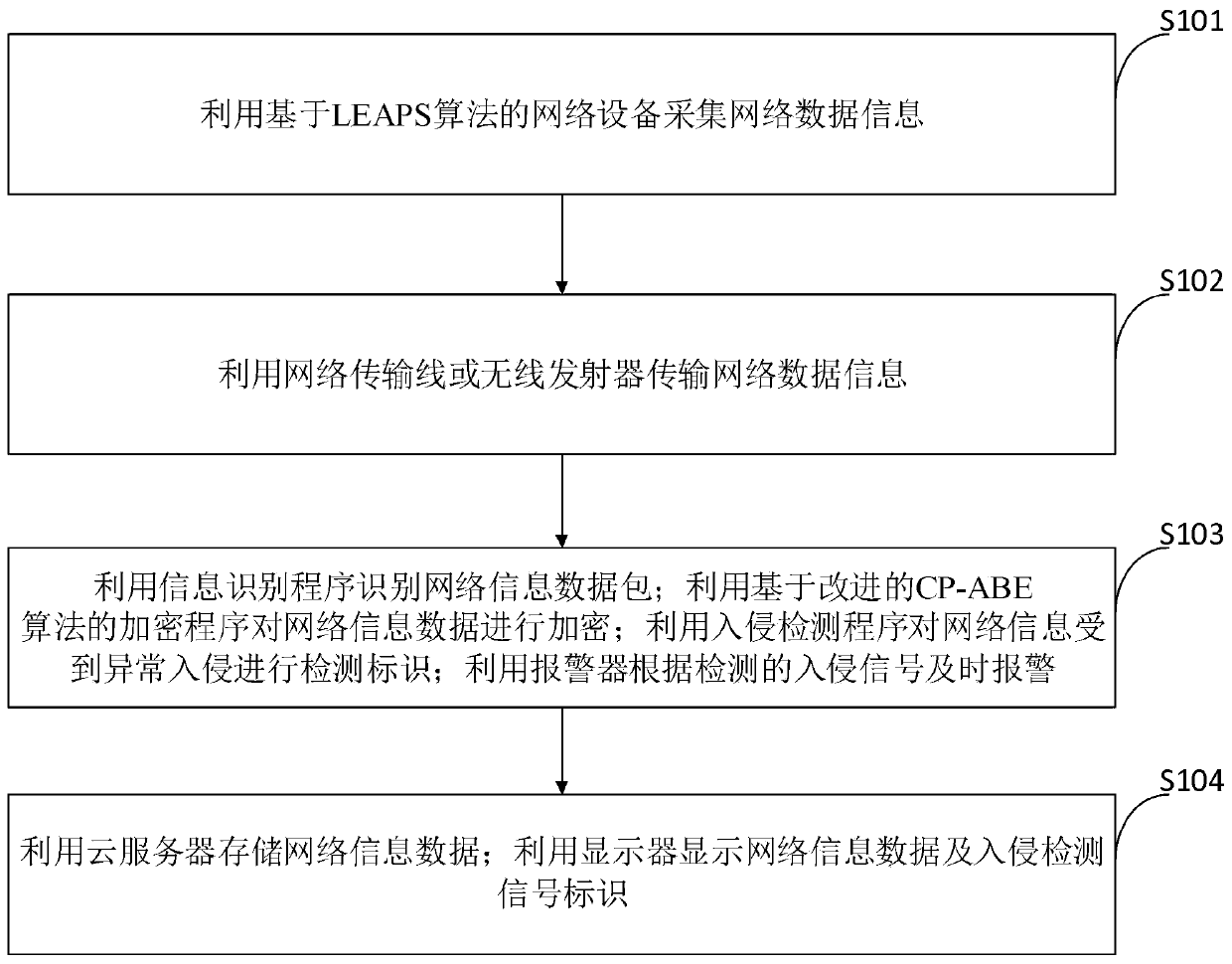
[0048] Such as figure 1 As shown, the computer network information security control method provided by the embodiment of the present invention includes:
[0049] S101: Collect network data information using network equipment based on the LEAPS algorithm;
[0050] S102: Using a network transmission line or a wireless transmitter to transmit network data information;
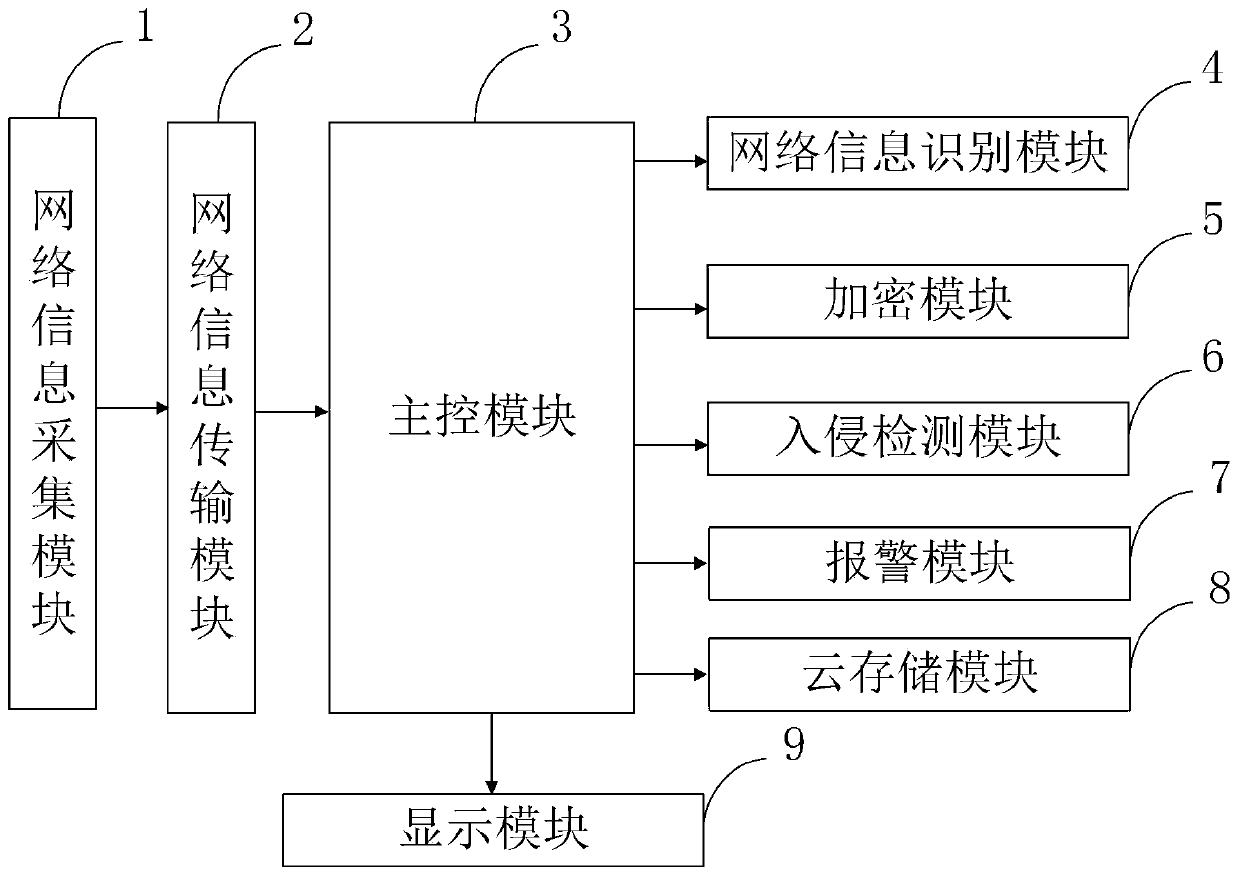
[0051] S103: Use the information identification program to identify network information data packets; use the encryption program based on the improved CP-ABE algorithm to encrypt the network information data; use the intrusion detection program to detect and mark the a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com