Internet of Vehicles equipment identity authentication method based on blockchain technology
A device identity and authentication method technology, applied in user identity/authority verification, digital transmission systems, electrical components, etc., can solve problems such as inability to guarantee security, and achieve the effect of space performance and safety performance advantages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] like Figure 1-Figure 4 As shown, a method for identity authentication of Internet of Vehicles devices based on blockchain technology,
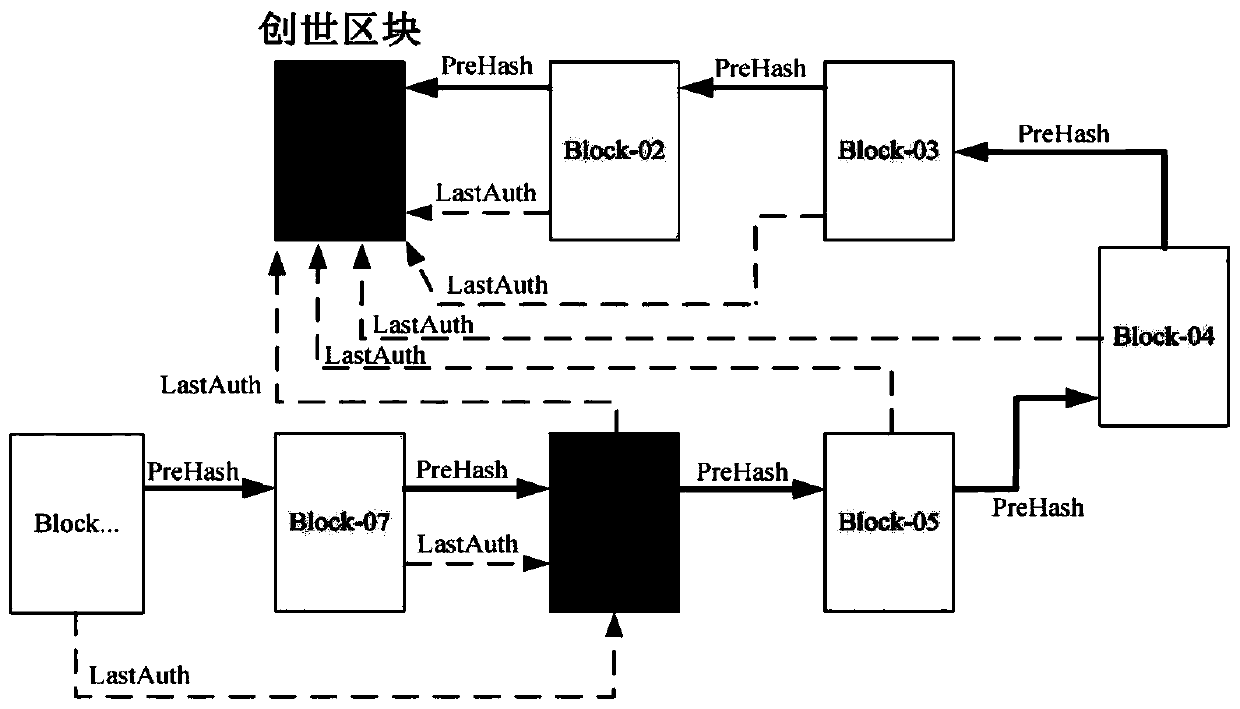
[0038] This method builds a distributed blockchain CA system based on the blockchain idea, and completes the identity authentication of the communication nodes of the Internet of Vehicles through the CA blockchain design; the blocks in the blockchain are updated by authoritative nodes and newly added certificate blocks Composed of, the blocks are connected by double chains, such as figure 2 The two chains shown are the authoritative node update chain and the common chain, the authoritative node update chain connects the adjacent authoritative nodes, and the common chain directly connects the adjacent blocks without distinguishing the block type; all The communication nodes can query the synchronous CA blockchain, and the authoritative node has the authority to generate blocks. Through the confirmation mechanism of the blockchain, it ...
Embodiment 2
[0041] 1. The update design of the authoritative node update block and the newly added certificate block is as follows:
[0042] 1) The authoritative node update block consists of a 240-byte block header and a variable-length block body, such as image 3 shown. The block header field includes the 4-byte current block version number Version, the 32-byte previous block hash value PreHash, the 32-byte current block content hash value ContentHash, the 8-byte block generation time stamp TimeStamp, and the 64 Byte public key AuthorPubkey of the current block generator, 64-byte block signature Signature, number of new and old authoritative nodes NodeNum in the 4-byte block body, and 32-byte last authoritative node block hash LastAuthBlock. The block body content of the authoritative node update block is divided into two parts, which are expressed in utf8 plaintext encoding. The block body contains the list of all authoritative node public keys that have become effective, the generat...
Embodiment 3
[0045] 2. The architecture design and identity authentication mechanism of CA blockchain authentication system are as follows:
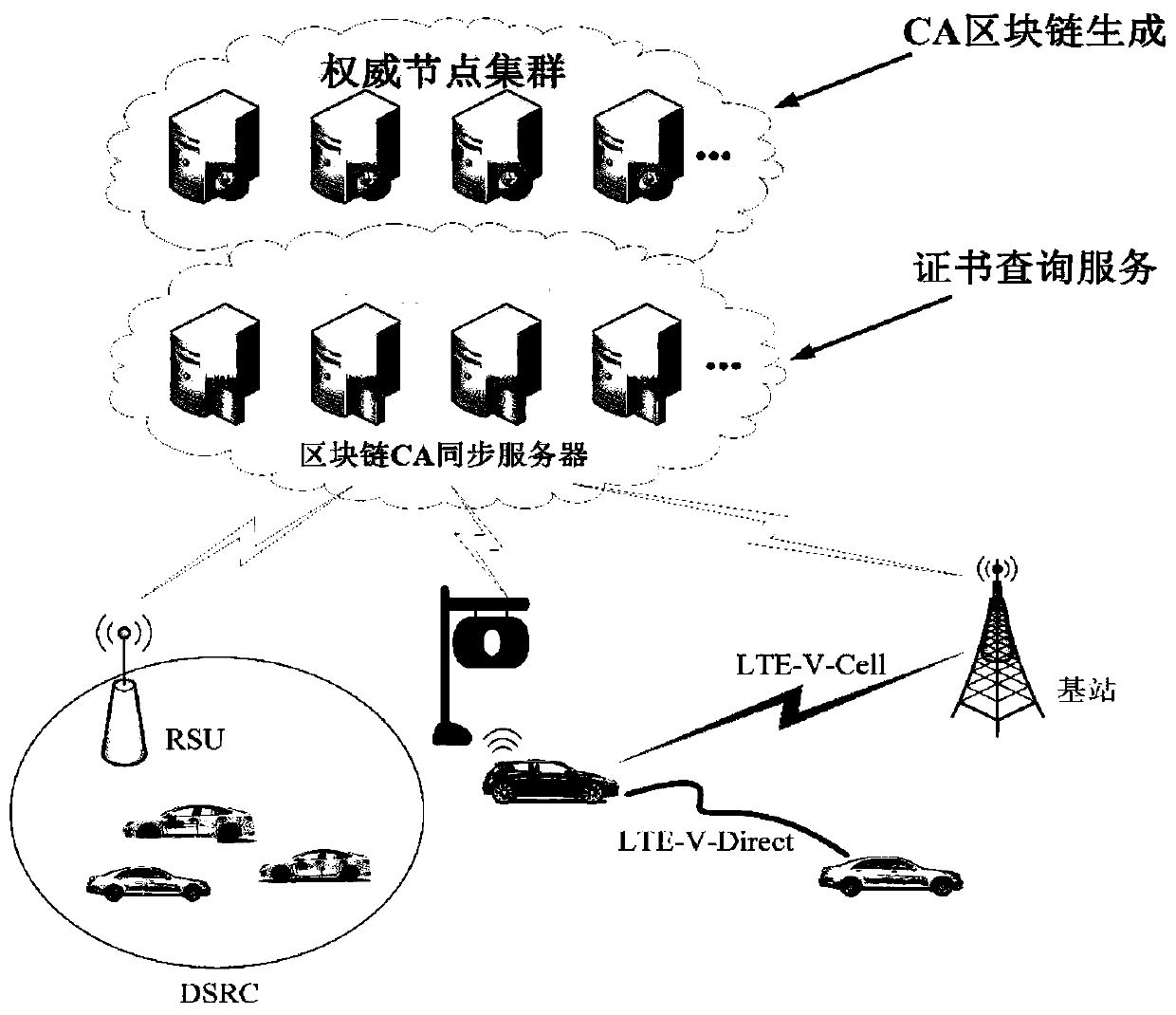
[0046] The working scenario of the distributed CA authentication system architecture is as follows: figure 1 shown. The authoritative node cluster and blockchain CA synchronization server in the figure are cloud CA blockchains; traffic lights and vehicle communication nodes belong to end devices, and each end device obtains the required node certificate through OBU via RSU or base station to communicate with the cloud. In the figure, the cloud CA blockchain consists of two parts: the authoritative node cluster and the blockchain CA synchronization server. The authoritative node cluster is the block producer of the blockchain. Only the authoritative nodes have the authority to add new blocks. They pass distributed A consensus algorithm keeps the blockchain in sync. The synchronization server is used to receive the certificate query request of the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com