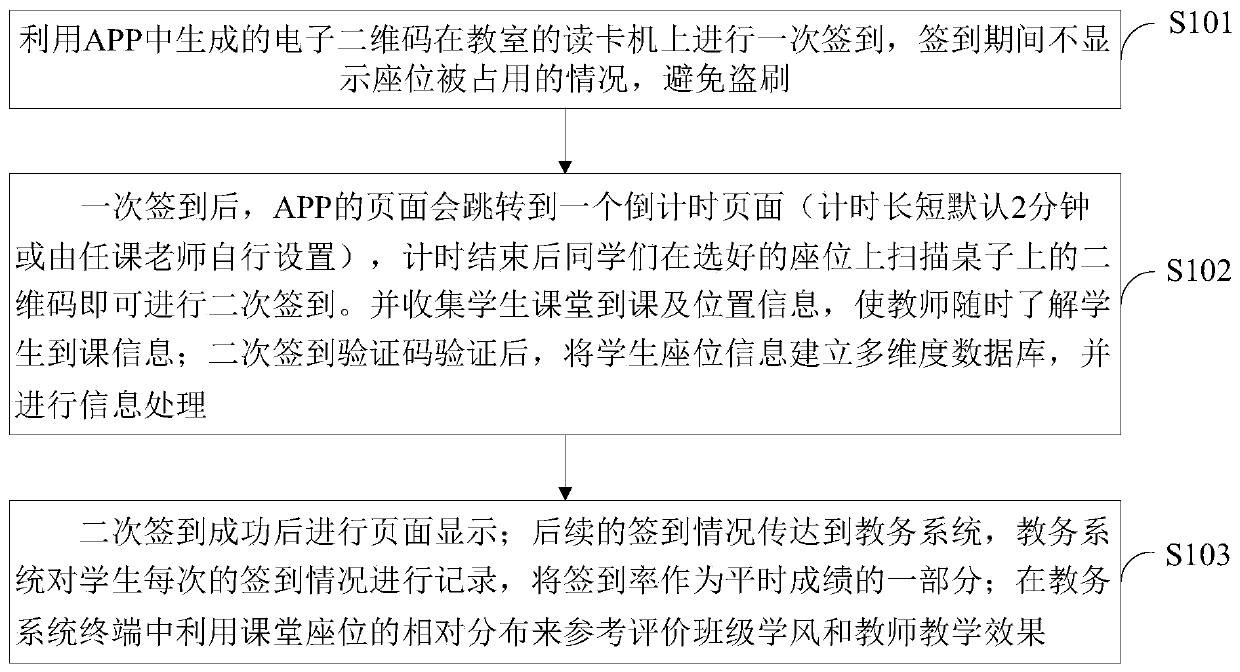
Sign-in APP coupled with electronic campus card and student classroom information base construction method
A construction method and campus card technology, applied in the direction of digital data information retrieval, multi-dimensional database, database model, etc., can solve problems such as disputes between teachers, omissions, effective use of classroom information using big data technology, and low dimensionality of sign-in data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
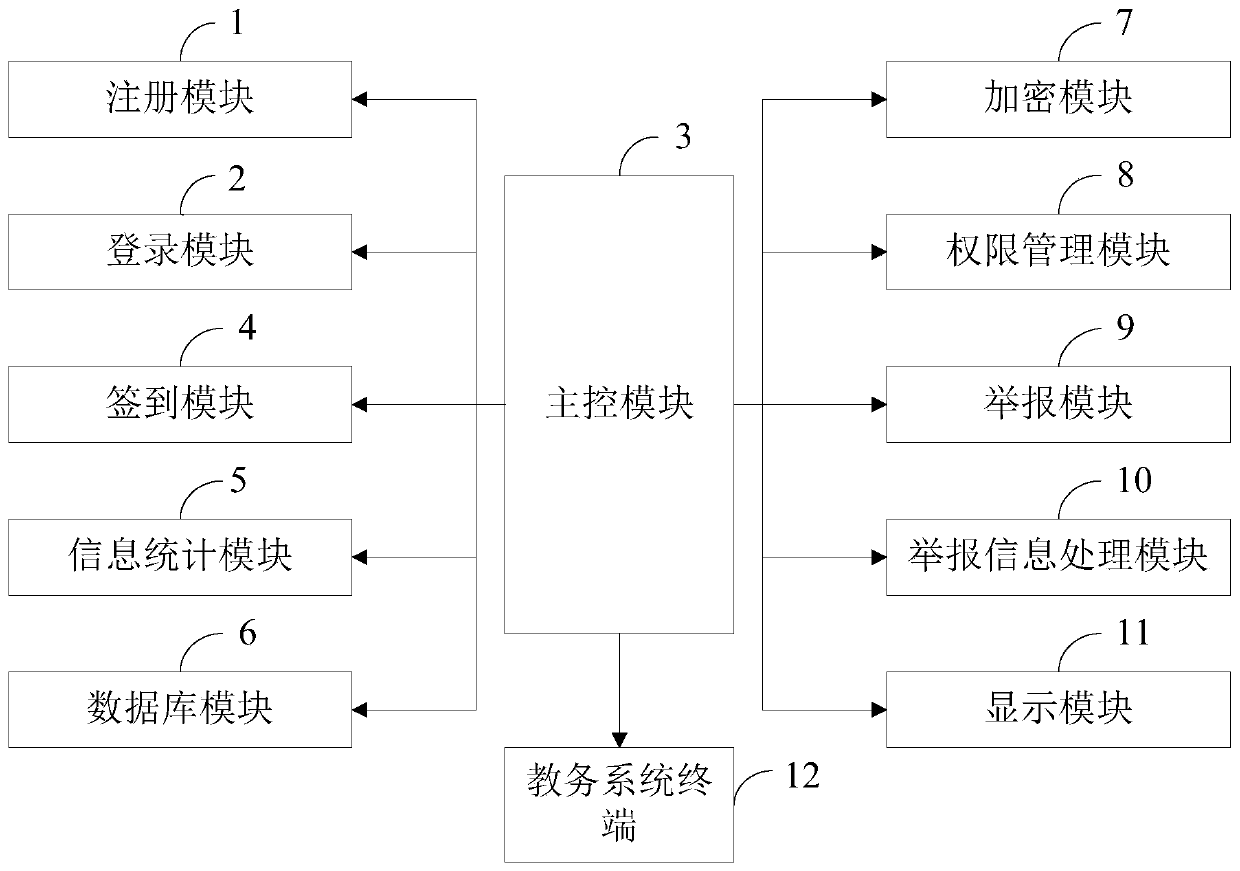
[0122] The encryption module 7 encryption method that the embodiment of the present invention provides comprises:
[0123] (1) Receive the data to be encrypted, the initial key value, and the mask value through the encryption program, and after the data to be encrypted is XORed with the masked value, then XORed with the initial key value to generate XORed mask data , this process takes time t.
[0124] (2) Perform row conversion processing on the XOR mask data to generate row conversion data, and perform split processing on the second converted data to generate first split data, second split data, and third split data Data and the fourth split data, this process takes time t.
[0125] (3) Randomly select the first split data for re-split processing to generate four groups of first re-split data, randomly perform byte replacement processing on the first re-split data of the four groups at the same time, generate four A group of byte substitute data is reassembled for four gro...
Embodiment 2
[0136] The rights management module 8 management methods provided by the present invention include:
[0137] 1) Obtain the authorization information from the received authorization SQL statement through the management program.
[0138] 2) When the authorization information includes the column identifier, add the authorization record generated according to the authorization information to the column authorization data table of the metadata database; when the authorization information does not include the column identifier, add the authorization record according to the The permission record generated by the authorization information is added to the table permission data table of the metadata database.
[0139] 3) When receiving the access SQL statement, perform table-level authority verification on the access SQL statement according to the authority record in the table authority data table, and when the table-level authority verification fails, according to the column authority da...
Embodiment 3
[0141] The management method provided by the embodiment of the present invention also includes:
[0142] Obtain revocation information from the received permission revocation SQL statement.
[0143] When the recycling information includes a column identifier, search for a permission record matching the recycling information in the column permission data table; when the recycling information does not include a column identifier, search in the table permission data table Find a permission record that matches the reclaim information.
[0144] Delete the found permission records.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com