A dual-system trusted computing system and method
A trusted computing and trusted technology, applied in the field of information security, can solve problems such as inability to adapt, violation of security principles, and damage to enterprise production systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
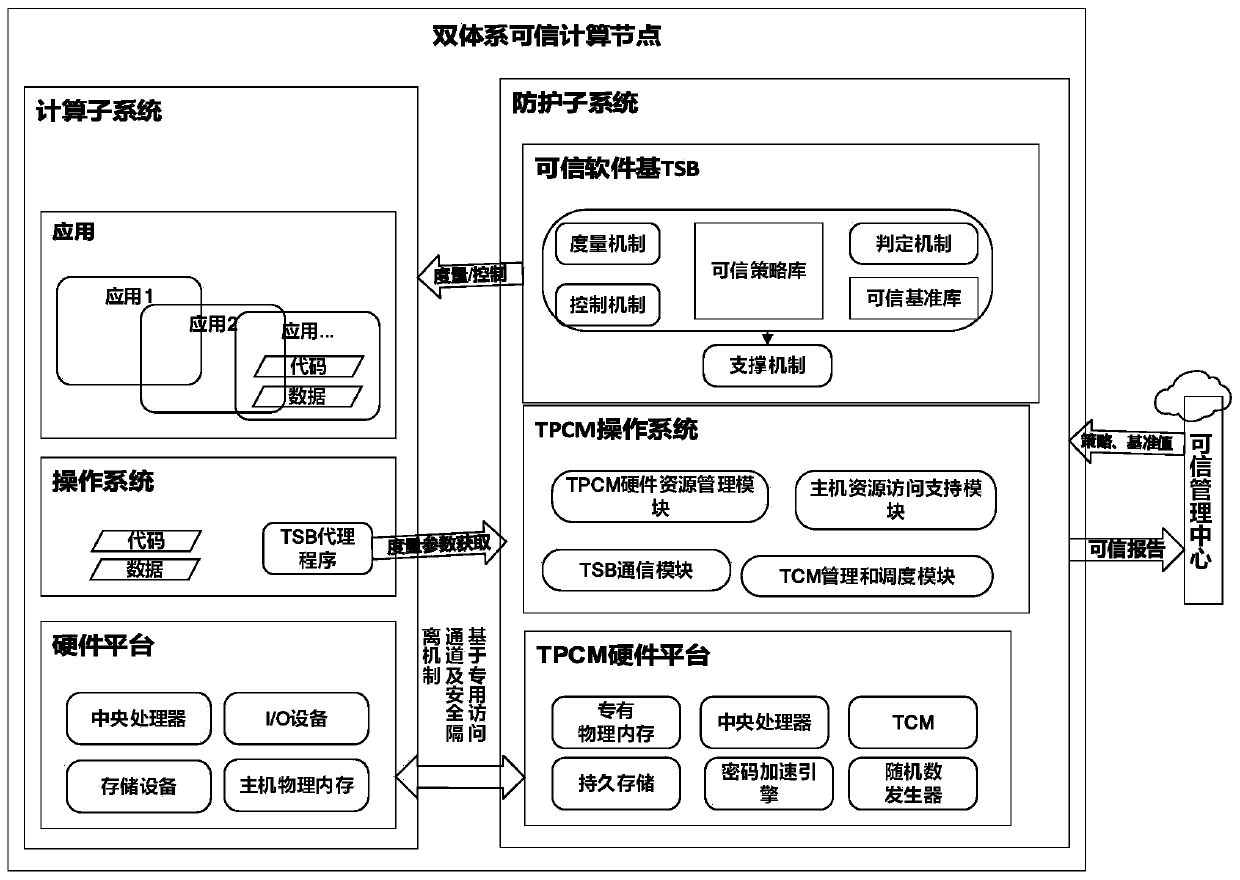
[0071] Such as figure 1 As shown, a dual-system trusted computing system, the system includes: a trusted management center and at least one dual-system trusted computing node connected to the trusted management center, the dual-system trusted computing node includes: parallel computing subsystems and The protection subsystem has a security isolation mechanism between the computing subsystem and the protection subsystem, and interacts through a dedicated access channel; wherein, the trusted management center is an independent management center or implemented inside a dual-architecture trusted computing node.
[0072] The computing subsystem is used to perform computing tasks, the protection subsystem is used to measure and control the computing subsystem according to the trusted policy in the trusted management center, and send the measurement records to the trusted management center, and the trusted management center uses For statistical analysis of measurement records.
[00...
Embodiment 2
[0159] An embodiment of the present invention also provides a dual-system trusted computing method, which is applied to the dual-system trusted computing system in Embodiment 1. The system includes: a trusted management center and at least one dual-system trusted computing system connected to the trusted management center. Trust computing nodes, dual-system trusted computing nodes include: parallel computing subsystems and protection subsystems, with a security isolation mechanism between the computing subsystems and protection subsystems, which interact through dedicated access channels;
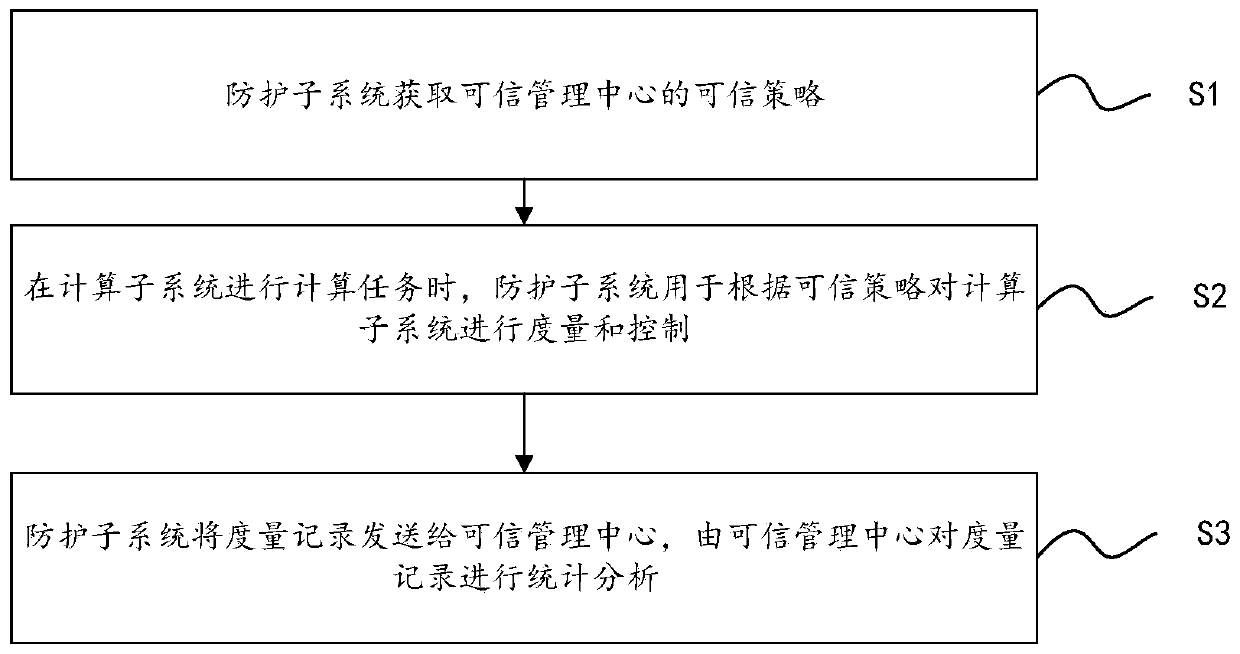
[0160] Such as figure 2 As shown, the methods include:
[0161] S1. The protection subsystem obtains the trusted strategy of the trusted management center;
[0162] S2. When the computing subsystem performs computing tasks, the protection subsystem is used to measure and control the computing subsystem according to trusted policies;
[0163] S3. The protection subsystem sends the measure...
Embodiment 3
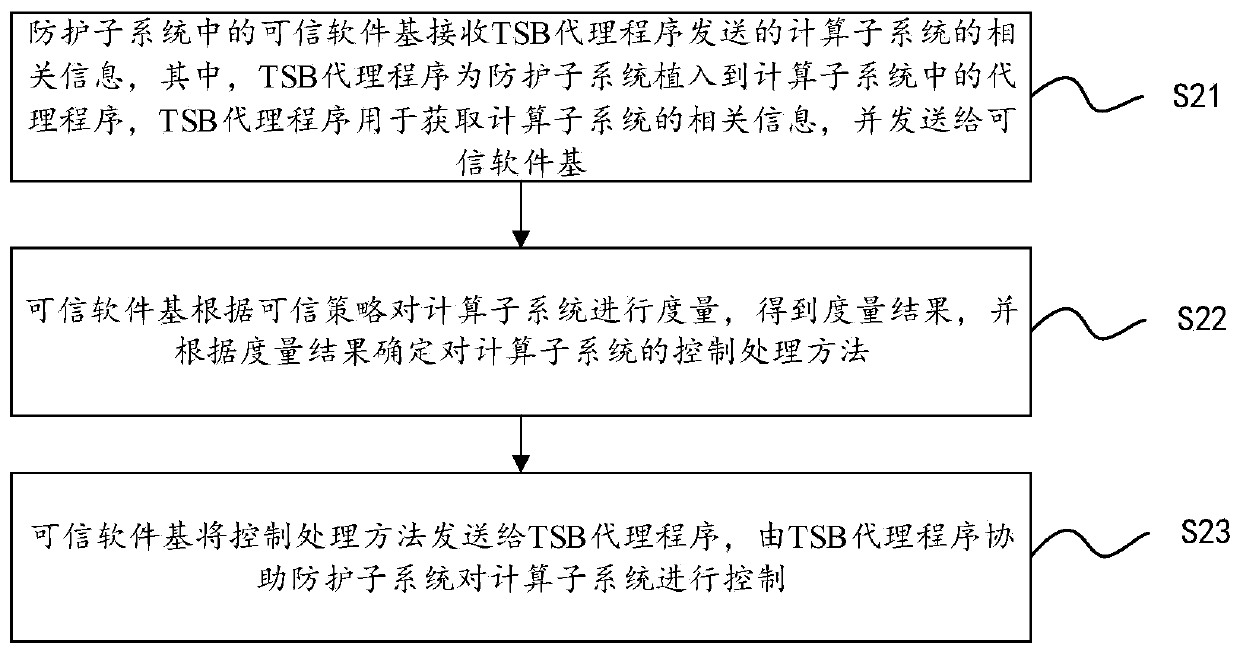
[0166] Based on a dual-system trusted computing method in Embodiment 2, the protection subsystem includes: a trusted software base, a TPCM operating system, and a TPCM hardware platform, and the computing subsystem includes: an application program, an operating system, and a hardware platform, such as image 3 As shown, step S2 includes:
[0167] S21. The trusted software base in the protection subsystem receives the relevant information of the computing subsystem sent by the TSB agent program, wherein the TSB agent program is an agent program implanted into the computing subsystem by the protection subsystem, and the TSB agent program is used to obtain Calculate the relevant information of the subsystem and send it to the trusted software base;
[0168] S22. The trusted software base measures the computing subsystem according to the trusted policy, obtains a measurement result, and determines a control and processing method for the computing subsystem according to the measure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com