Hot spot data storage method and terminal
A technology of hotspot data and data, applied in the Internet field, can solve problems such as performance bottlenecks and hotspots, and achieve the effects of improving efficiency, avoiding downtime, and alleviating performance bottlenecks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
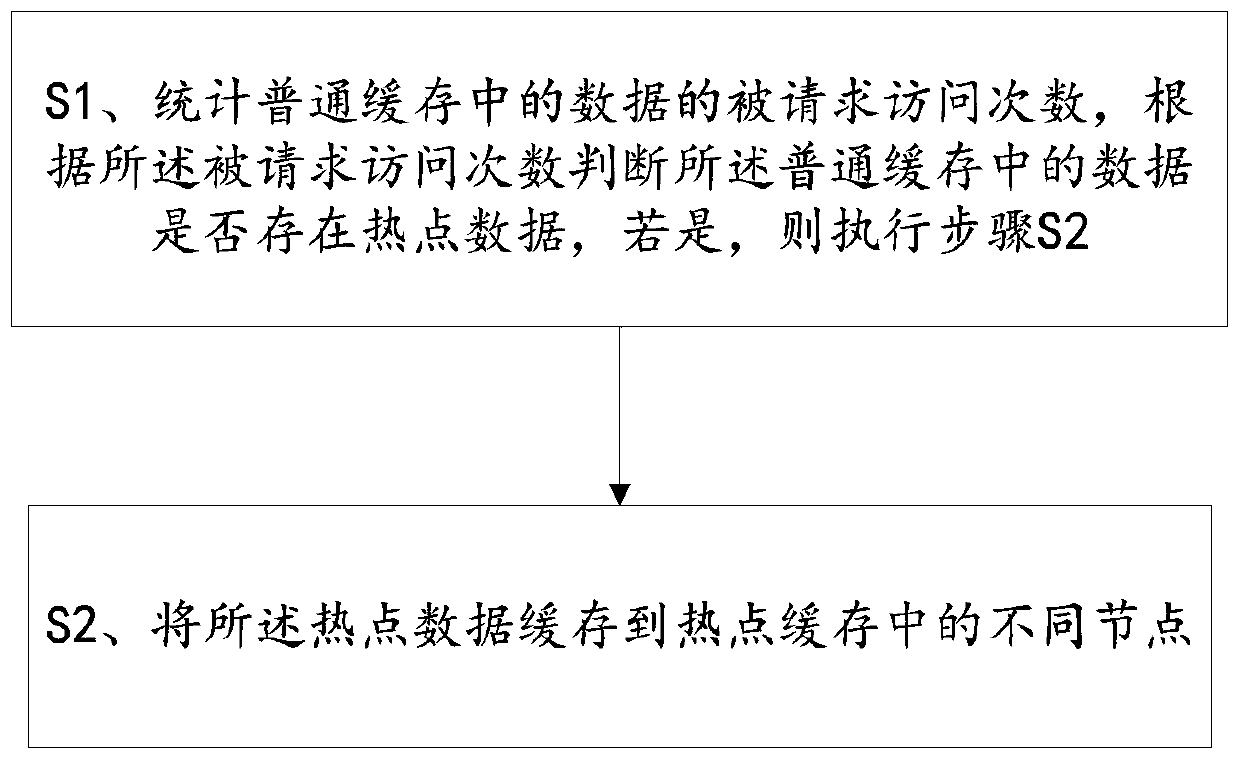
[0064] Please refer to figure 1 and image 3 , a method for storing hotspot data, comprising the steps of:
[0065] S1. Count the requested access times of the data in the ordinary cache, and judge whether there is hot data in the data in the ordinary cache according to the requested access times, and if so, perform step S2;
[0066] Wherein, the ordinary cache is an ordinary redis cluster or an ordinary single-point redis collection;
[0067] Specifically, it is judged by the hotspot calculation module whether the number of requested visits of the data in the common cache within the preset time is greater than the preset number of times, if yes, the data is hot data, if not, the data is not Hot data;
[0068] Preferably, the preset time is 1 minute, and the preset number of times is 100,000 times;
[0069] For example, if the number of access requests of an organization ID in the same interface occurs 100,000 times within one minute, it is determined that the data require...
Embodiment 2
[0085] The difference between this embodiment and Embodiment 1 is that it also includes:
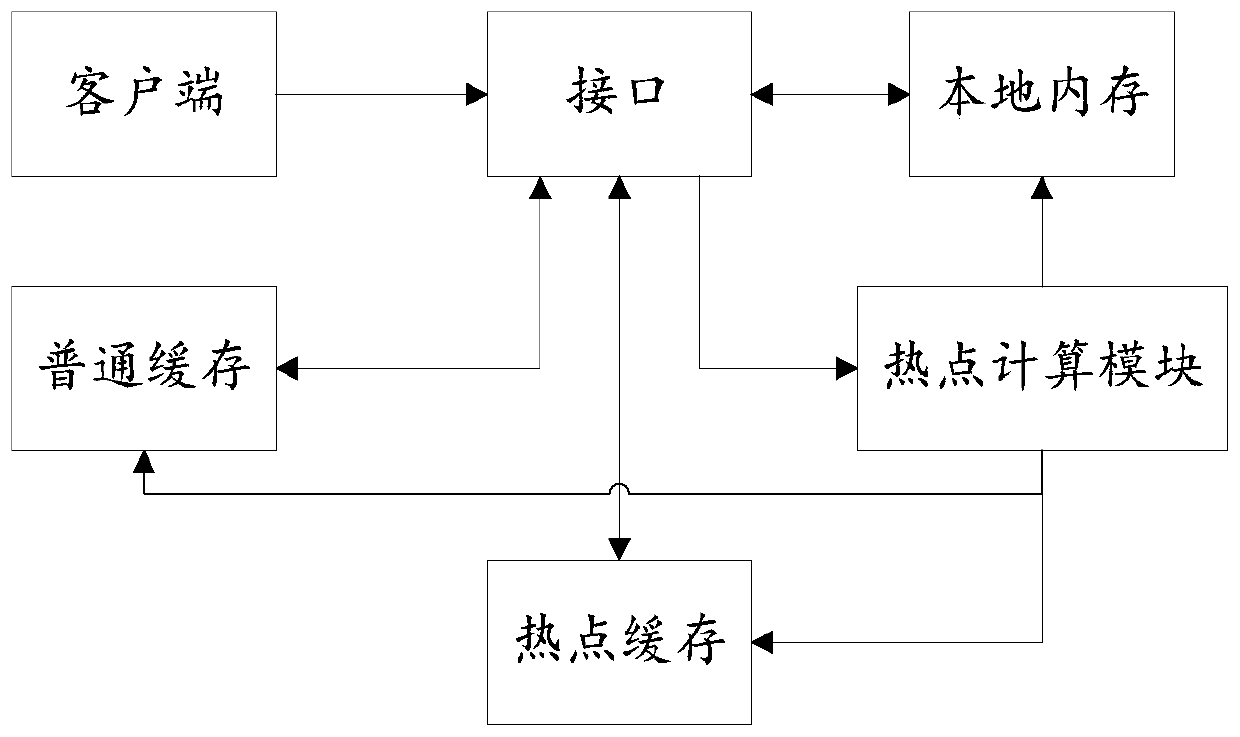
[0086] In a specific data request, the interface receives the data request from the client, and the data request includes the original cache key of the data;
[0087] Specifically, the client requests the interface, and the interface queries the data in the local memory;
[0088] When the switch sign indicates that access to the hotspot cache is closed, the interface directly accesses the common cache to obtain data;
[0089] When the switch sign indicates that hotspot cache access is enabled, the interface judges whether the data needs to query the hotspot cache, that is, judges whether the data is hotspot data;
[0090] If so, according to the mapping relationship between the saved original cache key and the hotspot cache key corresponding to different nodes, a hotspot cache key is randomly selected according to a certain random algorithm, and obtained from the corresponding node in t...
Embodiment 3
[0098] The difference between this embodiment and embodiment one or embodiment two is that it also includes:
[0099] When acquiring the hotspot data from the common cache, acquire the expiration time of the hotspot data in the common cache;
[0100] When saving the hotspot data in different nodes in the hotspot cache, setting the expiration time of the hotspot data in the hotspot cache;
[0101] Wherein, the expiration time of the hotspot data in the hotspot cache is consistent with the expiration time of the hotspot data in the common cache.
[0102]Preferably, when the quantity of hotspot data is lower than a preset value, only its expiration time in the hotspot cache is set, and it can be automatically deleted when the hotspot data expires; when the quantity of hotspot data reaches a preset value, then While setting the expiration time, you can also manage the hotspot data in the hotspot cache according to certain rules, for example, delete the preset number of hotspot da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com