Meta-knowledge federation method for behavior analysis, device, electronic equipment and system
A behavior analysis and knowledge technology, applied in the computer field, can solve the problems of user account security cannot be guaranteed, server-side data leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
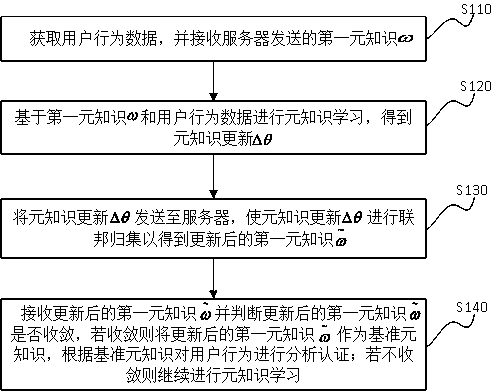
[0047] Embodiment 1 provides a behavior analysis-oriented meta-knowledge federation method, which aims to obtain the updated first meta-knowledge by sending the meta-knowledge update to the server through federated aggregation, and judge the updated first meta-knowledge. Whether the unary knowledge is convergent or not, the converged first meta-knowledge is used as the benchmark meta-knowledge to realize the analysis and authentication of user behavior. This method can ensure that user behavior data will not leave the client, thereby effectively protecting user data privacy, and can also ensure that each user data is used for learning to obtain more accurate meta-knowledge; the client only needs to collect a small amount of user behavior data , combined with the updated first meta-knowledge obtained by federated collection, you can quickly obtain stable custom meta-knowledge, so as to realize the analysis and authentication of user behavior on any client device, which is suitab...
Embodiment 2
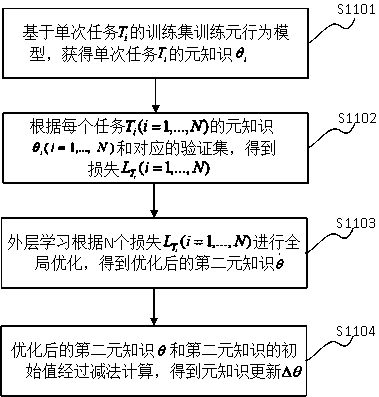
[0072] Embodiment 2 is an improvement on the basis of Embodiment 1. Meta-knowledge is learned through N tasks Meta-based model training and optimization to obtain meta-knowledge update , the meta-knowledge update As the user data of the client is sent to the server, the privacy of user data on the client is effectively protected. Please refer to figure 2 As shown, meta-knowledge learning includes the following steps:
[0073] S1101. Train the meta-basic model based on the training set of a single task to obtain a single task meta-knowledge .
[0074] For a single task , using the task The training set of the meta-basic model is trained for M iterations. From time step t=0 to t=M-1, based on the preset loss function L and gradient descent algorithm, the task parameters update to , the initial value of the parameter primary knowledge . The objective function L is not limited to one of the L1 loss function, the L2 loss function, and the cross-entropy loss ...
Embodiment 3
[0090] Embodiment 3 is an improvement on the basis of Embodiment 1, the first meta-knowledge Obtained by training the basic model through the basic behavior data of the server, as the initial value of the meta-basic model trained in the meta-knowledge learning on the client.
[0091] The basic behavior data can be obtained from the user behavior database created by itself, or from the third-party user behavior database in the financial industry or other industry security verification scenarios, which is not limited here.
[0092] According to the basic behavior data, get X tasks , and assign each task Part of the behavioral data in is divided into training set and part as validation set. Specifically, in the basic behavior data, the behavior data of one user is randomly selected as label 1, and the behavior data of other users is set as label 0. In the basic behavioral data of label 1 and label 0, randomly select part of the data as the training set, and other data as th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com