DDoS attack detection method based on chaos theory analysis
A technology of chaos theory and attack detection, applied in the direction of secure communication, digital transmission system, and electrical components through chaotic signals, can solve difficult problems such as network behavior supervision and auditing, and achieve strong purpose and deterministic effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
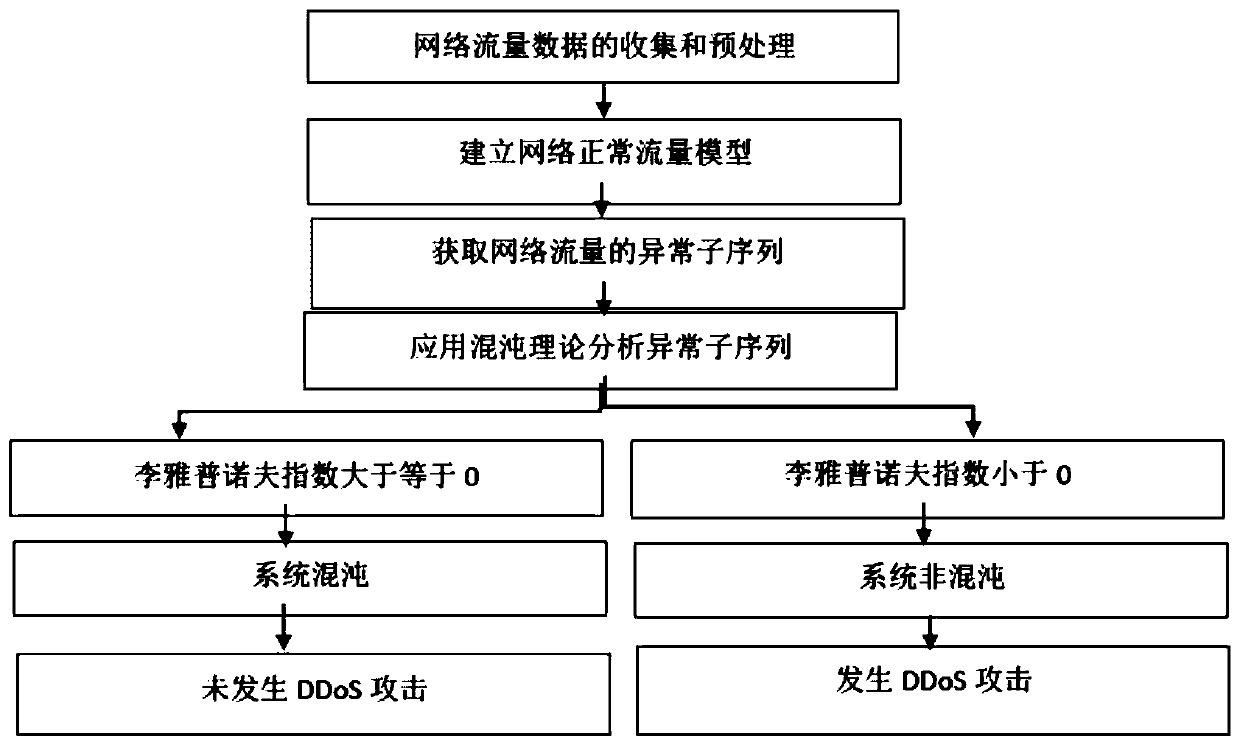
[0072] The present invention uses readable files of network data information to construct a normal network traffic model, and then designs a network distributed abnormal behavior detection algorithm based on chaos theory. The process is as follows:
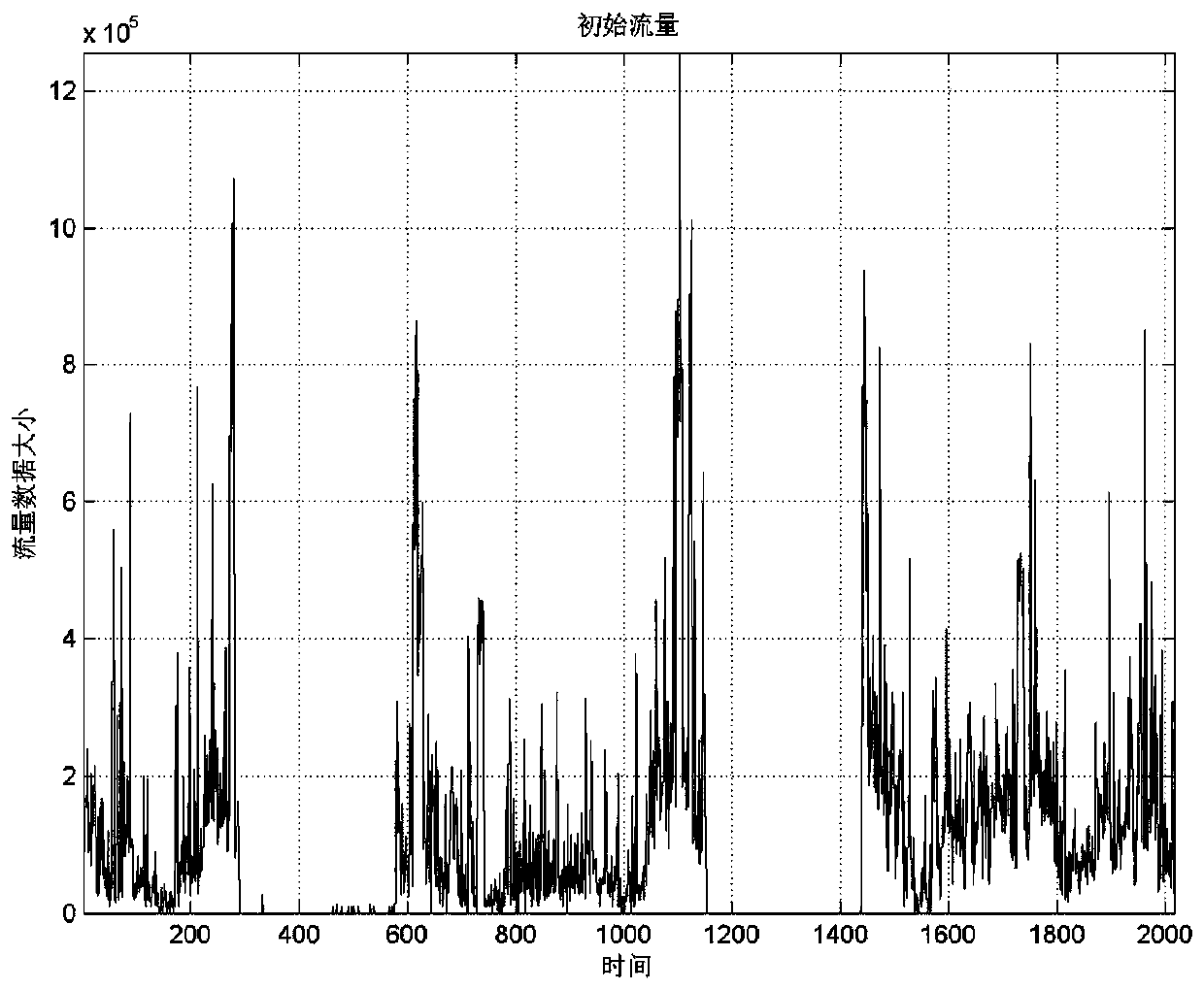
[0073] 1. Collect large-scale communication network traffic data, and preprocess the traffic information according to the needs of the research.
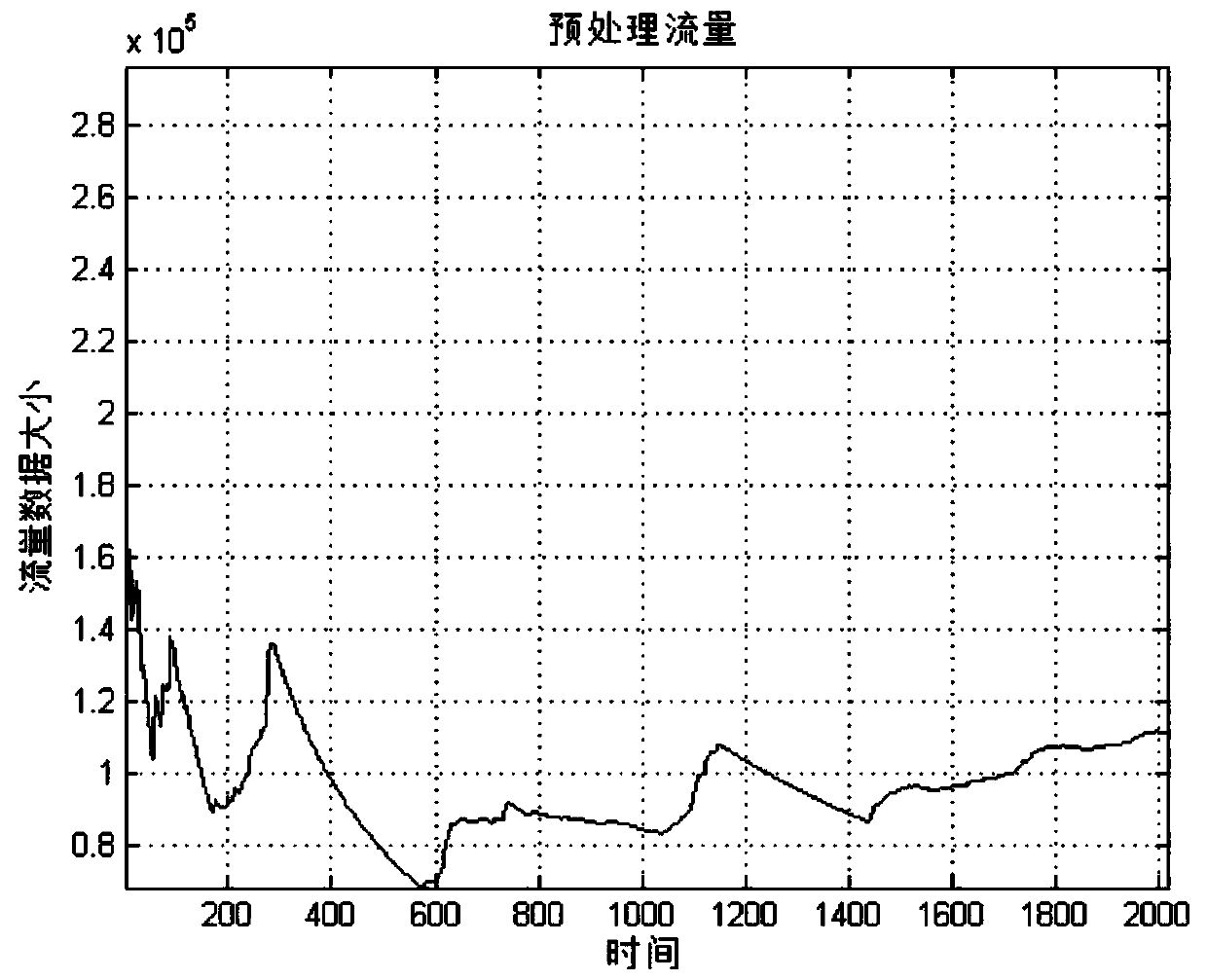
[0074] 2. Use the sequence prediction algorithm in the time series model to establish a normal network traffic model.
[0075] 3. The predicted normal model of network traffic is subtracted from the measured value of network traffic to obtain the corresponding innovation sequence, thereby obtaining the abnormal subsequence of network traffic.
[0076] 4. Use the Lyapunov exponent in chaos theory to analyze the abnormal subsequence, and detect whether the system is chaotic or non-chaotic at the current moment.
[0077] 5. If a DDoS attack occurs, the current system is non-chaotic. The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com