Big data desensitization method and system
A data desensitization and desensitization technology, applied in the field of information security, can solve the problem of desensitization complexity and desensitization algorithm flexibility, lack of sensitive data classification and more fine-grained management, lack of mature methods and processes, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] The present invention provides a kind of big data desensitization method, it is characterized in that comprising the following steps:
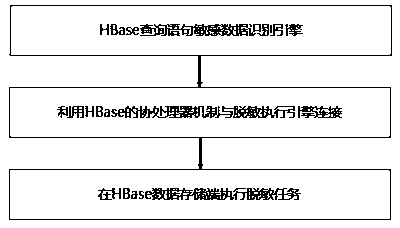
[0041] Such as figure 1 As shown, the flow of the big data desensitization method is as follows:
[0042] S1: Sensitive data identification
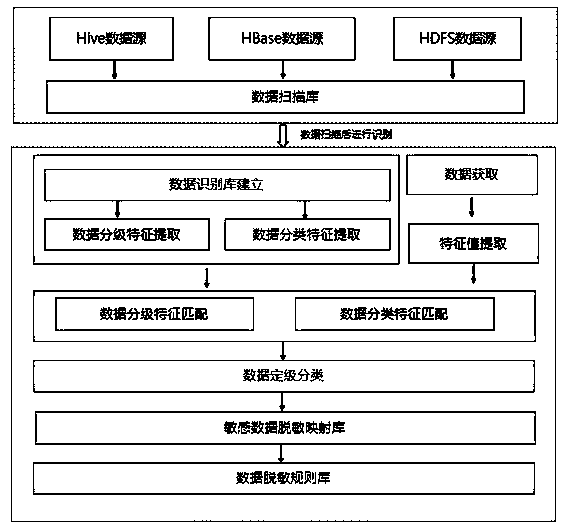
[0043] S10: Sensitive data scanning. In this embodiment, a full data scan is performed on the Hadoop big data platform, HDFS, Hive, and HBase data sources are found, and data samples and metadata are collected.
[0044] S11: Data format analysis. Obtain descriptions of HDFS file names, Hive, HBase database table names, columns, etc., analyze the format and content of source data, and realize sensitive information identification through data feature matching.
[0045] It should be noted that for different sources and types of data, the detection methods for sensitive features will be different. In this embodiment, a sensitive information database can be established for different source data cl...
Embodiment 2
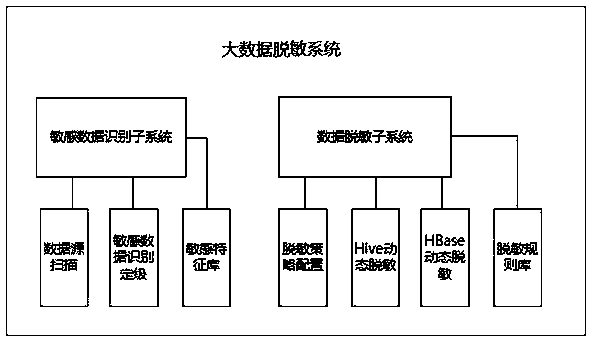
[0095] The present invention provides a big data desensitization system, specifically as follows.
[0096] The big data desensitization system includes two subsystems of sensitive data identification and data desensitization.
[0097] Such as Figure 4 As shown, the functional modules of the big data desensitization system are as follows:
[0098] S5: Sensitive Data Identification Subsystem
[0099] The sensitive data identification subsystem includes a data source scanning module, a sensitive data identification and grading module, and a sensitive feature database management module.
[0100] S50: the data source scanning module is configured to scan and discover the full amount of data on the Hadoop platform, and obtain Hive and HBase source data.
[0101] S51: The sensitive data identification and grading module is configured to discover sensitive data, classify and classify sensitive data, automatically detect sensitive information fields in the database through the conf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com