Attribute-based user identity authentication method and system
A user identity authentication and attribute technology, applied in the field of network security, can solve the problem of partial privacy leakage of users, and achieve the effects of improving security, improving authentication efficiency, and reducing communication overhead and computing overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
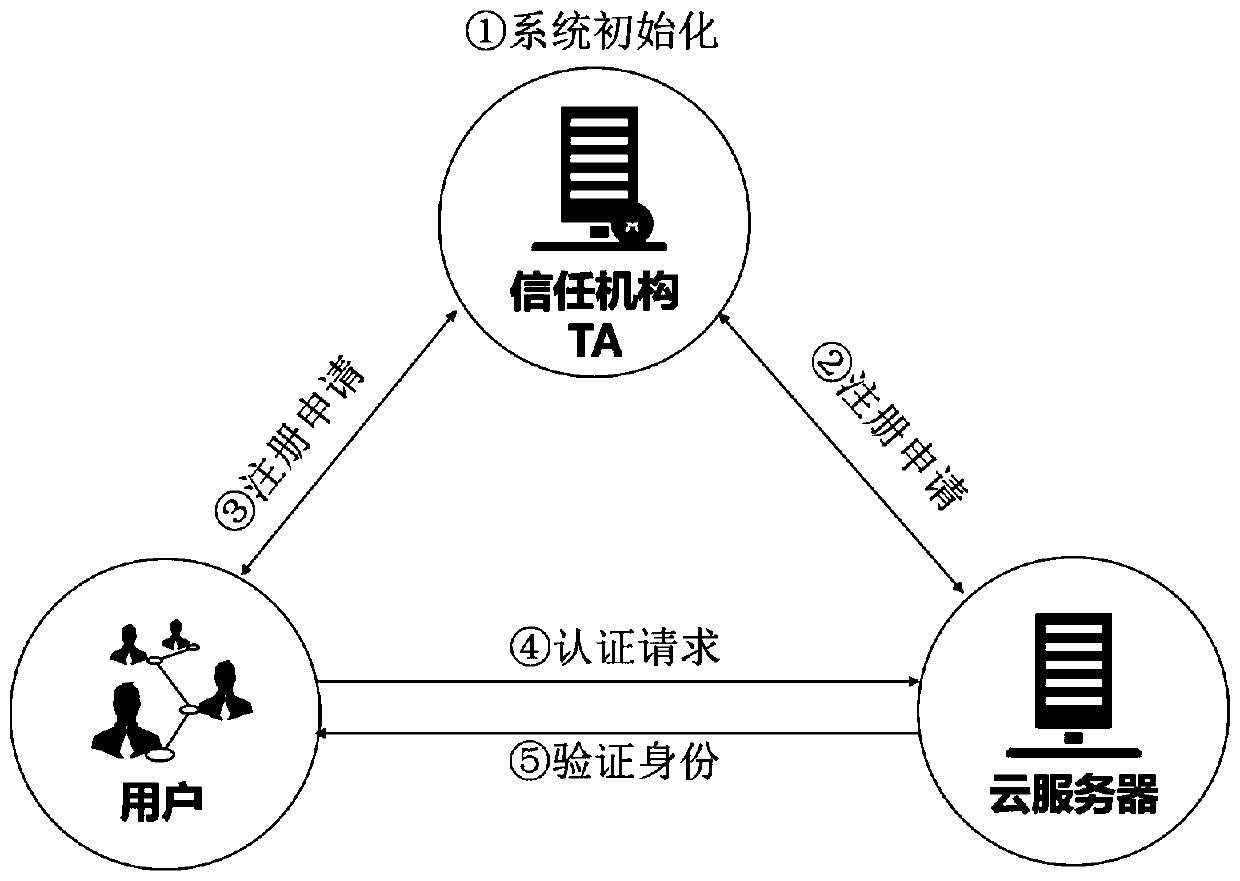
[0090] combine figure 1 , the present invention is an attribute-based user identity authentication system, including a third-party attribute organization, an authentication applicant, and an authentication server;
[0091] The third-party attribute mechanism is used to initialize the entire system;
[0092] The authentication applicant is used to generate an attribute certificate;
[0093] The authentication server is configured to check the validity of the attribute index to determine the authentication.
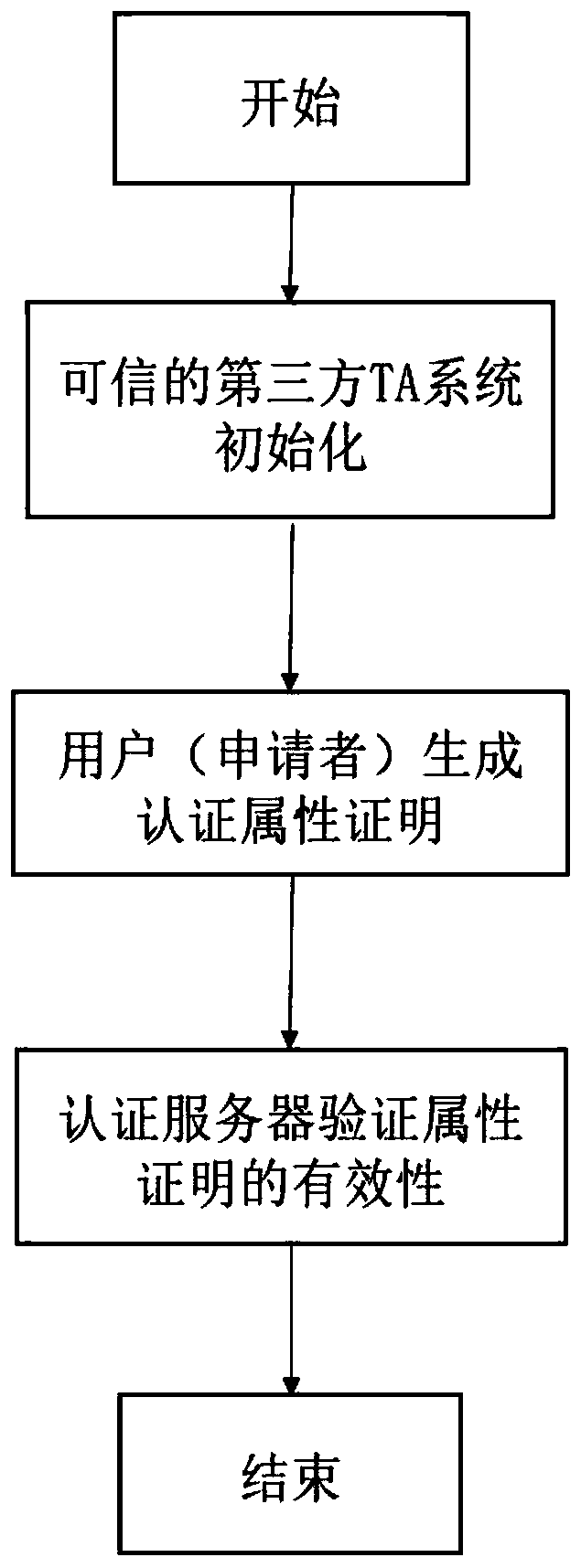
[0094] combine Figure 3-5 , an attribute-based user identity authentication method, comprising the following steps:
[0095] Step 1. The third-party attribute organization initializes the entire system, such as Figure 4 shown.
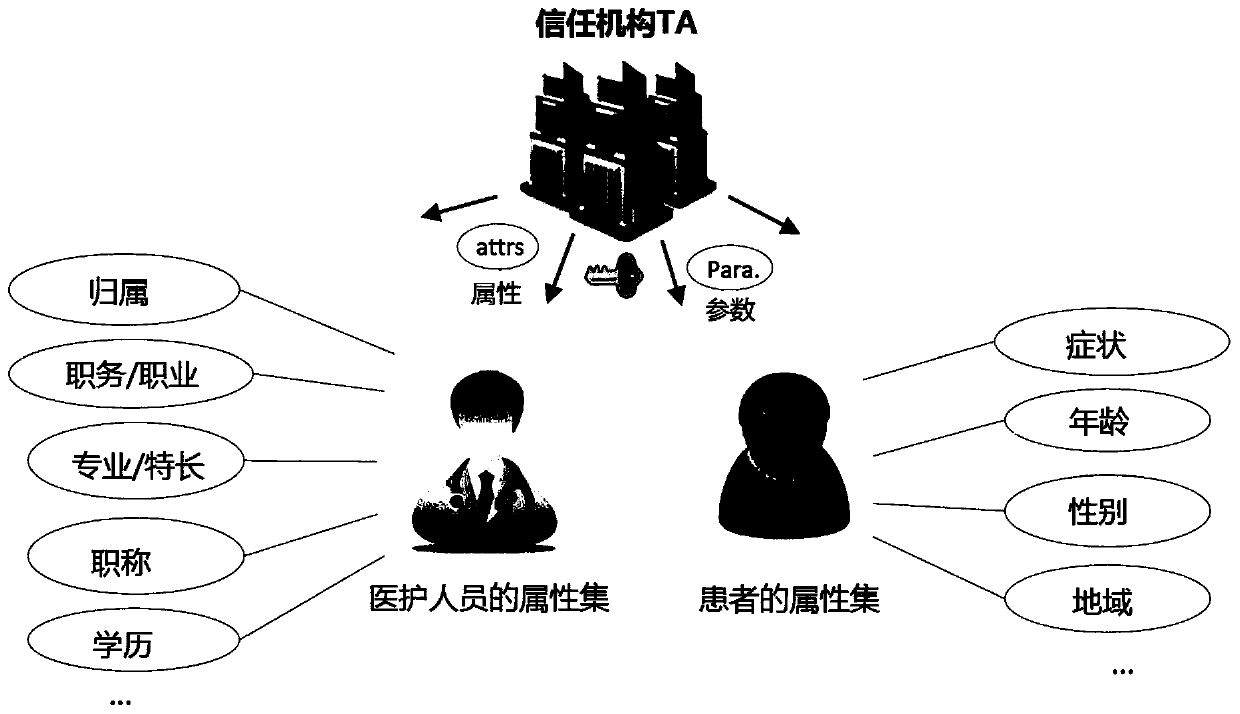
[0096] First, the common attribute set A U formalized as A U = {a1, a2, an} whose output is the system master key MK sys and the public parameter PK sys , where: system master key MK sys =(β, gα)
[0097] Public parameter PK sys Includ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap