An Android application maliciousness detection method based on application behaviors
A detection method and malicious technology, applied in the field of Android application detection, can solve problems such as difficult unknown application analysis, inability to learn complex information representation, difficult problems, etc., to achieve automatic classification learning, avoid path explosion problems, and reduce analysis time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
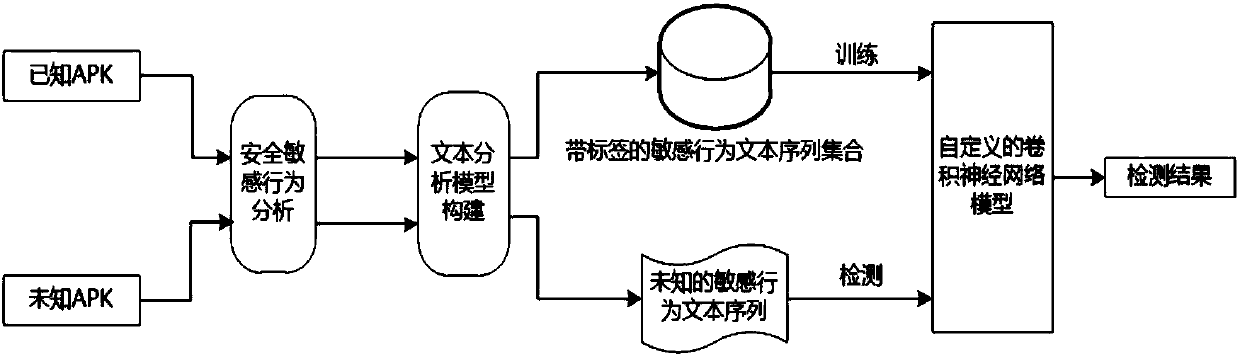
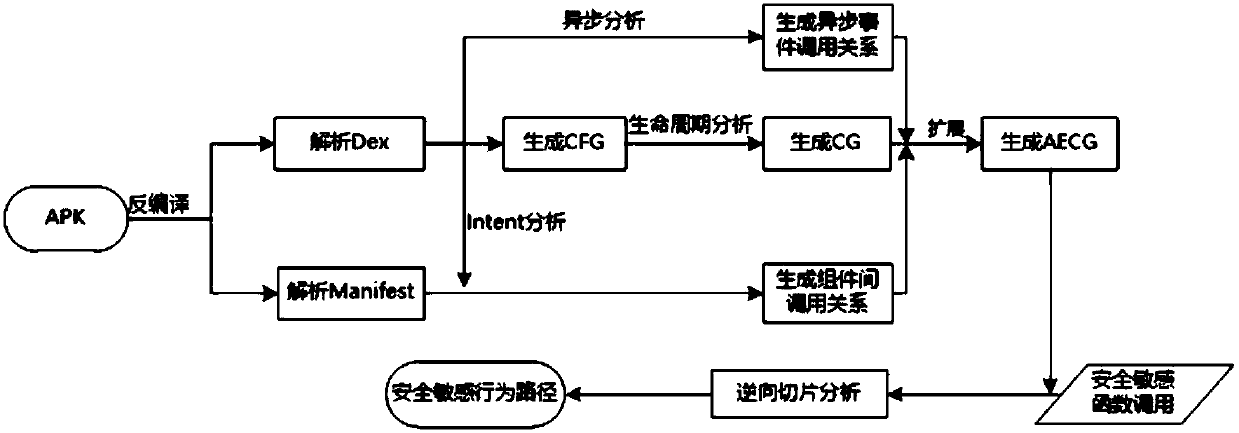
[0019] The present invention provides a static analysis method aimed at Android application behavior analysis. Aiming at the characteristics of the Android system, Android application function call graphs and control flow graphs are used, and reverse analysis and program slicing techniques are used to extract malicious behaviors that may be contained in Android applications. The complete behavior path of the Android application is finally combined with the deep learning model to detect the maliciousness of the behavior of the Android application.
[0020] The principle of the present invention is: because malicious functions are usually hidden in legal function codes, and the inherent multi-component and event-driven features of the Android system make malicious function codes more fragmented and more concealed, which intensifies the analysis of malicious functions of Android applications. difficulty. The present invention first uses the static analysis technology to analyze t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com