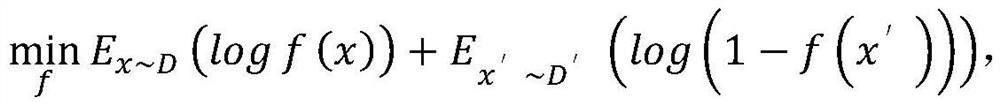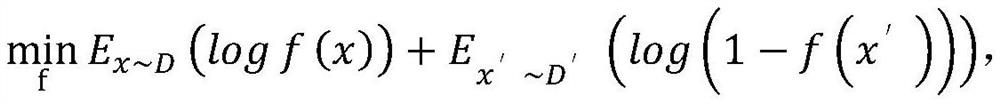A training method for automatic operation and maintenance strategy of information system
A technology of information system and training method, which is applied in software deployment and other directions, and can solve problems such as system crashes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
approach example 1
[0021] [Scheme Example 1] Using supervised learning
[0022] First, several neural networks are established as models of user behavior strategies and information system background.
[0023] Secondly, organize the real information system data into a data set D={(u,c,q,a,u')}, each piece of data corresponds to a tuple (u,c,q,a,u'), where u Indicates the current user set, c indicates the configured system parameters, q indicates the corresponding service quality under parameter c, a indicates user behavior, and u' indicates the new user set after the user performs action a.
[0024] Then, using the real (u, c) in the real data set D as input and the real service quality q as output, a supervised learning method is used to train the service quality evaluation function.
[0025] Again, use the real (u, q) in the real data set D as the input, and the real user behavior a as the output, and use the supervised learning method to train the user behavior strategy.
[0026] Then, use t...
Embodiment 1
[0040] [Example 1] Joint training (using confrontational learning and reinforcement learning)
[0041] First, several neural networks are established as models of user behavior strategies and information system background.
[0042] Secondly, establish a neural network as a discriminator to judge the credibility of the data. The value of the credibility is a real number between 0 and 1. The closer to 1, the more it looks like real data, and the closer it is to 0, the more it looks like generated data. .
[0043] Again, in the step 3)-6) of the information system background and user behavior strategy training process, the joint output of the user behavior strategy and the information system background is spliced into a tuple (u,c,q,a,u') , execute step 7), and construct a simulated data set D'={(u,c,q,a,u')}, use the real data set D and the simulated data set D' during training as data, and update a discriminant device, the update target is as follows:
[0044]
[0045] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com