File damage prevention method based on block chain and erasure code
A blockchain and erasure code technology, which is applied in the field of file anti-corruption based on blockchain and erasure code, can solve problems such as the inability of files to be used normally, the corresponding relationship between files is disordered, and the storage cost soaring, so as to avoid The risk of malicious tampering, the effect of increasing security, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
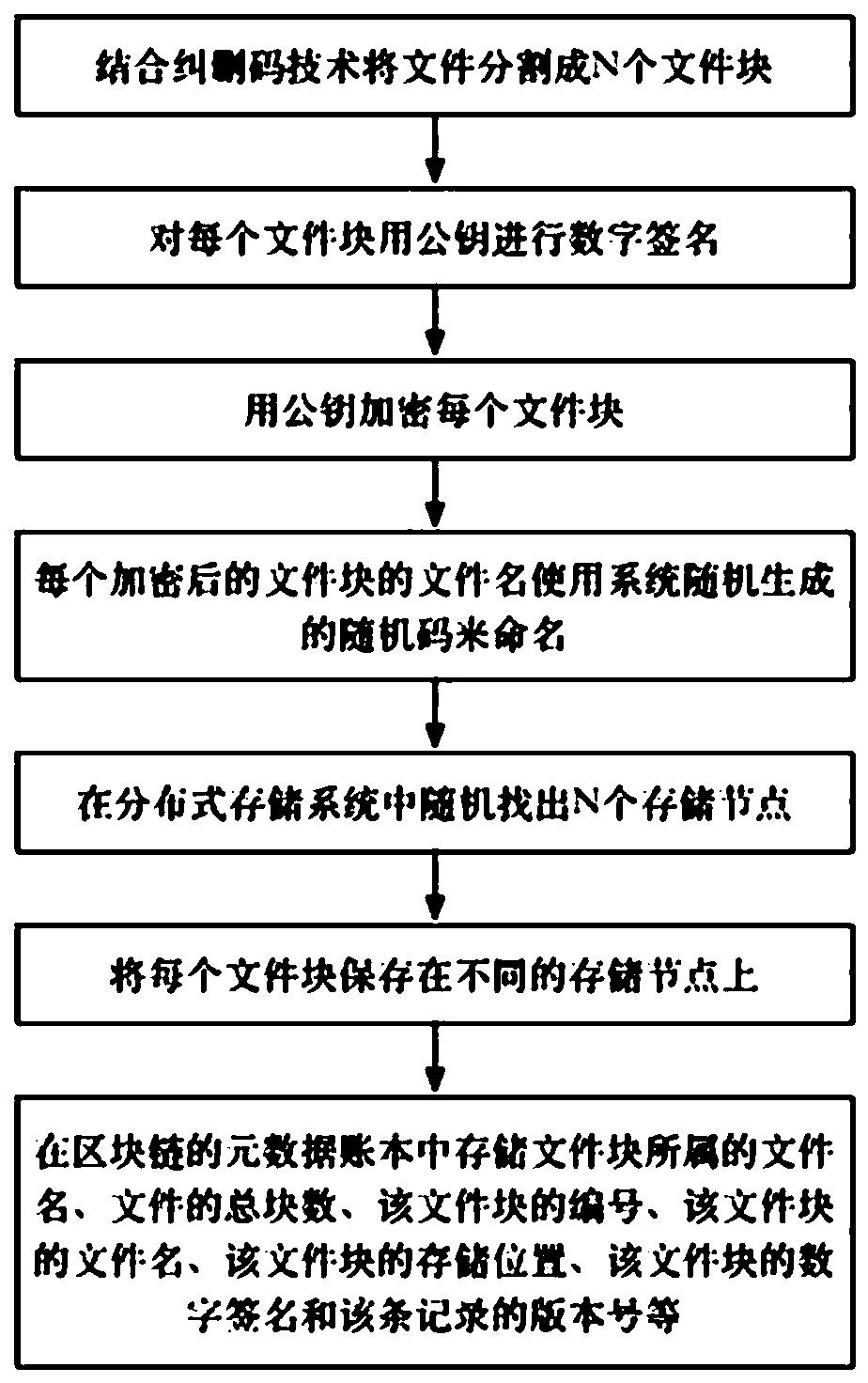
[0143] File storage method, see figure 1 , The detailed steps are as follows:
[0144] 1) Combine erasure coding technology to divide the file into N file blocks.
[0145] Erasure codes use RS codes, and the parameters (n, m) are uniformly configured according to the system. The parameter n indicates how many copies of the original file are to be divided, and the parameter m indicates how many check file blocks are required. A file is divided by the RS code with the parameter (n, m), and the number of file blocks after division is n+m. Among the n+m file blocks, only any n data blocks are needed to restore the entire file. For example, if it is configured as (6,3), it means that the file will be divided into 6 parts, and 3 check file blocks are required, so 9 file blocks will be generated in the end. Up to 3 file blocks are allowed to be destroyed in these 9 file blocks. Within this number range, the entire file can be restored.
[0146] 2) Digitally sign each file block with a p...
Embodiment 2
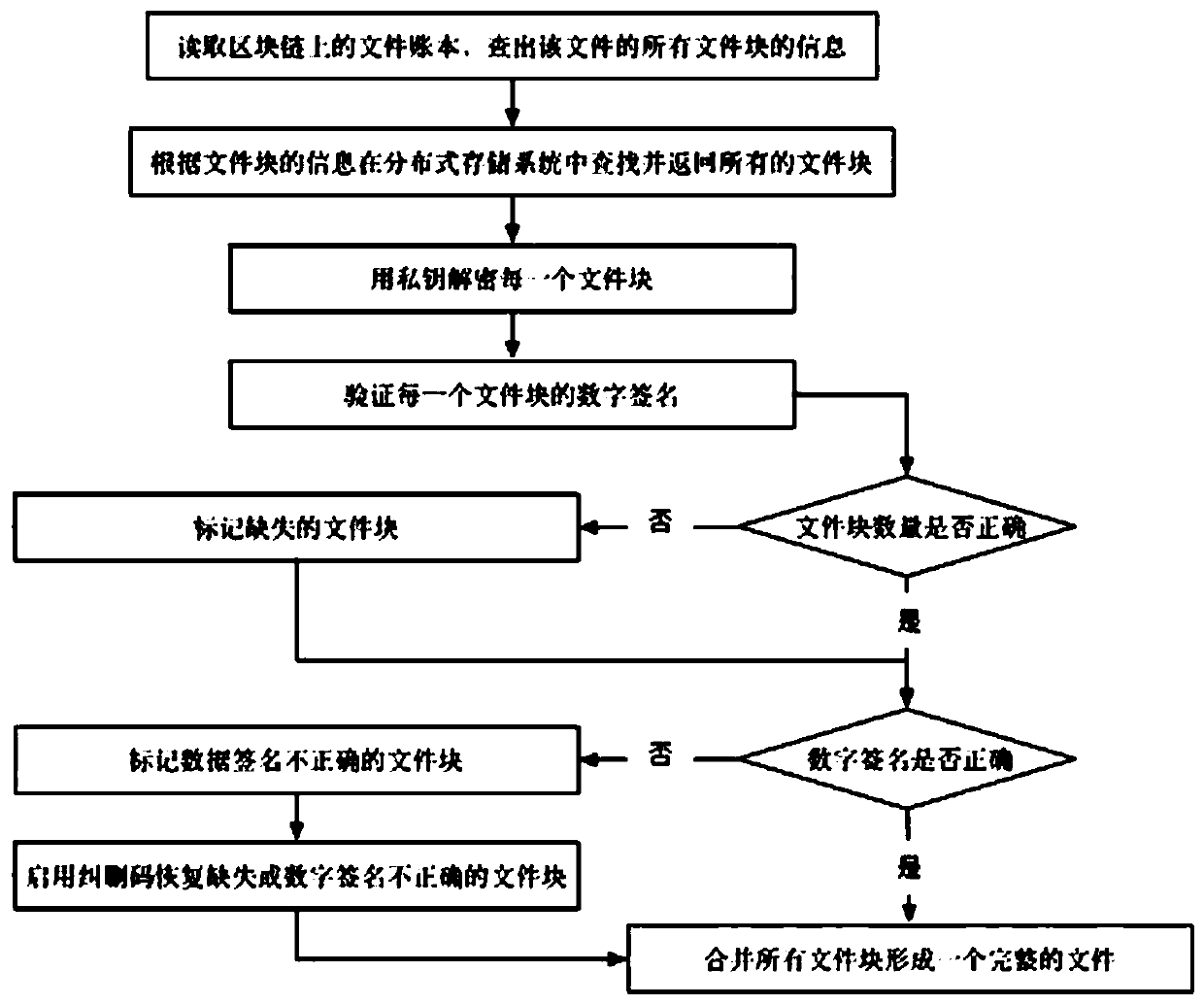
[0163] For the steps of file reading provided by the present invention, see 2. The detailed steps are described as follows:
[0164] 1) Read the file ledger on the blockchain to find out the information of all file blocks of the file.
[0165] Use the private key of the elliptic curve encryption algorithm to decrypt the file ledger on the blockchain. In the transactions data structure of the block body, find all the records whose FileName field is the file name that needs to be read. For example, the FileName field is ABIS_20180603123540_2051_000. All records of dat, and finally the record with the largest Version value is filtered out.
[0166] 2) Find and return all file blocks in the distributed storage system according to the file block information.
[0167] In the query result of the above step 1), obtain each file block from the corresponding storage node through the P2P protocol or through the RPC protocol according to the values of the BlockName and BlockLocation fields.
[0...
Embodiment 3
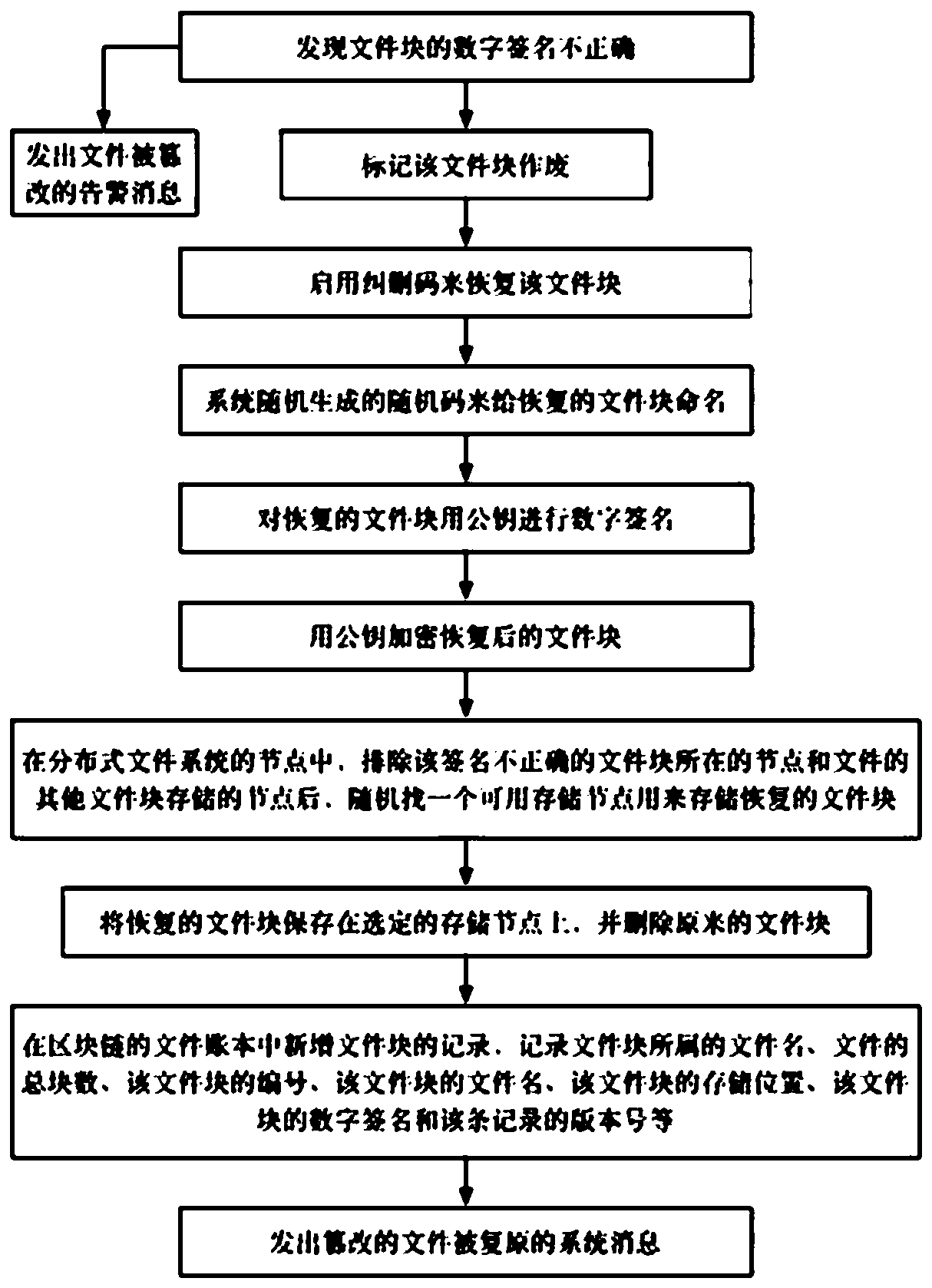
[0185] For the method of restoring a tampered file provided by the present invention, see 3. The detailed steps are as follows:
[0186] 1) It is found that the digital signature of the file block is incorrect.
[0187] In Embodiment 2, if the digital signature of a certain file block is found to be incorrect, it means that the file block has been tampered with, and the file block cannot be used.
[0188] 2) Mark the file block as invalid, and execute step 11) simultaneously.
[0189] The file block with incorrect digital signature is recorded in a list in the memory, and the file block is regarded as missing by the system. The system executes step 11) at the same time and sends out an alarm message.
[0190] 3) Enable erasure code to recover the file block.
[0191] Using erasure coding technology, the file block with incorrect digital signature is recovered through the correct file block, and the file block in the original state is obtained.
[0192] 4) The system randomly generates a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com