High-security IP secure communication method
A confidential communication and security technology, applied to secure communication devices and key distribution, can solve the problems of inability to crack the confidential communication system, destroy the integrity of ciphertext information, and inability to determine the group key, so as to resist attack threats and reduce investment costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
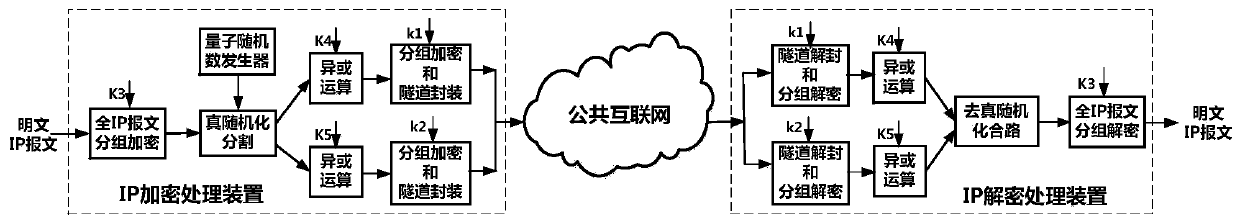
[0016] (1) Technical framework of the new IP secure communication method
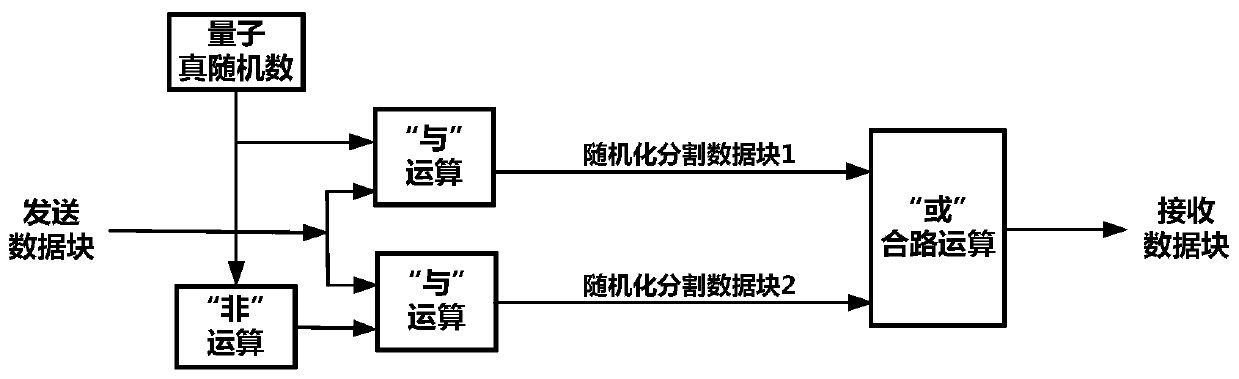
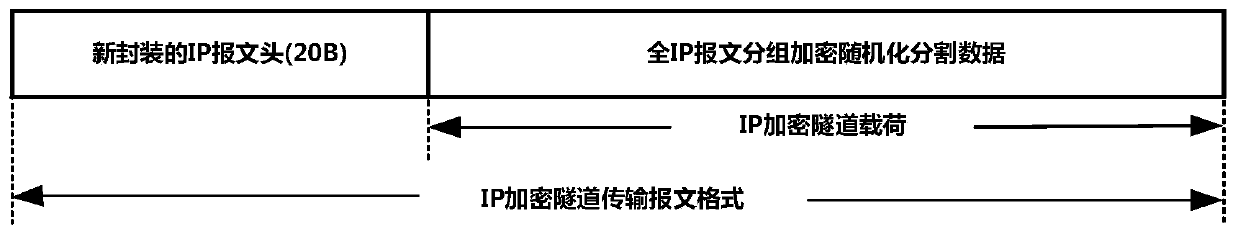
[0017] The core concept of the new high-security IP confidential communication method proposed by the present invention revolves around the true randomization and segmentation transmission technology of IP message content, and adopts three encryption mechanisms to provide transmission protection. For each plaintext IP message, three transmission protection mechanisms are respectively implemented: group encryption of all IP messages between IP encryption machines, true randomized segmentation and randomized XOR, and packet encryption of randomized segmented data blocks.
[0018] The present invention does not relate to the specific realization of dynamic key negotiation between IP encryption machines and IPSec message encapsulation between IP encryption machines.
[0019] 1. Realization architecture design of new high-security IP confidential communication method
[0020] In the new high-security IP con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com