Encryption and decryption system based on SM2 and RSA encryption algorithms and working method
An encryption algorithm and encryption and decryption technology, applied in the field of encryption and decryption systems based on SM2 and RSA encryption algorithms, can solve the problems of complex calculation steps, high cost, and difficulty in compromising calculation speed and encryption system area, so as to reduce costs, The effect of high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
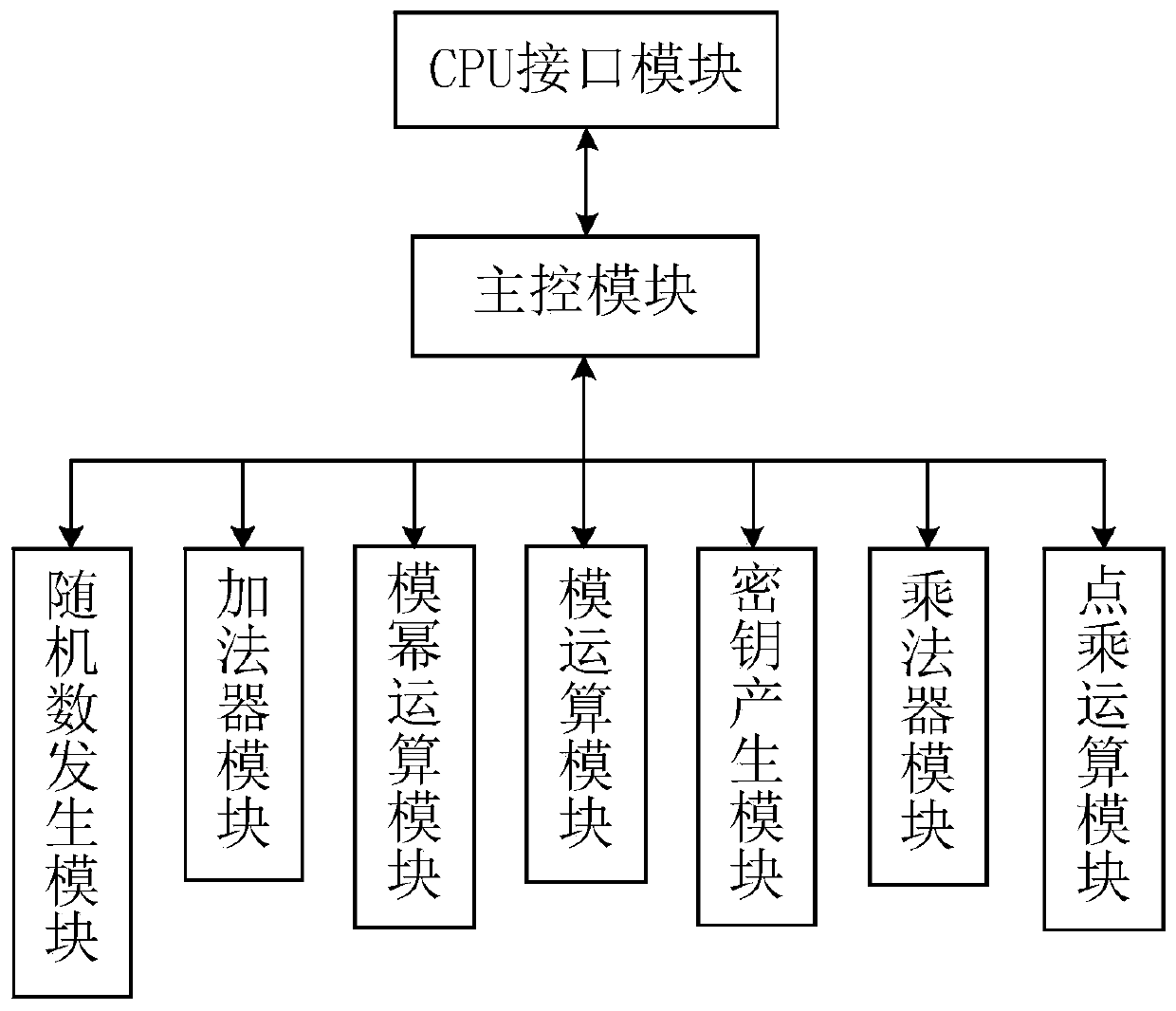
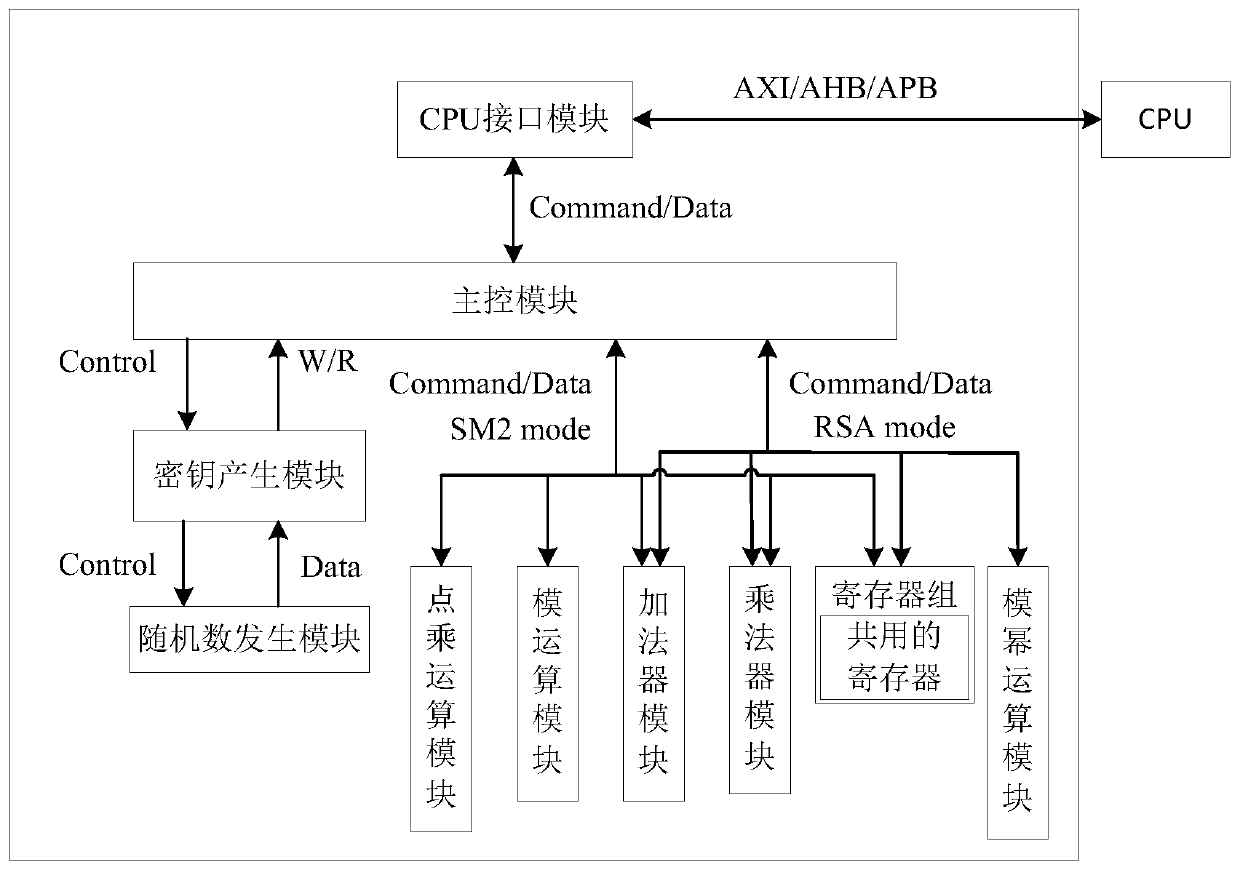
[0040] In order to reduce the area of the encryption and decryption system of the SM2 and RSA hybrid encryption algorithm, this scheme is based on the commonality of the multiplication and addition operations in the SM2 algorithm and the RSA algorithm, and the proposed technical scheme is:
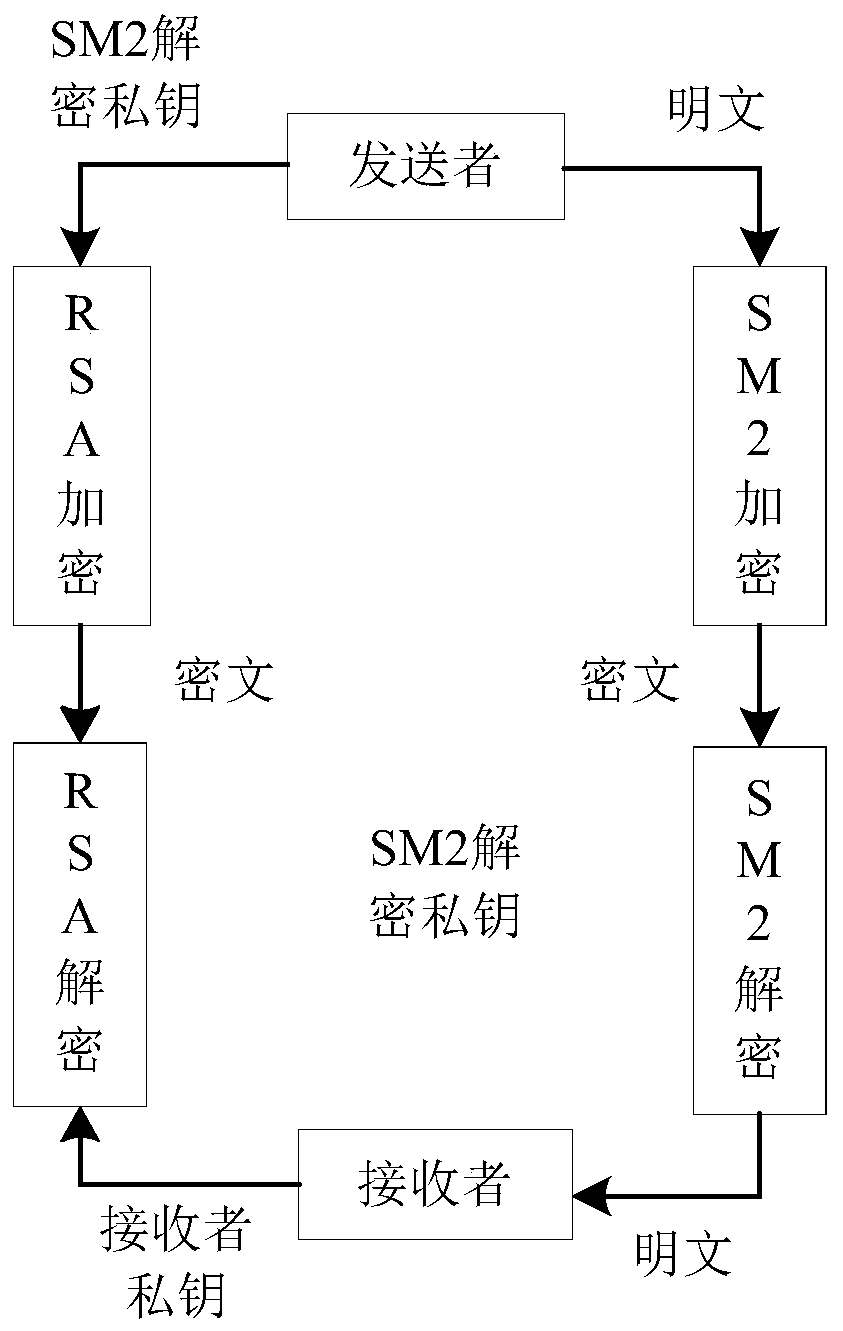
[0041] An encryption and decryption system based on SM2 and RSA encryption algorithms, including: a CPU interface module, a main control module connected to the CPU interface module, and a multiplier module, an adder module, and a modular operation module respectively connected to the main control module , dot product operation module, modular exponentiation operation module, random number generation module, and key generation module. In this system, modular control is adopted, and the larger multiplier, adder module and part registers of the consumption circuit area commonly used by shared SM2 and RSA operations make the circuit of the present invention consume more than the two encrypti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com