File detection method, device and system and data processing method
A file detection and file technology, applied in the Internet field, can solve the problems of low detection efficiency of malicious files, achieve the effects of improving intuitive perception and interpretability, solving low detection efficiency, and improving detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
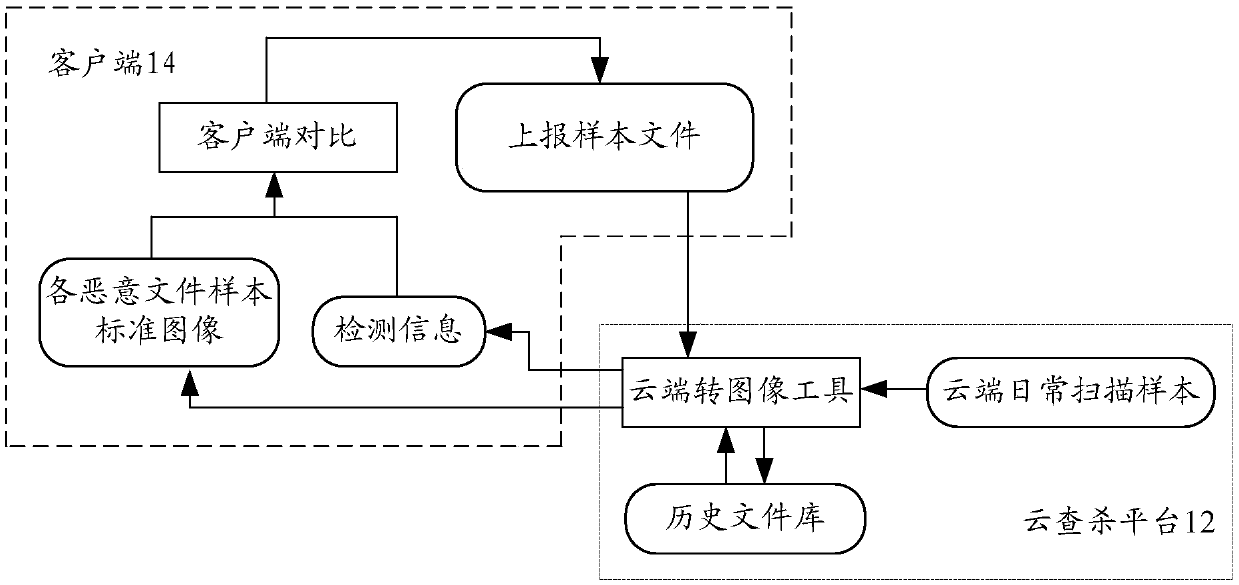
[0042] According to an aspect of an embodiment of the present invention, a file detection system is provided, figure 1It is a structural diagram of a file detection system according to Embodiment 1 of the present invention. Such as figure 1 As shown, the system includes: cloud killing platform 12 and client 14, wherein,
[0043] The client 14 uploads the file to be detected to the cloud killing platform 12;
[0044] The cloud killing platform 12 obtains the file to be detected, compares the file to be detected with the malicious file sample in the historical file storehouse, and obtains detection information; when the detection information indicates that the file to be detected is a malicious file, it determines that the file to be detected is Alert the file, and convert the file type of the file to be detected from a binary file to an image; return the detection information and image to the user;
[0045] The client 14 receives the detection result and the image returned b...
Embodiment 2
[0064] According to an embodiment of the present invention, an embodiment of a method for file detection is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
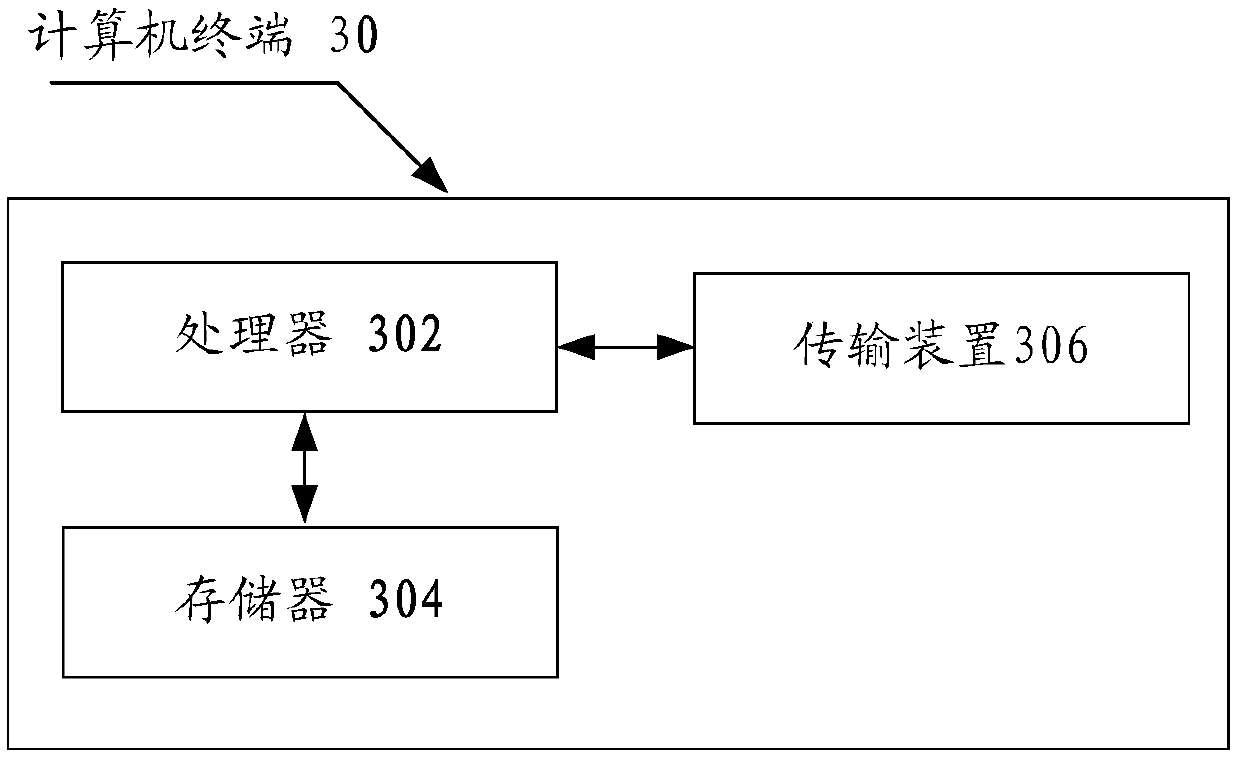
[0065] The method embodiment provided in Embodiment 2 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, image 3 It is a block diagram of the hardware structure of a computer terminal according to a file detection method in an embodiment of the present invention. Such as image 3 As shown, the computer terminal 30 may include one or more (only one is shown in the figure) processor 302 (the p...
Embodiment 3
[0106] According to another aspect of the embodiments of the present invention, a method for file detection is also provided, Figure 5 It is a flow chart of the method for file detection according to Embodiment 3 of the present invention. On the client side, such as Figure 5 As shown, the file detection method provided in the embodiment of the present application is as follows:
[0107] Step S502, uploading the file to be detected to the cloud scanning and killing platform;
[0108] Step S504, receiving detection information and images returned by the cloud scanning and killing platform;
[0109] Step S506, determine whether the file to be detected is a malicious file according to the image and detection information.
[0110] Specifically, in conjunction with steps S502 to S506, corresponding to the client 14 in the file detection system in Embodiment 1, if the client uploads the file to be detected, if it directly uploads the image to the cloud scanning and killing platf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com