User group identification method and device, electronic equipment and storage medium
An identification method and user technology, which is applied in the computer field, can solve problems such as misidentification, low identification accuracy, and the inability to rule out the influence of normal users' accidental consistent behavior, so as to avoid the influence of noise data and improve the recognition accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
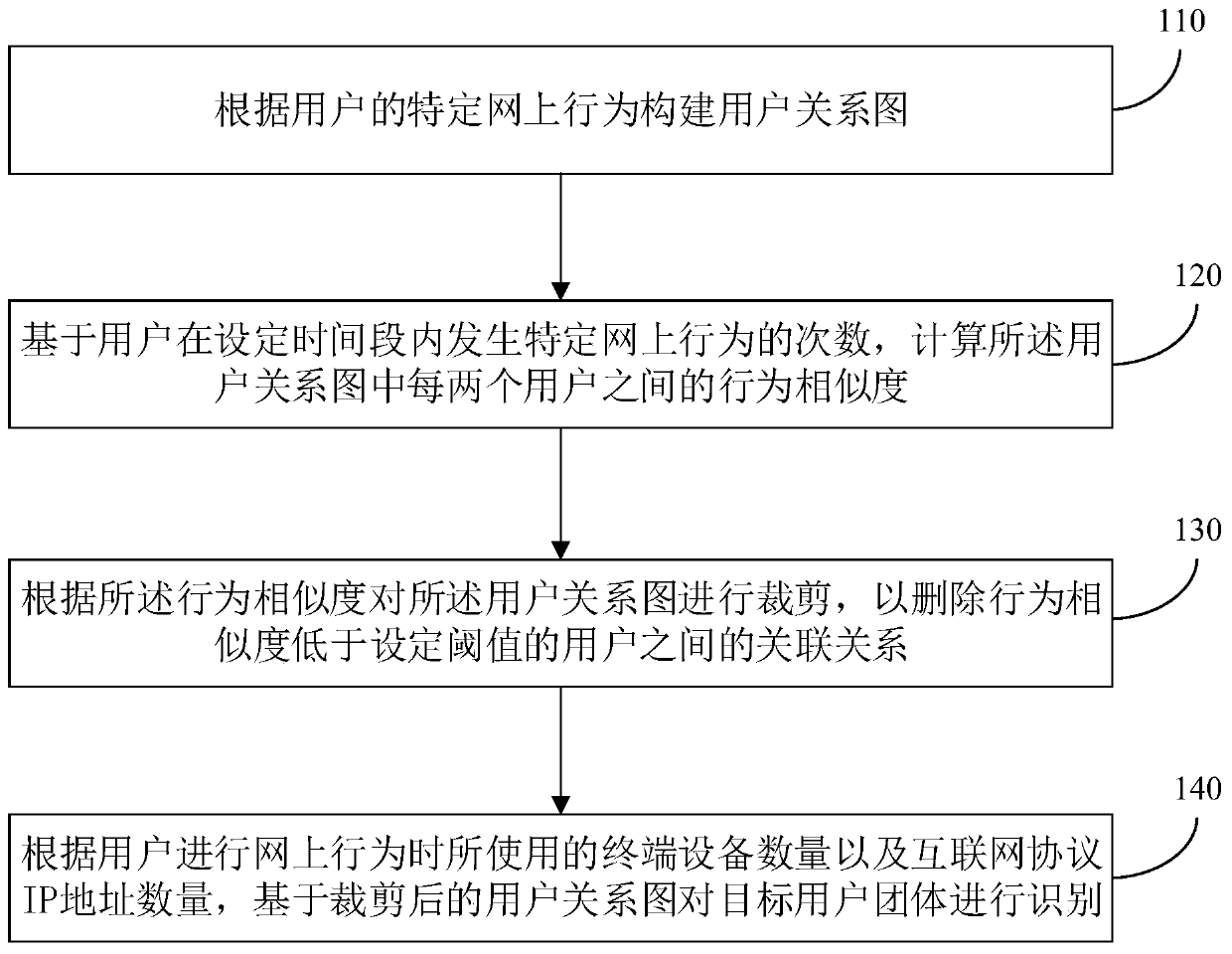
[0026] figure 1 It is a schematic flowchart of a user community identification method provided in Embodiment 1 of the present invention. The user group identification method disclosed in this embodiment can be applied to identify user groups engaged in online cheating behaviors, for example, to identify user groups who perform online cheating behaviors such as barrage and attention in the live broadcast room, which can be identified by user groups device, wherein the device may be implemented by software and / or hardware, and generally integrated into a terminal, such as a smart phone or a computer. For details, see figure 1 As shown, the method includes the following steps:
[0027] Step 110, constructing a user relationship graph according to the user's specific online behavior.
[0028] Wherein, the specific online behavior may specifically be a positive behavior worth advocating, such as online donation, or a negative behavior that needs to be resisted, such as the behav...
Embodiment 2
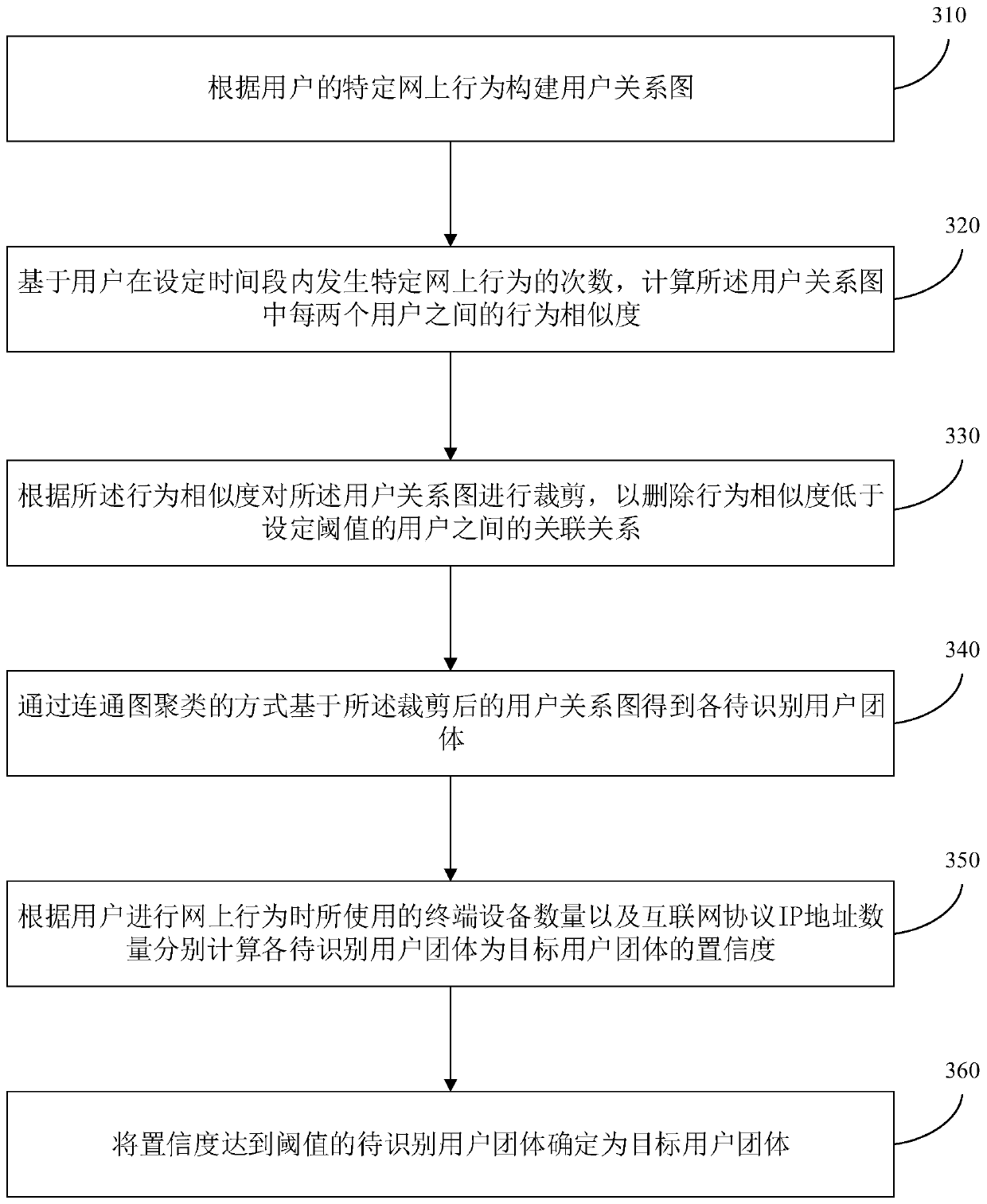
[0053] image 3 It is a schematic flowchart of a user group identification method provided by Embodiment 2 of the present invention. On the basis of the above embodiments, this embodiment performs step 120 "based on the number of times a user has a specific online behavior within a set period of time, calculate the The behavior similarity between every two users in the above user relationship diagram" and the step "according to the number of terminal devices and the number of Internet protocol IP addresses used by users when performing online behaviors, respectively calculate the confidence that each user group to be identified is the target user group Degree" gives the specific implementation, see image 3 As shown, the method includes:
[0054] Step 310, constructing a user relationship graph according to the user's specific online behavior.
[0055] Step 320 : Calculate the behavior similarity between every two users in the user relationship graph based on the number of t...
Embodiment 3
[0088] Figure 4 It is a schematic structural diagram of a user community identification device provided by Embodiment 3 of the present invention. see Figure 4 As shown, the device includes: a construction module 410, a calculation module 420, a cropping module 430 and an identification module 440;
[0089] Among them, the construction module 410 is used to construct a user relationship graph according to the user's specific online behavior; the calculation module 420 is used to calculate the number of times that the user has a specific online behavior within a set period of time, and calculate every two times in the user relationship graph. Behavioral similarity between users; clipping module 430, configured to clip the user relationship graph according to the behavioral similarity, so as to delete associations between users whose behavioral similarity is lower than a set threshold; identification module 440 , which is used to identify the target user group based on the ta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com