Data encryption transmission method, server and system based on virtual private network
A virtual private network and data encryption technology, applied in the field of information security, can solve the problems of virtual private network equipment operation burden, high computing resource overhead, complex operation mechanism, etc. Safe and reliable delivery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
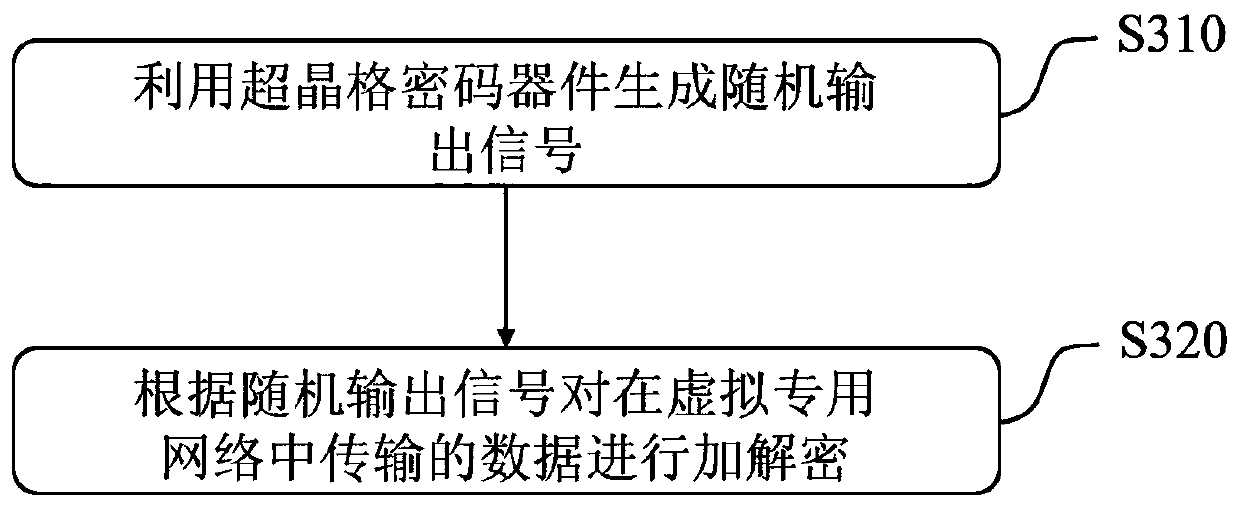
[0051] image 3 It is a flow chart of a data encryption transmission method based on a virtual private network according to an embodiment of the present invention. Here, the virtual private network-based data encryption transmission method according to the embodiment of the present invention is applied to the encryption system 1 . In this embodiment, according to different requirements, image 3 The order of execution of the steps in the flowcharts shown may be changed, and / or certain steps may be omitted.
[0052] refer to image 3 According to the embodiment of the present invention, the data encrypted transmission method based on virtual private network includes the steps of:
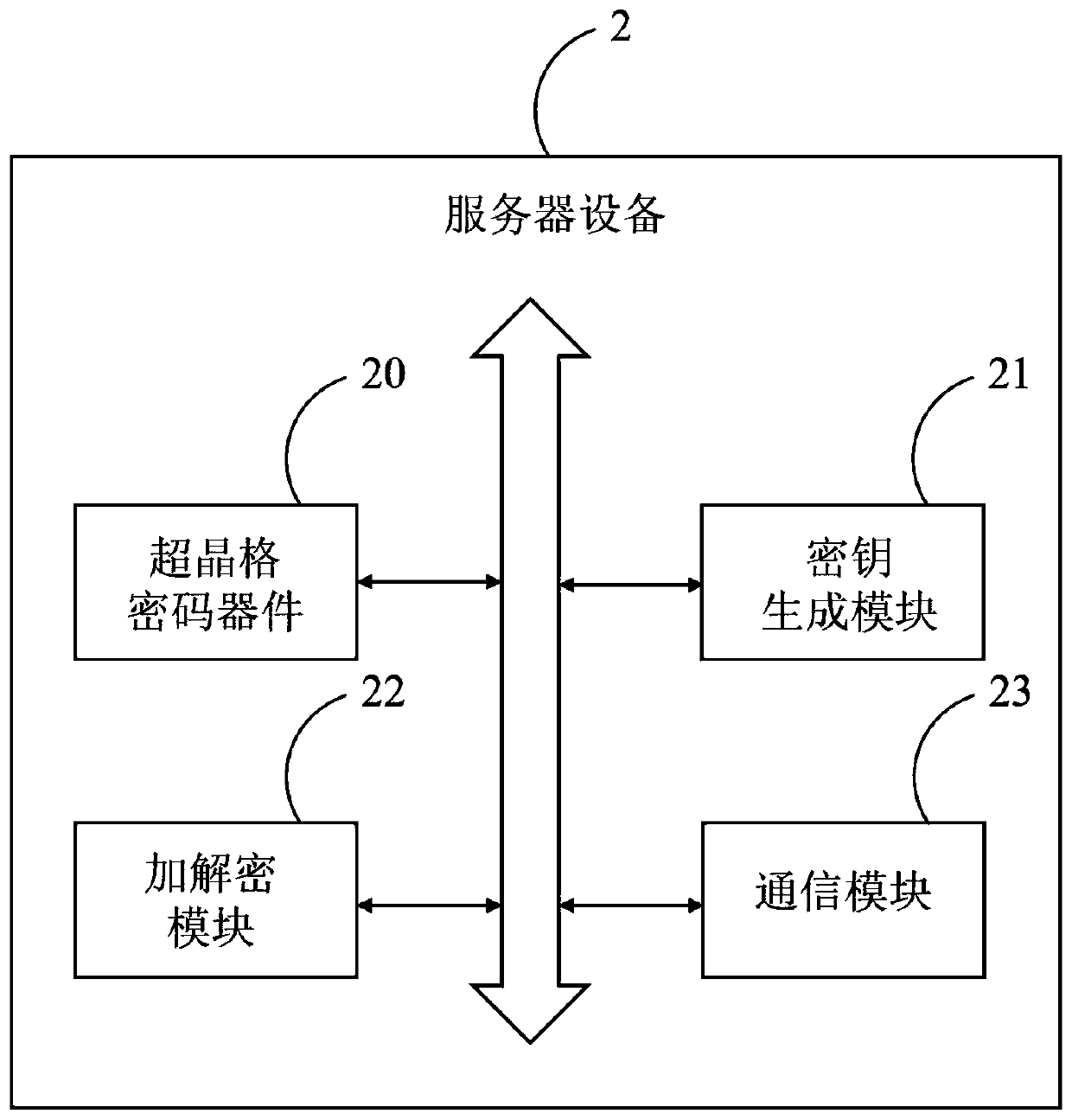
[0053] S310, using the superlattice cryptographic device 20 to generate a random output signal.
[0054] Specifically, in order to ensure that the keys generated by the first server 12 and the second server 13 are the same (or the same as possible to the greatest extent possible), so that there i...
no. 2 approach
[0078] Figure 5 It is a flow chart of a data encryption transmission method based on a virtual private network according to another embodiment of the present invention. In the detailed description of this embodiment, the sender (that is, the first server 12) is taken as the starting point. refer to Figure 5 According to another embodiment of the present invention, the method for encrypted data transmission based on a virtual private network includes the steps of:
[0079] S510, the superlattice cryptographic device 20 of the first server 12 generates a random output signal.
[0080] Here, the superlattice cryptographic device 20 of the first server 12 can generate a first random output signal driven by a signal of a specific form, and the first random output signal is a true random signal.
[0081] S520. The first server 12 encrypts data according to the first random output signal to obtain encrypted data.
[0082] Specifically, first, the key generation module 21 of the...
no. 3 approach
[0087] Figure 6 It is a flow chart of a data encryption transmission method based on a virtual private network according to another embodiment of the present invention. In the detailed description of this embodiment, the receiver (that is, the first server 13) is taken as the starting point. refer to Figure 6 According to another embodiment of the present invention, the method for encrypted data transmission based on a virtual private network includes the steps of:
[0088] S610, the communication module 23 of the second server 13 receives the encrypted data sent by the first server 12 from the virtual private network 11 .
[0089] Of course, here, as mentioned above, the first server 12 encrypts the data according to the first random output signal generated by its superlattice cryptographic device 20 to obtain encrypted data, for details, refer to the above description.
[0090]S620, the key generation module 21 of the second server 13 decrypts the encrypted data accordi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com