A Network Space Mapping Method Based on Service Authentication
A network space and server technology, applied in the field of network space surveying and mapping based on service verification, can solve problems such as low success rate of active detection, impact on network use, network congestion, etc., achieve rich space surveying and mapping information, increase use value, and improve reliability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
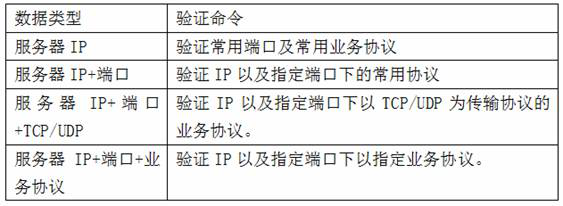
[0038] A network space mapping method based on service verification, characterized in that: the method includes the following steps:
[0039] A. Analyze traffic logs, mirrored traffic, and offline data in sequence to obtain analysis results;
[0040] The traffic log is analyzed: the metadata decoding server MDP parses the offline data packets put into the designated folder;
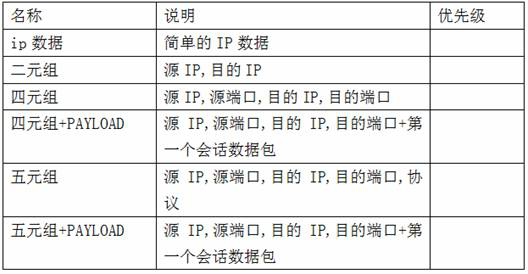
[0041] The mirrored traffic is analyzed: access traffic from the mirrored traffic port of the core switch to the INTER network card, and use the metadata decoding server MDP to parse the traffic data into quintuple+PAYLOAD data;
[0042] The offline data is analyzed: IP, destination port, and protocol obtained from the quintuple information. If there is PAYLOAD, the fingerprint analysis engine is used to identify the equipment corresponding to the port, the operating system, the application, and the primary key information from the PAYLOAD. Save the communication attributes of the original IP and the des...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com