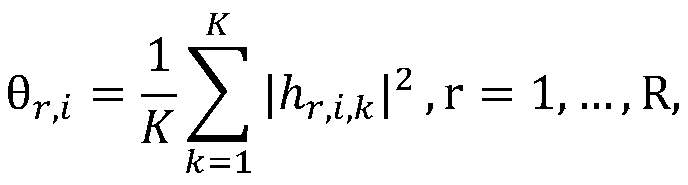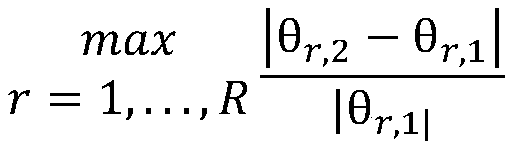Physical layer security authentication method based on large-scale fading characteristics
A large-scale fading, physical layer security technology, applied in security devices, electrical components, wireless communications and other directions, can solve problems such as application scenario limitations
Active Publication Date: 2019-07-05
UNIV OF ELECTRONIC SCI & TECH OF CHINA
View PDF5 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Therefore, the application scenarios of the existing physical layer security authentication technology based on channel information still have great limitations
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
[0030] The solution in the summary of the invention is the best implementation solution of the present invention, and will not be repeated here.
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
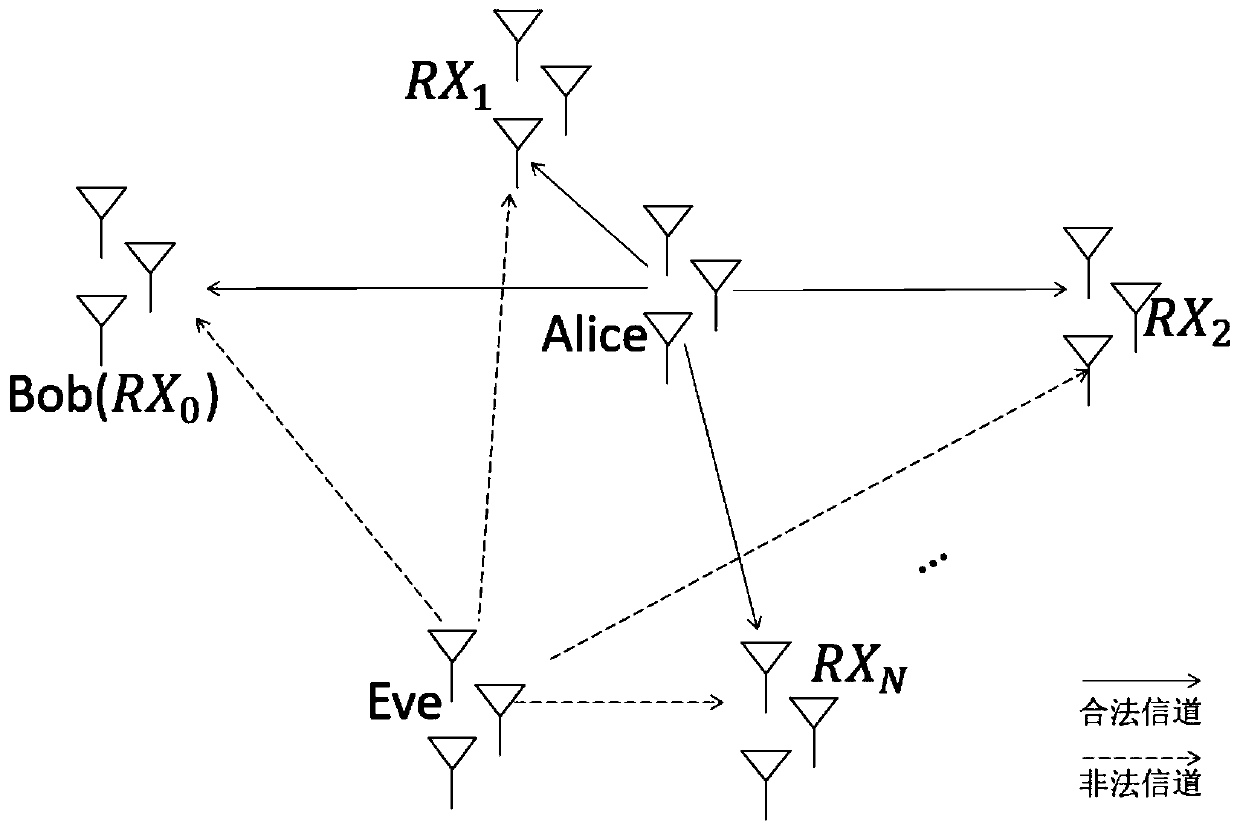
The invention belongs to the technical field of wireless communication, and relates to a physical layer security authentication method based on large-scale fading characteristics. According to the method, a large amount of channel information in one information packet is analyzed to obtain large-scale fading characteristics, and the correlation degree of the large-scale fading characteristics corresponding to the adjacent information packets is obtained by utilizing the normalized Euclidean distance, so that the Neyman-Pearson) verification is carried out to authenticate the identity of the user. According to the method, the user is authenticated on the basis of the large-scale fading characteristics of the channel, and compared with instantaneous channel information, the related conditions of the large-scale fading characteristics are looser, namely, when the moving distance of the user is large, certain correlation can still be kept between the large-scale fading characteristics corresponding to the user before and after moving.
Description
technical field [0001] The invention belongs to the technical field of wireless communication, and relates to a physical layer security authentication method based on large-scale fading characteristics. Background technique [0002] The broadcast feature of wireless network makes it face various attacks and many security threats. For example, a device can easily change its Media Access Control (MAC) layer address to declare itself to be another device. This makes wireless networks face very serious threats. From session hijacking to attacking access control lists, there are many attacks caused by malicious users masquerading as other users. However, the traditional security authentication is realized with the help of secret keys. The distribution and management of secret keys make the traditional security methods very complicated. On the other hand, with the continuous improvement of computer capabilities, traditional secret key methods have great big hole. [0003] As a...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04W12/06H04W12/08
CPCH04W12/08H04W12/06H04L63/16
Inventor 王倩陈智李航赵豆叶爽蔡建生陈文荣
Owner UNIV OF ELECTRONIC SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com