A group label authentication method based on secondary residual lightweight RFID
A secondary residual and authentication method technology, applied in the field of information processing, can solve the problems of high consumption of storage resources, high computational complexity, long authentication time, etc., and achieve the effect of cost reduction, wide application range, and efficient two-way authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
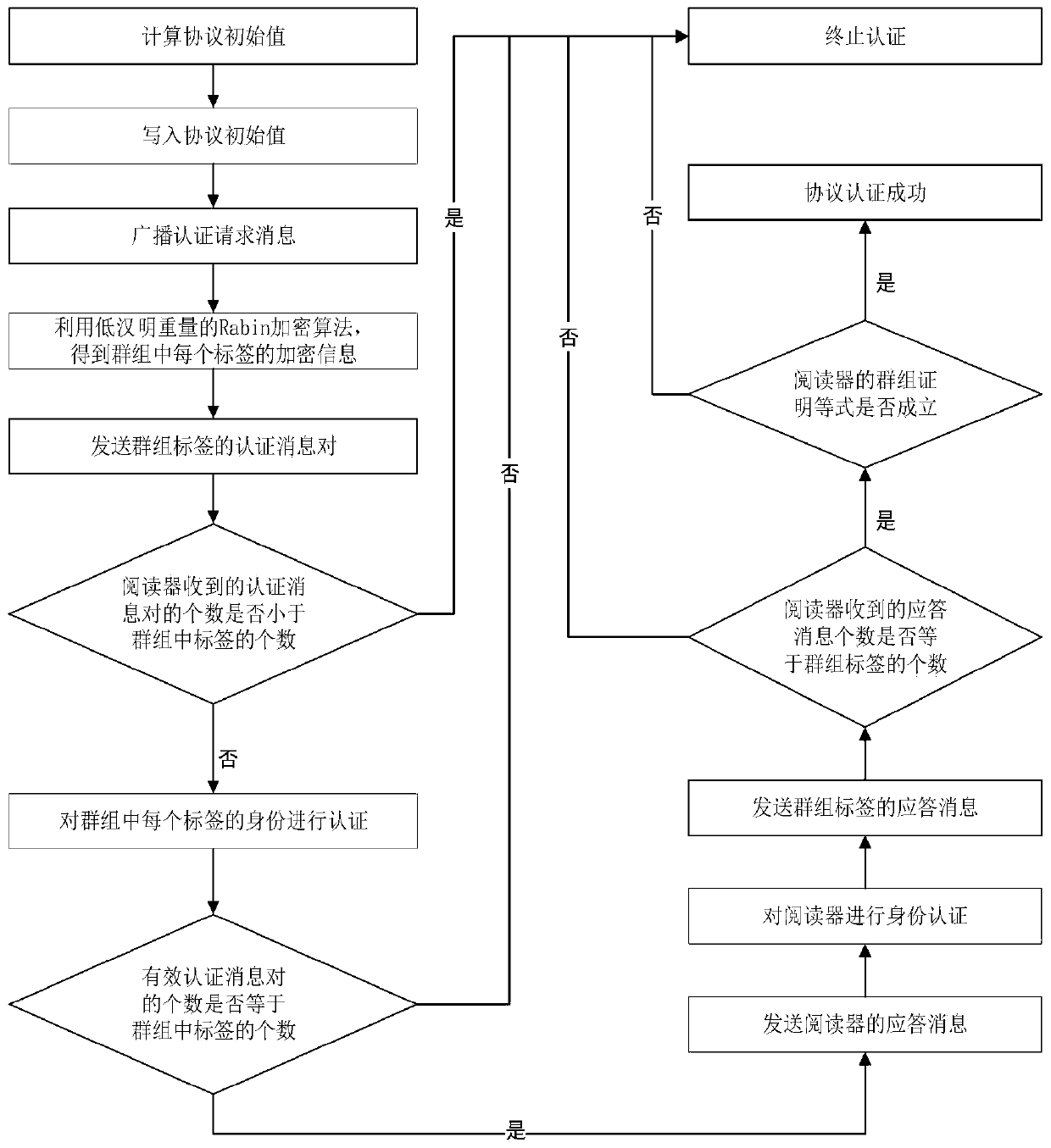
[0061] Attached below figure 1 , to further describe the specific steps of the present invention.
[0062] Step 1, calculate the protocol initial value.
[0063] Use a pseudo-random number generator to generate a large prime number n of length 1024 bits T Group public key as tag group.
[0064] Use a pseudo-random number generator to generate N random numbers as the private key of each tag in the group, where N represents the number of group tags, and each random number corresponds to a group tag.
[0065] The padding encoding method is used to perform padding encoding on the private key of each tag in the group to obtain the private key encoding value of each tag in the group.
[0066] The steps of the filling coding method are as follows:
[0067] Step 1, at length l 1 Bit tail padding of the character string to be encoded 256-l 1 0 characters, fill the character string to be encoded into a character string with a length of 256 bits;
[0068] Step 2, divide the charac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com