Method and system for detecting abnormal network traffic
A network anomaly and detection method technology, applied in the field of network information security, can solve the problem of difficult detection of local outliers, and achieve the effect of narrowing the feature space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be further described now in conjunction with accompanying drawing.
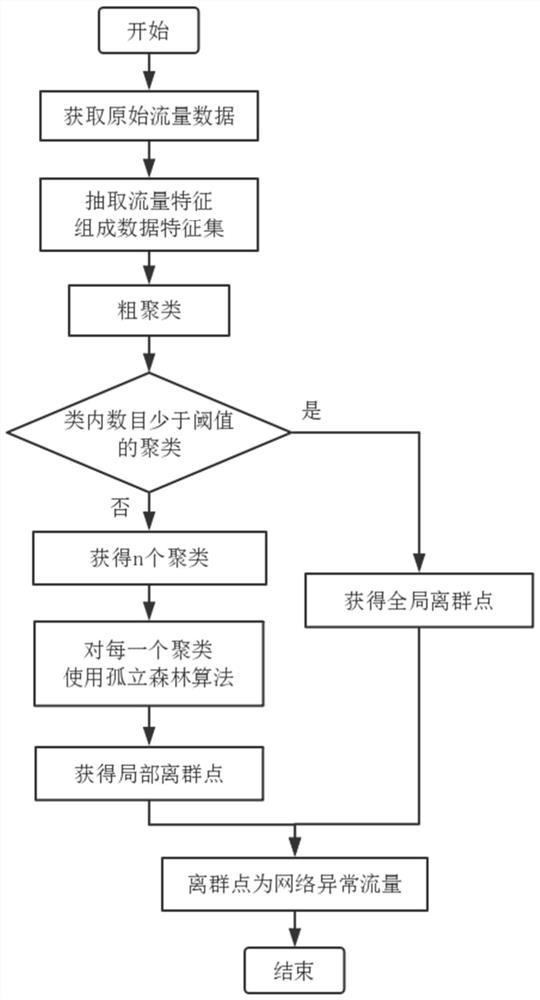
[0057] Such as figure 1 As shown, the present invention provides a method for detecting abnormal network traffic, the method comprising:
[0058] Step 1) obtaining traffic data, preprocessing the traffic data, extracting traffic features, and forming a data feature set; including the following steps:
[0059] Step 1-1) intercept the data flow packet from the network, gather a series of data with the same source address, destination address, source port, destination port and protocol into a data flow, usually gather the data packet into a bidirectional flow;
[0060] Step 1-2) construct training data set X={X 1 , X 2 ,...,X n}, where each flow data sample X i Include feature dimension A={a 1 , a 2 ,...,a m}, where all features a k It is the normalized value, 1≤k≤m.
[0061] Features include: flow duration, time between two packets in forward flow, time between two pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com