A method and device for processing abnormal nodes
A normal node, node technology, applied in the computer field, can solve the problem of no flood attack solution.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
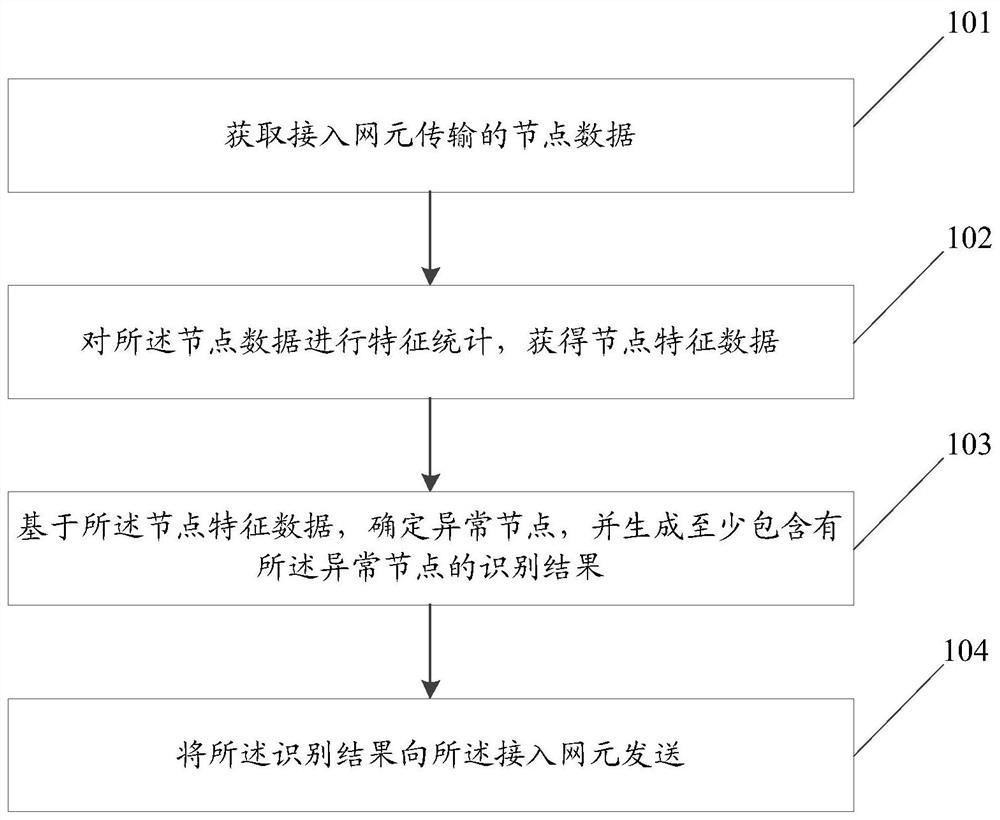
[0092] figure 1 A schematic flowchart of a processing method for a node to identify an entity-side abnormal node according to an embodiment of the present invention, such as figure 1 As shown, the processing method of the node identifying the abnormal node on the entity side according to the embodiment of the present invention includes the following steps:
[0093] Step 101: Acquire node data transmitted by an access network element;
[0094] The node data includes at least two kinds of data, one is control plane information, such as resource request messages, and the other is data plane information, such as service messages sent by nodes.
[0095] Step 102: perform feature statistics on the node data to obtain node feature data;
[0096] Wherein, according to the preconfigured node characteristic parameters, statistics are performed on the control plane information and data plane information when the node interacts with the access network element, and the control plane char...
Embodiment 2
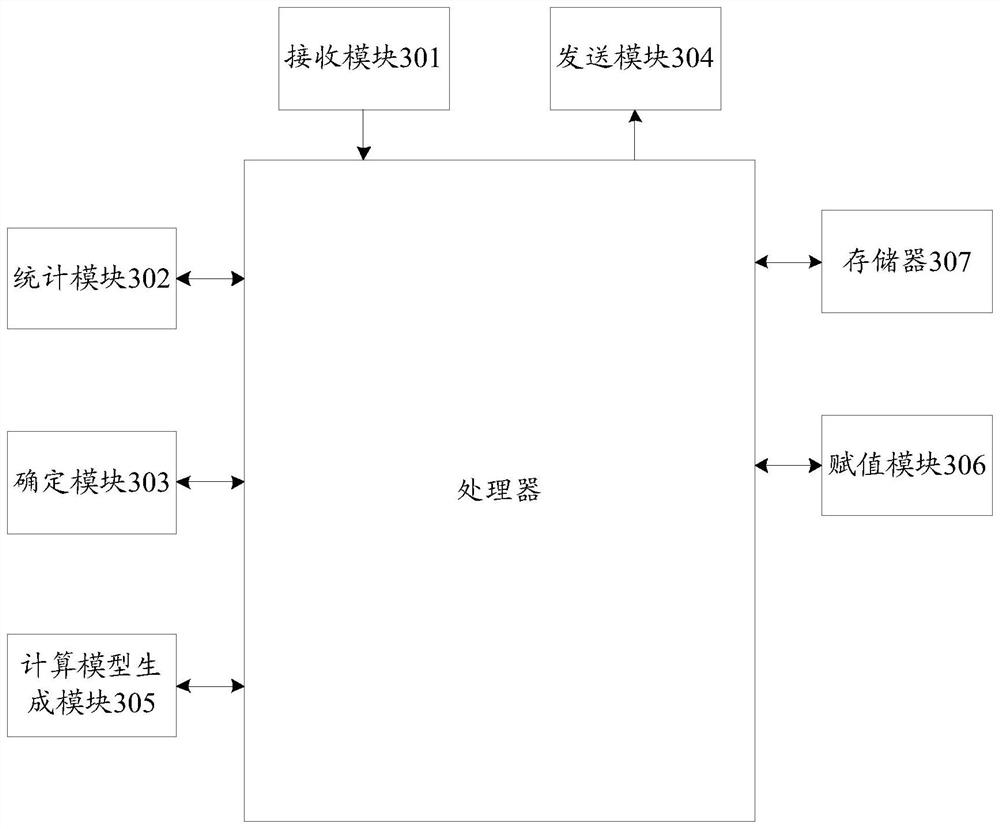
[0153] image 3 It is a schematic diagram of the composition structure of the node identification entity according to the embodiment of the present invention, such as image 3 As shown, the composition of the node identification entity in the embodiment of the present invention includes: a receiving module 301, a statistics module 302, a determining module 303, and a sending module 304; wherein,
[0154] A receiving module 301, configured to acquire node data transmitted by an access network element;
[0155] A statistics module 302, configured to perform feature statistics on the node data to obtain node feature data;
[0156] A determination module 303, configured to determine an abnormal node based on the node characteristic data, and generate an identification result including the abnormal node;
[0157] The sending module 304 sends the identification result to the access network element.
[0158] Wherein, the above-mentioned node data at least includes the control plan...
Embodiment 3
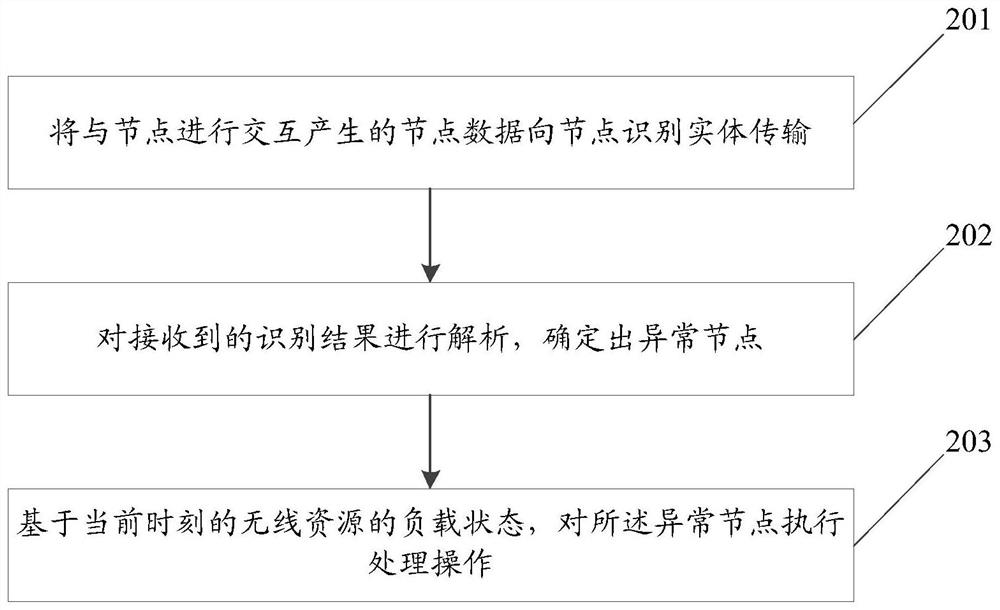
[0203] Figure 5 A schematic structural diagram of a processing system for an abnormal node according to an embodiment of the present invention, as shown in Figure 5 As shown, the structure of the abnormal node processing system according to the embodiment of the present invention includes: a node 501, a base station 502, and a node identification entity 503; wherein,
[0204] The node 501 forms an inter-vehicle network with other vehicles in the Internet of Vehicles system, and the inter-vehicle network is connected to the Internet through the base station 502, and the node 501 and the base station 502 are interconnected based on a unified wireless communication protocol. The node identification entity 503 can be set at the edge of the access network in the Internet of Vehicles, so as to reduce the end-to-end delay of mobile service delivery and improve user experience.
[0205]When the node 501 has services to transmit, the node 501 sends a resource request signaling to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com