Sequencing method based on fully homomorphic encryption
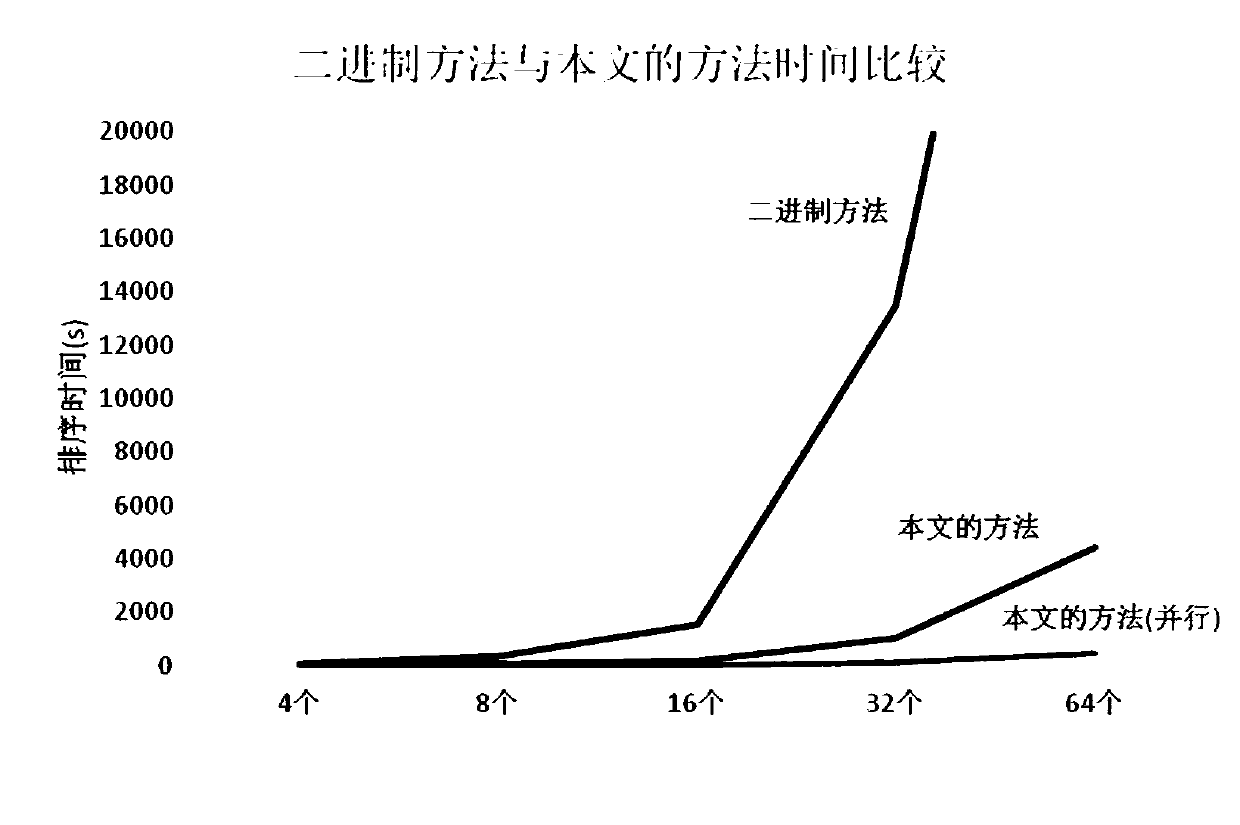
A fully homomorphic encryption and sorting method technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of low efficiency, reduce the amount of calculation, improve efficiency, reduce space complexity and time complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
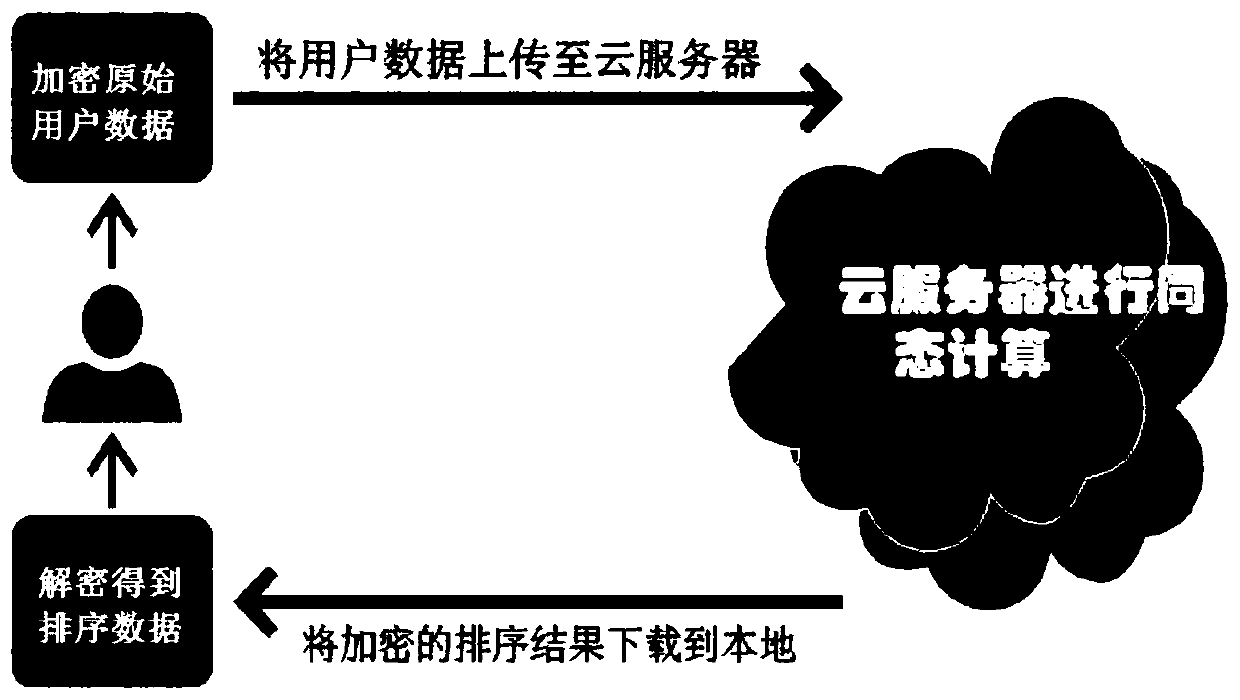
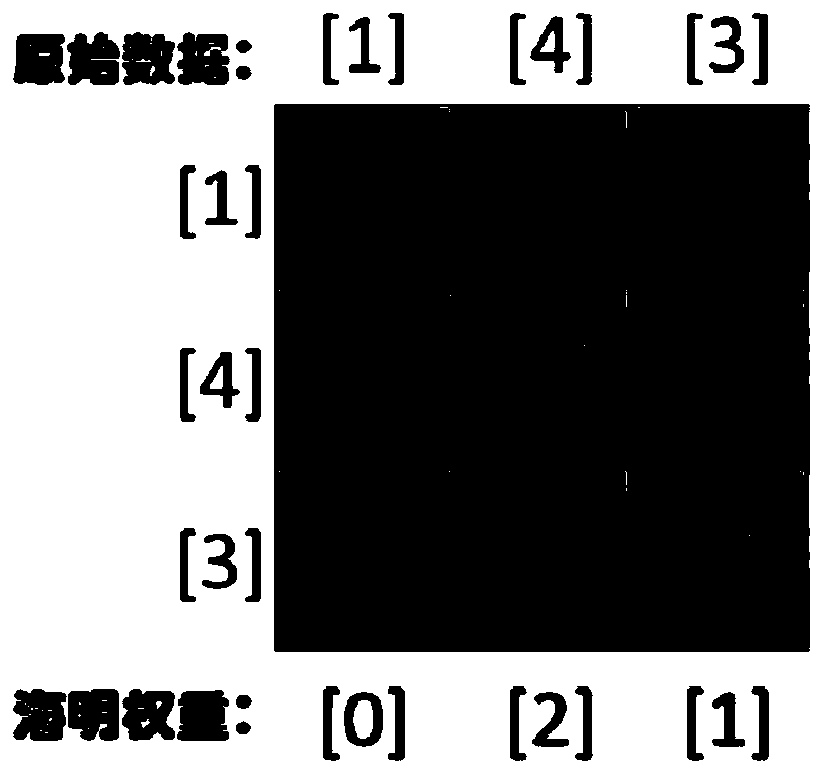
[0046] In order to make the features and advantages of the present invention more obvious, the present invention will be described in detail and completely below in conjunction with the accompanying drawings of the present invention.figure 1 It is a schematic flow chart of the present invention, which mainly includes a data encryption / decryption method and a homomorphic computing method. The client executes the encryption method, encrypts and uploads the data to be sorted to the cloud server; the cloud server executes the homomorphic computing method, sorts the ciphertext without decryption, and returns the sorted result in the form of ciphertext to the user; finally, the client performs decryption to obtain the requested sorting result. figure 2 To compare the calculation process of the matrix and the Hamming weight (only the constant term is shown in the figure, the specific process is explained in step 2, step 3 and step 4).
[0047] Step 1: Collect industrial data A that ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com