Binary collaborative security client architecture
A client and application client technology, which is applied in the fields of computer, network software, information security, and mobile terminals, can solve problems such as hidden viruses, authentication, encryption, signature counterfeiting fraud, information leakage, etc. The effect of preventing leakage and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
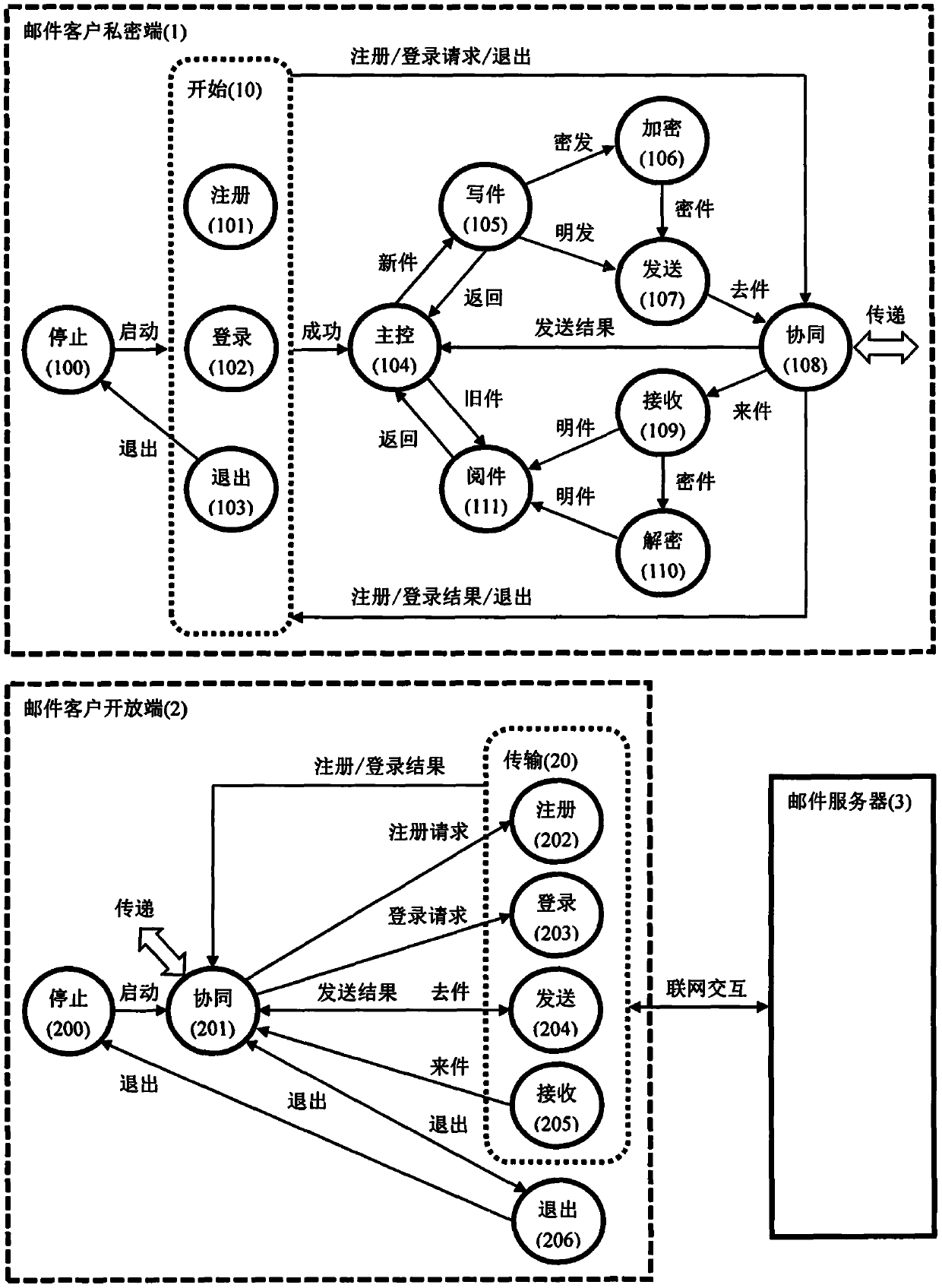
[0019] A dual collaborative and secure email service system client, referred to as the email client, is implemented below to illustrate a suitable implementation of the present invention. It should be noted that the following examples should not be understood as the entire possible scope of the present invention, nor should they be construed as limiting the rights of the present invention.
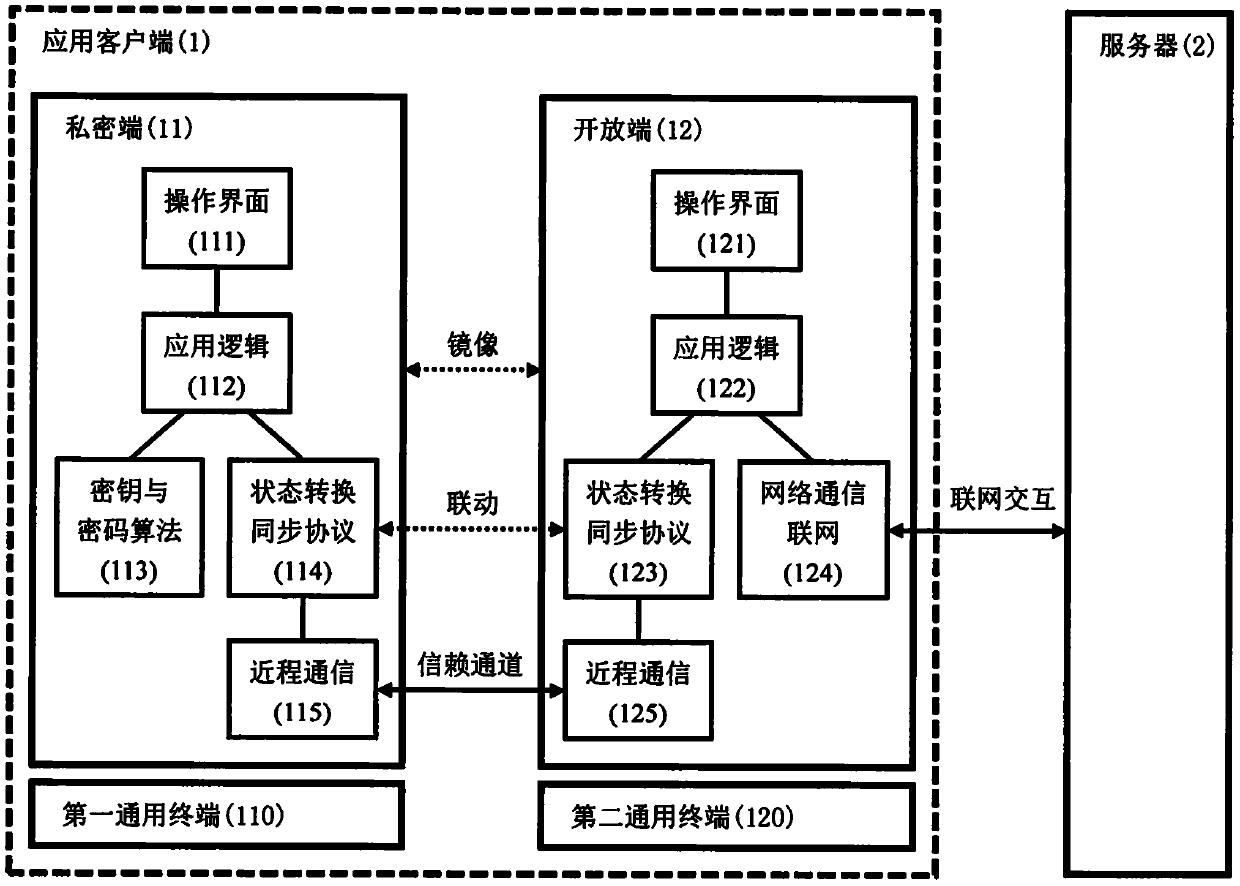
[0020] refer to figure 1 and its description. The application client (1), that is, the mail client, is binary distributed into two mobile phone APP program entities, the private end (11) and the open end (12), which will be installed on the first universal terminal (110) and the second universal terminal (110) respectively. Run concurrently on the terminal (120). The two general-purpose terminals are specifically two mobile phones, both of which are Android (Android) operating systems, and the short-distance interconnection between the two ends is realized through Bluetooth communication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com