Bidirectional anonymous secret communication protocol using bulletin board
A communication protocol and bulletin board technology, applied in the computer field, can solve the problems of selfish and anonymous abuse of nodes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0087] Example 1 Anonymity Analysis
[0088] Using the two-way anonymous secret communication protocol of the bulletin board, the identity privacy of both communication parties can be hidden.
[0089] Theorem 1. The receiving node cannot obtain the identity information and location information of the sending node.
[0090] Proof 1:
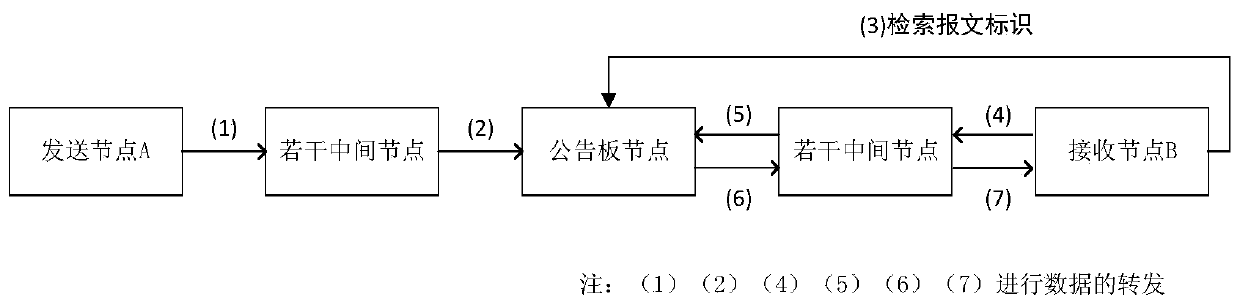
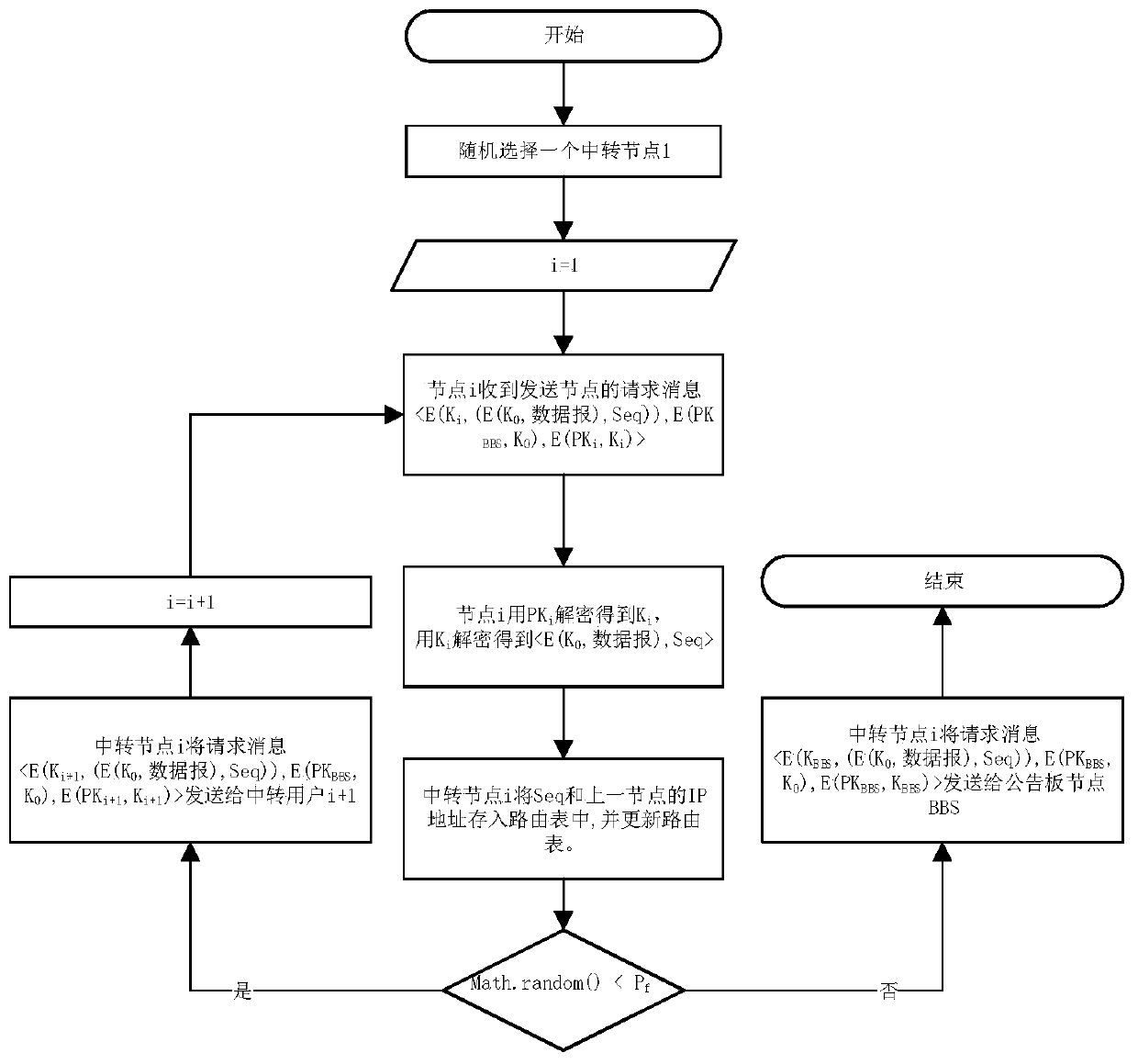
[0091] In the present invention, the bulletin board is used as a special node, and the message sent by the sending node is sent to the bulletin board node, not directly to the receiving node. There is no identity information of the sending node in the encrypted data sent, and the receiving node can only receive the message ID published by the bulletin board node, and the message ID does not contain the identity information of the sending node. Therefore, the receiving node has no knowledge of the identity information and location information of the sending node. On the other hand, Theorem 3 proves that it is impossible for bulletin board nodes ...
Embodiment 2
[0110] Embodiment 2 confidentiality analysis
[0111] Before sending the message, the sending node encrypts the message with the public key of the receiving node and then sends it out. Only when the receiving node can decrypt with its own private key can the plaintext of the message be decrypted. Any transit node does not have the private key of the receiving node, so it is impossible to decrypt the plaintext of the initial message. Similarly, any attacker does not have the private key of the receiving node, so even if it intercepts the ciphertext of the message in transmission, it cannot obtain the plaintext of the message.
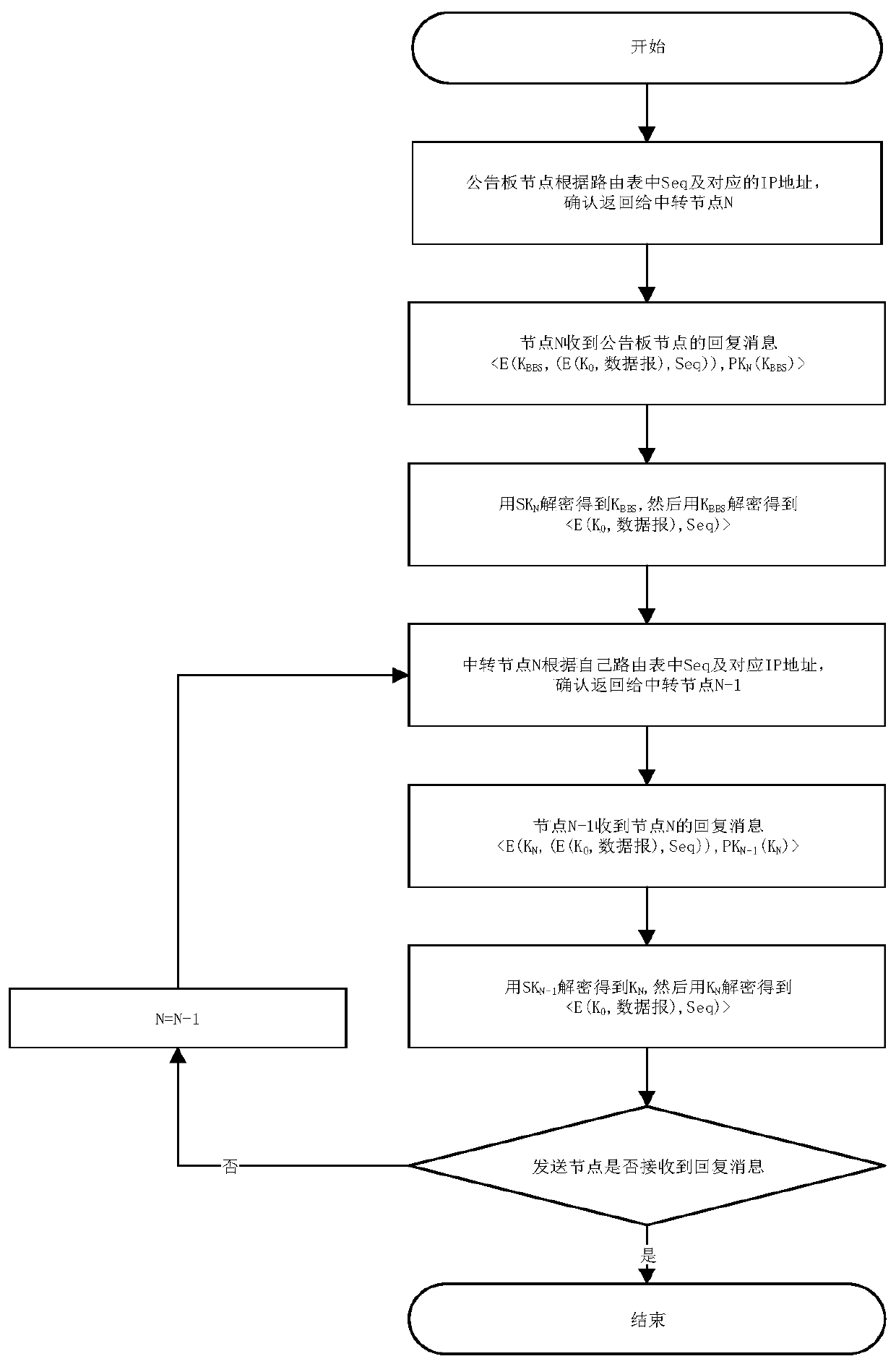
[0112] In the process of the bulletin board node replying the message to the receiving node, the data it sends is still encrypted using the public key of the receiving node. In addition to the receiving node, any third party including the transit node and the attacking node can Impossible to decrypt.
[0113] In summary, this protocol can realize secr...
Embodiment 3
[0114] Embodiment 3 robustness analysis
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com