Alarm intelligent analysis and display method
An intelligent analysis and post-analysis technology, applied in the network field, can solve problems such as imperfect configuration of policy rules, avalanche of alarms, inability to concentrate on troubleshooting network problems, etc., and achieve fast and efficient display, easy processing, and network alarm effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
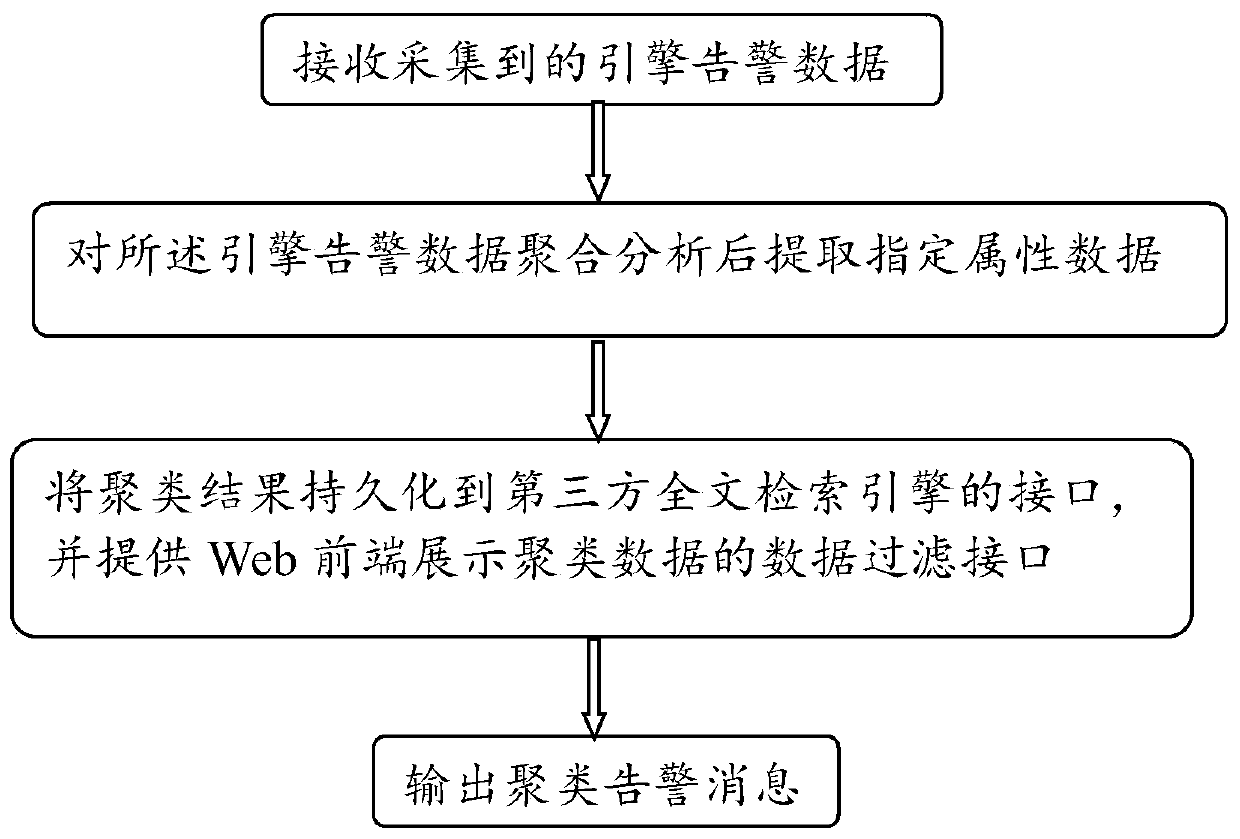
[0045] refer to figure 1 , this embodiment provides a schematic illustration of a method for intelligent analysis and display of alarms.
[0046] A method for intelligent analysis and presentation of an alarm comprises the following steps:
[0047] Step1: Receive the collected engine alarm data;
[0048] In this embodiment, the source of the engine's original alarm data is the network alarm monitoring and collection engine, and the engine sends the original alarm to the alarm collection module of the background service as Json data. Engine raw alarm data, for example, see attached Figure 7 .
[0049] attached Figure 7 Among the displayed attribute names, the most important attribute is the tag attribute, which is mainly used for cluster analysis, and alarms with the same tag are regarded as the same type of alarm.
[0050] Step2: extract specified attribute data after aggregation and analysis of the engine alarm data;
[0051] After consuming data from the acquisition ...
Embodiment 2
[0079] This embodiment allows for updating of the cluster analysis algorithm. The preferred embodiment is the same as the basic embodiment 1, and will not be repeated here.
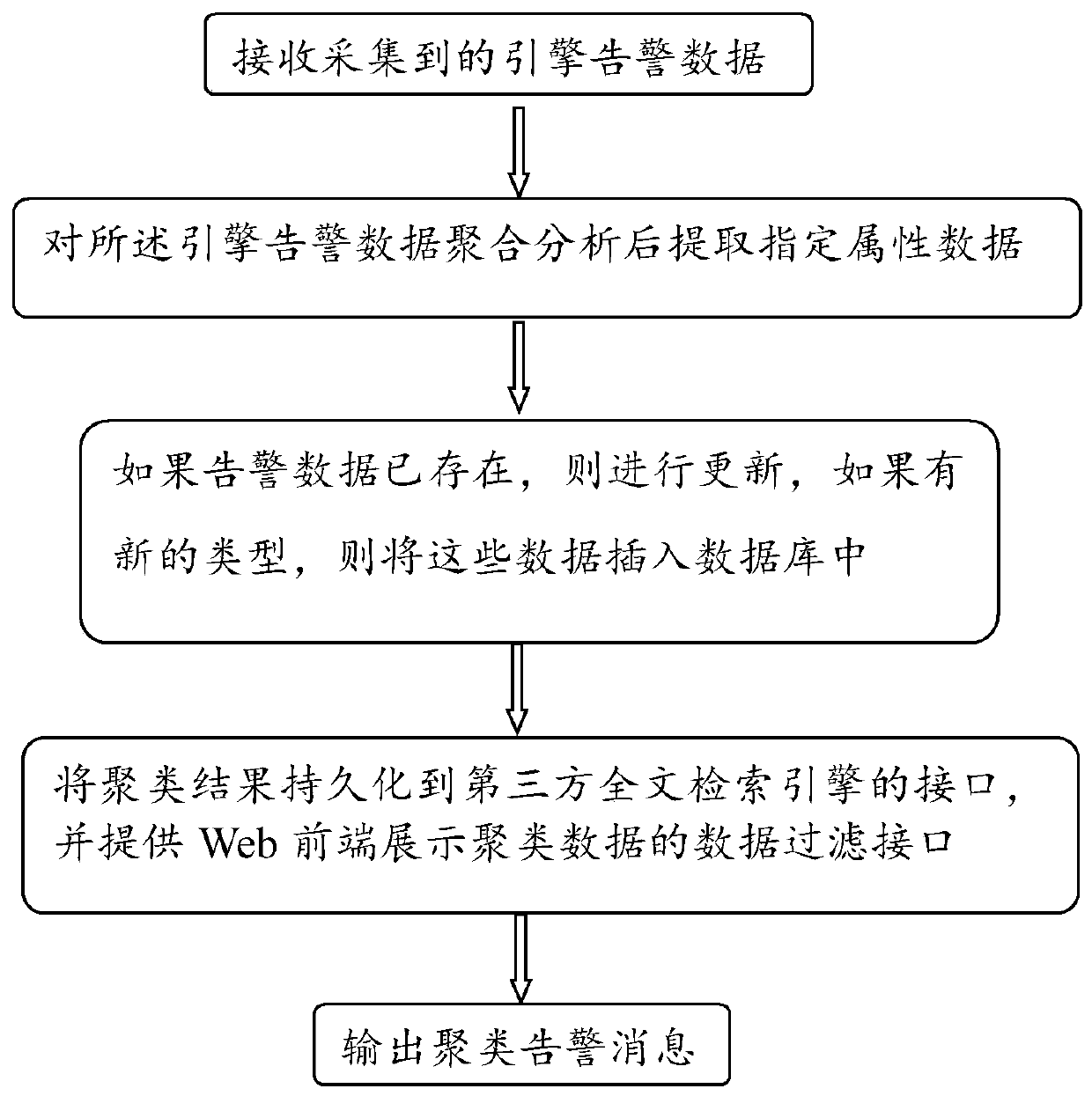
[0080] Such as image 3 As shown, a kind of alarm intelligent analysis and display method of this embodiment, said Step2 also includes:
[0081] Step21: If the alarm data already exists, update it, if there is a new type, insert the data into the database.
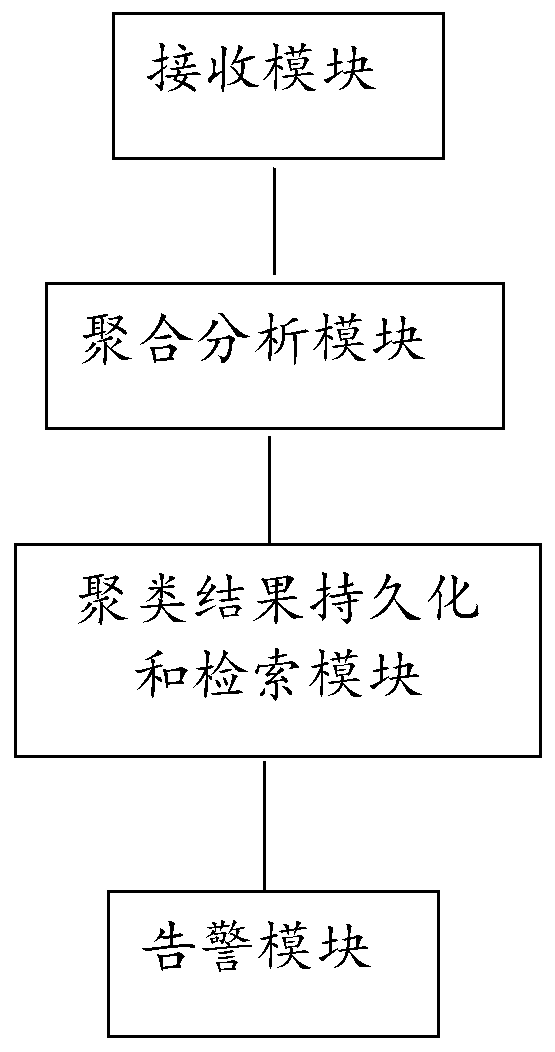
[0082] Correspondingly, an alarm intelligent analysis and display system of this embodiment, such as Figure 4 As shown, the aggregation analysis module also includes:
[0083] The update unit, if the alarm data already exists, it will be updated, if there is a new type, then these data will be inserted into the database.
[0084] If the alarm data has already existed, it will be updated with new data, and if it is new alarm data (tag has not appeared), these data will be inserted into the database.
Embodiment 3
[0086] In this embodiment, a preferred embodiment of a clustering algorithm is selected in consideration of the requirements for the aggregation function of the industrial control platform. The preferred embodiment is the same as the basic embodiment 1, and will not be repeated here.
[0087] Such as Figure 5 As shown, a method for intelligent alarm analysis and display in this embodiment, the aggregation analysis specifically includes:
[0088] Step21: Insert the engine alarm into the full-text search database ElasticSearch, and the ElasticSearch database indexes and encodes the original data according to the specified field, and establishes a mapping table for the encoding and alarm data;
[0089] When inserting into the database, the database builds an index (inverted index) on the original data according to the above-mentioned alarm feature Tag field, that is, encodes the Tag, and creates a mapping table between the code and the alarm data, so that it can be aggregated w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com